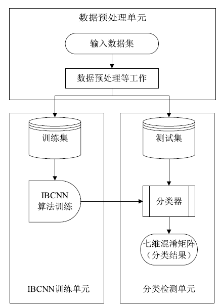
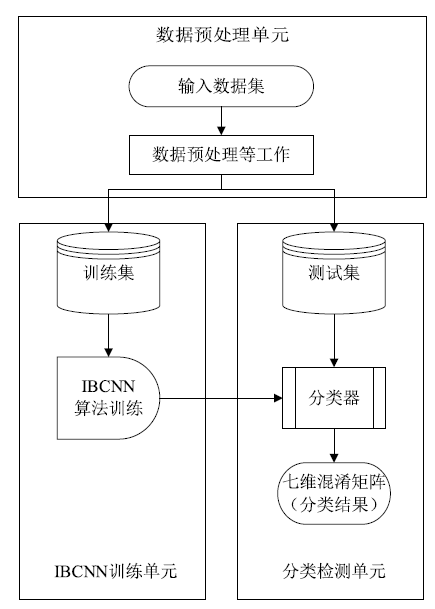
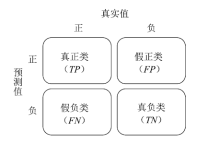
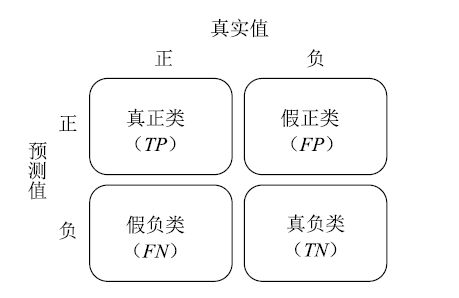
Netinfo Security ›› 2020, Vol. 20 ›› Issue (10): 67-74.doi: 10.3969/j.issn.1671-1122.2020.10.009
Previous Articles Next Articles
Classification of Malicious Network Traffic Based on Improved Bilinear Convolutional Neural Network
GU Zhaojun1,2, HAO Jintao1,2( ), ZHOU Jingxian1
), ZHOU Jingxian1
- 1. Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
2. Computer Science and Technology, Civil Aviation University of China, Tianjin 300300, China
-
Received:2020-03-02Online:2020-10-10Published:2020-11-25 -
Contact:HAO Jintao E-mail:haojintao291@163.com
CLC Number:
Cite this article
GU Zhaojun, HAO Jintao, ZHOU Jingxian. Classification of Malicious Network Traffic Based on Improved Bilinear Convolutional Neural Network[J]. Netinfo Security, 2020, 20(10): 67-74.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.10.009
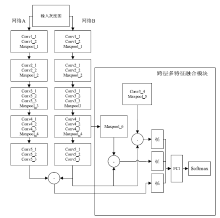
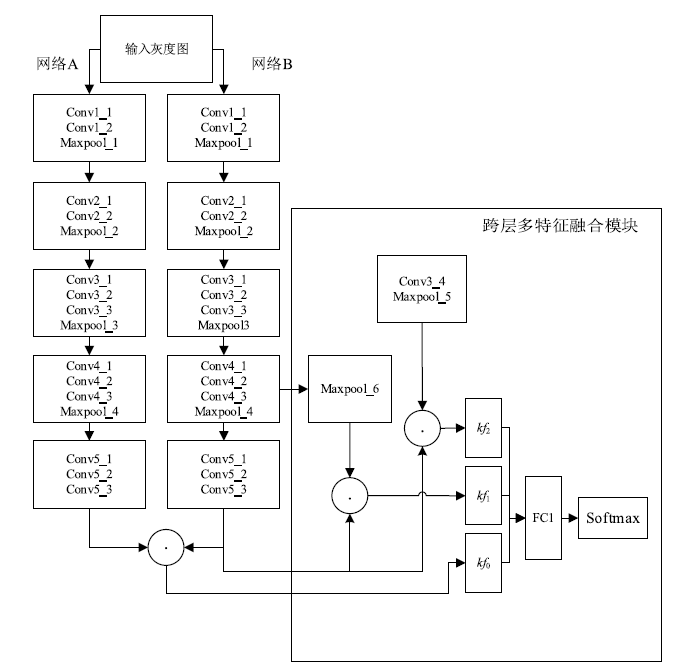
| 单元模块 | 层名 | 参数 (卷积核大小、步长、填充) | 输出通道数 | 输出特征图大小(长×宽×通道数) |
|---|---|---|---|---|
| Conv1_X | Conv1_1 | 3×3,1×1,1 | 64 | 32×32×64 |
| Conv1_2 | 3×3,1×1,1 | 64 | 32×32×64 | |
| Maxpool_1 | 2×2,2,0 | 64 | 16×16×64 | |
| Conv2_X | Conv2_1 | 3×3,1×1,1 | 128 | 16×16×128 |
| Conv2_2 | 3×3,1×1,1 | 128 | 16×16×128 | |
| Maxpool_2 | 2×2,2,0 | 128 | 8×8×128 | |
| Conv3_X | Conv3_1 | 3×3,1×1,1 | 256 | 8×8×256 |
| Conv3_2 | 3×3,1×1,1 | 256 | 8×8×256 | |
| Conv3_3 | 3×3,1×1,1 | 256 | 8×8×256 | |
| Maxpool_3 | 2×2,2,0 | 256 | 4×4×256 | |
| Conv4_X | Conv4_1 | 3×3,1×1,1 | 512 | 4×4×512 |
| Conv4_2 | 3×3,1×1,1 | 512 | 4×4×512 | |
| Conv4_3 | 3×3,1×1,1 | 512 | 4×4×512 | |
| Maxpool_4 | 2×2,2,0 | 512 | 2×2×512 | |
| Conv5_X | Conv5_1 | 3×3,1×1,1 | 512 | 2×2×512 |
| Conv5_2 | 3×3,1×1,1 | 512 | 2×2×512 | |
| Conv5_3 | 3×3,1×1,1 | 512 | 2×2×512 |
| [1] | China Internet Network Information Center. The 44th Statistical Report on Internet Development in China[EB/OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/201908, 2019-8-30. |
| 中国互联网络信息中心.第44次中国互联网络发展现状统计报告[EB/OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/201908, 2019-8-30. | |
| [2] | MADHUKAR A, WILLIAMSON C. A Longitudinal Study of P2P Traffic Classification [C]//IEEE. 14th IEEE International Symposium on Modeling, Analysis, and Simulation, September 11-14, 2006, Monterey, CA, USA. New York: IEEE, 2006: 179-188. |
| [3] | JAISWAL R C, LOKHANDE S D. Machine Learning Based Internet Traffic Recognition with Statistical Approach [C]//IEEE. 2013 Annual IEEE India Conference(INDICON), December 13-15, 2013, Mumbai. New York: IEEE, 2013: 1-6. |
| [4] | DHOTE Y, AGRAWAL S, DEED A J. A Survey on Feature Selection Techniques for Internet Traffic Classification [C]//IEEE. 2015 International Conference on Computational Intelligence and Communication Networks(CICN), December 12-14, 2015, Jabalpur. New York: IEEE, 2015: 1375-1380. |
| [5] | ZHANG Jian, CHEN Bohan, GONG Liangyi, et al. Research on Malware Detection Technology Based on Image Analysis[J]. Netinfo Security, 2019,19(10):24-31. |
| [6] | ZHANG Chenbin, ZHANG Yunchun, ZHENG Yang, et al. Malware Classification Based on Grayscale Texture Fingerprints[J]. Computer Science, 2018,45(S1):383-386. |
| 张晨斌, 张云春, 郑杨, 等. 基于灰度图纹理指纹的恶意软件分类[J]. 计算机科学, 2018,45(S1):383-386. | |
| [7] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning [C]//IEEE. 2017 International Conference on Information Networking(ICOIN), January 11-13, 2017, Da Nang, Vietnam. New York: IEEE, 2017: 712-717. |
| [8] | RAN Jing, CHEN Yexin, LI Shulan. Three-dimensional Convolutional Neural Network Based Traffic Classification for Wireless Communications [C]//IEEE. 2018 IEEE Global Conference on Signal and Information Processing(GlobalSIP), November 26-29, 2018, Anaheim, CA, USA. New York: IEEE, 2018: 624-627. |
| [9] | ZHANG Fan, WANG Yong, MIAO Ye. Network Traffic Classification Method Based on Improved Capsule Neural Network [C]//IEEE. 14th International Conference on Computational Intelligence and Security(CIS), November 16-19, 2018, Hangzhou, China. New York: IEEE, 2018: 174-178. |
| [10] | LIM H, KIM J, HEO J, et al. Packet-Based Network Traffic Classification Using Deep Learning [C]//IEEE. 2019 International Conference on Artificial Intelligence in Information and Communication(ICAIIC), February 11-13, 2019, Okinawa, Japan. New York: IEEE, 2019: 46-51. |
| [11] | LI Daoquan, WANG Xue, YU Bo, et al. Network Traffic Classification Method Based on One-dimensional Convolutional Neural Network[J]. Computer Engineering and Applications, 2020,56(3):94-99. |
| 李道全, 王雪, 于波, 等. 基于一维卷积神经网络的网络流量分类方法[J]. 计算机工程与应用, 2020,56(3):94-99. | |
| [12] | HAN Xiaoguang, QU Wu, YAO Xuanxia, et al. Research on Detection Method of Malicious Code Variant Based on Texture Fingerprint[J]. Journal of Communications, 2014,35(8):125-136. |
| 韩晓光, 曲武, 姚宣霞, 等. 基于纹理指纹的恶意代码变种检测方法研究[J]. 通信学报, 2014,35(8):125-136. | |
| [13] | HAN Xiaoguang. Research on Key Technologies of Malicious Code Detection[D]. Beijing: University of Science and Technology Beijing, 2015. |
| 韩晓光. 恶意代码检测关键技术研究[D]. 北京:北京科技大学, 2015. | |
| [14] | XIE Bo. Research on ResNet Based Intrusion Detection Model[D]. Lanzhou: Lanzhou University, 2019. |
| 谢博. 基于ResNet的入侵检测模型研究[D]. 兰州:兰州大学, 2019. | |
| [15] | LUO Jianhao, WU Jianxin. Review of Fine-grained Image Classification Based on Deep Convolution Features[J]. Journal of Automation, 2017,43(8):1306-1318. |
| 罗建豪, 吴建鑫. 基于深度卷积特征的细粒度图像分类研究综述[J]. 自动化学报, 2017,43(8):1306-1318. | |
| [16] | LIU Shuying, DENG Weihong. Very Deep Convolutional Neural Network Based Image Classification Using Small Training Sample Size [C]//IEEE. 3rd IAPR Asian Conference on Pattern Recognition(ACPR), November 3-6, 2015, Kuala Lumpur, Malaysia. New York: IEEE, 2015: 730-734. |
| [17] | HE Kaiming, ZHANG Xiangyu, REN Shaoqin, et al. Deep Residual Learning for Image Recognition [C]//IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition(CVPR), June 27-30, 2016, Las Vegas, NV. New York: IEEE, 2016: 770-778. |
| [18] | HUANG Gao, LIU Zhuang, MAATEN V D, et al. Densely Connected Convolutional Networks [C]//IEEE. 2017 IEEE Conference on Computer Vision and Pattern Recognition(CVPR), July 21-26, 2017, Honolulu, HI. New York: IEEE, 2017: 2261-2269. |
| [19] | KRIZHEVSKY A, SUTSKEVER I, HINTON G E. ImageNet Classification with Deep Convolutional Neural Networks[EB/OL]. http://www.image-net.org/challenges/LSVRC, 2019-12-23. |
| [20] | ZAREBA W, SUTSKEVER I, VINYALS O, Recurrent Neural Network Regularization[EB/OL]. https://arxiv.org/abs/1409.2329, 2014-9-8. |
| [1] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [2] | LIU Jing, ZHANG Xueqian, LIU Quanming. Research on Captcha Recognition of Lightweight Convolutional Neural Network with Gabor [J]. Netinfo Security, 2020, 20(7): 77-84. |
| [3] | ZHANG Leihua, HUANG Jin, ZHANG Tao, WANG Shengyu. Portrait Intelligent Analysis Application and Algorithm Optimization in Video Investigation [J]. Netinfo Security, 2020, 20(5): 88-93. |
| [4] | LIU Jianwei, HAN Yiran, LIU Bin, YU Beiyuan. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [5] | Liangchen CHEN, Baoxu LIU, Shu GAO. Research on Traffic Data Sampling Technology in Network Attack Detection [J]. Netinfo Security, 2019, 19(8): 22-28. |
| [6] | Yitao NI, Yongjia CHEN, Bogang LIN. Automatic De-obfuscation-based Malicious Webpages Detection [J]. Netinfo Security, 2019, 19(4): 37-46. |
| [7] | Liangchen CHEN, Shu GAO, Baoxu LIU, Zhigang LU. Research Status and Development Trends on Network Encrypted Traffic Identification [J]. Netinfo Security, 2019, 19(3): 19-25. |
| [8] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| [9] | Shuning WEI, Xingru CHEN, Yong TANG, Hui LIU. Research on the Application of AR-HELM Algorithm in Network Traffic Classifi cation [J]. Netinfo Security, 2018, 18(1): 9-14. |
| [10] | Liping XU, Wenjiang HAO. Analysis and Enlightenment of US Government and Enterprise Cyber Threat Intelligence [J]. Netinfo Security, 2016, 16(9): 278-284. |
| [11] | Qing HU, Benyong LIU. Speaker Recognition Algorithm Based on Convolutional Neural Networks [J]. Netinfo Security, 2016, 16(4): 55-60. |
| [12] | Zehui WU, Qiang WEI. A Secure Fault Recovery Approach Using OwnShip-Proof Model for Controller Cluster of Software Defined Networks [J]. Netinfo Security, 2016, 16(12): 13-18. |
| [13] | Shi-yuan YU, San-jun CHENG. The Application of Big Data Tools in Monitoring Network Attack [J]. Netinfo Security, 2015, 15(9): 149-153. |
| [14] | LI Zhan-bao, ZHANG Wen-gui. Cyber Resilience: New Ideas of Cyber Security Development [J]. 信息网络安全, 2014, 14(9): 76-79. |
| [15] | HOU Yu-chen. Legal Protective System of Cyber Surveillance in the United States and Its Meaning to China [J]. 信息网络安全, 2014, 14(9): 189-192. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||