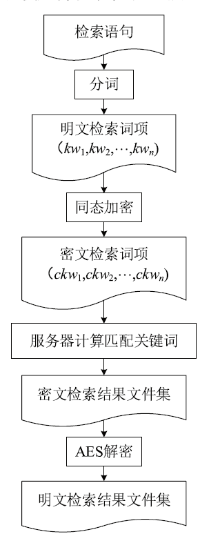
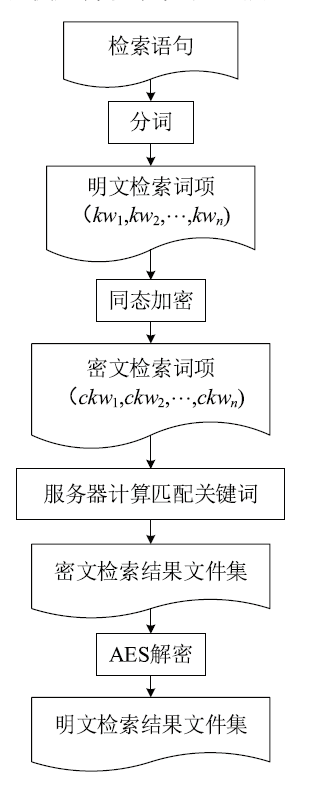
| [1] |
FENG Dengguo, ZHANG Min, ZHANG Yan, et al.Study on Cloud Computing Security[J]. Journal of Software, 2011, 22(1): 71-83.
|
|
冯登国,张敏,张妍,等. 云计算安全研究[J]. 软件学报,2011,22(1):71-83.
|
| [2] |
FENG Chaosheng, QIN Zhiguang, YUAN Ding.Techniques of Secure Storage for Cloud Data[J]. Chinese Journal of Computers, 2015, 38(1): 150-163.
|
|
冯朝胜,秦志光,袁丁. 云数据安全存储技术[J]. 计算机学报,2015,38(1):150-163.
|
| [3] |
GONG Changqing, XIAO Yun, LI Mengfei, et al.Summary of Cloud Computing Security Research[J]. Journal of Shenyang Aerospace Ace University, 2017, 34(4): 1-17.
|
|
拱长青,肖芸,李梦飞,等. 云计算安全研究综述[J]. 沈阳航空航天大学学报,2017,34(4):1-17.
|
| [4] |
BOKHARI M U, MAKKI Q, TAMANDANI Y K.A Survey on Cloud Computing[J]. International Journal on Computer Science & Engineering, 2018, 5(6): 302-311.
|
| [5] |
CACHIN C, KEIDAR I, SHRAER A.Trusting the Cloud[J]. Acm Sigact News, 2009, 40(2): 81-86.
|
| [6] |
TAKABI H, JOSHI J B D, AHN G J. Security and Privacy Challenges in Cloud Computing Environments[J]. IEEE Security & Privacy, 2010, 8(6): 24-31.
|
| [7] |
SINGH A, CHATTERJEE K. Cloud Security Issues and Challenges: A Survey[EB/OL]. , 2018-2-11.
|
| [8] |
WANG Wenxu, ZHANG Jian, CHANG Qing, et al.Research on the Security Problem of Cloud Computing Virtualization Platform[J]. Netinfo Security, 2016, 16(9): 163-168.
|
|
王文旭,张健,常青,等. 云计算虚拟化平台安全问题研究[J]. 信息网络安全,2016,16(9):163-168.
|
| [9] |
XIA Zhihua, CHEN Li, SUN Xingming, et al.A Multi-keyword Ranked Search over Encrypted Cloud Data Supporting Semantic Extension[J]. International Journal of Multimedia & Ubiquitous Engineering, 2016, 11(8): 107-120.
|
| [10] |
NA Haiyang, YANG Geng, SHU Xiaowei.Multi-keyword Ranked Search Scheme over Encrypted Cloud Data[J]. Computer Science, 2017, 44(1): 149-154.
|
|
那海洋,杨庚,束晓伟. 基于B+树的多关键字密文排序检索方法[J]. 计算机科学,2017,44(1):149-154.
|
| [11] |
YAN Xiaolong, PANG Xiaoqiong, REN Mengqi.Multi-keyword Ranked Search Method Supporting Dynamic Update[J]. Computer Engineering and Design, 2018, 39(4): 901-906.
|
|
严小龙,庞晓琼,任孟琦. 支持动态更新的多关键词密文排序检索[J]. 计算机工程与设计,2018,39(4):901-906.
|
| [12] |
DING Wei, LIU Yongji, ZHANG Jianfeng.Chinese-keyword Fuzzy Search and Extraction over Encrypted Patent Documents[C]//IEEE. 7th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management, November 12-14, 2015, Lisbon, Portugal. New Jersey: IEEE, 2015: 168-176.
|
| [13] |
WANG Yilei, BAO Wenyi, ZHAO Yang, et al.An ElGamal Encryption with Fuzzy Keyword Search on Cloud Environment[J]. International Journal of Network Security, 2016, 19(3): 481-486.
|
| [14] |
LV Qi.Research on Fuzzy Search and Access Control over Encrypted Data in Cloud Storage[D]. Nanning: Guangxi University, 2018.
|
|
吕琦. 云存储中密文的模糊搜索与访问控制研究[D].南宁:广西大学,2018.
|
| [15] |
DIJK M V, GENTRY C, HALEVI S, et al.Fully Homomorphic Encryption over the Integers[C]//Springer. 2010 Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 30-June 3, 2010, Monaco and Nice, France. Heidelberg: Springer, 2010: 24-43.
|
| [16] |
RIVEST R L, ADLEMAN L, DERTOUZOS M L. On Data Banks and Privacy Homomorphisms[EB/OL]. ,2018-2-15.
|
| [17] |
GENTRY C.Fully Homomorphic Encryption Using Ideal Lattices[J]. Stoc, 2009, 9(4): 169-178.
|
| [18] |
GENTRY C. A Fully Homomorphic Encryption Scheme[EB/OL]. , 2018-2-18.
|
| [19] |
BLACK N.Homomorphic Encryption and the Approximate GCD Problem[D]. Clemson: Clemson University, 2014.
|
| [20] |
MARINELLI F, ARAGONA R, MARCOLLA C, et al.Some Security Bounds for the Key Sizes of DGHV Scheme[J]. Applicable Algebra in Engineering Communication & Computing, 2014, 25(5): 383-392.
|
| [21] |
CORON J S, NACCACHE D, TIBOUCHI M.Public Key Compression and Modulus Switching for Fully Homomorphic Encryption over the Integers[C]//Springer. 31st Annual International Conference on Theory and Applications of Cryptographic Techniques, April 15-19, 2012, Cambridge, United Kingdom. Heidelberg: Springer, 2012: 446-464.
|
| [22] |
LI Zichen, ZHANG Fengjuan, WANG Peidong.Highly Efficient Fully Homomorphic Encryption Scheme with Shorter Public Keys[J]. Application Research of Computers, 2017, 34(2): 487-489.
|
|
李子臣,张峰娟,王培东. 一种短密钥高效全同态加密方案[J]. 计算机应用研究,2017,34(2):487-489.
|
| [23] |
CHEON J H, CORON J S, KIM J, et al.Batch Fully Homomorphic Encryption over the Integers[C]//Spring. 2013 Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 26-30, 2013, Athens, Greece. Heidelberg: Springer, 2013: 315-335.
|
| [24] |
XIE Xueshuo.An Effectively Fully Homomorphic Encryption over the Integers[D]. Jinan: Shandong University, 2014.
|
|
谢学说. 一类整数上有效的全同态加密方案[D]. 济南:山东大学,2014.
|
| [25] |
WANG Rongbing, LI Yanan, XU Hongyan, et al.Full Homomorphic Encryption Scheme over Real Number Suitable for Cloud Service Environment[J]. Netinfo Security, 2018, 19(11): 49-56.
|
|
王嵘冰,李雅囡,徐红艳,等. 适合云服务环境的实数全同态加密方案[J]. 信息网络安全,2018,19(11):49-56.
|
| [26] |
WU Zuowei, LI Taoshen.An Improved Fully Homomorphic Encryption Scheme under the Cloud Environment[C]//ACM. 12th Chinese Conference on Computer Supported Cooperative Work and Social Computing, September 22-23, 2017, Chongqing, China. New York: ACM, 2017: 251-252.
|
 ), Yin HAN2, Xuejin ZHU2
), Yin HAN2, Xuejin ZHU2