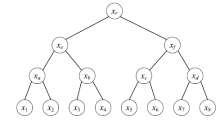
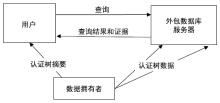
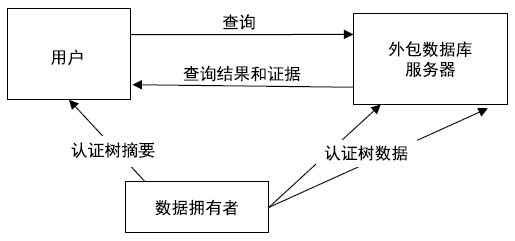
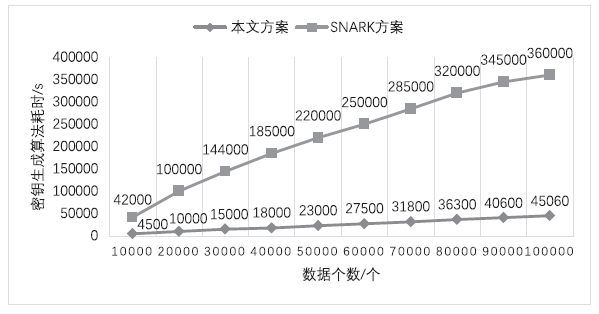
Netinfo Security ›› 2020, Vol. 20 ›› Issue (2): 91-97.doi: 10.3969/j.issn.1671-1122.2020.02.012
• 理论研究 • Previous Articles Next Articles
Outsourcing Database Join Query Verification Scheme Based on Authentication Tree
HOU Lin, FENG Da( ), XUAN Pengkai, ZHOU Fucai
), XUAN Pengkai, ZHOU Fucai
- Software College of Northeastern University, Shenyang 110169, China
-
Received:2019-10-23Online:2020-02-10Published:2020-05-11
CLC Number:
Cite this article
HOU Lin, FENG Da, XUAN Pengkai, ZHOU Fucai. Outsourcing Database Join Query Verification Scheme Based on Authentication Tree[J]. Netinfo Security, 2020, 20(2): 91-97.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.02.012
| [1] | XIAN Hequn, FENG Dengguo.An Integrity Checking Scheme in Outsourced Database Model[J]. Journal of Computer Research and Development, 2010, 47(6): 1107-1115. |
| 咸鹤群,冯登国.外包数据库模型中的完整性检测方案[J]. 计算机研究与发展, 2010, 47(6):1107-1115. | |
| [2] | GUPTA R.Above the Clouds: A View of Cloud Computing[J]. Eecs Department University of California Berkeley, 2012, 53(4): 50-58. |
| [3] | RIVEST R L, SHAMIR A, ADLEMAN L.A Method for Obtaining Digital Signatures and Public-key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126. |
| [4] | LI Feifei, HADJIELEFTHERIOU M, KOLLIOS G, et al.Dynamic Authenticated Index Structures for Outsourced Databases[C]//ACM. International Conference on Management of Data and Symposium on Principles Database and Systems, June 27-29, 2006, Chicago, IL, USA. New York: ACM, 2006: 121-132. |
| [5] | YANG Yin, PAPADOPOULOS S, PAPADIAS D, et al.Authenticated Indexing for Outsourced Spatial Databases[J]. The VLDB Journal, 2009, 18(3): 631-648. |
| [6] | YIU M L, LO E, YUNG D.Authentication of Moving kNN Queries[C]// IEEE. IEEE 27th International Conference on Data Engineering, April 11-16, 2011, Hannover, Germany. NJ: IEEE, 2011: 565-576. |
| [7] | LI Feifei, HADJIELEFTHERIOU M, KOLLIOS G, et al.Authenticated Index Structures for Aggregation Queries[J]. ACM Transactions on Information & System Security, 2010, 13(4): 1-35. |
| [8] | HU Haibo, XU Jianliang, CHEN Qian, et al.Authenticating Location-based Services without Compromising Location Privacy[C]//ACM. International Conference on Management of Data, May 20-25, 2012, Scottsdale Arizona, USA. New York: ACM, 2012: 301-312. |
| [9] | CHEN Qian, HU Haibo, XU Jianliang.Authenticating Top-k Queries in Location-based Services with Confidentiality[J]. Proceedings of the Vldb Endowment, 2014, 7(1): 49-60. |
| [10] | PAPADOPOULOS S, WANG Lixing, YANG Yin, et al.Authenticated Multistep Nearest Neighbor Search[J]. IEEE Transactions on Knowledge & Data Engineering, 2011, 23(5): 641-654. |
| [11] | HUANG Qingyuan, WANG Yongjun, SU Jinshu.A Bilinear Pairing-based Key Agreement Protocol in MANET[J]. Computer Science, 2008, 35(2): 78-80. |
| 黄清元,王勇军,苏金树.一种基于双线性配对的移动自组网密钥协商协议[J]. 计算机科学, 2008, 35(2):78-80. | |
| [12] | CHEN Anlin, PAN Jin, GUO Chao.Research on Authenticated Key Agreement Protocol in Cross-domain Two-party for Mobile Ad Hoc Network[J]. Application Research of Computers, 2011, 28(7): 2734-2737. |
| 陈安林,潘进,郭超.移动自组网中跨域两方认证密钥协商协议研究[J]. 计算机应用研究, 2011, 28(7):2734-2737. | |
| [13] | AU M H, TSANG P P, SUSILO W, et al.Dynamic Universal Accumulators for DDH Groups and Their Application to Attribute-based Anonymous Credential Systems[M]// Springer. Topics in Cryptology - CT-RSA 2009. Heidelberg: Springer-Verlag, 2009: 295-308. |
| [14] | NGUYEN L.Accumulators from Bilinear Pairings and Applications[M]// Springer. Topics in Cryptology - CT-RSA 2005. Heidelberg: Springer Berlin, 2005: 275-292. |
| [15] | BITANSKY N, CANETTI R, CHIESA A, et al. Recursive Composition and Bootstrapping for SNARKs and Proof-carrying Data[EB/OL]. , 2019-9-20. |
| [1] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [2] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [3] | XIA Tianyu, GU Yijun. A Dynamic Link Prediction Method Based on Improved Dynamic Triad Model [J]. Netinfo Security, 2020, 20(9): 97-101. |
| [4] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [5] | LI Shibin, LI Jing, TANG Gang, LI Yi. Method of Network Security States Prediction and Risk Assessment for Industrial Control System Based on HMM [J]. Netinfo Security, 2020, 20(9): 57-61. |
| [6] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [7] | WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net [J]. Netinfo Security, 2020, 20(9): 27-31. |
| [8] | TONG Xin, WANG Luona, WANG Runzheng, WANG Jingya. A Generation Method of Word-level Adversarial Samples for Chinese Text Classification [J]. Netinfo Security, 2020, 20(9): 12-16. |
| [9] | WU Jing, LU Tianliang, DU Yanhui. Generation of Malicious Domain Training Data Based on Improved Char-RNN Model [J]. Netinfo Security, 2020, 20(9): 6-11. |
| [10] | YU Xiaojun, WU Yabiao, ZHANG Yuqing. Research on the Design of Cloud Security Architecture [J]. Netinfo Security, 2020, 20(9): 62-66. |
| [11] | LIU Wenmao, YOU Yang. Shifting Security Protection Mindset and Mechanisms for Novel 5G Infrastructures [J]. Netinfo Security, 2020, 20(9): 67-71. |
| [12] | BI Qinbo, ZHAO Chengdong. Research and Application of 5G Cybersecurity Threat Modeling Based on STRIDE-LM [J]. Netinfo Security, 2020, 20(9): 72-76. |
| [13] | YU Guo, WANG Chonghua, CHEN Xuehong, LI Jun. Industrial Internet Identifier Resolution Security from the Perspective of Authentication [J]. Netinfo Security, 2020, 20(9): 77-81. |
| [14] | LIU Hong, XIE Yongheng, WANG Guowei, JIANG Shuai. Ontology-based Cross-domain Security Analysis [J]. Netinfo Security, 2020, 20(9): 82-86. |
| [15] | WANG Wenhua, HAO Xin, LIU Yan, WANG Yang. The Safety Evaluation and Defense Reinforcement of the AI System [J]. Netinfo Security, 2020, 20(9): 87-91. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||