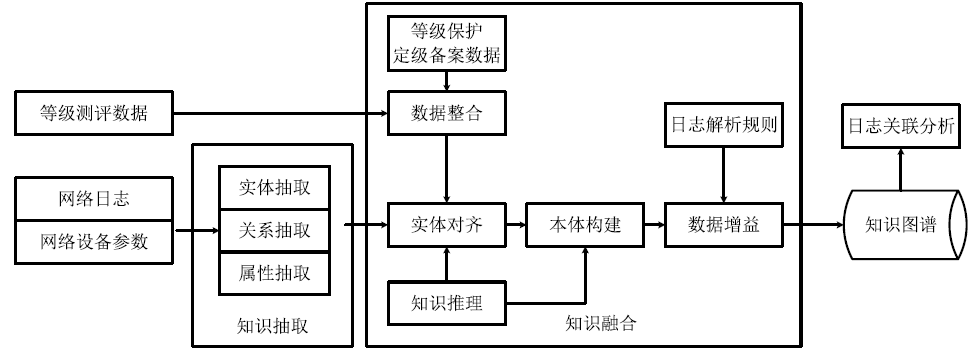
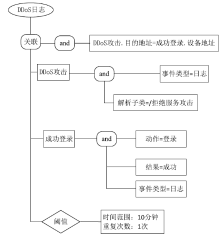
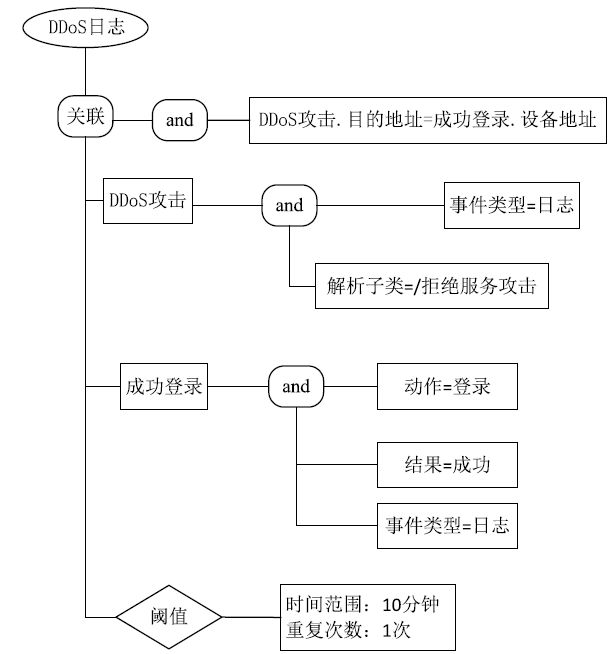
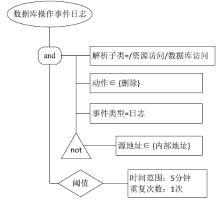
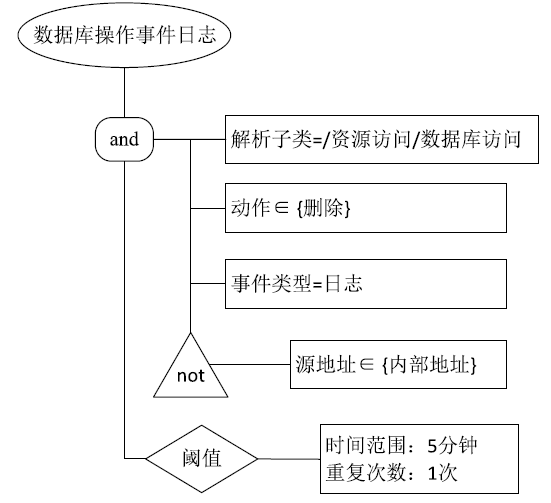
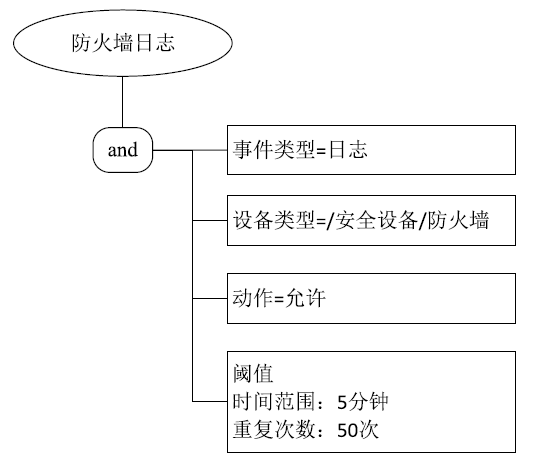
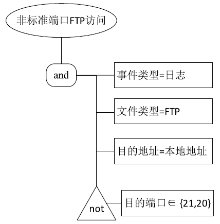
| [1] |
LIAO Xiangke, LI Shanshan, DONG Wei, et al.Survey on Log Research of Large-Scale Software System[J]. Journal of Software, 2016, 27(8): 1934-1947.
|
|
廖湘科,李姗姗,董威,等.大规模软件系统日志研究综述[J].软件学报,2016,27(8):1934-1947.
|
| [2] |
TAOYuan, ZHANG Yuxiang, MA Siyuan, et al.Combining the Big Data Analysis and the Threat Intelligence Technologies for the Classified Protection Model[J]. Cluster Computing, 2017, 20(2):1035-1046.
|
| [3] |
CHEN Xingshu, ZENG Xuemei, WANG Wenxian, et al.Big Data Analytics for Network Security and Intelligence[J]. Journal of Sichuan University(Engineering Science Edition), 2017, 49(3): 1-12.
|
|
陈兴蜀,曾雪梅,王文贤.基于大数据的网络安全与情报分析[J].工程科学与技术,2017,49(3):1-12.
|
| [4] |
CHEN Shimin.Big Data Analysis and Data Velocity[J]. Journal of Computer Research and Development, 2015, 52(2): 333-342.
|
|
陈世敏. 大数据分析与高速数据更新[J].计算机研究与发展,2015,52(2):333-342.
|
| [5] |
WANG Tao, ZHANG Wenbo, XU Jiwei,et al.A Survey of Fault Detection for Distributed Software Systems with Statistical Monitoring in Cloud Computing[J]. Chinese Journal of Computers, 2017, 40(2): 397-413.
|
|
王焘,张文博,徐继伟,等.云环境下基于统计监测的分布式软件系统故障检测技术研究[J].计算机学报,2017,40(2):397-413.
|
| [6] |
LIU Qiao, LI Yang, Duan Hong, et al.Knowledge Graph Construction Techniques[J]. Journal of Computer Research and Development, 2016, 53(3): 582-600.
|
|
刘峤,李杨,段宏,等.知识图谱构建技术综述[J].计算机研究与发展,2016,53(3):582-600.
|
| [7] |
JIA Yan, QI Yulu, SHANG Huaijun, et al.A Practical Approach to Constructing a Knowledge Graph for Cybersecurity[J]. Engineering, 2018, 4(1): 53-60.
|
|
贾焰,亓玉璐,尚怀军,等.一种构建网络安全知识图谱的实用方法[J].工程(英文),2018,4(1):53-60.
|
| [8] |
LIU Yadong, HU Dewen.High Performance Computing in the Viewpoint of Brain Research[J]. Chinese Journal of Computers, 2017, 40(9): 2148-2166.
|
|
刘亚东,胡德文.脑科学视角下的高性能计算[J].计算机学报,2017,40(9):2148-2166.
|
| [9] |
TAO Yuan, GUO Fengming, LUO Zheng, et al.GA/T 1349-2017 Information Security Technology Knowledge Library Interface Specification for Cybersecurity Classified Protection[S]. Beijing: Standards Press of China, 2017.
|
|
陶源,郭俸明,罗峥,等. GA/T 1349-2017 信息安全技术网络安全等级保护专用知识库接口规范[S].北京:中国标准出版社,2017.
|
| [10] |
MA li, CHEN Gongyong, ZHANG Zhenfeng, et al. GB/T 22239-2019 Information Security Technology Baseline for Classified Protection of Cybersecurity[S]. Beijing: Standards Press of China, 2019.
|
|
马力,陈广勇,张振峰,等. GB/T 22239-2019 信息安全技术网络安全等级保护基本要求[S].北京:中国标准出版社,2019.
|
| [11] |
ZHANG Lei, CUI Yong, LIU Jing, et al.Application of Machine Learning in Cyberspace Security Research[J]. Chinese Journal of Computers, 2018, 41(9): 1943-1975.
|
|
张蕾,崔勇,刘静,等.机器学习在网络空间安全研究中的应用[J].计算机学报,2018,41(9):1943-1975.
|
| [12] |
OLGA R, JIA Deng, HAO Su, et al.ImageNet Large Scale Visual Recognition Challenge[J]. International Journal of Computer Vision, 2015, 115(3): 1-42.
|
| [13] |
JÜRGEN S. Deep Learning in Neural Networks: An Overview[J]. Neural Networks, 2015, 61(1): 85-117.
|
| [14] |
HAO Yao, CHEN Zhouguo, PU Shi, et al.Exploration on Attribution of Multi-Source Network Attack[J]. Communications Technology, 2013, 46(12): 77-81.
|
|
郝尧,陈周国,蒲石,等.多源网络攻击追踪溯源技术研究[J].通信技术,2013,46(12):77-81.
|