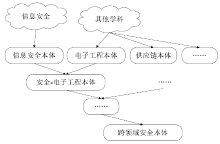
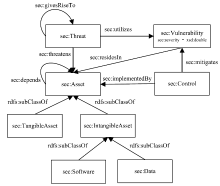
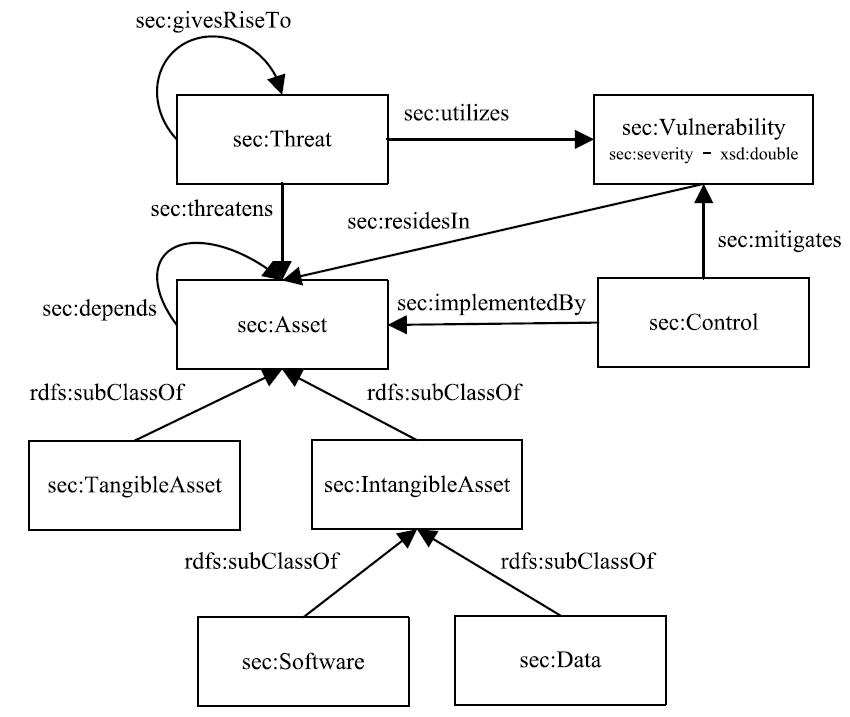
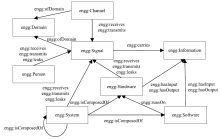
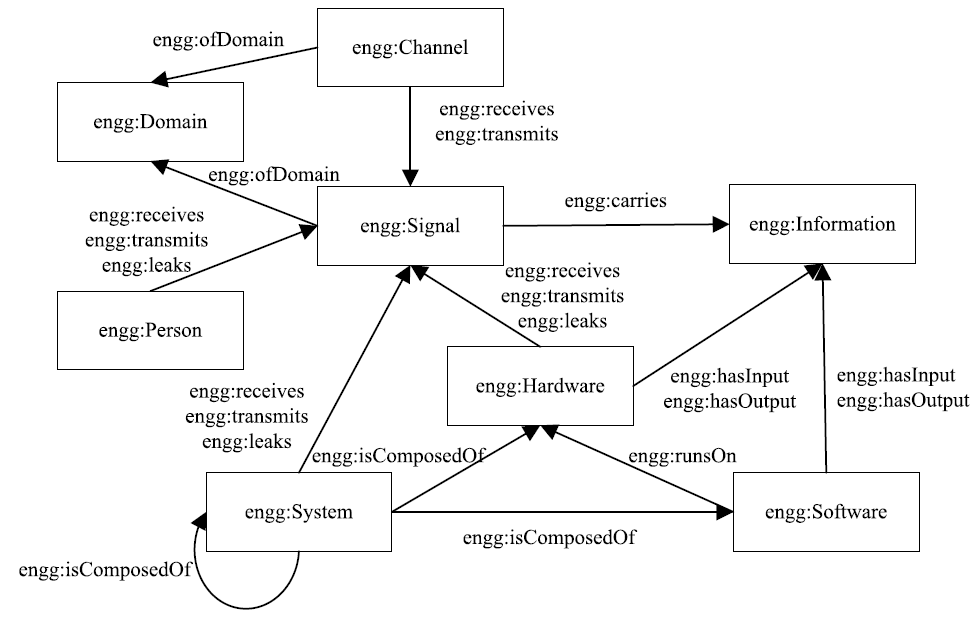
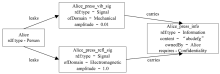
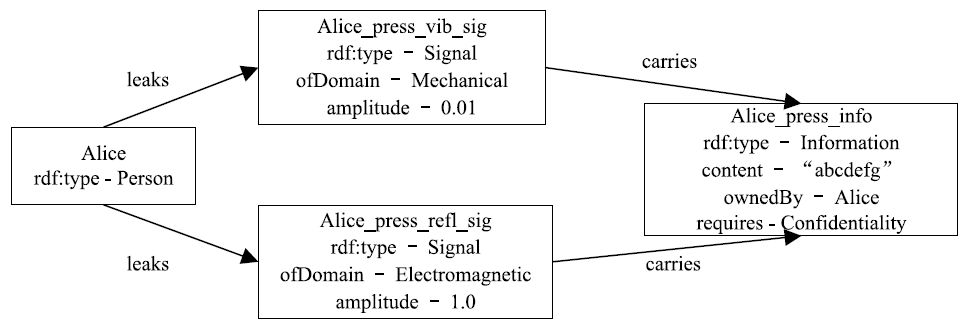
| [1] |
FENZ S, EKELHART A. Formalizing Information Security Knowledge[C]// ACM. 4th International Symposium on Information, Computer, and Communications Security, March 10, 2009, Sydney, NSW, Australia. New York: ACM, 2009: 183-194.
|
| [2] |
SYED Z, PADIA A, FININ T, et al. A Unified Cybersecurity Ontology[C]// AAAI. 13th AAAI Conference on Artificial Intelligence, February 12, 2016, Phoenix, Arizona, USA. Palo Alto: AAAI, 2016: 80-87.
|
| [3] |
MAVROEIDIS V, BROMANDER S. Cyber Threat Intelligence Model: An Evaluation of Taxonomies, Sharing Standards, and Ontologies within Cyber Threat Intelligence[C]// IEEE. European Intelligence and Security Informatics Conference(EISIC), September 11, 2017, Attica, Greece. New York: IEEE, 2017: 91-98.
|
| [4] |
MAI Chengcheng, ZHOU Jiakun, ZHU Han, et al. A Review on Security Ontology: Document Analysis from 2010 to 2016[J]. Journal of Information Security Research, 2017,3(2):151-159.
|
| [5] |
The CyBOK Project Team. The Cyber Security Body of Knowledge: Hardware Security Knowledge Tree version 1.0[EB/OL]. https://www.cybok.org/, 2020-6-11.
|
| [6] |
BORST P, AKKERMANS H. Engineering Ontologies[J]. International Journal of Human-Computer Studies, 1997,46(2-3):365-406.
doi: 10.1006/ijhc.1996.0096
URL
|
| [7] |
HWAITAT A A, SHAHEEN A, ADHIM K, ARKEBAT E N, et al. Computer Hardware Components Ontology[J]. Modern Applied Science, 2018,12(3):35-40.
|
| [8] |
HACHEM S, TEIXEIRA T, ISSARNY V. Ontologies for the Internet of Things[C]// Springer. 12th International Middleware Conference, December 12, 2011, Lisbon, Portugal. Heidelberg: Springer, 2011: 1-6.
|
| [9] |
BOUTEKKOUK F. Towards an Ontology-driven Intellectual Properties Reuse for Systems on Chip Design[C]// INASE. International Conference on Systems, Control, Signal Processing and Informatics, July 16, 2013, Rhodes Island, Greece. London: INASE, 2013: 394-399.
|
| [10] |
NOY N F, MUSEN M A. Algorithm and Tool for Automated Ontology Merging and Alignment[C]// AAAI. 17th National Conference on Artificial Intelligence(AAAI-00), July 30, 2000, Austin, Texas, USA. Palo Alto: AAAI, 2000: 450-455.
|
| [11] |
MARQUARDT P, VERMA A, CARTER H, et al. (sp)iPhone: Decoding Vibrations from Nearby Keyboards using Mobile Phone Accelerometers[C]// ACM. 18th ACM Conference on Computer and Communications Security, October 17, 2011, Chicago, Illnois, USA. New York: ACM, 2011: 551-562.
|
| [12] |
SHUMAILOV I, SIMON L, YAN J, et al. Hearing Your Touch: A New Acoustic Side Channel on Smartphones[EB/OL]. https://arxiv.org/pdf/1903.11137, 2020-6-11.
|
 ), XIE Yongheng1, WANG Guowei3, JIANG Shuai3
), XIE Yongheng1, WANG Guowei3, JIANG Shuai3