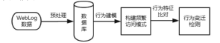
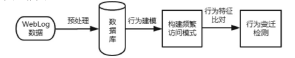
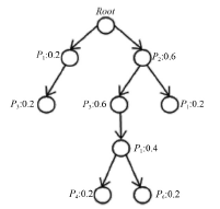
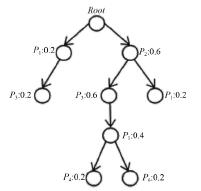
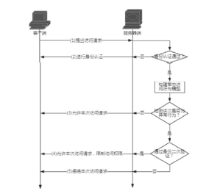
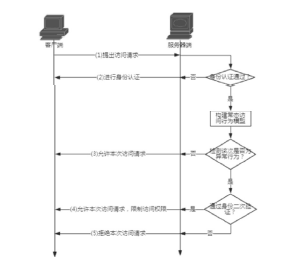
| [1] |
YAO H, HU H, HUANG B, et al.Dynamic Role and Context-based Access Control for Grid Applications[C]// IEEE. 6th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT 2005), December 5-8, 2005, Dalian, China. USA: IEEE, 2005:404-406.
|
| [2] |
ZHANG Yixuan, HE Jingsha, ZHAO Bin, et al.Towards More Pro-active Access Control Computer Systems and Networks[J]. Compuer Science, Information Systems, SCI Computer Science, 2015, 3(49):132-146.
|
| [3] |
XING L, LIU L.A Reputation-based Trust Model for Peer-to-peer Ecommerce Communities[C]//IEEE. IEEE International Conference on E-Commerce (CEC 2003), June 24-27, 2003, NEWPORT BEACH, CA. USA:IEEE, 2003:275-284.
|
| [4] |
李凤华,王巍,马建峰,等. 基于行为的访问控制模型及其行为管理[J]. 电子学报,2008(10):1881-1890.
|
| [5] |
牟琦,龚尚福. 基于用户行为模型的身份验证算法研究[J].西安科技大学学报,2006(3):376-378, 387.
|
| [6] |
FRIAS-MARTINEZ V, SHERRICK J, STOLFO S J, et al . A Network Access Control Mechanism Based on Behavior Profiles[C]// IEEE. 25th Annual Computer Security Applications Conference, December 7-11, 2009, Honolulu, HI. HI:IEEE, 2009:3-12.
|
| [7] |
SONG Xuejun, YOU Tiantong.A Network Access Control Mechanism Based on Role And Behavior[C]// IEEE.Proceedings - 2010 3rd IEEE International Conference on Broadband Network andMultimedia Technology, October 26-28, 2010, CHINA. CHINA:IEEE, 2010:95-99.
|
| [8] |
ZHU Xing Peng, HAO Feng, CHEN Hong.Access Control Policy Based on Behavior Patterns[C]// IEEE. 3rd International Conference on Genetic and Evolutionary Computing, WGEC 2009, October 14-17, 2009, China. New York: IEEE, 2009 : 557-560.
|
| [9] |
隋喆. 群体网络行为模型研究与应用[D]. 成都:四川大学,2006.
|
| [10] |
郑周,张大军,李运发. 云计算中面向数据存储的安全访问控制机制[J]. 信息网络安全,2015(9):221-226.
|
| [11] |
冯登国,张阳, 张玉清. 信息安全风险评估综述[J]. 通信学报, 2014(7):10-18.
|
| [12] |
王红凯,王志强,龚小刚. 移动互联网安全问题及防护措施探讨[J]. 信息网络安全,2014(9):207-210.
|
| [13] |
HAN J W 著. 范明,孟小峰,译. 数据挖掘:概念与技术[M]. 北京:机械工业出版社,2012.
|