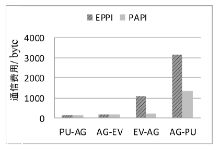
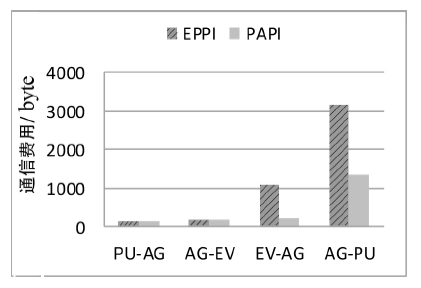
| [1] |
VALSERA-NARANJO E, SUMPER A, LLORET-GALLEGO P, et al. Electrical vehicles: State of Art and Issues for Their Connection to the Network[EB/OL].,2018-3-15.
|
| [2] |
CHAN C, CHAN K.Modern Electric Vehicle Technology[M]. New York: Oxford University Press, 2001.
|
| [3] |
LIU C,FAN J, BRANCH J, LEUNG K.Toward QoI and Energy-efficiency in Internet-of-Things Sensory Environments[J]. IEEE Transactions on Emerging Topics in Computing, 2014, 2(4): 473-487.
|
| [4] |
TONYALI S, CAKMAK O, AKKAYA K, et al.Secure Data Obfuscation Scheme to Enable Privacy-preserving State Estimation in Smart Grid AMI Networks[J]. IEEE Internet of Things Journal, 2016, 3(5): 709-719.
|
| [5] |
YANG Zhenyu, YU Shucheng, LOU Wenjing, et al.Privacy-preserving Communication and Precise Reward Architecture for V2G Networks in Smart Grid[J]. IEEE Transactions on Smart Grid, 2011, 2(4): 697-706.
|
| [6] |
WANG Huaqun, QIN Bo, WU Qianhong, et al.TPP: Traceable Privacy-preserving Communication and Precise Reward for Vehicle-to-grid Networks in Smart Grids[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(11): 2340-2351.
|
| [7] |
MAHMOUD M, SAPUTRO N, AKULA P.Privacy-preserving Power Injection over a Hybrid AMI/LTE Smart Grid Network[J]. IEEE Internet of Things Journal, 2017, 4(4): 870-880.
|
| [8] |
ZHANG Yinghui, ZHAO Jiangfan, ZHENG Dong.Efficient and Privacy-aware Power Injection over AMI and Smart Grid Slice in Future 5G Networks[J]. Mobile Information Systems, 2017(6): 1-11.
|
| [9] |
ZHANG Ping, TAO Yunzheng, ZHANG Zhi.Survey of Several Key Technologies for 5G[J]. Communications, 2016, 37(7):15-29.
|
|
张平,陶运铮,张治. 5G若干关键技术评述[J]. 通信学报,2016,37(7):15-29.
|
| [10] |
YOU Xiaohu, PAN Zhiwen, GAO Xiqi, et al.5G Mobile Communication Development Trend and Several Key Technologies[J]. SCIENTIA SINICA Informationis, 2014(5): 551-563.
|
|
尤肖虎,潘志文,高西奇,等. 5G移动通信发展趋势与若干关键技术[J]. 中国科学:信息科学, 2014(5):551-563.
|
| [11] |
PAILLIER P.Public-key Cryptosystems Based on Composite Degree Residuosity Classes[C] //Springer. EUROCRYPT’99 Proceedings of the 17th International Conference on Theory and Application of Cryptographic Techniques, May 2-6,1999,Prague,Czech Republic.Berlin: Springer, 1999: 223-238.
|
| [12] |
ZHENG Dong, ZHAO Qinglan, ZHANG Yinghui.A Brief Overview on Cryptography[J]. Xi’an University of Posts and Telecommunications, 2013, 18(6): 1-10.
|
|
郑东,赵庆兰,张应辉. 密码学综述[J]. 西安邮电大学学报, 2013,18(6):1-10.
|
| [13] |
DODIS Y, KANUKURTHI BKATZ J, et al.Robust Fuzzy Extractors and Authenticated Key Agreement from Close Secrets[J]. IEEE Transactions on Information Teroy, 2012, 58(9): 6207-6222.
|
| [14] |
XIA Xu, ZHU Xuetian, XING Yanxia, et al.Network Slicing Makes 5G Multi-scene Applications Possible[J]. Telecom World, 2017(27): 48-49.
|
|
夏旭,朱雪田,邢燕霞,等. 网络切片让5G多场景应用成为可能[J]. 通信世界, 2017(27):48-49.
|
| [15] |
KEMPTON W, TOMIC J.Vehicle-to-grid Power Fundamentals: Calculating Capacity and Net Revenue[J]. Power Sources, 2005, 144(1): 268-279.
|
| [16] |
XIA Zhuoqun, ZHAO Lei, WANG Jing, et al.Research on a Privacy Protection Method for Power Users Based on Virtual Ring Architecture[J]. Netinfo Security, 2018, 18(2): 48-53.
|
|
夏卓群, 赵磊, 王静,等. 一种基于虚拟环架构的电力用户隐私保护方法研究[J]. 信息网络安全, 2018, 18(2): 48-53.
|
 ), Tiantian ZHANG1
), Tiantian ZHANG1