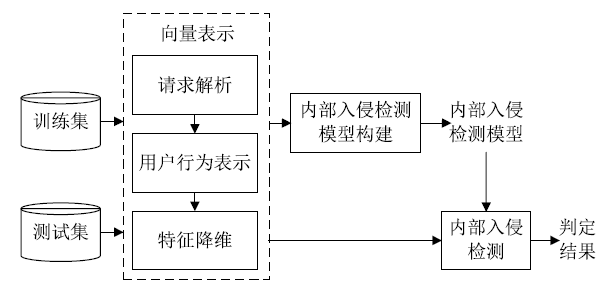
Netinfo Security ›› 2020, Vol. 20 ›› Issue (2): 83-90.doi: 10.3969/j.issn.1671-1122.2020.02.011
• 技术研究 • Previous Articles Next Articles
A Method of Internal Intrusion Detection of Database in RBAC Mode
- Information System & Security and Countermeasures Experiments Center, Beijing Institute of Technology, Beijing 100081, China
-
Received:2019-10-21Online:2020-02-10Published:2020-05-11
CLC Number:
Cite this article
YU Lu, LUO Senlin. A Method of Internal Intrusion Detection of Database in RBAC Mode[J]. Netinfo Security, 2020, 20(2): 83-90.
share this article
| 子特征 | 描述 | f-triplet特征元素 | s-triplet特征元素 |
|---|---|---|---|
| SQL-CMD | 命令特征 | C | C |
| QL(包含空格) | QL(SQL语句词组数目) | ||
| PR-DEC | PR特征 | PR | PR |
| PRID | PRID | ||
| PA-DEC | PA特征 | (PA、PAC、PAID) | (PA、PAC、PAID、SPAV、NPAV) |
| SA-DEC | SA特征 | (SA、SAC、SAID) | (SA、SAC、SAID、SSAV、NSAV) |
| G-DEC | G特征 | (GA、GAC、GAID) | (GA、GAC、GAID、SGV、NGV) |
| O-DEC | O特征 | (OA、OAC、OAID) | (OA、OAC、OAID、SOV、NOV) |
| VAL-DEC | 数值特征 | SV(字符串数目) | SV(字符串数目) |
| SL(字符串拼接长度) | SLmax(字符串最大长度) | ||
| SLmin(字符串最小长度) | |||
| NV(数字数目) | NV(数字数目) | ||
| Nmax(最大数值) | |||
| Nmin(最小数值) | |||
| J(JOIN数目) | J(JOIN数目) | ||
| AO(AND、OR数目) | AO(AND、OR数目) |
| 特征数 | LDA | PCA | ICA | FA | 平均值 | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| 14 | 44 | 68 | 19 | |||||||
| 分类器 | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR |
| NB | 7.45 | 2.05 | 26.71 | 4.61 | 24.24 | 10.78 | 17.27 | 3.39 | 18.92 | 5.21 |
| MLP | 5.42 | 1.45 | 24.93 | 12.12 | 15.58 | 4.96 | 13.25 | 1.97 | 14.80 | 5.13 |
| SVM | 4.21 | 1.11 | 7.09 | 1.11 | 24.33 | 9.26 | 12.34 | 1.81 | 11.99 | 3.32 |
| CART | 4.57 | 1.53 | 8.36 | 1.87 | 4.12 | 1.07 | 5.33 | 1.39 | 5.41 | 1.47 |
| RF | 4.09 | 1.09 | 6.03 | 1.41 | 6.94 | 1.67 | 4.09 | 1.12 | 5.29 | 1.32 |
| WRF | 3.84 | 0.53 | 6.45 | 1.05 | 6.78 | 0.69 | 3.96 | 0.26 | 5.26 | 0.63 |
| 平均值 | 4.93 | 1.29 | 13.26 | 3.70 | 13.67 | 4.74 | 9.37 | 1.66 | ||
| 特征数 | LDA | PCA | ICA | FA | 平均值 | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| 16 | 50 | 74 | 40 | |||||||
| 分类器 | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR |
| NB | 6.63 | 0.59 | 26.45 | 1.43 | 20.57 | 1.19 | 14.81 | 1.84 | 17.12 | 1.26 |
| MLP | 5.29 | 0.51 | 25.86 | 1.53 | 7.48 | 0.28 | 11.58 | 0.73 | 12.55 | 0.76 |
| SVM | 4.51 | 0.29 | 6.69 | 0.23 | 15.55 | 0.53 | 11.95 | 1.18 | 9.68 | 0.56 |
| CART | 4.06 | 0.26 | 5.82 | 0.74 | 4.12 | 0.13 | 4.95 | 0.34 | 4.74 | 0.37 |
| RF | 3.92 | 0.31 | 5.79 | 0.61 | 4.08 | 0.26 | 3.81 | 0.46 | 4.40 | 0.41 |
| WRF | 3.06 | 0.28 | 5.71 | 0.61 | 3.08 | 0.28 | 3.41 | 0.43 | 3.82 | 0.40 |
| 平均值 | 4.58 | 0.37 | 12.72 | 0.86 | 9.15 | 0.45 | 8.42 | 0.83 | ||
| 特征数 | LDA | PCA | ICA | FA | 平均值 | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| 12 | 46 | 50 | 18 | |||||||
| 分类器 | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR |
| NB | 1.00 | 0.11 | 5.83 | 0.25 | 6.05 | 0.71 | 22.91 | 14.07 | 8.95 | 3.79 |
| MLP | 1.02 | 0.11 | 6.35 | 0.23 | 1.16 | 0.21 | 5.30 | 0.78 | 3.46 | 0.33 |
| SVM | 1.00 | 0.17 | 9.61 | 0.56 | 2.78 | 0.34 | 4.88 | 0.66 | 4.57 | 0.43 |
| CART | 0.91 | 0.12 | 0.91 | 0.22 | 0.91 | 0.19 | 0.82 | 0.40 | 0.89 | 0.23 |
| RF | 0.73 | 0.17 | 0.79 | 0.13 | 0.91 | 0.17 | 1.00 | 0.13 | 0.86 | 0.15 |
| WRF | 0.62 | 0.10 | 0.61 | 0.10 | 0.74 | 0.10 | 0.91 | 0.29 | 0.72 | 0.14 |
| 平均值 | 0.88 | 0.13 | 4.02 | 0.25 | 2.09 | 0.29 | 5.97 | 2.72 | ||
| 特征数 | LDA | PCA | ICA | FA | 平均值 | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| 15 | 51 | 40 | 20 | |||||||
| 分类器 | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR |
| NB | 0.91 | 0.06 | 11.93 | 2.78 | 6.65 | 0.62 | 15.20 | 6.25 | 8.67 | 2.43 |
| MLP | 0.95 | 0.06 | 5.62 | 0.75 | 1.96 | 0.17 | 4.73 | 0.56 | 3.32 | 0.39 |
| SVM | 1.04 | 0.10 | 4.09 | 0.42 | 1.53 | 0.15 | 4.71 | 0.51 | 4.07 | 0.41 |
| CART | 0.78 | 0.10 | 0.98 | 0.10 | 0.85 | 0.10 | 0.85 | 0.06 | 0.87 | 0.09 |
| RF | 0.76 | 0.12 | 0.91 | 0.10 | 0.91 | 0.10 | 0.76 | 0.10 | 0.84 | 0.11 |
| WRF | 0.62 | 0.09 | 0.61 | 0.10 | 0.63 | 0.10 | 0.64 | 0.19 | 0.63 | 0.12 |
| 平均值 | 0.84 | 0.09 | 4.02 | 0.71 | 2.09 | 0.21 | 4.48 | 1.28 | ||
| s | NB | MLP | SVM | CART | RF | WRF | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR | FPR | FNR | |
| 0 | 6.63 | 0.59 | 5.29 | 0.51 | 4.51 | 0.29 | 4.06 | 0.26 | 3.92 | 0.31 | 3.06 | 0.28 |
| 1 | 5.22 | 0.38 | 5.31 | 0.39 | 3.91 | 0.24 | 3.83 | 0.21 | 3.61 | 0.24 | 2.74 | 0.21 |
| 2 | 5.08 | 0.37 | 3.31 | 0.22 | 3.04 | 0.12 | 3.71 | 0.17 | 2.77 | 0.12 | 2.25 | 0.11 |
| 3 | 2.12 | 0.17 | 2.08 | 0.15 | 2.05 | 0.12 | 1.78 | 0.12 | 1.74 | 0.09 | 1.31 | 0.10 |
| 4 | 0.91 | 0.06 | 0.95 | 0.06 | 1.04 | 0.10 | 0.78 | 0.10 | 0.76 | 0.12 | 0.58 | 0.06 |
| 平均值 | 3.99 | 0.31 | 3.39 | 0.27 | 3.64 | 0.17 | 2.83 | 0.17 | 2.56 | 0.17 | 1.99 | 0.15 |
| [1] | LI Yong, YANG Huafen.Simulation and Analysis of ACCESS Control List in Simulator[J]. Research and Exploration in Laboratory, 2018, 37(12): 144-147. |
| 李勇,杨华芬.访问控制列表在模拟器中的实验仿真与分析[J]. 实验室研究与探索,2018,37(12):144-147. | |
| [2] | XIONG Houren, CHEN Xingyuan, DU Xuehui, et al.Survey of Security Analysis for Role-based Access Control[J]. Application Research of Computers, 2015, 32(11): 3201-3208. |
| 熊厚仁,陈性元,杜学绘,等.基于角色的访问控制模型安全性分析研究综述[J]. 计算机应用研究,2015,32(11):3201-3208. | |
| [3] | QI Jianhuai, SONG Jing, WANG Yang, et al.Application of Mandatory Access Control Technology in Database Security Access[J]. Communications Technology, 2018, 51(3): 692-695. |
| 戚建淮,宋晶,汪暘,等.强制访问控制技术在数据库安全访问中的应用[J]. 通信技术,2018,51(3):692-695. | |
| [4] | DARWISH S M, GUIRGUIS S K, GHOZLAN M M.Intrusion Detection in Role Administrated Database: Transaction-based Approach[C]//IEEE. International Conference on Computer Engineering & Systems, November 26-28, 2013, Cairo, Egypt. New Jersey: IEEE, 2013: 73-79. |
| [5] | ISLAM M S, KUZU M, KANTARCIOGLU M.A Dynamic Approach to Detect Anomalous Queries on Relational Databases[C]//ACM. 5th ACM Conference on Data and Application Security and Privacy, March 1, 2015, San Antonio, USA. New York: ACM, 2015: 245-252. |
| [6] | BERTINO E, KAMRA A, TERZI E, et al.Intrusion Detection in RBAC-administered Databases[C]//IEEE. Annual Computer Security Applications Conference, December 5-9, 2005, Tucson, AZ, USA. New York: IEEE, 2005: 173-182. |
| [7] | KAMRA A, TERZI E, BERTINO E.Detecting Anomalous Access Patterns in Relational Databases[J]. VLDB Journal, 2008, 17(5): 1063-1077. |
| [8] | RONAO C A, CHO S B.Mining SQL Queries to Detect Anomalous Database Access Using Random Forest and PCA[C]//IEA. Current Approaches in Applied Artificial Intelligence, June 10-12, 2015, Seoul, South Korea. Heidelberg: Springer, 2015: 151-160. |
| [9] | BU S J, CHO S B.A Hybrid System of Deep Learning and Learning Classifier System for Database Intrusion Detection[C]//HAIS. International Conference on Hybrid Artificial Intelligence Systems, June 21-23, 2017, La Rioja, Spain. Heidelberg: Springer, 2017: 615-625. |
| [10] | LIU Jianping. Summary of the Principle of Linear Discriminant Analysis[EB/OL]. , 2017-1-3. |
| 刘建平.线性判别分析LDA原理总结[EB/OL]. ,2017-1-3. | |
| [11] | DAHO M E H, SETTOUTI N, LAZOUNI M E A, et al. Weighted Vote for Trees Aggregation in Random Forest[C]//IEEE. International Conference on Multimedia Computing & Systems, April 14-16, 2014, Marrakech, Morocco. New Jersey: IEEE, 2014: 438-443. |
| [12] | TPC. TPC benchmark E, Standard specification, Version 1.13.0[EB/OL]. , 2007-2-11. |
| [13] | YANG chao. Design and Implementation of TPC-E[D]. Wuhan: Huazhong University of Science and Technology, 2011. |
| 杨超. TPC-E测试系统的设计与实现[D].武汉:华中科技大学,2011. | |
| [14] | LIU Shengjiu, LI Tianrui, ZHU Jie.Zipf’s Law and Webometrics[J]. Journal of Chinese Information Processing, 2015, 29(4): 89-94. |
| 刘胜久,李天瑞,珠杰. Zipf定律与网络信息计量学[J]. 中文信息学报,2015,29(4):89-94. | |
| [15] | RONAO C A, CHO SB. A Comparison of Data Mining Techniques for Anomaly Detection in Relational Databases[EB/OL]. , 2015-2-22. |
| [1] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [2] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [3] | LIU Peng, HE Qian, LIU Wangyang, CHENG Xu. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [4] | XU Shengwei, WANG Feijie. Attribute-based Encryption Scheme Traced Under Multi-authority [J]. Netinfo Security, 2020, 20(1): 33-39. |
| [5] | BAI Jiameng, KOU Yingshuai, LIU Zeyi, ZHA Daren. Docker-based RBAC Task Management System [J]. Netinfo Security, 2020, 20(1): 75-82. |
| [6] | Jinmiao WANG, Guowei WANG, Mei WANG, Ruijin ZHU. Achieving Privacy Preserving and Flexible Access Control in Fog Computing [J]. Netinfo Security, 2019, 19(9): 41-45. |
| [7] | A-yong YE, Junlin JIN, Lingyu MENG, Ziwen ZHAO. Research on Access Control for Privacy Protection of Mobile Terminals [J]. Netinfo Security, 2019, 19(8): 51-60. |
| [8] | Zhongyuan QIN, Yin HAN, Qunfang ZHANG, Xuejin ZHU. An Improved Scheme of Multi-PKG Cloud Storage Access Control [J]. Netinfo Security, 2019, 19(6): 11-18. |
| [9] | Fangbo CAI, Jingsha HE, Nafei ZHU, Song HAN. Research on Cascading Failure of Nodes in Distributed Access Control Model [J]. Netinfo Security, 2019, 19(12): 47-52. |
| [10] | Xiangquan SHI, Jing TAO, Baokang ZHAO. A Network Access Control System in Virtualized Environments [J]. Netinfo Security, 2019, 19(10): 1-9. |
| [11] | Zhanzhen WEI, Shourong WANG, Zhaobin LI, Weilong LI. Research on SDN Terminal Access Control Based on OpenFlow [J]. Netinfo Security, 2018, 18(4): 23-31. |
| [12] | Yue SHI, Xianglong LI, Fangfang DAI. An Enhanced Security Framework of Software Defi ned Network Based on Attribute-based Encryption [J]. Netinfo Security, 2018, 18(1): 15-22. |
| [13] | Guojun MA, Kai LI, Qingqi PEI, Yang ZHAN. A Fine-Grained Face Privacy Protection Scheme in Social Networks [J]. Netinfo Security, 2017, 17(8): 26-32. |
| [14] | QING Yong, SUN Wei, XIONG Hu, ZHAO Yang. Outsourcing Encryption and Decryption CP-ABE Scheme with Revocation Storage in Cloud Computing [J]. 信息网络安全, 2017, 17(6): 6-8. |
| [15] | Chunhua GU, Yuan GAO, Xiuxia TIAN. Security Optimized RBAC Access Control Model [J]. Netinfo Security, 2017, 17(5): 74-79. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||