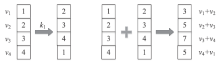
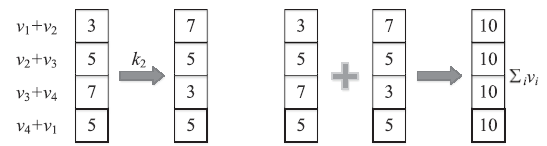
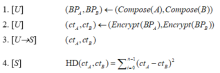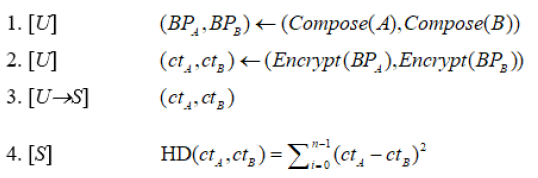| [1] |
BELGUECHI R, CHERRIER E, ALIMI V, et al.An Overview on Privacy Preserving Biometrics[M]. Recent Application in Biometrics. Croatia: InTech, 2014.
|
| [2] |
RATHA N K,CONNELL J H, BOLLE R M.Enhancing Security and Privacy in Biometrics-based Authentication Systems[J]. Ibm Systems Journal, 2001, 40(3): 614-634.
|
| [3] |
JUELS A, SUDAN M.A Fuzzy Vault Scheme[J]. Designs Codes & Cryptography, 2006, 38(2): 237-257.
|
| [4] |
WATTENBERG M, WATTENBERG M.A Fuzzy Commitment Scheme[C] //ACM. The 6th ACM Conference on Computer and Communications Security, November 1-4,1999, Singapore. New York: ACM, 1999: 28-36.
|
| [5] |
BLANTON M, GASTI P.Secure and Efficient Protocols for Iris and Fierprint Identification[C] // LNCS.Proc. of the 16thESORICS, September 12-14, 2011, Leuven, Belgium. Berlin: Springer, 2011: 190-209.
|
| [6] |
DAMGARD I, GEISLER M, KROIGARD M.Homomorphic Encryption and Secure Comparison[J]. Journal of Applied Cryptography, 2008, 1(1): 22-31.
|
| [7] |
KULKARNI R, NAMBOODIRI A.Secure Hamming Distance Based Biometric Authentication[C] // IEEE.International Conference on Biometrics, June 4-7, 2013, Madrid, Spain. New York: IEEE, 2013: 1-6.
|
| [8] |
GENTRY, CRAIG.Fully Homomorphic Encryption Using Ideal Lattices[J]. Stoc, 2009 , 9(4) :169-178.
|
| [9] |
KARABAT C, KIRAZ M, ERDOGAN H,et al.THRIVE: Threshold Homomorphic Encryption Based Secure and Privacy Preserving Biometric Verification System[J]. Eurasip Journal on Advances in Signal Processing, 2015, 2015(1): 1-18.
|
| [10] |
SHA-3 Standard: Permutation-based Hash and Extendable-output Functions[S]. Gaithersburg: NIST, 2015.
|
| [11] |
FAN J, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption [EB/OL]. .
|
| [12] |
CHEN H, LAINE K, PLAYER R. Simple Encrypted Arithmetic Library - SEAL v2.1 [EB/OL]. , 2017-5-18.
|
| [13] |
BRAKERSKI Z, GENTRY C, HALEVI S.Packed Ciphertexts in LWE-Based Homomorphic Encryption[M]. Public-Key Cryptography - PKC 2013. Berlin: Springer Berlin Heidelberg, 2013.
|
| [14] |
SMART N P, VERCAUTEREN F.Fully Homomorphic SIMD Operations[J]. Designs, Codes and Cryptography, 2014, 71(1): 57-81.
|
| [15] |
DENG Jing, XU Chunxiang, YANG Haomiao.A Secure Computation Scheme of Inner Product Based on Fully Homomorphic Encryption[J].Journal of University of Electronic Science and Technology of China, 2016, 45(5): 808-811.
|
|
邓江,许春香,杨浩淼. 一种全同态加密的安全内积计算方案[J]. 电子科技大学学报,2016,45(5):808-811.
|
| [16] |
THAVALENGAL S,BIGIOI P, CORCORAN P.Iris Authentication in Handheld Devices - Considerations for Constraint-free Acquisition[J]. IEEE Transactions on Consumer Electronics, 2015, 61(2): 245-253.
|
| [17] |
C. A. of Science-Institute of Automation. CASIA Iris Database [EB/OL]. .
|
| [18] |
MASEK L, KOVESI P. MATLAB Source Code for A Biometric Identification System Based on Iris Patterns [EB/OL]. .
|
| [19] |
TIAN Qichuan, LIU Zhengguang.Survey of Iris Recognition[J]. Application Research of Computers, 2008, 25(5): 1295-1300.
|
|
田启川,刘正光. 虹膜识别综述[J]. 计算机应用研究,2008,25(5):1295-1300.
|
| [20] |
ALBRECHT M R.On Dual Lattice Attacks Against Small-secret LWE and Parameter Choices in HElib and SEAL[C] // IACR. International Conference on the Theory and Applications of Cryptographic Techniques, April 30 - May 4, 2017, Paris, France. Berlin: Springer, 2017: 103-129.
|
|
(2)
|
 ), Kefei CHEN3
), Kefei CHEN3