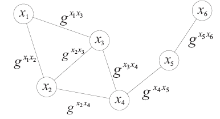
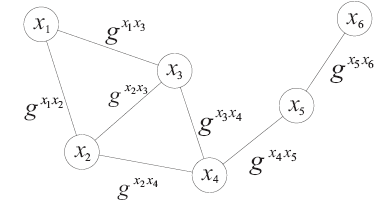
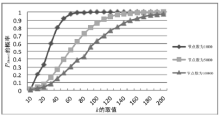
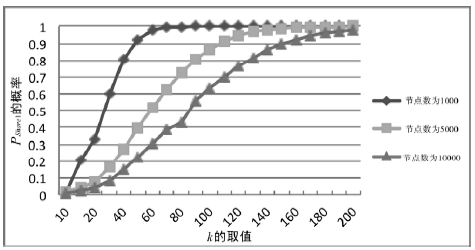
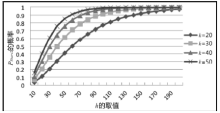
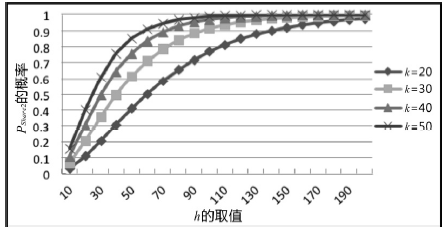
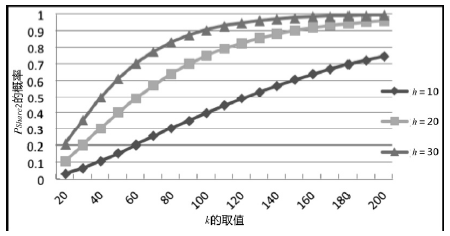
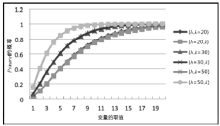
Netinfo Security ›› 2017, Vol. 17 ›› Issue (8): 45-52.doi: 10.3969/j.issn.1671-1122.2017.08.007
• Orginal Article • Previous Articles Next Articles
Regional Autonomous Identity Authentication Management Scheme for Space Self-organized Networks
Jian ZHOU1,2( ), Liyan SUN1, Aihua DUAN1, Wenjun SHI1
), Liyan SUN1, Aihua DUAN1, Wenjun SHI1
- 1. School of Management Science and Engineering, Anhui University of Finance and Economics, Bengbu Anhui 233041, China
2. School of Computer Science, Beijing University of Post and Telecommunications, Beijing 100083, China
-
Received:2017-06-10Online:2017-08-20Published:2020-05-12
CLC Number:
Cite this article
Jian ZHOU, Liyan SUN, Aihua DUAN, Wenjun SHI. Regional Autonomous Identity Authentication Management Scheme for Space Self-organized Networks[J]. Netinfo Security, 2017, 17(8): 45-52.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2017.08.007
| [1] | WEBER W J, CESARONE R J,ABRAHAM D S.Transforming the Deep Space Network into the Interplanetary Network[J]. Acta Astronautica, 2006,58(8):411-421. |
| [2] | POSNER E C, STEVENS R.Deep Space Communication-Past, Present, and Future[J].IEEE Communications Magazine, 1984(22):8-21. |
| [3] | WILLIAMSON M.Deep Space Communications[J].IEEE Review, 1998, 44(3):119-122. |
| [4] | DOYLE R,BERNARD D,RIEDEL E,et al.Autonomy and Software Technology on NASA's Deep Space One[J].IEEE Intelligent Systems & Their Applications,1999,14(3):10-15. |
| [5] | CUI P, XU R, ZHU S, et al.State of the Art and Development Trends of On-board Autonomy Technology for Deep Space Explorer[J]. Hangkong Xuebao/acta Aeronautica Et Astronautica Sinica, 2014, 35(1):13-28. |
| [6] | CAMP T, BOLENG J, DAVIES V.A Survey of Mobility Models for Ad-hoc Network Research[J].Wireless Communications and Mobile Computing,2002,2(5):483-502. |
| [7] | HAO Y,HAI Y L,FAN Y,et al.Security in Mobile Ad-hoc Networks: Challenges and Solutions[J]. IEEE Wireless Communications, 2004,11(1):38-47. |
| [8] | SAKHAEE E,JAMALIPOUR A,KATO N.Aeronautical Ad-hoc Networks[C]//IEEE WCNC.Wireless Communications and Networking Conference 2006 , April 3-6,2006,Las Vegas, NV, USA.New York:IEEE,2006, :246-251. |
| [9] | ILKER B,SAHINGOZ O K,SAMIL T.Flying Ad-Hoc Networks (FANETs): a Survey[J]. Ad Hoc Networks, 2013, 11(11):1254-1270. |
| [10] | ARNE B,JOHANNES E,SIMON J,et al.New Generation Sensor Web Enablement[J].Sensors, 2011, 11(3):2652-2699. |
| [11] | SHEN C C,RAJAGOPALAN S,BORKAR G,et al.A Flexible Routing Architecture for Ad-hoc Space Networks[J].Computer Networks the International Journal of Computer & Telecommunications Networking, 2004, 46(3):389-410. |
| [12] | VLADIMIROVA T,WU X,BRIDGES C P.Development of a Satellite Sensor Network for Future Space Missions[C]// IEEE .Aerospace Conference 2008, March 1-8,2008,Big Sky, MT, USA.New York:IEEE ,2008:1-8. |
| [13] | SUN R, GUO J, GILL E K A. Opportunities and Challenges of Wireless Sensor Networks in Space[J].International Astronautical Federation,2010,28(87):517-521. |
| [14] | 王友俊,张红旗,王津,等. 面向任务的网络空间故障定位模型[J]. 信息网络安全,2017(4):61-70. |
| [15] | 马宗峰,辛明瑞,申景诗,等. 分布式集群空间飞行器综述[J].航天器工程,2013,22(1):101-105. |
| [16] | 刘川葆,陈明志, 林伟宁,等. HCE模式下一种基于零知识证明的身份认证方法[J]. 信息网络安全,2017(6):68-74. |
| [17] | BOURKE J,UDREA B,NAYAK M.Pirarucu: The Mars Moon Prospector[C]// IEEE. Aerospace Conference 2016,March 5-12,2016 ,Big Sky, MT, USA.New York:IEEE,2016:1-6. |
| [18] | DRENTSCHEW M,MARSZALEK M,ZEIGER F. Pico-and Nano-satellite Based Mobile Ad-hoc Networks - A Requirements Study[EB/OL].,2017-3-10. |
| [19] | WU W R,LIU W W,JINAG Y P.Development of Deep Space Exploration beyond the Moon[J].Aerospace China, 2011(7): 9-12. |
| [20] | HINCHEY M,Dai Y S, Rouff C A,et al.Modeling for NASA Autonomous Nano-Technology Swarm Missions and Model-Driven Autonomic Computing[C]// IEEE.International Conference on Advanced NETWORKING and Applications,May 21 - 23, 2007 ,Niagara Falls, Ontario, Canada. Washington:IEEE Computer Society ,2007:250-257. |
| [21] | AN J P,JIN S,XU J,et al.Development and Outlook of Deep Space Communication Network Protocol[J].Journal on Communications, 2016, 37(7):50-61. |
| [22] | IVANCIC W D.Security Analysis of DTN Architecture and Bundle Protocol Specification for Space Based Networks[C]// IEEE.Aerospace Conference 2010 IEEE, March 6-13,2010,Big Sky, MT, USA.New York:IEEE, 2010:1-12. |
| [23] | BINDRA H S, SANGAL A L.Considerations and Open Issues in Delay Tolerant Network'S (DTNs) Security[J].Wireless Sensor Network, 2010, 2(8): 645-648. |
| [24] | JIANG C X,WANG X X,WANG J,et al.Security in Space Information Networks[J].IEEE Communications Magazine,2015,53(8):82-88. |
| [25] | BHUTTA N,ANSA G,JOHNSON E,et al.Security Analysis for Delay/Disruption Tolerant Satellite and Sensor Networks[C]// IWSSC 2009.International Workshop on Satellite and Space Communications,september 9-11, 2009,Tuscany, Italy.New York:IEEE, 2009:385-389. |
| [26] | YANG D M,MU D J.Novel Key Management and Authentication Scheme for Ad hoc Space Networks[J].Journal on Communications, 2006,27(8):104-112. |
| [27] | ZHONG Y T,MA J F.Identity Based Group Key Management Scheme for LEO/MEO Double-Layer Space Information Network[J].Journal of Astronautics,2011, 32(7): 1551-1557. |
| [28] | LIU Y C,ZHANG A X,LI J H, et al.An Anonymous Distributed Key Management System Based on CL-PKC for Space Information Network[C]//IEEE. ICC 2016 SAC Satellite and Space Communications, May 22-27,2016 ,Kuala Lumpur, Malaysia.New York:IEEE,2016:1-7. |
| [29] | 杨德明,慕德俊,许钟. Ad hoc空间网络密钥管理与认证方案[J].通信学报,2006,27(8):104-112. |
| [30] | KLAOUDATOU E,KONSTANTINOU E.A Survey on Cluster-Based Group Key Agreement Protocols for WSNs[J].Communications Surveys & Tutorials,2011,13(3):429-442. |
| [31] | SON J H,LEE J S,SEO S W.Topological Key Hierarchy for Energy-Efficient Group Key Management in Wireless Sensor Networks[J].Wireless Personal Communications,2010, 52(2):359-382. |
| [32] | SEBA H,LAGRAA S,KHEDDOUCI H.Alliance-based Clustering Scheme for Group Key Management in Mobile Ad hoc Networks[J].Journal of Supercomputing, 2012,61(3):481-501. |
| [33] | SEUNG Y,ROBIN K.Composite Key Management for Ad Hoc Networks[C]// IEEE.Proceeding of the First Annual Internationl Conference on Mobile and Ubiquitous Systems: Networking and Services( MobiQuitous 04),August 26,2004,Boston, MA, USA. New York:IEEE,2004:52-61. |
| [34] | FRANK S.The Resurrecting Duckling—What Next?[J].Lecture Notes in Computer Science, 2001, 2133(2001): 204-214. |
| [35] | VENKATESAN S,OLESHCHUK V A,CHELLAPPAN C, et al.Analysis of Key Management Protocols for Social Networks[J].Social Network Analysis and Mining,2016, 6(1):1-16. |
| [36] | CAINI C,CRUICKSHANK H,FARRELL S, et al. Delay- and Disruption-Tolerant Networking (DTN): An Alternative Solution for Future Satellite Networking Applications[EB/OL]. ,2011-10-20. |
| [37] | DRAKAKIS K E, PANAGOPOULOS A D, COTTIS P G.Overview of Satellite Communication Networks Security: Introduction of EAP[J].International Journal of Security and Networks, 2009,4(3):164-170. |
| [38] | LV X,MU Y,LI H.Non-Interactive Key Establishment for Bundle Security Protocol of Space DTNs[EB/OL]. ,2013-11-7. |
| [39] | ZHOU J, SONG M, SONG J, et al.Autonomic Group Key Management in Deep Space DTN[J]. Wireless Personal Communications, 2014, 77(1):269-287. |
| [40] | LV X X,LI H.Error-andloss-tolerant Bundle Fragment Authentication for Space DTNs[J]. Frontiers of Computer Science, 2014, 8(6):1012-1023. |
| [41] | BHASIN K,HAYDEN J L.Space Internet Architecture and Technologies for NASA Enterprises[J]. International Journal of Satellite Communications , 2002 ,20(5) : 311-332. |
| [42] | ZHOU J,ZHOU X W.Autonomous Shared Key Management Scheme for Space Networks[J]. Wireless Personal Communications, 2013, 72(4):2425-2443. |
| [43] | DIFFIE W.Hellman"New directions in cryptography"[J]. IEEE Transactions on Information Theory,1976,22(6):644-654. |
| [44] | FENG Bao, ROBERT H Deng, HuaFei Zhu.Variations of Diffie-Hellman Problem[J].Lecture Notes in Computer Science, 2003: 301-312. |
| [45] | GILBERT E N.Random Graphs[J].Annals of Mathematical Statistics, 1959,30(4):1141-1144. |
| [46] | ERDOS P,RENYI A.On random graphs[J].Publications Mathematic, 1959,6(4):290-297. |
| [1] | Xiaofen LIU, Xiaofeng CHEN, Guiren LIAN, Song LIN. Authenticated Multiparty Quantum Secret Sharing Protocol with d-level Single Particle [J]. Netinfo Security, 2020, 20(3): 51-55. |
| [2] | Fuyou ZHANG, Qiongxiao WANG, Li SONG. Research on Unified Identity Authentication System Based on Biometrics [J]. Netinfo Security, 2019, 19(9): 86-90. |
| [3] | Shun ZHANG, Zhangkai CHEN, Fengyu LIANG, Runhua SHI. A Quantum Identity Authentication Based on Bell State [J]. Netinfo Security, 2019, 19(11): 43-48. |
| [4] | Wei HU, Qiuhan WU, Shengli LIU, Wei FU. Design of Secure eID and Identity Authentication Agreement in Mobile Terminal Based on Guomi Algorithm and Blockchain [J]. Netinfo Security, 2018, 18(7): 7-9. |
| [5] | Lin YOU, Jiahao LIANG. Research on Secure Identity Authentication Based on Homomorphic Encryption and Biometric [J]. Netinfo Security, 2018, 18(4): 1-8. |
| [6] | Ziwen SUN, Fu LI. Gesture Authentication Method Based on HMM and D-S Evidence Theory [J]. Netinfo Security, 2018, 18(10): 17-23. |
| [7] | Baoyuan KANG, Jiaqiang WANG, Dongyang SHAO, Chunqing LI. A Secure Authentication and Key Agreement Protocol for Heterogeneous Ad Hoc Wireless Sensor Networks [J]. Netinfo Security, 2018, 18(1): 23-30. |
| [8] | ZHAN Man, XIAN Hequn, ZHANG Shuguang. Research on Identity Authentication Technology Based on Gravity Sensor [J]. 信息网络安全, 2017, 17(9): 58-62. |
| [9] | ZHAO Kaili, LI Danyi, LI Qiang, MA cunqing. Implementation of Identity Authentication Scheme Based on Smart Mobile Cryptographic Module [J]. 信息网络安全, 2017, 17(9): 107-110. |
| [10] | LIU Chuanbao, CHEN Mingzhi, LIN Weining, FENG Yingyan. A Method of Identity Authentication Based on Zero Knowledge Proof in HCE Mode [J]. 信息网络安全, 2017, 17(6): 68-74. |
| [11] | Jiebin GUO, Yunfa LI, Dajun ZHANG. Research on an Authentication Strategy for Data Security in Cloud Computing [J]. Netinfo Security, 2017, 17(3): 72-77. |
| [12] | ZHAO Jian, ZHANG Chang, WEN Xiangdong. Research and Design of Remote Control System of Host Resources [J]. 信息网络安全, 2016, 16(7): 29-34. |
| [13] | WANG Jing. Application of the Unified Identity Authentication and User Management Platform in Electric Group Enterprise [J]. 信息网络安全, 2016, 16(12): 81-85. |
| [14] | LIU Chang, HE Jingsha. A Network Behavior-based Access Control Model [J]. 信息网络安全, 2016, 16(10): 34-39. |
| [15] | ZHANG Yuting, YAN Chenghua. Research on RFID Authentication Technology Based on Two-way Authentication Protocol [J]. 信息网络安全, 2016, 16(1): 64-69. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||