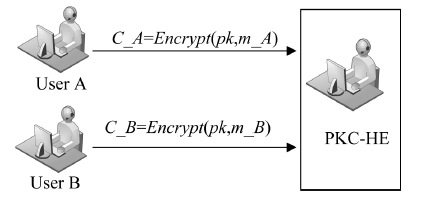
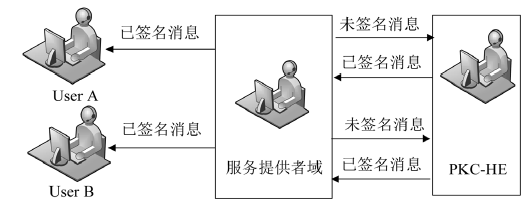
| [1] |
石沙沙,孙文红,江明建,等.基于分布式数据聚合的智能电网隐私保护协议研究[J]. 信息网络安全,2015(12):59-65.
|
| [2] |
张东霞,苗新,刘丽平,等. 智能电网大数据技术发展研究[J]. 中国电机工程学报,2015(1):2-12.
|
| [3] |
李兴源,魏巍,王渝红,等.坚强智能电网发展技术的研究[J]. 电力系统保护与控制,2009,37(17):1-7.
|
| [4] |
陈福臻,程久军,廖竞学,等. 基于网络编码的同态HASH抗污染攻击系统研究[J]. 信息网络安全,2015(6):33-40.
|
| [5] |
MCDANIEL P, MCLAUGHLIN S.Security and Privacy Challenges in the Smart Grid[J]. IEEE Security & Privacy, 2009, 7(3): 75-77.
|
| [6] |
SKOPIK F.Security Is Not Enough! On Privacy Challenges in Smart Grids[J]. International Journal of Smart Grid Clean Energy, 2012, 1(1): 7-14.
|
| [7] |
ZEADALLY S, PATHAN A S K, ALCARAZ C, et al. Towards Privacy Protection in Smart Grid[J]. Wireless Personal Communications, 2013, 73(1): 23-50.
|
| [8] |
METKE A R, EKL R L.Security Technology For Smart Grid Networks[J]. IEEE Transactions on Smart Grid, 2010, 1(1): 99-107.
|
| [9] |
李斌,白淑君,宋怀刚.具备多级安全机制的在线数据库同态加密方案[J]. 信息网络安全,2014(12):12-15.
|
| [10] |
LI Fengjun, LUO Bo, LIU Peng.Secure Information Aggregation for Smart Grids Using Homomorphic Encryption[C]//IEEE. 2010 First IEEE International Conference on Smart Grid Communications (SmartGridComm), October 4-6, 2010, Gaithersburg, MD. New Jersey: IEEE, 2010:327-332.
|
| [11] |
GENTRY C.A Fully Homomorphic Encryption Scheme[D]. Palo Alto: Stanford University, 2009.
|
| [12] |
龚凡. 基于群签名的智能电网用电量统计及电费的缴纳方案[D]. 西安:西安电子科技大学,2013.
|
| [13] |
DIJK M V, GENTRY C, HALEVI S, et al.Fully Homomorphic Encryption over the Integers[C]//IACR. 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 30-June 3, 2010, Riviera, French. Heidelberg: Springer, 2010: 24-43.
|
| [14] |
LU Rongxing, LIANG Xiaohui, LI Xu, et al.Eppa: An Efficient And Privacy-Preserving Aggregation Scheme for Secure Smart Grid Communications[J]. IEEE Transactions on Parallel and Distributed Systems, 2012, 23(9): 1621-1631.
|
| [15] |
吕海峰,丁勇,代洪艳,等. LWE上的全同态加密方案研究[J]. 信息网络安全,2015(1):32-38.
|
| [16] |
STEHLÉ D, STEINFELD R.Faster Fully Homomorphic Encryption[C]//IACR. 16th International Conference on the Theory and Application of Cryptology and Information Security, December 5-9, 2010, Singapore. Heidelberg: Springer, 2010: 377-394.
|
| [17] |
CORON J S, MANDAL A, NACCACHE D, et al.Fully Homomorphic Encryption over the Integers with Shorter Public Keys[C]//IACR. 31st Annual Cryptology Conference, August 14-18, 2011, Santa Barbara, CA, USA. Heidelberg: Springer, 2011: 487-504.
|
| [18] |
CORON J S, NACCACHE D, TIBOUCHI M.Public Key Compression and Modulus Switching for Fully Homomorphic Encryption over the Integers[C]//IACR. 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 15-19, 2012, Cambridge, UK. Heidelberg: Springer, 2012: 446-464.
|
| [19] |
CHEON J H, CORON J S, KIM J, et al.Batch Fully Homomorphic Encryption over the Integers[C]//IACR. 32nd Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 26-30, 2013, Athens, Greece. Heidelberg: Springer, 2013: 315-335.
|
| [20] |
FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. .
|
| [21] |
CORON J S, LEPOINT T, TIBOUCHI M.Scale-Invariant Fully Homomorphic Encryption over the Integers[C]//IACR. 17th International Conference on Practice and Theory in Public-Key Cryptography, March 26-28, 2014, Buenos Aires, Argentina. Heidelberg: Springer, 2014: 311-328.
|
| [22] |
CHEON J H, STEHLÉ D.Fully Homomophic Encryption over the Integers Revisited[C]//IACR. 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 26-30, 2015, Sofia, Bulgaria. Heidelberg: Springer, 2015: 513-536.
|
| [23] |
NUIDA K, KUROSAWA K.(Batch) Fully Homomorphic Encryption over Integers for Non-Binary Message Spaces[C]//IACR. 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 26-30, 2015, Sofia, Bulgaria. Heidelberg: Springer, 2015: 537-555.
|
| [24] |
HIROMASA R, ABE M, OKAMOTO T.Packing Messages and Optimizing Bootstrapping in GSW-FHE[C]//IACR. 18th IACR International Conference on Practice and Theory in Public-Key Cryptography, March 30-April 1, 2015, Gaithersburg, MD, USA. Heidelberg: Springer, 2015: 699-715.
|
| [25] |
COHEN J D, FISCHER M J.A Robust and Verifiable Cryptographically Secure Election Scheme[C]//IEEE. 26th Annual Symposium on Foundations of Computer Science, October 21-23, 1985, Portland, OR, USA. New Jersey: IEEE, 1985: 372-382.
|
| [26] |
HOWGRAVE-GRAHAM N. Approximate Integer Common Divisors[EB/OL]. .
|
| [27] |
GENTRY C, HALEVI S.Implementing Gentry's Fully-Homomorphic Encryption Scheme[C]//IACR. 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 15-19, 2011, Tallinn, Estonia. Heidelberg: Springer, 2011: 129-148.
|
| [28] |
BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V.(Leveled) Fully Homomorphic Encryption without Bootstrapping[J]. Acm Transactions on Computation Theory, 2011, 18(3): 169-178.
|
| [29] |
CHEN Yuanmi, NGUYEN P Q.Faster Algorithms for Approximate Common Divisors: Breaking Fully-Homomorphic-Encryption Challenges over the Integers[C]//IACR. 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 15-19, 2012, Cambridge, UK. Heidelberg: Springer, 2015: 502-519.
|
| [30] |
BRAKERSKI Z.Fully Homomorphic Encryption without Modulus Switching from Classical GapSVP[C]//IACR. 32nd Annual Cryptology Conference, August 19-23, 2012, Santa Barbara, CA, USA. Heidelberg: Springer, 2015: 868-886.
|
| [31] |
REGEV O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography[J]. Journal of the Acm, 2005, 56(6): 84-93.
|
| [32] |
王志刚,马春光,史晓倩. 基于Binary LWE的全同态加密方案研究[J]. 信息网络安全,2015(7):41-50.
|
 )
)