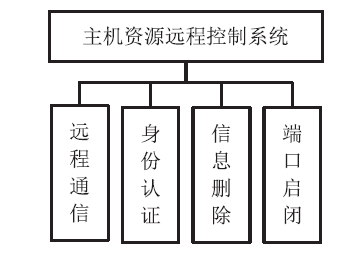
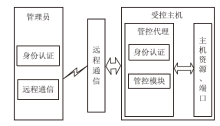
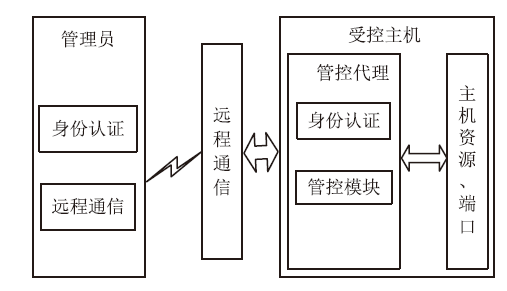
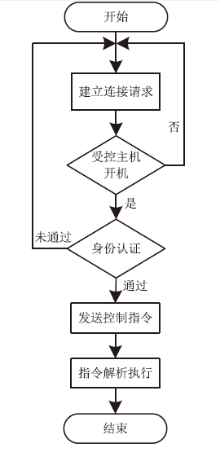
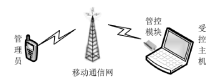
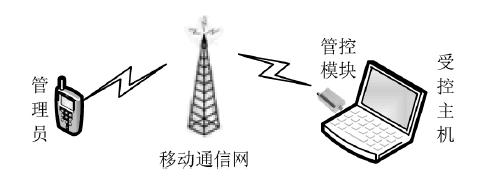
| [1] |
查鑫. 基于Android的移动智能终端远程控制系统的设计与实现[D]. 北京:北京邮电大学,2014.
|
| [2] |
穆胜亮,秦贵和. 基于3G网络和CAN总线的汽车远程控制系统设计[J]. 计算机测量与控制,2015,23(7):2396-2399.
|
| [3] |
范睿. 研究了基于TCP/IP协议的远程控制系统[D]. 长沙:中南大学,2013.
|
| [4] |
尹燕彬,文伟平. 计算机数据安全删除和隐私保护[J]. 信息网络安全,2009(5):55-58.
|
| [5] |
李敏,周安民. 计算机数据安全删除的研究与实现[J]. 信息安全与通信保密,2010(10):73-77.
|
| [6] |
郭松辉,王玉龙,邵奇峰,等. 基于关键页覆写的数据清除技术[J]. 计算机工程与设计,2015,36(1):88-92.
|
| [7] |
聂元铭,吴晓明,贾磊雷. 重要信息系统数据销毁/恢复技术及其安全措施研究[J]. 信息网络安全,2011(1):12-14.
|
| [8] |
杨泽明,许榕生,刘宝旭. 文件删除的恢复与反恢复[J]. 信息网络安全,2002(4):38-41.
|
| [9] |
高阳. 信息载体实时安全监控与销毁系统的研究[D]. 南京:南京航空航天大学,2010.
|
| [10] |
郑争兵,赵峰. 基于GSM的远程心率监控系统设计[J]. 计算机应用,2012,32(7):2082-2084.
|
| [11] |
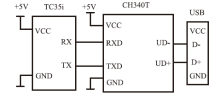
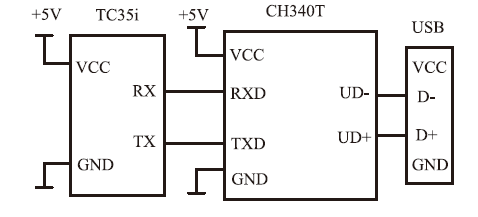
苏维嘉,张其阳. 基于TC35I的无线数据采集系统的设计[J]. 电子技术应用,2009(12):88-90.
|
| [12] |
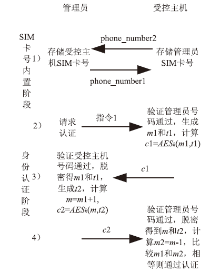
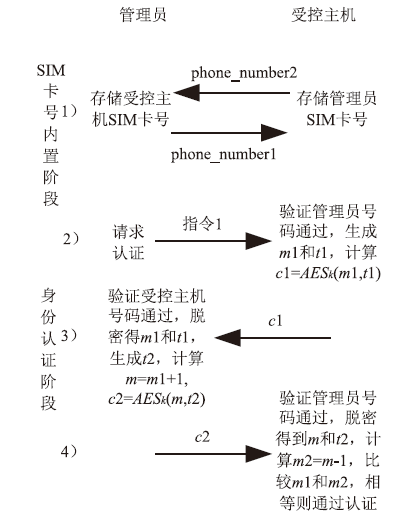
郑兆华,彭金莲,程杰仁. 基于手机令牌的移动应用双向身份认证方案研究[J]. 电信科学,2014(9):87-91.
|
| [13] |
宋四新,裴金勇. 基于HOOK技术的认证系统研究[J]. 计算机安全,2008(4):10-12.
|
| [14] |
马骏驰. 基于API函数实现应用程序的隐藏[J]. 电子科技,2009(4):82-84.
|
| [15] |
卢立蕾,文伟平. Window环境木马进程隐藏技术研究[J]. 信息网络安全,2009(5):34-35.
|
| [16] |
孙瑜. 基于SNMP的主机性能远程监控的研究与实现[D]. 哈尔滨:哈尔滨工业大学,2013.
|
| [17] |
孙玉伟,童新海,张林惠,等.云桌面中USB设备重定向技术研究[J]. 信息网络安全,2015(4):78-85.
|