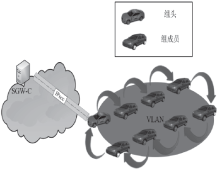
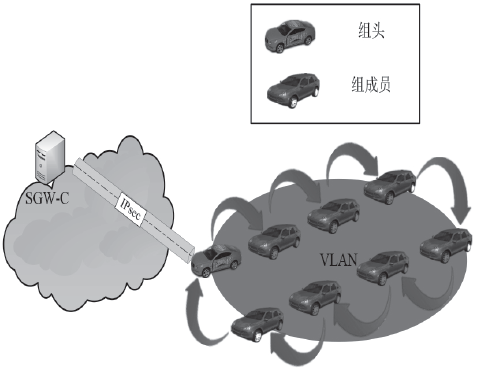
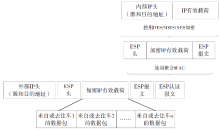
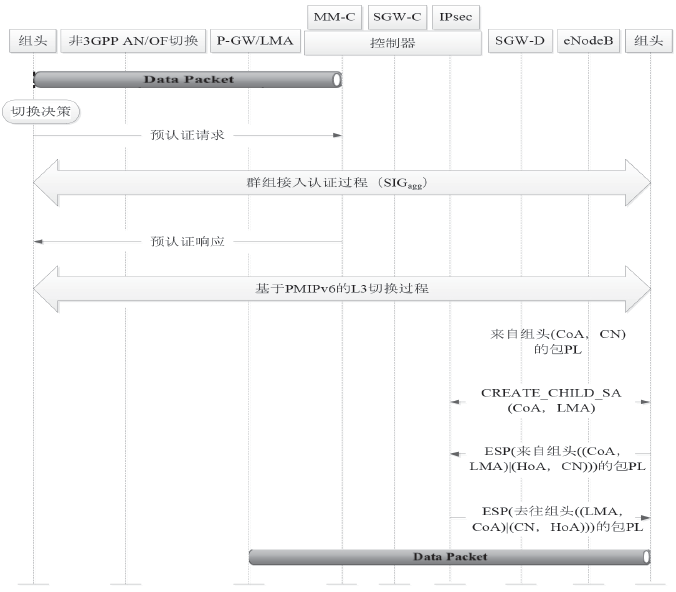
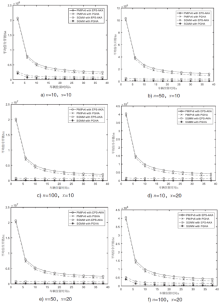
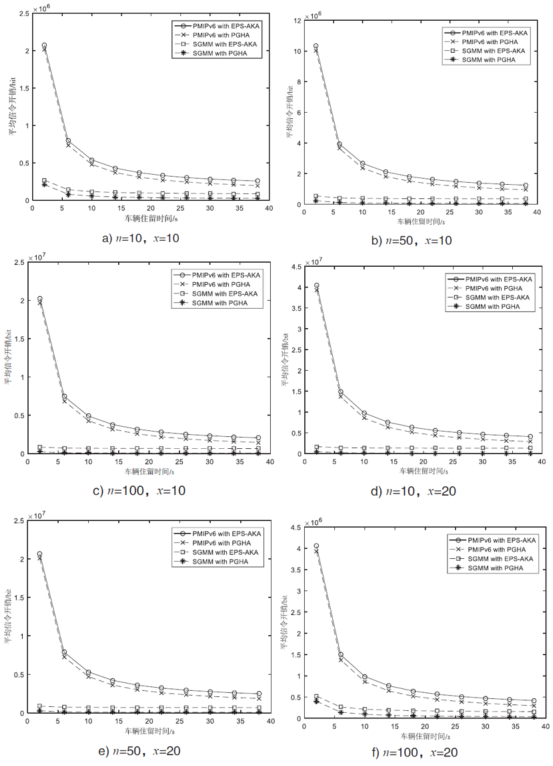
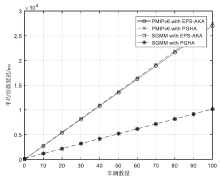
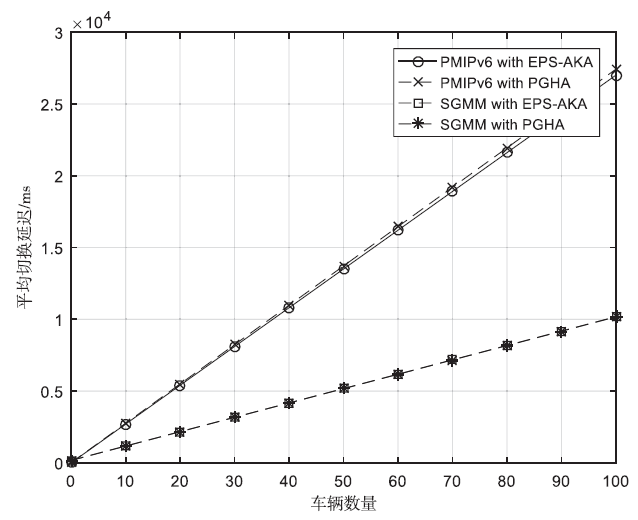
Netinfo Security ›› 2018, Vol. 18 ›› Issue (7): 36-46.doi: 10.3969/j.issn.1671-1122.2018.07.005
• Orginal Article • Previous Articles Next Articles
Secure Mobility Management Framework with Privacy Preservation for Vehicle Platoon
- National Engineering Laboratory for Wireless Security, Xi’an University of Posts and Telecommunications, Xi’an Shaanxi 710121, China
-
Received:2017-11-15Online:2018-07-15Published:2020-05-11
CLC Number:
Cite this article
Chengzhe LAI, Wenjuan WANG. Secure Mobility Management Framework with Privacy Preservation for Vehicle Platoon[J]. Netinfo Security, 2018, 18(7): 36-46.
share this article
| [1] | LU N, CHENG N, ZHANG N, et al.Connected Vehicles: Solutions and Challenges[J].Internet of Things Journal IEEE, 2014, 1(4):289-299. |
| [2] | SU Z, HUI Y, YANG Q.The Next Generation Vehicular Networks: A Content-Centric Framework[J].IEEE Wireless Communications, 2017, 24(1):60-66. |
| [3] | LUAN T H,LU R,SHEN X, et al.Social on the Road: Enabling Secure and Efficient Social Networking on Highways[J].IEEE Wireless Communications, 2015, 22(1):44-51. |
| [4] | LAI C,ZHANG K,CHENG N,et al.SIRC: A Secure Incentive Scheme for Reliable Cooperative Downloading in Highway VANETs[J].IEEE Transactions on Intelligent Transportation Systems, 2017,18(99):1-16. |
| [5] | FU Z,WU X,GUAN C, et al.Toward Efficient Multi-Keyword Fuzzy Search Over Encrypted Outsourced Data With Accuracy Improvement[J].IEEE Transactions on Information Forensics & Security, 2016, 11(12):2706-2716. |
| [6] | LUAN T H, LING X, SHEN X.MAC in Motion: Impact of Mobility on the MAC of Drive-Thru Internet[J].IEEE Transactions on Mobile Computing, 2011, 11(2):305-319. |
| [7] | SHANG Jin, XIE Jun, JIANG Dongyi, et al.Research on Abnormal Behavior Analysis of Modern Networking Security Architecture. Netinfo Security, 2015, 15(9): 15-19. |
| 尚进,谢军,蒋东毅,等.现代网络安全架构异常行为分析模型研究[J].信息网络安全,2015,15(9):15-19. | |
| [8] | PERKINS C E, JOHNSON D B. Mobility Support in IPv6[EB/OL]. ,2011-7-15. |
| [9] | TSAO S L,LIN C C.Design and Evaluation of UMTS-WLAN Interworking Strategies[EB/OL].,2017-10-15. |
| [10] | CHEN J C, CHEN W M, LIN H W. Design and Analysis of GPRS-WLAN Mobility Gateway (GWMG)[EB/OL].,2017-10-15. |
| [11] | PHIRI F A, MURTHY M B R. WLAN-GPRS Tight Coupling Based Interworking Architecture with Vertical Handoff Support[J].Wireless Personal Communications, 2007, 40(2):137-144. |
| [12] | WU I W, CHEN W S, Liao H E, et al.A seamless handoff approach of Mobile IP protocol for mobile wireless data networks[J]. IEEE Transactions on Consumer Electronics, 2002, 48(2):335-344. |
| [13] | YUAN Chao, ZHANG Hao, Gulliver Thomas Aaron.ASEP Performance Analysis of Vehicle-to-Vehicle Communication System over N-Rayleigh Fading Channels in IoV[J].Netinfo Security, 2016,16(3): 40-46. |
| 袁超,张浩,GULLIVER T A.车联网中协作车—车通信系统在N-Rayleigh信道下ASEP性能分析[J].信息网络安全,2016,16(3):40-46. | |
| [14] | BADCHE N,TANDJAOUI D.A Seamless Handoff Protocol for Hierarchical Mobile IPv4[C]//IEEE. International Workshop on Mobile and Wireless Communications Network, September 9-11, 2002, Stockholm, Sweden. New York: IEEE, 2002:651-655. |
| [15] | ZUO Qingyun, ZHANG Haisu.Analysis and Research on Network Security for OpenFlow-based SDN[J].Netinfo Security, 2015, 15(2): 26-32. |
| 左青云,张海粟. 基于OpenFlow的SDN网络安全分析与研究[J]. 信息网络安全,2015,15(2):26-32. | |
| [16] | KIM M S, LEE S K.Enhanced Network Mobility Management for Vehicular Networks[J].IEEE Transactions on Intelligent Transportation Systems, 2016, 17(5):1329-1340. |
| [17] | FERNANDEZ J, BERNAL F, et al.Securing Vehicular IPv6 Communications[J].IEEE Transactions on Dependable and Secure Computing, 2016, 13(1):46-58. |
| [18] | VINEL A, LAN L, LYAMIN N.Vehicle-to-Vehicle Communication in C-ACC/Platooning Scenarios[J].IEEE Communications Magazine, 2015, 53(8):192-197. |
| [19] | COOPER C, FRANKLIN D, ROS M, et al.A Comparative Survey of VANET Clustering Techniques[J].IEEE Communications Surveys & Tutorials, 2017, 19(1):657-681. |
| [20] | LU R,LIN X,SHEN X.SPOC: A Secure and Privacy-Preserving Opportunistic Computing Framework for Mobile-Healthcare Emergency[J].IEEE Transactions on Parallel and Distributed Systems, 2013, 24(3):614-624. |
| [21] | LAI Chengzhe, ZHENG Dong.Research on 3GPP Authentication and Key Agreement Protocols[J].Netinfo Security, 2016, 16(8): 24-31. |
| 赖成喆,郑东.3GPP认证和密钥协商协议综述[J].信息网络安全,2016,16(8):24-31. | |
| [22] | KIM Y, PERRIG A,TSUDIK G.Simple and Fault-tolerant Key Agreement for Dynamic Collaborative Groups[C]//ACM. ACM Conference on Computer and Communications Security. November 1-4, 2000, Athens, Greece. New York: ACM, 2000:235-244. |
| [23] | LAI C,LU R,ZHENG D.SPGS: A Secure and Privacy-Preserving Group Setup Framework for Platoon-based Vehicular Cyber-Physical Systems[M]. New York:Scurity and Communication Networks,2016. |
| [24] | LI J, KIM K, ZHANG F, et al.Aggregate Proxy Signature and Verifiably Encrypted Proxy Signature[C]//Springer-Verlag. International Conference on Provable Security. November 1-2, 2007, Wollonggong, Australia. Berlin, Germany: Springer-Verlag, 2007:208-217. |
| [25] | LO S C, LEE G, CHEN W T, et al.Architecture for Mobility and QoS Support in all-IP Wireless Networks[J]. IEEE Journal on Selected Areas in Communications, 2004, 22(4):691-705. |
| [26] | KONG K S, LEE W, HAN Y H, et al.Mobility Management for all-IP Mobile Networks: Mobile IPv6 vs. Proxy Mobile IPv6[J]. IEEE Wireless Communications, 2008, 15(2):36-45. |
| [27] | STEPHANE A, AGHVAMI A H.Fast Handover Schemes for Future Wireless IP Networks: A Proposal and Analysis[C]//IEEE. Vehicular Technology Conference, May 6-9, 2001, Rhodes, Greece. New York: IEEE, 2001:2046-2050. |
| [28] | LAI C, LI H, LU R, et al.SE-AKA: A Secure and Efficient Group Authentication and Key Agreement Protocol for LTE Networks[J].Computer Networks, 2013, 57(17):3492-3510. |
| [29] | LAI C, LI H, LU R, et al.SEGR: A Secure and Efficient Group Roaming Scheme for Machine to Machine Communications between 3GPP and WiMAX Networks[C]//IEEE. IEEE International Conference on Communications, June 10-14, 2014, Sydney, NSW, Australia. New York: IEEE, 2014:1011-1016. |
| [30] | LAI C, LU R, ZHENG D. Achieving Secure and Seamless IP Communications for Group-Oriented Software Defined Vehicular Networks[EB/OL]., 2017-10-15. |
| [31] | FAIGL Z,LINDSKOG S,BRUNSTROM A.Performance Evaluation of IKEv2 Authentication Methods in Next Generation Wireless Networks[J].Security and Communication Networks, 2010, 3(1):83-98. |
| [32] | FATHI H, PRASASD R,CHAKRABORTY S.Mobility Management for VoIP in 3G Systems: Evaluation of Low-Latency Handoff Schemes[J].IEEE Wireless Communications, 2005, 12(2):96-104. |
| [33] | LAI C,LU R,ZHENG D, et al.GLARM: Group-based Lightweight Authentication Scheme for Resource-Constrained Machine to Machine Communications[J].Computer Networks,2016,99:66-81. |
| [1] | Jinmiao WANG, Guowei WANG, Mei WANG, Ruijin ZHU. Achieving Privacy Preserving and Flexible Access Control in Fog Computing [J]. Netinfo Security, 2019, 19(9): 41-45. |
| [2] | Quan ZHOU, Shumei XU, Ningbin YANG. A Privacy Protection Scheme for Smart Grid Based on Attribute-based Group Signature [J]. Netinfo Security, 2019, 19(7): 25-30. |
| [3] | Xiangquan SHI, Jing TAO, Baokang ZHAO. A Network Access Control System in Virtualized Environments [J]. Netinfo Security, 2019, 19(10): 1-9. |
| [4] | Qinghe DONG, Qian HE, Bingcheng JIANG, Peng LIU. Scheme of Cloud Database Oriented Multi-tenant Attribute-based Security Isolation and Data Protection [J]. Netinfo Security, 2018, 18(7): 60-68. |
| [5] | Yue WANG, Xiangguo CHENG, Xuqi WANG. Research on Key-insulated Group Signature Scheme Based on Bilinear Pairings [J]. Netinfo Security, 2018, 18(6): 61-66. |
| [6] | Weijun ZHU, Yongwen FAN, Shaohuan BAN. A Mimic-automaton-based Model for the MSISDN Virtualization and Its Method for Verifying the Security [J]. Netinfo Security, 2018, 18(4): 15-22. |
| [7] | Zhanzhen WEI, Shourong WANG, Zhaobin LI, Weilong LI. Research on SDN Terminal Access Control Based on OpenFlow [J]. Netinfo Security, 2018, 18(4): 23-31. |
| [8] | Yimin XIA, Chungen XU, Bennian DOU. An Anonymous Identity-based Encryption Scheme in the Standard Model [J]. Netinfo Security, 2018, 18(4): 72-78. |
| [9] | LI Jianfeng, LIU Yuan, ZHANG Hao, WANG Xiaofeng. Research and Implementation of Routing Performance Optimization for IaaS Cloud Platform [J]. 信息网络安全, 2017, 17(9): 10-15. |
| [10] | DU Qingling. Identity-based Dynamic Group Communication Signcryption Scheme [J]. 信息网络安全, 2017, 17(9): 42-44. |
| [11] | MA Guojun, LI Kai, PEI Qingqi, ZHAN Yang. A Fine-Grained Face Privacy Protection Scheme in Social Networks [J]. 信息网络安全, 2017, 17(8): 26-32. |
| [12] | YAN Xixi, YE Qing, LIU Yu. Attribute-based Encryption Scheme Supporting Privacy Preserving and User Revocation in the Cloud Environment [J]. 信息网络安全, 2017, 17(6): 14-21. |
| [13] | WANG Shuo, CHENG Xiangguo, CHEN Yameng, WANG Yue. Research on Key-insulated Group Signature Scheme [J]. 信息网络安全, 2017, 17(4): 40-45. |
| [14] | YOU Weiqing, CHEN Xiaoming, QI Jian. Research on a Kind of Anti-quantum Computing Public Key Cryptosystem [J]. 信息网络安全, 2017, 17(4): 53-60. |
| [15] | MEN Hong, YAO Shunli. Research on a Framework Based on Virtual Cloud Network for Monitoring Safe Production [J]. 信息网络安全, 2017, 17(3): 14-20. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||