Netinfo Security ›› 2019, Vol. 19 ›› Issue (12): 10-21.doi: 10.3969/j.issn.1671-1122.2019.12.002
Previous Articles Next Articles
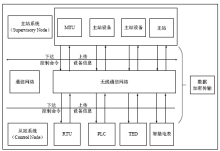
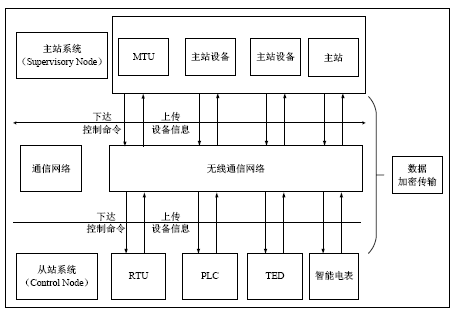
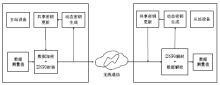
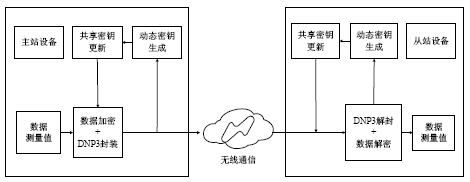
Smart Grid Wireless Communication Data Encryption Transmission Scheme Based on Dynamic Key
Meihong LI, Xiaochen QI( ), Qianqian WU
), Qianqian WU
- School of Computer and Information Technology, Beijing Jiaotong University 100044, China
-
Received:2019-09-11Online:2019-12-10Published:2020-05-11
CLC Number:
Cite this article
Meihong LI, Xiaochen QI, Qianqian WU. Smart Grid Wireless Communication Data Encryption Transmission Scheme Based on Dynamic Key[J]. Netinfo Security, 2019, 19(12): 10-21.
share this article
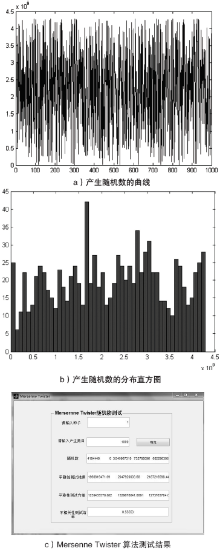
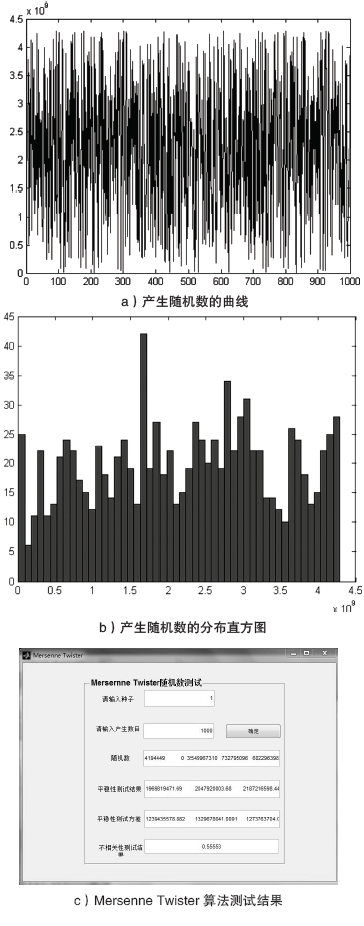
| 组号 | 均值 | 标准差 |
|---|---|---|
| 1 | 1969819471.69 | 1239435578.882 |
| 2 | 2047920003.68 | 1329678041.0091 |
| 3 | 2187216598.44 | 1273763704.0216 |
| 4 | 2105560471.31 | 1139708764.0567 |
| 5 | 2139772842.11 | 1211137659.5703 |
| 6 | 2029205991.4 | 1236946250.1248 |
| 7 | 1890509205.75 | 1222092447.2377 |
| 8 | 2038292762.02 | 1332333892.945 |
| 9 | 2192560510.94 | 1279633148.2906 |
| 10 | 2104964707.38 | 1189347360.2849 |
| 请求 次数 | 重传请求次数 | N= 4 | N=8 | N=16 | N=32 | ||||
|---|---|---|---|---|---|---|---|---|---|
| 理论 | 实际 | 理论 | 实际 | 理论 | 实际 | 理论 | 实际 | ||
| 10000 | 623 | 2344 | 2344 | 1172 | 1172 | 586 | 586 | 293 | 293 |
| 20000 | 1312 | 4672 | 4672 | 2336 | 2336 | 1168 | 1168 | 584 | 584 |
| 30000 | 1944 | 7014 | 7014 | 3507 | 3507 | 1753 | 1753 | 876 | 876 |
| 40000 | 2704 | 9324 | 9324 | 4662 | 4662 | 2331 | 2331 | 1165 | 1165 |
| 50000 | 3265 | 11684 | 11684 | 5842 | 5842 | 2921 | 2921 | 1461 | 1461 |
| 60000 | 3756 | 14061 | 14061 | 7030 | 7030 | 3515 | 3515 | 1757 | 1757 |
| 70000 | 4382 | 16404 | 16404 | 8202 | 8202 | 4101 | 4101 | 2050 | 2050 |
| 80000 | 5032 | 18742 | 18742 | 9371 | 9371 | 4685 | 4685 | 2342 | 2342 |
| 90000 | 5787 | 21053 | 21053 | 10526 | 10526 | 5263 | 5263 | 2631 | 2631 |
| 100000 | 6570 | 23357 | 23357 | 11678 | 11678 | 5839 | 5839 | 2919 | 2919 |
| 本文方案 | ||
|---|---|---|
| CN | SN | |
| 动态密钥 | 4TSE+Th | 4TSD+Th |
| 数据加密 | 5TXOR+4Thmac | 5TXOR+4Thmac |
| 总开销 | 4TSE+Th+5TXOR+4Thmac | 4TSD+Th+5TXOR+4Thmac |
| 更新次数 | 1 | 1 |
| 文献[ | ||
| CN | SN | |
| 动态密钥 | 4TSE+nTparse+4Th | 4TSD+nTparse+4Th |
| 数据加密 | 4TXOR | 4TXOR |
| 总开销 | 4TSE+nTparse+4Th+4TXOR | 4TSD+nTparse+4Th+4TXOR |
| 更新次数 | 4 | 4 |
| 文献[ | ||
| CN | SN | |
| 动态密钥 | 4TSE+nTparse+Th | 4TSD+nTparse+Th |
| 数据加密 | 4TXOR | 4TXOR |
| 总开销 | 4TSE+nTparse++Th+4TXOR | 4TSD+nTparse+Th+4TXOR |
| 更新次数 | 1 | 1 |
| [1] | GAO Tao, DENG Ling.Survey on Smart Grid and Its Development at Home and Abroad[J]. Northeast Electric Power Technology, 2012, 33(2): 5-10. |
| [2] | LIU Qian.Design and Imlpemention of Secure Distributed Network Protocol for SCADA System[D]. Xi’an: Xidian University, 2017. |
| 刘茜. 面向SCADA系统安全分布式网络协议的设计与实现[D].西安:西安电子科技大学,2017. | |
| [3] | XIAO Sheng, GONG Weibo. Wireless Network Security Using Randomness[EB/OL]. . |
| [4] | ZHANG Jianhua, HASANDKA A, WEI Jin, et al. Hybrid Communication Architectures for Distributed Smart Grid Applications[EB/OL]. , 2018-4-9. |
| [5] | SAXENA N, GRIJALVA S.Dynamic Secrets and Secret Keys Based Scheme for Securing Last Mile Smart Grid Wireless Communication[J]. IEEE Transactions on Industrial Informatics, 2017, 13(3): 1482-1491. |
| [6] | YAN Shuang.The Research and Implemention of Security Mechanism for Smart Grid DNP3[D]. Changsha: National University of Defense Technology, 2016. |
| 闫爽. 智能电网DNP3协议安全机制研究与实现[D].长沙:国防科学技术大学,2016. | |
| [7] | YAN Shaobin.Analysis of M-states Stop-and-Wait ARQ Protocol[D]. Beijing: Beijing Jiaotong University, 2009. |
| 闫绍彬. 对M种状态停止等待ARQ协议的分析[D].北京:北京交通大学,2009. | |
| [8] | BELLARE M, DESAI A, JokiPii E, et al. A Concrete Security Treetment of Symmetric Encryption[C]//IEEE. 38th Annual Symposium on Foundations of Computer Science, October 20-22, 1997, Miami Beach, FL, USA. New Jersey: IEEE, 1997: 1-32. |
| [9] | ZHOU Qian, QIN Xiaolin, DING Youwei.Hash-based Contextual Privacy Preservation in Wireless Sensor Networks[J]. Journal of Nanjing University of Science and Technology, 2017, 41(6): 753-759. |
| 周倩,秦小麟,丁有伟.无线传感器网络中基于哈希函数的上下文隐私保护[J].南京理工大学学报(自然科学版),2017,41(6):753-759. | |
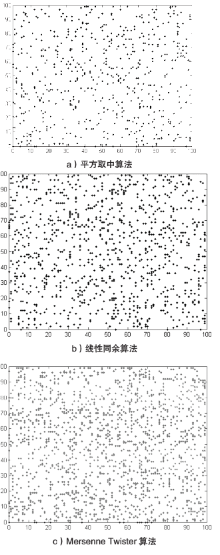
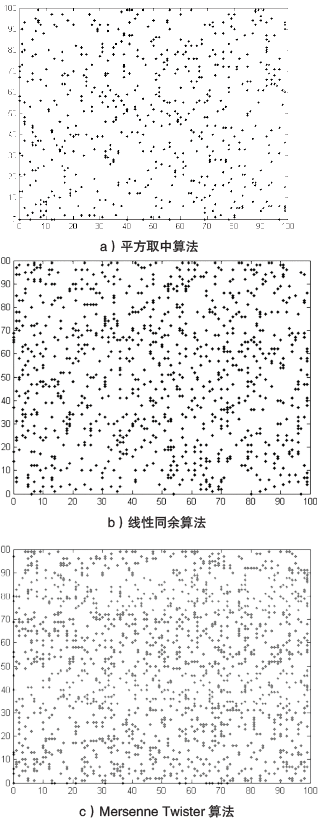
| [10] | ZHANG Dawei, SHAO Yinghai, ZUO Lei.Pseudo Random Number Generation Algorithm Based on Linear Congruence Method[J]. Journal of Liaodong University: Natural Sciences, 2018, 25(3): 201-206. |
| 张大伟,邵英海,左垒.基于线性同余法的伪随机数产生算法[J].辽东学院学报(自然科学版),2018,25(3):201-206. | |
| [11] | ECHEVERRIA P, MARISA L V.High Performance FPGA-oriented Mersenne Twister Uniform Random Number Generator[J]. Journal of Signal Processing Systems for Signal, Image, and Video Technology, 2013, 71(2): 105-109. |
| [12] | LEE M Y.On the Durbin-Watson Statistic Based on a Z-test in Large Samples[J]. International Journal of Computational Economics and Econometrics, 2016, 6(1): 114-121. |
| [13] | MATSUMOTO M, NISHIMURA T.Mersenne Twister: A 623-Dimensionally Equidistributed Uniform Pseudo-Random Number Generator[J]. ACM Transactions on Modeling and Computer Simulation: A Publication of the Association for Computing Machinery, 1998, 23(1): 3-30. |
| [14] | LIU Ting, LIU Yang, MAO Yashan, et al.A Dynamic Secret-based Encryption Scheme for Smart Grid Wireless Communication[J]. IEEE Transactions on Smart Grid, 2014, 5(3): 1175-1182. |
| [15] | GUSTAVUS J. Data Encryption Standard[EB/OL]. , 2019-5-24. |
| [16] | RIVEST R L, SHAMIR A, ADLEMAN L.A Method for Obtaining Digital Signatures and Public-key Cryptosystems[J]. Communications of the ACM, 1983, 26(1): 96-99. |
| [17] | HE Mingxing, LIN Hao.Implementation of the Advanced Encryption Standard(AES)[J]. Application Research of Computers, 2002(12): 63-65. |
| [18] | MAO Wenbo.Modern Cryptography: Theory and Practice[M]. WANG Jihong, WU Qianhong. Beijing: Publishing House of Electronics Industry, 2004. |
| MAO Wenbo.现代密码理论与实践[M].王继红,伍前红,译.北京:电子工业出版社,2004. | |
| [19] | RICHARD Spillman.Clssial and Contemporary Cryptology[M]. Beijing: Tsinghua University Press. 2005. |
| RICHARD Spillman.经典密码学与现代密码学[M].北京:清华大学出版社.2005. | |
| [20] | LI Zhimin.Design and Analysis of The Hash Functions[D]. Beijing: Beijing University of Posts and Telecommunications, 2009. |
| 李志敏. 哈希函数设计与分析[D].北京:北京邮电大学,2009. |
| [1] | Wei DONG, Yonggang LI. Research on Analysis of Attacks on Smart Grid Network Based on Complex Network [J]. Netinfo Security, 2020, 20(1): 52-60. |
| [2] | LIU Yuling, TANG Yunshan, ZHANG Qi, LI Feng. Power Dispatch Software Security Situation Assessment Method [J]. Netinfo Security, 2019, 19(8): 15-21. |
| [3] | ZHOU Quan, XU Shumei, YANG Ningbin. A Privacy Protection Scheme for Smart Grid Based on Attribute-based Group Signature [J]. Netinfo Security, 2019, 19(7): 25-30. |
| [4] | Zhigang JIN, Tong WU, Gen LI. Research on Internet of Things Security Mechanism Based on Short Distance Wireless Communication [J]. Netinfo Security, 2019, 19(10): 16-23. |
| [5] | Xiuxia TIAN, Xi CHEN, Fuliang TIAN. Community Distributed Power Security Transaction Scheme Based on Blockchain [J]. Netinfo Security, 2019, 19(1): 51-58. |
| [6] | LI Liang, ZHANG Yinghui, DENG Kaixin, ZHANG Tiantian. Privacy-aware Power Injection in 5G Smart Grid [J]. 信息网络安全, 2018, 18(12): 87-92. |
| [7] | CHEN Yang, WANG Yong, SUN Wei. A YARN-based Smart Grid Big Data Abnormal Detection [J]. 信息网络安全, 2017, 17(7): 11-17. |
| [8] | ZENG Yu, GUO Jinquan. Research of the Security Situation about Industrial Control Information System [J]. 信息网络安全, 2016, 16(9): 169-172. |
| [9] | LIU Jianan, WENG Jian. Survey on Smart Grid Security [J]. 信息网络安全, 2016, 16(5): 78-84. |
| [10] | LI Zengpeng, ZOU Yan, ZHANG Lei, MA Chunguang. A Privacy Preservation Scheme for Data Exchange of Smart Grid Based on Homomorphic Encryption [J]. 信息网络安全, 2016, 16(3): 1-7. |
| [11] | ZHENG Shengjun, GUO Longhua, CHEN Jian, NAN Shujun. An Online Detection System for Advanced Malware Based on Virtual Execution Technology [J]. 信息网络安全, 2016, 16(1): 29-33. |
| [12] | LIU Wei, YE Qing, WANG Cheng. Improved LEACH Algorithm Based on Dynamic Key Management [J]. 信息网络安全, 2015, 15(8): 41-46. |
| [13] | SHI Shasha, SUN Wenhong, JIANG Mingjian, QU Haipeng. Research on Smart Grid Privacy Protocol Based on Distributed Data Aggregation [J]. 信息网络安全, 2015, 15(12): 59-65. |
| [14] | . NULL [J]. , 2012, 12(8): 0-0. |
| [15] | . Study on Industrial Control SCADA Systems Information Security Protection System [J]. , 2012, 12(5): 0-0. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||