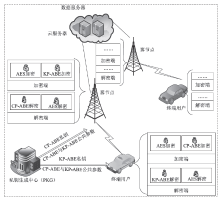
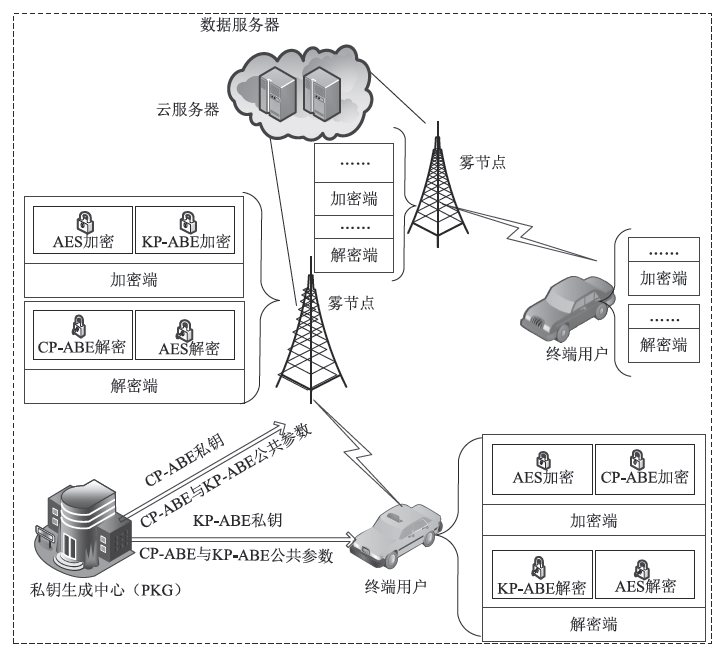
| [1] |
WANG Yifang, UEHARA T, SASAKI R.Fog Computing: Issues and Challenges in Security and Forensics[C]//IEEE. IEEE Computer Software and Applications Conference, July 1-5, 2015, Taiwan, China. New Jersey: IEEE, 2015: 53-59.
|
| [2] |
YI Shanhe, QIN Zhengrui, LI Qun.Security and Privacy Issues of Fog Computing: A Survey[C]//Springer. Wireless Algorithms Systems and Applications, August 10-12, 2015, Qufu, China. Heidelberg: Springer, 2015: 685-695.
|
| [3] |
ALLIANCE C. Security Guidance for Critical Areas of Focus in Cloud Computing v3.0[EB/OL]. , 2019-1-22.
|
| [4] |
SAHAI A, WATERS B.Fuzzy Identity-based Encryption[C]//Springer. Advances in Cryptology-EUROCRYPT 2005, May 22-26, 2005, California, USA. Heidelberg: Springer, 2005: 457-473.
|
| [5] |
GOYAL V, PANDEY O, SAHAI A, et al.Attribute-based Encryption for Fine-grained Access Control of Encrypted Data[C]//ACM. ACM Conference on Computer and Communications Security, October 30-November 3, 2006, Alexandria, Virginia, USA. New York: ACM, 2006: 89-98.
|
| [6] |
BETHENCOURT J, SAHAI A, WATERS B.Ciphertext-policy Attribute-based Encryption[C]//IEEE. IEEE Symposium on Security and Privacy, May 20-23, 2007, Berkeley, USA. New Jersey: IEEE, 2007: 321-334.
|
| [7] |
YI Shanhe, LI Cheng, LI Qun.A Survey of Fog Computing: Concepts, Applications and Issues[C]//ACM. ACM Workshop on Mobile Big Data, June 21, 2015, Hangzhou, China. New York: ACM, 2015: 37-42.
|
| [8] |
KANNA T R, NAGARAJU M, BHASKAR C V.Secure Fog Computing: Providing Data Security[J]. International Journal of Research in Computer and Communication Technology, 2015, 4(1): 53-55.
|
| [9] |
YU Shucheng, WANG C, REN Kui, et al.Achieving Secure, Scalable, and Fine-grained Data Access Control in Cloud Computing[C]//IEEE. 29th Conference on Information Communications, March 14-19, 2010, San Diego, California, USA. New Jersey: IEEE, 2010: 1-9.
|
| [10] |
LANG Bo, WANG Jinmiao, LIU Yanxi. AchievingFlexible and Self-Contained Data Protection in Cloud Computing[EB/OL]. , 2017-3-13.
|
| [11] |
LANG Bo, XU Runhua, DUAN Yawei.Extending the Ciphertext-policy Attribute Based Encryption Scheme for Supporting Flexible Access Control[C]//IEEE. 10th International Conference on Security and Cryptography, July 29-31, 2013, Reykjavik, Iceland. New Jersey: IEEE, 2013: 147-157.
|
| [12] |
YU Zuoxia, AU M H, XU Qiuliang, et al. Towards Leakage-resilient Fine-grained Access Control in Fog Computing[EB/OL]. , 2019-2-11.
|
| [13] |
DSOUZA C, AHN G J, TAGUINOD M.Policy-driven Security Management for Fog Computing: Preliminary Framework and a Case Study[C]//IEEE. IEEE International Conference on Information Reuse and Integration, August 13-15, 2014, Redwood City, CA. New Jersey: IEEE, 2014: 16-23.
|
| [14] |
LU Rongxing, LIANG Xiaohui, LI Xu, et al.EPPA: An Efficient and Privacy-preserving Aggregation Scheme for Secure Smart Grid Communications[J]. IEEE Transactions On Parallel and Distributed Systems, 2012, 23(9): 1621-1631.
|
| [15] |
CAO Zhenhai, LANG Bo, WANG Jinmiao.An Efficient and Fine-grained Access Control Scheme for Multidimensional Data Aggregation in Smart Grid[C]//IEEE. IEEE International Conference on Trust, Security and Privacy in Computing and Communications, August 23-26, 2016, Tianjin, China. New Jersey: IEEE, 2016: 362-369.
|
| [16] |
LIU Jianhua, ZHENG Xiaokun, ZHENG Dong, et al.Secure Attribute Based Encryption Enabled Cloud Storage System with Ciphertext Search[J]. Netinfo Security, 2019, 19(7): 50-58.
|
|
刘建华,郑晓坤,郑东,等.基于属性加密且支持密文检索的安全云存储系统[J].信息网络安全,2019,19(7):50-58.
|