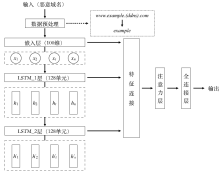
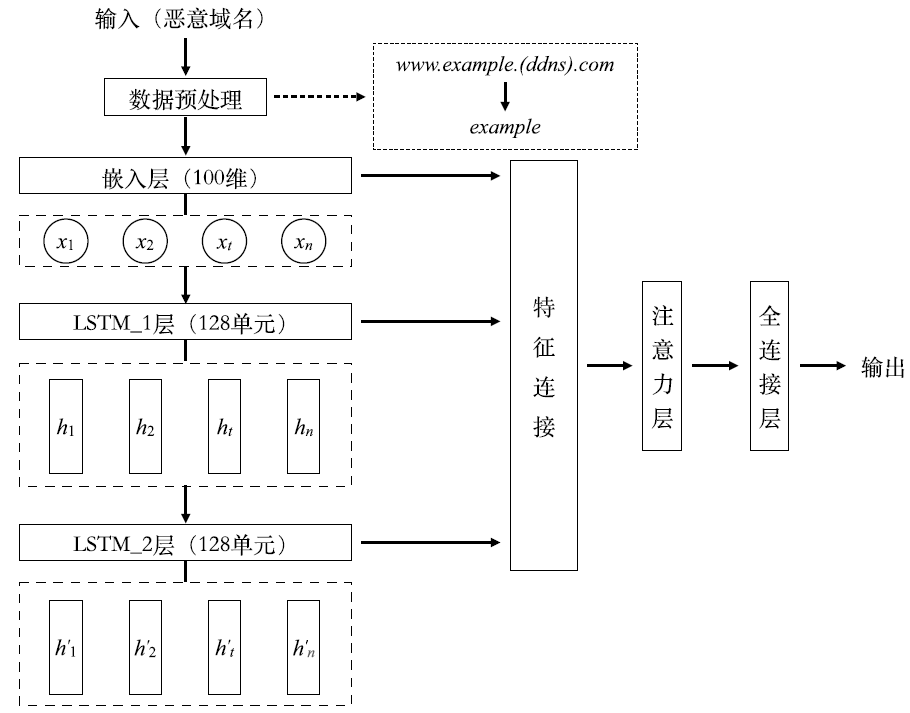
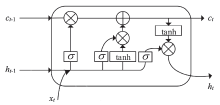
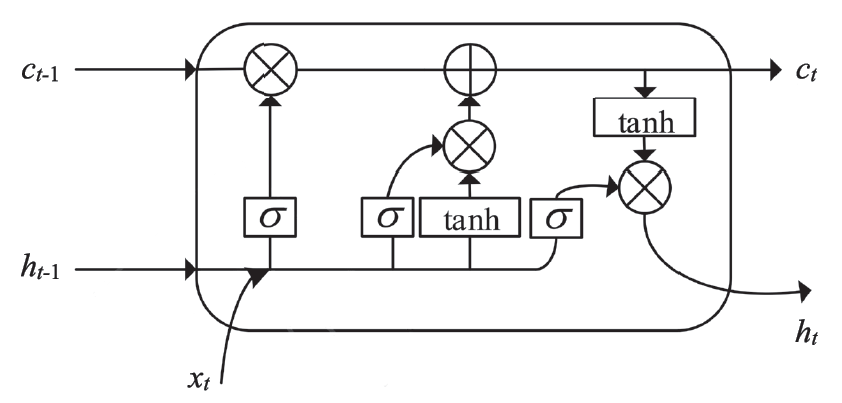
| [1] |
GOEBEL J, HOLZ T. Rishi: Identify Bot Contaminated Hosts by IRC Nickname Evaluation[J]. HotBots, 2007,7(8):192.
|
| [2] |
JIANG Jian, ZHUGE Jianwei, DUAN Haixin, et al. Research on Botnet Mechanisms and Defenses[J]. Jonrnal of Software, 2012,23(1):82-96.
|
|
江健, 诸葛建伟, 段海新, 等. 僵尸网络机理与防御技术[J]. 软件学报, 2012,23(1):82-96.
|
| [3] |
MOHAISEN A, ALRAWI O, MOHAISEN M. Amal: High-fidelity, Behavior-based Automated Malware Analysis and Classification[J]. Computers &Security, 2015,15(52):251-266.
|
| [4] |
WANG Yuanyuan, WU Chunjiang, LIU Qihe, et al. Overview of Malicious Domainname Detection and Application[J]. Computer Applications and Software, 2019,36(9):310-316.
|
|
王媛媛, 吴春江, 刘启和, 等. 恶意域名检测研究与应用综述[J]. 计算机应用与软件, 2019,36(9):310-316.
|
| [5] |
YU Bin, PAN Jie, HU Jiaming. Character Level based Detection of DGA Domain Names[C]// IEEE. 2018 International Joint Conference on Neural Networks (IJCNN), July 8-13, 2018, Rio de Janeiro, Brazil. New York: IEEE, 2018: 1-8.
|
| [6] |
YADAV S, REDDY A K, REDDY, et al. Detecting Algorithmically Generated Malicious Domain Names[C]// ACM. Proceedings of the 10th ACM SIGCOMM Conference on Internet Measurement, November 27-30, 2010, Melbourne, Australia. New York: ACM, 2010: 48-61.
|
| [7] |
BILGE L, KIRDA E, KRUEGEL C, et al. EXPOSURE: Finding Malicious Domains Using Passive DNS Analysis[C]// NDSS. Proceedings of the Network and Distributed System Security Symposium, February 6-9, 2011, San Diego, California, USA. New York: NDSS, 2011: 1-17.
|
| [8] |
ZANG Xiaodong, GONG Jian, HU Xiaoyan. Detecting Malicious Domain Names Based on AGD[J]. Journal on Communications, 2018,39(7):15-25.
|
|
臧小东, 龚俭, 胡晓艳. 基于AGD的恶意域名检测[J]. 通信学报, 2018,39(7):15-25.
|
| [9] |
ZHAO Kejun, GE Liansheng, QIN Fenglin, et al. Deep Model for DGA Botnet Detection Based on Word-hashing[J]. Journal of Southeast University(Natural Science Edition), 2017,47(S1):30-33.
|
|
赵科军, 葛连升, 秦丰林, 等. 基于word-hashing的DGA僵尸网络深度检测模型[J]. 东南大学学报(自然科学版), 2017,47(S1):30-33.
|
| [10] |
WOODBRIDGE J, ANDERSON H S, AHUJA A, et al. Predicting Domain Generation Algorithms with Long Short-term Memory Networks[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=d3e2183530fbe98be88b18431f31dc19&site=xueshu_se, 2020-4-25.
|
| [11] |
YANG Luhui, LIU Guangjie, ZHAI Jiangtao, et al. Improved Algorithm for Detection of the Malicious Domain Name Based on the Convolutional Neural Network[J]. Journal of Xidian University, 2020,47(1):37-43.
|
|
杨路辉, 刘光杰, 翟江涛, 等. 一种改进的卷积神经网络恶意域名检测算法[J]. 西安电子科技大学学报, 2020,47(1):37-43.
|
| [12] |
ANDERSON H S, WOODBRIDGE J, FILAR B. Deep DGA: Adversarially-tuned Domain Generation and Detection[C]// ACM. Proceedings of the 2016 ACM Workshop on Artificial Intelligence and Security, October 27-30, 2016, Vienna ,Austria. New York: ACM, 2016: 13-21.
|
| [13] |
YUAN Chen. Research and Implementation of Malicious Domains' Detection Method Based on Adversarial Model[D]. Beijing: Beijing University of Civil Engineering and Architecture, 2018.
|
|
袁辰. 基于对抗模型的恶意域名检测方法的研究与实现[D]. 北京:北京建筑大学, 2018.
|
| [14] |
CHENG Hua, CAI Jing, FANG Yiquan. RL-Gen: A Character-Level Text Generation Framework with Reinforcement Learning in Domain Generation Algorithm Case[C]// Springer. International Conference on Neural Information Processing, December 12-15, 2019, Sydney, Australia. Berlin: Springer, 2019: 690-697.
|
| [15] |
WANG Qixin, LUO Tianyi, WANG Dong. Chinese Song Iambics Generation with Neural Attention-based Model[EB/OL]. Eprint arXiv: 1604. 06274, 2016-12-20.
|
| [16] |
KARPATHY A. The Unreasonable Effectiveness of Recurrent Neural Networks[EB/OL]. http://karpathy.github.io/2015/05/21/rnn-effectiveness, 2020-5-21.
|
| [17] |
GLUSHKOVA T, ARTEMOVA E. Char-RNN and Active Learning for Hashtag Segmentation[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1x3f0at0h42a0gp09m080pb0bn496380&site=xueshu_se, 2019-12-31.
|
| [18] |
HOCHREITER S, SCHMIDHUBER J. Long Short-term Memory[J]. Neural Computation, 1997,9(8):1735-1780.
doi: 10.1162/neco.1997.9.8.1735
URL
pmid: 9377276
|
| [19] |
CHO K, VAN Merriënboer B, GULCEHRE C, et al. Learning Phrase Representations Using RNN Encoder-decoder for Statistical Machine Translation[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=2ba31a0b87d74d25317da3521cca2915&site=xueshu_se&hitarticle=1, 2014-12-31.
|
| [20] |
RAFFEL C, ELLIS D P W. Feed-forward Networks with Attention can Solve some Long-term Memory Problems[EB/OL]. https://www.researchgate.net/publication/288890112_Feed-Forward_Networks_with_Attention_Can_Solve_Some_Long-Term_Memory_Problems, 2015-12-20.
|
 ), DU Yanhui
), DU Yanhui