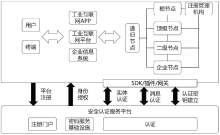
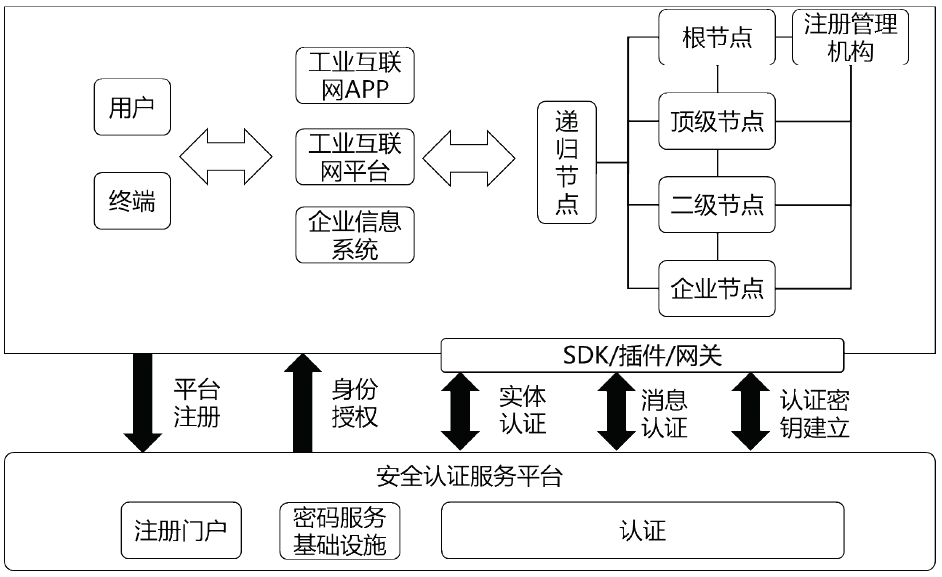
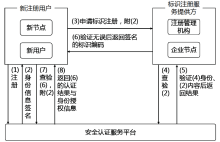
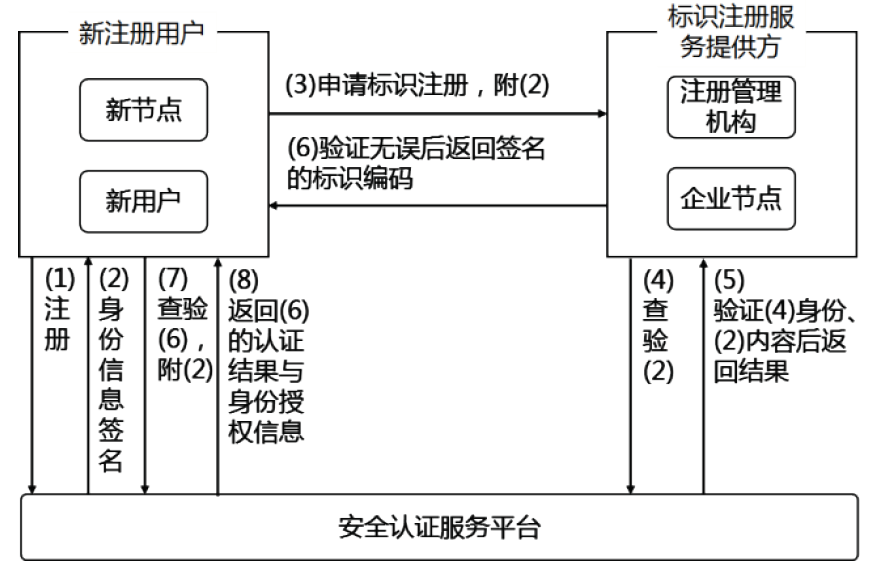
| [1] |
LIAO Kai. Deepen the Integration of the Internet, Big Data, Artificial Intelligence and the Real Economy, and Enhance the Ability to Ensure Industrial Information Security[J]. Security & Informatization, 2018,18(12):4-6.
|
|
廖凯. 深化互联网、大数据、人工智能与实体经济融合提升工业信息安全保障能力[J]. 网络安全和信息化, 2018,18(12):4-6.
|
| [2] |
WANG Chonghua, HE Xiaolong, CHEN Xuehong. Industrial Internet Identifier Resolution Security Capability Needs to be Improved Right Now[J]. China Information Security, 2019,19(6):53-55.
|
|
王冲华, 何小龙, 陈雪鸿. 工业互联网标识解析安全保障能力亟需提高[J]. 中国信息安全, 2019,19(6):53-55.
|
| [3] |
MA Yuanyuan, LIU Zhoubin, WANG Zixiang. Research on Heterogeneous Terminal Security Access Technology in Edge Computing Scenario[J]. Computer Engineering and Applications, 2020,56(17):115-120.
|
|
马媛媛, 刘周斌, 汪自翔. 边缘计算场景下的异构终端安全接入技术研究[J]. 计算机工程与应用, 2020,56(17):115-120.
|
| [4] |
MAO W B. Modern Cryptography: Theory and Practice[M]. WANG Jilin, WU Qianhong, Translate. Beijing: Publishing House of Electronics Industry, 2004.
|
|
MAO W B. 现代密码学理论与实践[M]. 王继林, 伍前红,译.北京:电子工业出版社, 2004.
|
| [5] |
YANG Bin, CHEN Guoqing, SUN Yonghong. Research of a New Identity-based Authentication Model for Multi-domain[J]. Computer Security, 2010,10(8):15-18.
|
|
杨斌, 陈国庆, 孙永红. 一种新的基于身份的多信任域认证模型研究[J]. 计算机安全, 2010,10(8):15-18.
|
| [6] |
ZHANG Meng, YIN Qiqi. Research Progress of Cryptography Algorithms Used in Identity Authentication Technology[J]. Cyberspace Security, 2018,9(6):56-58.
|
|
张猛, 尹其其. 身份认证技术中应用的密码算法研究进展[J]. 网络空间安全, 2018,9(6):56-58.
|
| [7] |
CHENG Zhaohui. Certificateless Public Key Encryption Based on SM2[EB/OL]. http://kns.cnki.net/kcms/detail/10.1195.TN.20200904.1536.008.html, 2020-6-8.
|
|
程朝辉. 基于SM2的无证书加密算法[EB/OL]. http://kns.cnki.net/kcms/detail/10.1195.TN.20200904.1536.008.html,2020-6-8.
|
 )
)