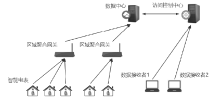
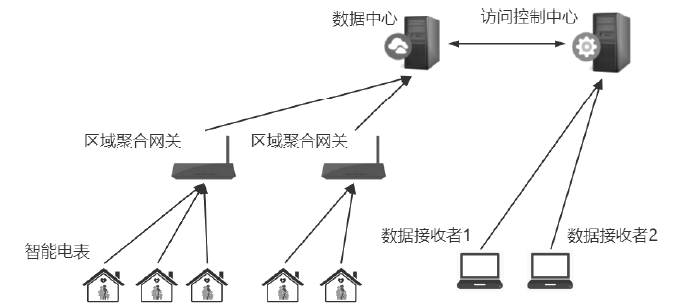
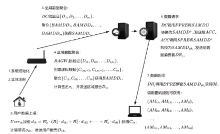
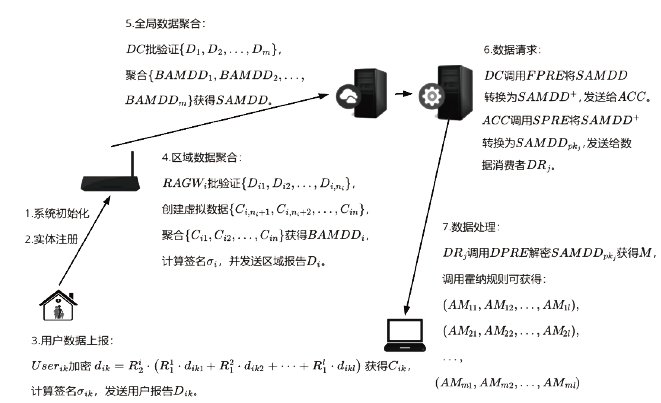
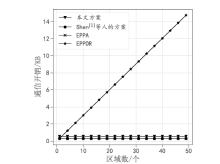
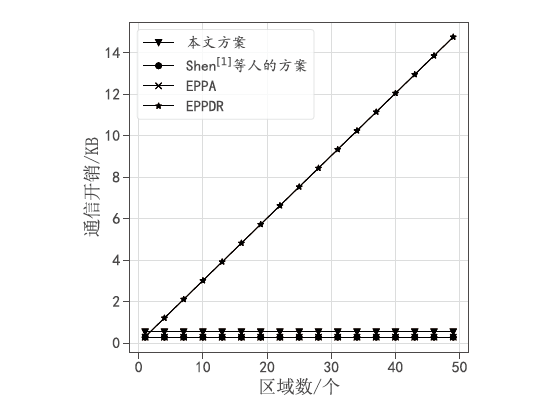
Netinfo Security ›› 2021, Vol. 21 ›› Issue (11): 28-39.doi: 10.3969/j.issn.1671-1122.2021.11.004
Previous Articles Next Articles
Privacy-preserving Data Aggregation with Fine Grained Access Control for Smart Grid
XIA Zhe1( ), LUO Bin2, XU Guibin2, XIAO Xinxiu2
), LUO Bin2, XU Guibin2, XIAO Xinxiu2
- 1. School of Computer and Artificial Intelligence, Wuhan University of Technology, Wuhan 430071, China
2. Hubei Huazhong Electric Power Technology Development Co. Ltd., Wuhan 430207, China
-
Received:2021-07-08Online:2021-11-10Published:2021-11-24 -
Contact:XIA Zhe E-mail:xiazhe@whut.edu.cn
CLC Number:
Cite this article
XIA Zhe, LUO Bin, XU Guibin, XIAO Xinxiu. Privacy-preserving Data Aggregation with Fine Grained Access Control for Smart Grid[J]. Netinfo Security, 2021, 21(11): 28-39.
share this article
| 符号 | 含义 |
|---|---|
| DC | 数据中心 |
| ACC | 访问控制中心 |
| RAGWi | i区域的区域聚合网关 |
| Userik | i区域中的第k个智能电表 |
| BAMDDi | i区域的多维聚合密文数据 |
| SAMDD | 全体多维聚合密文数据 |
| κ,q,G1,G2,P,a,b,e | 双线性映射的参数 |
| N,g,G | EDD加密的参数 |
| H | 哈希函数 |
| R1,R2 | 霍纳参数 |
| CID | 公开的计算标识符 |
| m | 总区域数 |
| n | 每个区域最大用户数 |
| ni | i区域实际用户数 |
| D | 单个维度数据的最大值 |
| dik1,⋯,dikl | Userik的多维数据 |
| dik | 经过霍纳规则降维的Userik的多维数据 |
| Cik | dik经过加密后的密文 |
| (skDC,pkDC) | 数据中心DC的公私钥对 |
| (skACC,pkACC) | 访问控制中心ACC的公私钥对 |
| PK | DC与ACC的Diffie-Hellman密钥 |
| (xi,Yi) | 区域聚合网关RAGWi用于签名的公私钥对 |
| (xik,Yik) | Userik用于签名的公私钥对 |
| [1] |
SHEN Hua, ZHANG Mingwu, SHEN Jian, et al. Efficient Privacy-preserving Cube-data Aggregation Scheme for Smart Grids[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(6):1369-1381.
doi: 10.1109/TIFS.2017.2656475 URL |
| [2] | DOMINGO-FERRER J, FARRÀS O, RIBES-GONZÁLEZ J, et al. Privacy-preserving Cloud Computing on Sensitive Data: A Survey of Methods, Products and Challenges[J]. Computer Communications, 2019, 140(5):38-60. |
| [3] |
SHEN Hua, ZHANG Mingwu, WANG Hao, et al. A Lightweight Privacy-preserving Fair Meeting Location Determination Scheme[J]. IEEE Internet of Things Journal, 2020, 7(4):3083-3093.
doi: 10.1109/JIoT.6488907 URL |
| [4] |
CHIM T, YIU S, LI V, et al. PRGA: Privacy-preserving Recording & Gateway-assisted Authentication of Power Usage Information for Smart Grid[J]. IEEE Transactions on Dependable and Secure Computing, 2014, 12(1):85-97.
doi: 10.1109/TDSC.2014.2313861 URL |
| [5] |
SHEN Gang, SU Yixin, ZHANG Danhong, et al. A Robust, Distributed, and Privacy-preserving Aggregation Scheme for Smart Grid Communications[J]. Journal of the Chinese Institute of Engineers, 2019, 42(1):54-65.
doi: 10.1080/02533839.2018.1547662 |
| [6] | ZHANG Shaomin, RONG Jieqi, WANG Baoyi. A Privacy Protection Scheme of Smart Meter for Decentralized Smart Home Environment Based on Consortium Blockchain[J]. International Journal of Electrical Power & Energy Systems, 2020, 121(10):121. |
| [7] |
CHEN Yuwen, ORTEGA J, CASTILLEJO P, et al. An Elliptic Curve-based Scalable Data Aggregation Scheme for Smart Grid[J]. IEEE Systems Journal, 2019, 14(2):2066-2077.
doi: 10.1109/JSYST.4267003 URL |
| [8] |
XU Chang, ZHANG Lühan, ZHU Liehuang, et al. Aggregate in My Way: Privacy-preserving Data Aggregation without Trusted Authority in ICN[J]. Future Generation Computer Systems, 2020, 111(10):107-116.
doi: 10.1016/j.future.2020.04.021 URL |
| [9] |
WANG Xiaodi, LIU Yining, CHOO K R. Fault Tolerant, Ulti-subset Aggregation Scheme for Smart Grid[J]. IEEE Transactions on Industrial Informatics, 2020, 17(6):4065-4072.
doi: 10.1109/TII.2020.3014401 URL |
| [10] |
ZHAO Shuai, LI Fenghua, LI Hongwei, et al. Smart and Practical Privacy-preserving Data Aggregation for Fog-based Smart Grids[J]. IEEE Transactions on Information Forensics and Security, 2020, 16(8):521-536.
doi: 10.1109/TIFS.2020.3014487 URL |
| [11] |
SHEN Hua, LIU Yajing, XIA Zhe, et al. An Efficient Aggregation Scheme Resisting on Malicious Data Mining Attacks for Smart Grid[J]. Information Sciences, 2020, 526(7):289-300.
doi: 10.1016/j.ins.2020.03.107 URL |
| [12] |
WANG Xiaodi, MENG Weizhi, LIU Yining. Lightweight Privacy-preserving Data Aggregation Protocol Against Internal Attacks in Smart Grid[J]. Journal of Information Security and Applications, 2020, 55(12):102628-102637.
doi: 10.1016/j.jisa.2020.102628 URL |
| [13] | PAILLIER P. Public-key Cryptosystems Based on Composite Degree Residuosity Classes[C]// Springer. 1999 International Conference on the Theory and Applications of Cryptographic Techniques, May 2-6, 1999, Berlin. Heidelberg: Springer, 1999: 223-238. |
| [14] | BONEH D, LYNN B, SHACHAM H. Short Signatures from the Weil Pairing[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security, December 9-13, 2001, Heidelberg, Berlin. Heidelberg: Springer, 2001: 514-532. |
| [15] | DING Wenxiu, YAN Zheng, ROBERT H D. Encrypted Data Processing with Homomorphic Re-encryption[J]. Information Sciences, 2017, 409(10):35-55. |
| [16] | BRESSON E, CATALANO D, POINTCHEVAL D. A Simple Public-key Cryptosystem with a Double Trapdoor Decryption Mechanism and its Applications[C]// Springer. 2003 International Conference on the Theory and Application of Cryptology and Information Security, November 30-December 4, 2003, Taipei, Taiwan, China. Heidelberg: Springer, 2003: 37-54. |
| [17] | BELLARE M, ROGAWAY P. Random Oracles are Practical: A Paradigm for Designing Efficient Protocols[C]// ACM. First ACM Conference on Computer & Communications Security, November 3-5, 1993, Fairfax, Virginia. New York: ACM, 1993: 62-73. |
| [18] |
LU Rongxing, LIANG Xiaohui, LI Xu, et al. EPPA: An Efficient and Privacy-preserving Aggregation Scheme for Secure Smart Grid Communications[J]. IEEE Transactions on Parallel and Distributed Systems, 2012, 23(9):1621-1631.
doi: 10.1109/TPDS.2012.86 URL |
| [19] |
LI Hongwei, LIN Xiaodong, YANG Haomiao, et al. EPPDR: An Efficient Privacy-preserving Demand Response Scheme with Adaptive Key Evolution in Smart Grid[J]. IEEE Transactions on Parallel and Distributed Systems, 2013, 25(8):2053-2064.
doi: 10.1109/TPDS.2013.124 URL |
| [1] | ZHANG Yongtang. A Secure Area Based Clustering Approach for Traffic Analysis in WSN [J]. Netinfo Security, 2021, 21(9): 80-89. |
| [2] | LIN Wenbing, ZHANG Minqing, ZHOU Neng, KONG Yongjun. Research on Technology of Reversible Data Hiding in Encrypted Domain Based on Homomorphic Encryption [J]. Netinfo Security, 2021, 21(4): 73-80. |
| [3] | LI Kunchang, SHI Runhua, LI En. Survey on Data Aggregation and Privacy Protection of User Query in Smart Grid [J]. Netinfo Security, 2021, 21(11): 65-74. |
| [4] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [5] | LI Ningbo, ZHOU Haonan, CHE Xiaoliang, YANG Xiaoyuan. Design of Directional Decryption Protocol Based on Multi-key Fully Homomorphic Encryption in Cloud Environment [J]. Netinfo Security, 2020, 20(6): 10-16. |
| [6] | ZHOU Haonan, LI Ningbo, CHE Xiaoliang, YANG Xiaoyuan. Multi-key Fully Homomorphic Encryption Scheme over Prime Power Cyclotomic Rings [J]. Netinfo Security, 2020, 20(5): 83-87. |
| [7] | FU Zhizhou, WANG Liming, TANG Ding, ZHANG Shuguang. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [8] | TANG Chunming, LIN Xuhui. Protocol of Privacy-preserving Set Intersection Computation [J]. Netinfo Security, 2020, 20(1): 9-15. |
| [9] | DONG Wei, LI Yonggang. Research on Analysis of Attacks on Smart Grid Network Based on Complex Network [J]. Netinfo Security, 2020, 20(1): 52-60. |
| [10] | Yuling LIU, Yunshan TANG, Qi ZHANG, Feng LI. Power Dispatch Software Security Situation Assessment Method [J]. Netinfo Security, 2019, 19(8): 15-21. |
| [11] | Quan ZHOU, Shumei XU, Ningbin YANG. A Privacy Protection Scheme for Smart Grid Based on Attribute-based Group Signature [J]. Netinfo Security, 2019, 19(7): 25-30. |
| [12] | Wenchao LIU, Feng PAN, Xiaoyuan YANG, Tanping ZHOU. Debug and Analysis of Fully Homomorphic Encryption Library Based on GPU [J]. Netinfo Security, 2019, 19(6): 76-83. |
| [13] | Yilin LI, Zheng YAN, Haomeng XIE. Survey of Privacy Preservation in VANET [J]. Netinfo Security, 2019, 19(4): 63-72. |
| [14] | Meihong LI, Xiaochen QI, Qianqian WU. Smart Grid Wireless Communication Data Encryption Transmission Scheme Based on Dynamic Key [J]. Netinfo Security, 2019, 19(12): 10-21. |
| [15] | Zhongyuan QIN, Yin HAN, Xuejin ZHU. Research on Ciphertext Full-text Retrieval of Cloud Storage Based on Improved DGHV Algorithm [J]. Netinfo Security, 2019, 19(1): 8-8. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||