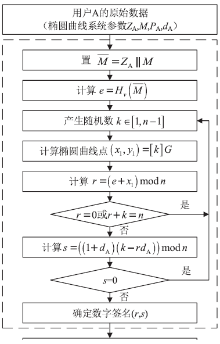
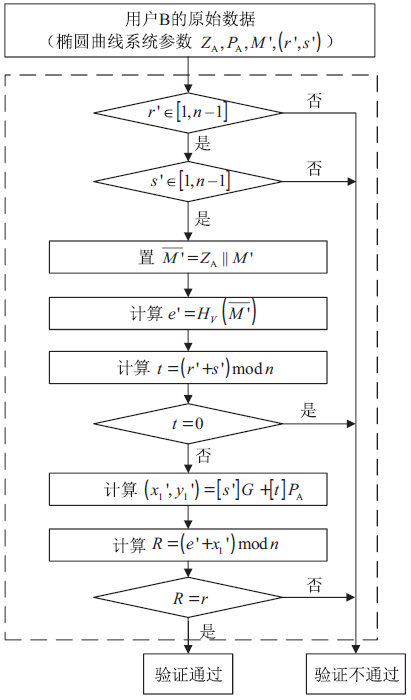
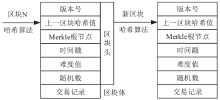
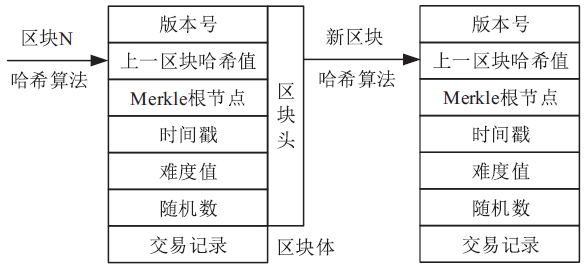
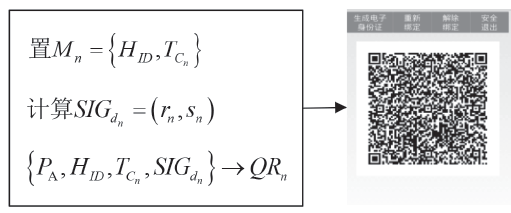
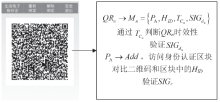
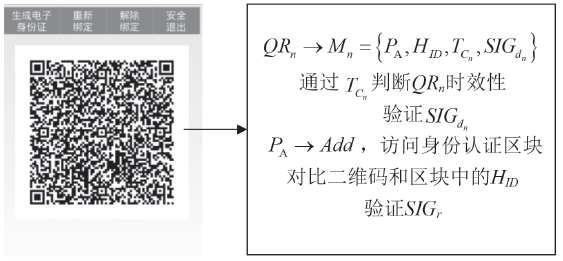
| [1] |
SHANG Ming, MA Yuan, LIN Jingqiang, et al.A Threshold Scheme for SM2 Elliptic Curve Cryptographic Algorithm[J]. Journal of Cryptologic Research, 2014, 1(2): 155-166.
|
|
尚铭,马原,林璟锵,等. SM2椭圆曲线门限密码算法[J]. 密码学报,2014,1(2):155-166.
|
| [2] |
REN Zirong.A Third-party Authentication Service System Based on Mobile Terminal and PKI[D]. Shanghai: Shanghai Jiaotong University, 2014.
|
|
任子荣. 基于移动终端和PKI技术的第三方身份认证服务系统[D]. 上海:上海交通大学,2014.
|
| [3] |
GU Guojin.Study and Implement of Authentication and Authorization System Based on SM2 Algorithm[D]. Jinan: Shandong University, 2013.
|
|
谷国进. 基于SM2算法的认证授权系统研究与实现[D]. 济南:山东大学,2013.
|
| [4] |
WANG Jie.Design and Implementation of Certificate Status Query System Based on SM2[D]. Xi’an: Xidian University, 2015.
|
|
王杰. 基于商密SM2算法的证书状态查询机制设计与实现[D]. 西安:西安电子科技大学,2015.
|
| [5] |
LI Zhaobin, LIU Dandan, HUANG Xin, et al.Design and Implementation of Secure Access Device Based on Guomi Algorithm[J]. Netinfo Security, 2016, 16(11): 19-27.
|
|
李兆斌,刘丹丹,黄鑫,等. 基于国密算法的安全接入设备设计与实现[J]. 信息网络安全,2016,16(11):19-27.
|
| [6] |
LI Zichen, LIU Boya, WANG Peidong, et al.Two-way Authentication Protocol Based on SM2 and Zero Knowledge for Radio Frequency Identification[J]. Computer Engineering, 2017, 43(6): 97-100.
|
|
李子臣,刘博雅,王培东,等. 基于SM2与零知识的射频识别双向认证协议[J]. 计算机工程,2017,43(6):97-100.
|
| [7] |
YAN Junzhi, PENG Jin, ZUO Min, et al.Blockchain Based PKI Certificate System[J]. Telecommunications Engineering Technology and Standardization, 2017, 30(11): 16-20.
|
|
阎军智,彭晋,左敏,等. 基于区块链的PKI数字证书系统[J]. 电信工程技术与标准化,2017,30(11):16-20.
|
| [8] |
HUANG Xiaofang, XU Lei, YANG Xi.A Blockchain Model of Cloud Forensics[J].Journal of Beijing University of Posts and Telecommunications, 2017(5): 1-4.
|
|
黄晓芳,徐蕾,杨茜. 一种区块链的云计算电子取证模型[J]. 北京邮电大学学报,2017(5):1-4.
|
| [9] |
MIN Xurong, DU Kui, DAI Yicong.Electronic Certification Sharing Platform Based on Blockchain Technology[J]. Command Information System and Technology, 2017, 8(2): 47-51.
|
|
闵旭蓉,杜葵,戴逸聪. 基于区块链技术的电子证照共享平台设计[J]. 指挥信息系统与技术,2017,8(2):47-51.
|
| [10] |
XUE Tengfei, FU Qunchao, WANG Cong, et al.A Medical Data Sharing Model via Blockchain[J]. Acta Automatica Sinica, 2017, 43(9): 1555-1562.
|
|
薛腾飞,傳群超,王枞,等. 基于区块链的医疗数据共享模型研究[J]. 自动化学报,2017,43(9):1555-1562.
|
| [11] |
WANG Jun, WU Peng, WANG Xiangyu, et al.The Outlook of Blockchain Technology for Construction Engineering Management[J]. Frontiers of Engineering Management, 2017, 4(1): 67-75.
|
| [12] |
CNNIC. 41st A Statistical Report on the Development of the Internet in China[EB/OL]. . 2018-1-31.
|
|
CNNIC. 第41次《中国互联网络发展状况统计报告》[EB/OL]. . 2018-1-31.
|
| [13] |
LIU Yonglei, JIN Zhigang, GAO Tianying.Survey of Security Research in Mobile Payment System[J]. Netinfo Security, 2017, 17(2): 1-5.
|
|
刘永磊,金志刚,高天迎. 移动支付系统安全性研究综述[J]. 信息网络安全,2017,17(2):1-5.
|
| [14] |
SHEN Yanzhao.Cryptanalysis of SM3 Cryptographic Hash Algorithm[D]. Shanghai: Donghua University, 2013.
|
|
申延召. SM3密码哈希算法分析[D]. 上海:东华大学,2013.
|
| [15] |
ZHAO Kuo, XING Yongheng.Security Survey of Internet of Things Driven by Blockchain Technology[J]. Netinfo Security, 2017, 17(5): 1-6.
|
|
赵阔,邢永恒. 区块链技术驱动下的物联网安全研究综述[J]. 信息网络安全,2017,17(5):1-6.
|
| [16] |
CAI Weide, YU Lian, WANG Rong, et al.Blockchain Application Development Techniques[J]. Journal of Software, 2017, 28(6): 1474-1487.
|
|
蔡维德,郁莲,王荣,等. 基于区块链的应用系统开发方法研究[J]. 软件学报,2017,28(6):1474-1487.
|
| [17] |
NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. , 2017-12-11.
|
| [18] |
QING Sude, JIANG Ying, WANG Qiuye.Technology Principle and Significance of Blockchain[J].Telecommunications Network Technology, 2016(12): 14-20.
|
|
卿苏德,姜莹,王秋野. 区块链的技术原理和意义[J]. 电信网技术,2016(12):14-20.
|
| [19] |
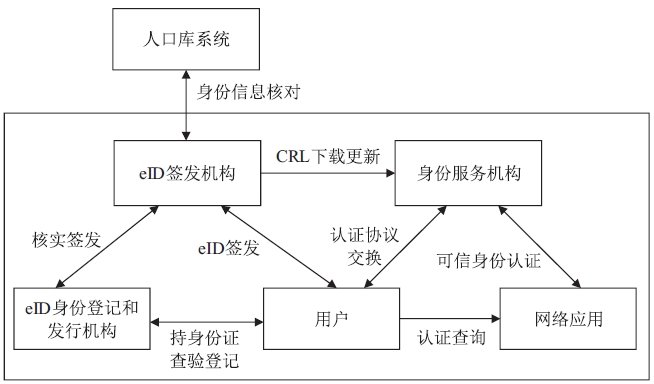
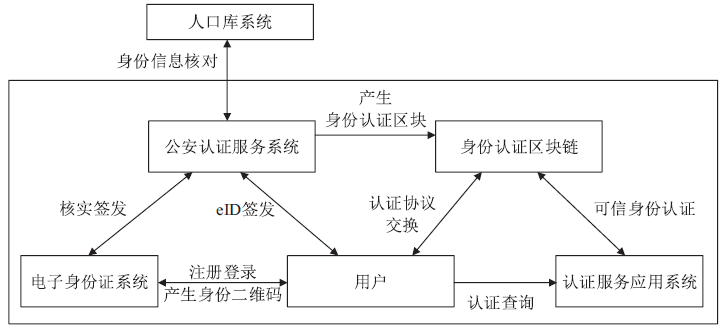
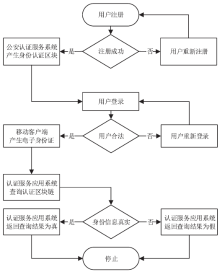
WANG Zhipeng, YANG Minghui, LV Liang.Research on Trusted Identity Architecture in Cyberspace Based on eID[J]. Netinfo Security, 2015, 15(9): 97-100.
|
|
汪志鹏,杨明慧,吕良. 基于eID的网络可信身份体系建设研究[J]. 信息网络安全,2015,15(9):97-100.
|
 ), Shengli LIU2, Wei FU1
), Shengli LIU2, Wei FU1