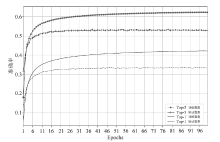
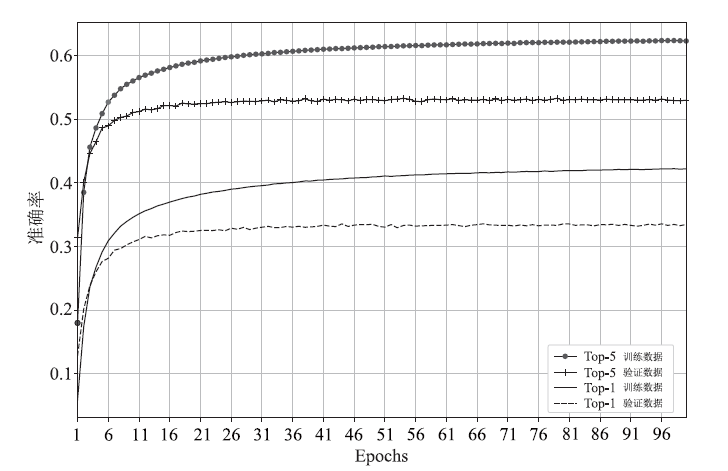
| [1] |
WANG Wenjie, HU Baiqing, LIU Chi.A Survey of Open Source Software for Big Data Governance and Security[J]. Netinfo Security, 2017, 17(5): 28-36.
|
|
王文杰,胡柏青,刘驰.开源大数据治理与安全软件综述[J].信息网络安全,2017,17(5):28-36.
|
| [2] |
LECUN Y, BENGIO Y, HINTON G. Deep Learning[EB/OL]. , 2015-5-28.
|
| [3] |
BENGIO Y, DUCHARME R, VINCENT P, et al. A Neural Probabilistic Language Model[EB/OL]. , 2019-2-11.
|
| [4] |
SZEGEDY C, VANHOUCKE V, IOFFE S, et al. Rethinking the Inception Architecture for Computer Vision[EB/OL]. , 2019-2-11.
|
| [5] |
HOCHREITER S, SCHMIDHUBER J.Long Short-term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
|
| [6] |
SRIVASTAVA N, HINTON G, KRIZHEVSKY A, et al.Dropout: A Simple Way to Prevent Neural Networks from Overfitting[J]. Journal of Machine Learning Research, 2014, 15(1): 1929-1958.
|
| [7] |
JONES K S.A Statistical Interpretation of Term Specificity and Its Application in Retrieval[J]. Journal of Documentation, 1972, 28(1): 11-21.
|
| [8] |
MIKOLOV T, CHEN Kai, CORRADO G, et al. Efficient Estimation of Word Representations in Vector Space[EB/OL]. , 2019-2-11.
|
| [9] |
Wikimedia Foundation. Wikimedia Chinese Corpus[EB/OL]. , 2019-2-11.
|