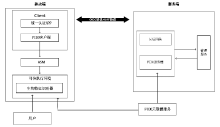
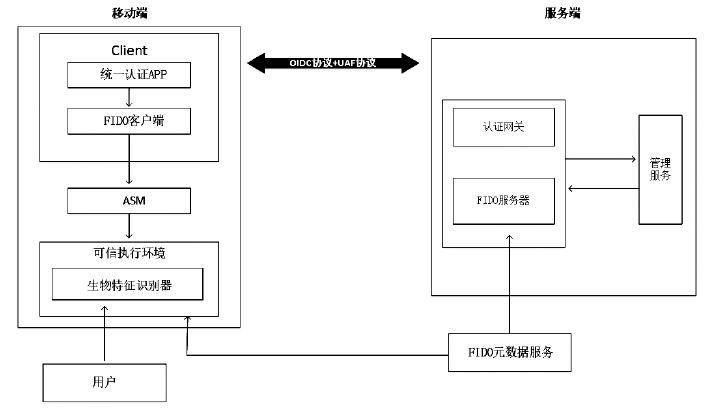
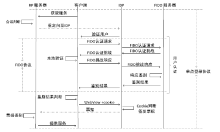
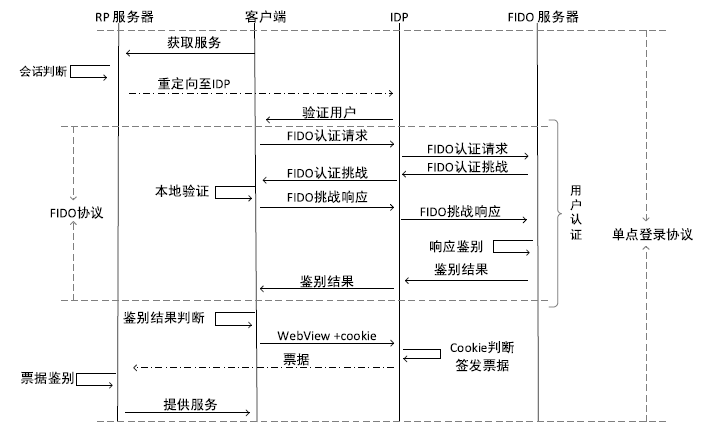
| [1] |
ADAMS A, SASSE M A.Users are not the Enemy[J]. Communications of the ACM, 1999, 42(12): 41-46.
|
| [2] |
ION I, REEDER R, CONSOLVO S.“.. no one can hack my mind”: Comparing Expert and Non-Expert Security Practices[C]//ACM. Eleventh Symposium on Usable Privacy and Security, July 22-24, 2015, Carleton University, Ottawa, Canada. New York: ACM, 2015: 327-346.
|
| [3] |
PEARMAN S, THOMAS J, NAEINI P E, et al.Let’s Go in for a Closer Look: Observing Passwords in Their Natural Habitat[C]//ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, October 30-November 3, 2017, Dallas, USA. New York: ACM, 2017: 295-310.
|
| [4] |
ZENG J, DUAN J, WU C.Empirical Study on Lexical Sentiment in Passwords from Chinese Websites[J]. Computers & Security, 2019, 80(1): 200-210.
|
| [5] |
MELICHER W, KURILOVA D, SEGRETI S M, et al.Usability and Security of Text Passwords on Mobile Devices[C]//ACM. Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems, May 07-12, San Jose, CA, USA. New York: ACM, 2016: 527-539.
|
| [6] |
WASH R, RADER E, BERMAN R, et al.Understanding Password Choices: How Frequently Entered Passwords are Re-used Across Websites[C]//ACM. Twelfth Symposium on Usable Privacy and Security, June 22-24, 2016, Santa Clara, CA. New York: ACM, 2016: 175-188.
|
| [7] |
LOCKHART H, CAMPBELL B.Security Assertion Markup Language(saml) v2.0 Technical Overview[J]. OASIS Committee Draft, 2008, 12(9): 94-106.
|
| [8] |
SAKIMURA N, NRI J. Bradley, PING Identity, et al. OpenID Connect Core 1.0 Incorporating Errata Set 1[EB/OL]. , 2014-11-8.
|
| [9] |
IMAI I, SHIN S H, KOBARA K.Authenticated Key Exchange for Wireless Security[C]// IEEE. IEEE Wireless Communications and Networking Conference, 2005, March 13-17, 2005, New Orleans, LA, USA. New York: IEEE, 2005: 1180-1186.
|
| [10] |
WANG Y, LUO W, SHEN C.Analysis on Imai-Shin’s LR-AKE Protocol for Wireless Network Security[C]//Springer. International Business Conference on Communications and Networking in China, August 28 2008, Hangzhou, China. Berlin: Springer, 2008: 84-89.
|
| [11] |
HALLER N, METZ C, NESSER P, et al. A One-Time Password System[EB/OL]. , 2018-7-15.
|
| [12] |
BURIRO A.Behavioral Biometrics for Smartphone User Authentication[D]. Trento: University of Trento, 2017.
|
| [13] |
Android. Google: Ice Cream Sandwich[EB/OL]. , 2011-11-15.
|
| [14] |
JAIN A K, ROSS A, PANKANTI S.Biometrics: A Tool for Information Security[J]. IEEE Transactions on Information Forensics and Security, 2006, 1(2): 125-143.
|
| [15] |
DE L A, HANG A, VON Z E, et al.I Feel Like I’m Taking Selfies All Day!: Towards Understanding Biometric Authentication on Smartphones[C]//ACM. Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing Systems, April 18-23, 2015, Seoul, Republic of Korea, New York: ACM, 2015: 1411-1414.
|
| [16] |
FIDO Alliance. What is FIDO?[EB/OL]. , 2017-2-13.
|