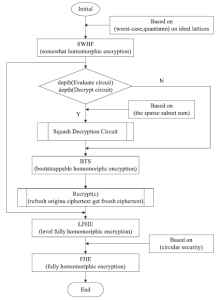
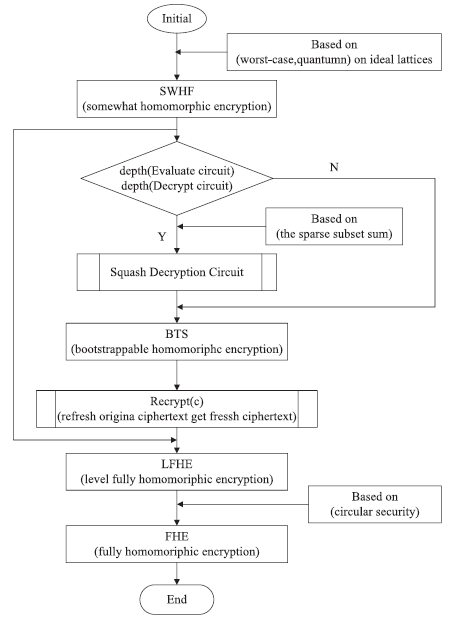
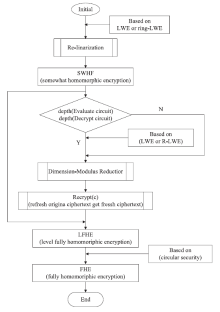
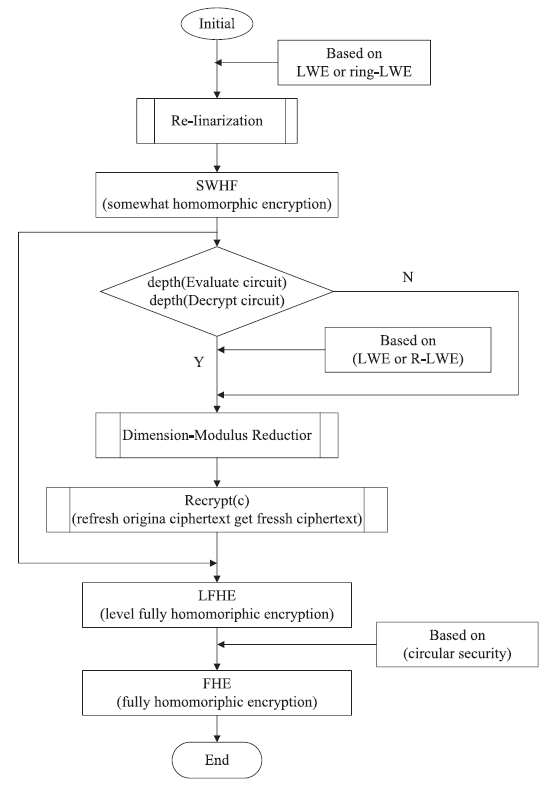
| [1] |
RIVEST R L, ADLEMAN L, DERTOUZOS M L.On data banks and privacy homomorphisms[J]. Foundations of Secure Computation, 1978: 169-179.
|
| [2] |
GOLDWASSER S, MICALI S.Probabilistic encryption[J]. Journal of Computer and System Sciences, 1984, 28(2): 270-299.
|
| [3] |
PAILLIER P.Public-key cryptosystems based on composite degree residuosity classes[J]. Advances in Cryptology-Eurocrypt, 1999: 223-238.
|
| [4] |
DAMGARD I, JURIK M.A generalisation, a simplification and some applications of paillier’s probabilistic public-key system[J]. Public Key Cryptography, 2001: 119-136.
|
| [5] |
BONEH D, GOH E, NISSIM K.Evaluating 2-DNF formulas on ciphertexts[C]//Second Theory of Cryptography Conference, Cambridge, 2005, 325-341.
|
| [6] |
GENTRY C.Fully homomorphic encryption using ideal lattices[J]. Proc Stoc, 2009, 2011, (4):169-178.
|
| [7] |
SMART N P, VERCAUTEREN F.Fully homomorphic encryption with relatively small key and ciphertext sizes[C]//13th International Conference on Practice and Theory in Public Key Cryptography, Paris, 2010: 420-443.
|
| [8] |
STEHLÉ D, STEINFELD R.Faster fully homomorphic encryption[C]//16th International Conference on the Theory and Application of Cryptology and Information Security, 2010: 377-394.
|
| [9] |
BRAKERSKI Z, VAIKUNTANATHAN V.Fully homomorphic encryption from ring-LWE and security for key dependent messages[C]//31st Annual Cryptology Conference, Santa, 2011, 505-524.
|
| [10] |
GENTRY C, HALEVI S.Fully Homomorphic Encryption without Squashing Using Depth-3 Arithmetic Circuits[J]. Foundations of Computer Science Annual Symposium on, 2011, 47(10): 107-109.
|
| [11] |
DIJK M, GENTRY C, HALEVI S, VAIKUNTANATHAN V.Fully homomorphic encryption over the integers[C]//29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, 2010: 24-43.
|
| [12] |
BRAKERSKI Z, VAIKUNTANATHAN V.Efficient Fully Homomorphic Encryption from (Standard) LWE[C]//Foundations of Computer Science, IEEE Annual Symposium on. IEEE, 2011: 97-106.
|
| [13] |
GENTRY C, HALEVI S, PEIKERT C, et al.Ring Switching in BGV-Style Homomorphic Encryption[C]//8th International Conference, SCN 2012, Amalfi, 2012: 19-37.
|
| [14] |
BRAKERSKI Z, GENTRY C, HALEVI S.Packed Ciphertexts in LWE-based Homomorphic Encryption[J]. Lecture Notes in Computer Science, 2013: 1-13.
|
| [15] |
BAI S, STEVEN D.Lattice Decoding Attacks on Binary LWE[C]// 19th Australasian Conference on Information Security and Privacy, Wollongong, 2014: 322-337.
|
| [16] |
REGEV O.Lattice-based cryptography[C]//26th Annual International Cryptology Conference, Santa Barbara, 2006: 131-141.
|
| [17] |
吕海峰,丁勇,代洪艳,等. LWE上的全同态加密方案研究[J]. 信息网络安全,2015,(1):32-38.
|
| [18] |
GENTRY C, HALEVI S, SMART P.Fully Homomorphic Encryption with Polylog Overhead[C]//31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, 2012: 465-482.
|
| [19] |
BRAKERSKI Z. Fully Homomorphic Encryption without Modulus Switching from Classical GapSVP[R]. stanford edu, Advances in Cryptology-CRYPTO 2012 Lecture Notes in Computer Science, 20120518:231322, 2012.
|
| [20] |
REGEV O.On lattices, learning with errors, random linear codes, and cryptography[J]. Journal of the Acm, 2005, 56(6):84-93.
|
 ), MA Chun-guang2, SHI Xiao-qian1
), MA Chun-guang2, SHI Xiao-qian1