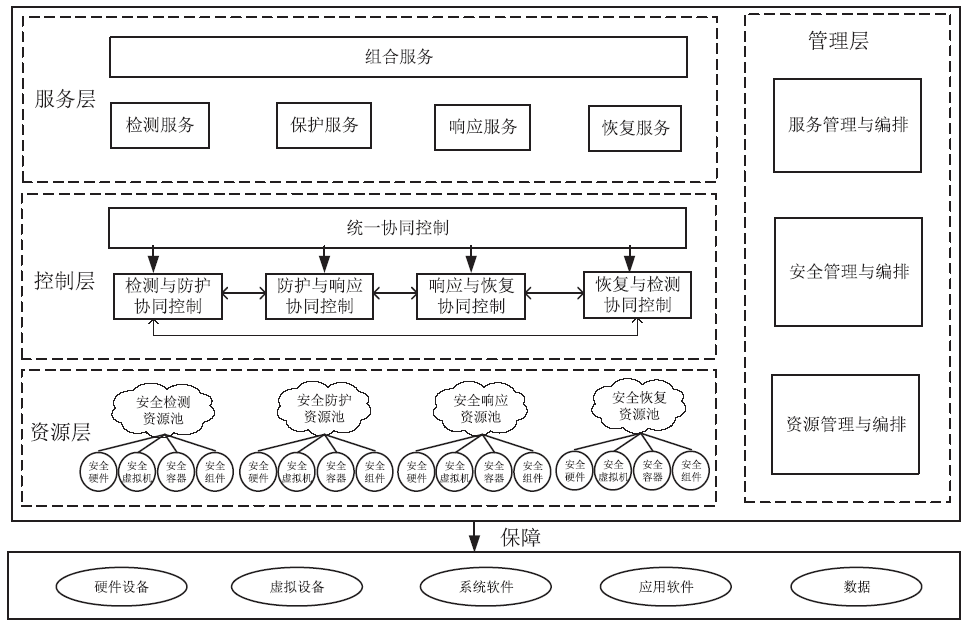
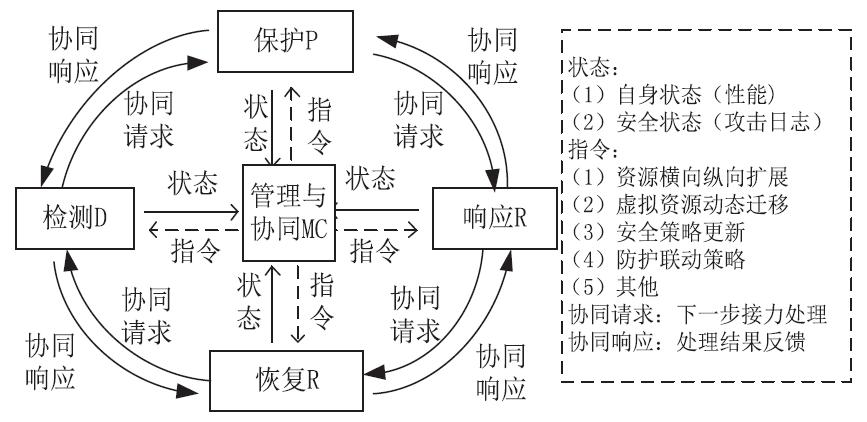
| [1] |
Cloud Security Alliance. 12Top threats[EB/OL]. https://downloads.cloudsecurityalliance.org/assets/research/top-threats/treacherous-12-top-threats.pdf, 2020-5-15.
|
| [2] |
ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al. Survey on Cloud Computing Security[J]. Journal of Software, 2016,27(6):1328-1348.
|
|
张玉清, 王晓菲, 刘雪峰, 等. 云计算环境安全综述[J]. 软件学报, 2016,27(6):1328-1348.
|
| [3] |
FENG Dengguo, SUN Rui, ZHANG Yang. Information Security Architecture[M]. Beijing: Tsinghua University Press, 2008.
|
|
冯登国, 孙锐, 张阳. 信息安全体系结构[M]. 北京: 清华大学出版社, 2008.
|
| [4] |
Gartner. Staying Secure in the Cloud Is a Shared Responsibility[EB/OL]. https://www.gartner.com/doc/3277620/staying-secure-cloud-shared-responsibility, 2020-5-15.
|
| [5] |
GAT 1390. 2-2017 Information security technology——General requirements for classified protection of cyber security——Part 2: Special security requirements for cloud computing[S]. Beijing: Standards Press of China, 2017
|
|
GAT 1390. 2-2017 信息安全技术 网络安全等级保护基本要求第2部分:云计算安全扩展要求[S]. 北京:中国标准出版社: 中国标准出版社, 2017.
|
| [6] |
Aliyun. Aliyun Cloud Security White Paper V4.1[EB/OL]. https://security.aliyun.com/2020, 2020-5-15.
|
|
阿里云. 阿里云安全白皮书V4.1[EB/OL]. https://security.aliyun.com/2020, 2020-5-15.
|
| [7] |
AMAZON. AWSShared Responsibility Model[EB/OL]. https://aws.amazon.com/compliance/shared-responsibility-model, 2020-5-15.
|
| [8] |
Microsoft. Microsoft Shared Responsibilities for Cloud Computing[EB/OL]. https://gallery.technet.microsoft.com/Shared-Responsibilities-81d0ff91, 2020-5-15.
|
| [9] |
Tencent Cloud. Tencent Cloud Security White Paper 2016[EB/OL]. https://ask.qcloudimg.com/draft/2800919/pu3imp4m5d.pdf.2016, 2020-5-15.
|
|
腾讯云. 腾讯云安全白皮书2016.[EB/OL]. https://ask.qcloudimg.com/draft/2800919/pu3imp4m5d.pdf.2016, 2020-5-15.
|
| [10] |
China Telecom Network Security Laboratory. Cloud Computing Security: Technology And Application[M]. Beijing: Electronic Industry Press, 2012.
|
|
中国电信网络安全实验室. 云计算安全:技术与应用[M]. 北京: 电子工业出版社, 2012.
|
| [11] |
CSA. CSA Security Guidance for Critical Areas of Focusin Cloud Computingv4-0[EB/OL]. https://cloudsecurityalliance.org/document/security-guidance-for-critical-areas-of-focus-in-cloud-computing-v4-0/, 2020-5-15.
|
| [12] |
FEND Dengguo, ZHANG Min, ZHANG Yan, et al. Cloud Security Research[J]. Journal of software, 2011,22(1):71-83.
doi: 10.3724/SP.J.1001.2011.03958
URL
|
|
冯登国, 张敏, 张妍, 等. 云安全研究[J]. 软件学报, 2011,22(1):71-83.
|
| [13] |
SHEN Changxiang, ZHANG Huanguo, WANG Huaimin, et al. Research and Development of Trusted Computing[J]. Chinese Science: Information Science, 2010,40(2):139-166.
|
|
沈昌祥, 张焕国, 王怀民, 等. 可信计算的研究与发展[J]. 中国科学:信息科学, 2010,40(2):139-166.
|
| [14] |
LIN Chuang, SU Wenbo, MENG Kun, et al. Cloud Computing Security: Architecture, Mechanism and Model Evaluation[J] Chinese Journal of computer science, 2013,36(9):1765-1784.
|
|
林闯, 苏文博, 孟坤, 等. 云计算安全:体系结构、机制与模型评价[J] 计算机学报, 2013,36(9):1765-1784.
|
| [15] |
TU Shanshan, HU Jun, NING Zhenhu. Trusted Computing: Building A New Cloud Security Architecture[J] Information Security Research, 2017,3(5):440-450
|
|
涂山山, 胡俊, 宁振虎 .可信计算: 打造云安全新体系结构[J]. 信息安全研究, 2017,3(5):440-450.
|
| [16] |
H3C VCF. Controller Service Chain Technology White Paper[EB/OL]. http://www0.h3c.com.cn/cn/d201605/928711300030.htm.2016, 2020-5-15.
|
|
H3C VCF. 控制器服务链技术白皮书[EB/OL]. http://www0.h3c.com.cn/cn/d201605/928711300030.htm, 2020-5-15.
|
 ), WU Yabiao1, ZHANG Yuqing2
), WU Yabiao1, ZHANG Yuqing2