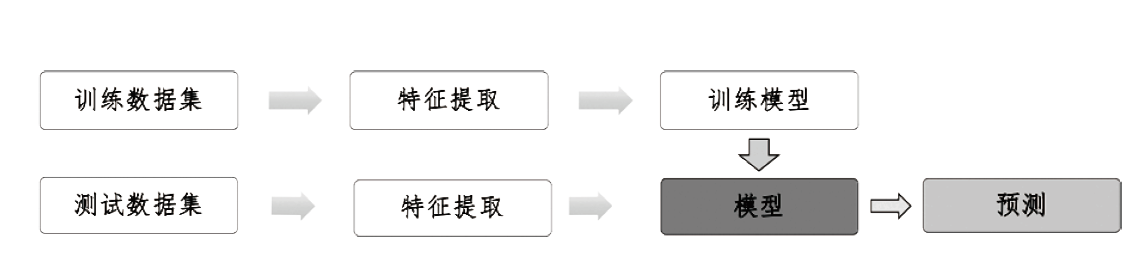
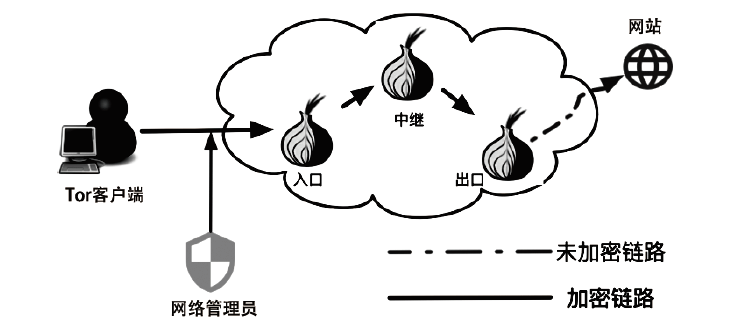
Netinfo Security ›› 2021, Vol. 21 ›› Issue (4): 39-48.doi: 10.3969/j.issn.1671-1122.2021.04.005
Previous Articles Next Articles
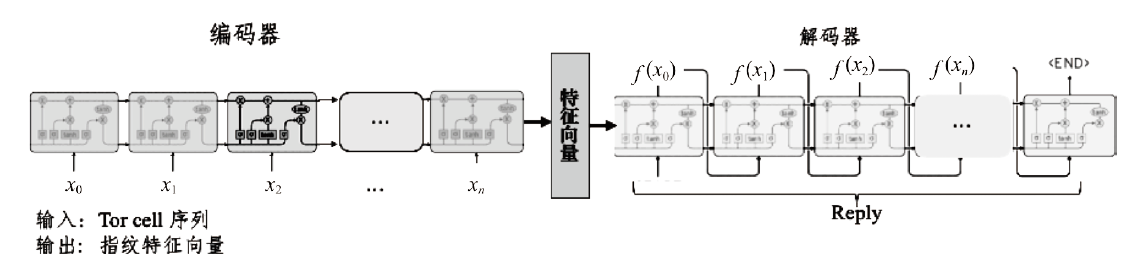
ARF-based Tor Website Fingerprint Recognition Technology
CAI Manchun, WANG Tengfei( ), YUE Ting, LU Tianliang
), YUE Ting, LU Tianliang
- Department of Information Cyber Security, People’s Public Security University of China, Beijing 100076, China
-
Received:2020-11-03Online:2021-04-10Published:2021-05-14 -
Contact:WANG Tengfei E-mail:2018211264@stu.ppsuc.edu.cn
CLC Number:
Cite this article
CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology[J]. Netinfo Security, 2021, 21(4): 39-48.
share this article
| [1] | SHI Y, MATSUURA K. Fingerprinting Attack on the Tor Anonymity System[C]// Springer. International Conference on Information and Communications Security(ICICS), December 14-17, 2009, Beijing, China. Heidelberg: Springer, 2009: 425-438. |
| [2] | JUAREZ M, AFROZ S, ACAR G, et al. A Critical Evaluation of Website Fingerprinting Attacks[C]// ACM. Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, November 3-7, 2014, Scottsdale Arizona USA. New York: Association for Computing Machinery, 2014: 263-274. |
| [3] | DEY R, SALEM F M. Gate-variants of Gated Recurrent Unit (GRU) Neural Networks[C]// IEEE. 2017 IEEE 60th International Midwest Symposium on Circuits and Systems (MWSCAS), August 6, 2017, Medford, MA, United States. New York: IEEE, 2017: 1597-1600. |
| [4] | BHAT S, LU D, KWON A, et al. Var-cnn: A Data-efficient Website Fingerprinting Attack Based on Deep Learning[J]. Proceedings on Privacy Enhancing Technologies, 2019,19(4):292-310. |
| [5] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, October 15-19, 2018, Toronto Canada. New York: Association for Computing Machiner, 2018: 1928-1943. |
| [6] | HINTZ A. Fingerprinting Websites Using Traffic Analysis[EB/OL]. https://link.springer.com/chapter/10.1007/3-540-36467-6_13, 2020-10-08. |
| [7] | LU Liming, CHANG E C, CHAN M C. Website Fingerprinting and Identification Using Ordered Feature Sequences[C]// Springer. European Symposium on Research in Computer Security. September 20-22, 2010, Athens, Greece. Heidelberg: Springer, 2010: 199-214. |
| [8] | HERRMANN D, WENDOLSKY R, FEDERRATH H. Website Fingerprinting: Attacking Popular Privacy Enhancing Technologies with the Multinomial Naïve-bayes Classifier[C]// ACM. Proceedings of the 2009 ACM Workshop on Cloud Computing Security, November 13-15, 2009, Chicago Illinois, USA. New York: Association for Computing Machinery, 2009: 31-42. |
| [9] | PANCHENKO A, NIESSEN L, ZINNEN A, et al. Website Fingerprinting in Onion Routing Based Anonymization Networks[C]// ACM. Proceedings of the 10th Annual ACM Workshop on Privacy in the Electronic Society. October 15-17, 2011, Chicago Illinois, USA. New York: Association for Computing Machinery, 2011: 103-114. |
| [10] | CAI Xiang, ZHANG Xincheng, JOSHI B, et al. Touching From a Distance: Website Fingerprinting Attacks and Defenses[C]// ACM. Proceedings of the 2012 ACM Conference on Computer and Communications Security. October 7-9, 2012, Raleigh North Carolina, USA. New York: Association for Computing Machinery, 2012: 605-616. |
| [11] | WANG Tao, CAI Xiang, NITHYANAND, et al. Effective Attacks and Provable Defenses against Website Fingerprinting[C]// USENIX. Usenix Conference on Security Symposium, August 16-18, 2014, San Diego, Berkeley. New York: USENIX Association, 2014: 143-157. |
| [12] | RIMMER V, PREUVENEERS D, JUAREZ M, et al. Automated Website Fingerprinting through Deep Learning[EB/OL]. https://arxiv.org/pdf/1708.06376.pdf, 2020-10-02. |
| [13] | RAHMAN M S, SIRINAM P, MATHEWS N, et al. Tik-Tok: The Utility of Packet Timing in Website Fingerprinting Attacks[J]. Proceedings on Privacy Enhancing Technologies, 2020,20(3):5-24. |
| [14] | HE Xiaomin, WANG Jin, HE Yueying, et al. A Deep Learning Approach for Website Fingerprinting Attack[C]// IEEE. 2018 IEEE 4th International Conference on Computer and Communications (ICCC), December 10, 2018, Chengdu, China. New York: IEEE, 2018: 1419-1423. |
| [15] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, October 15-19 ,2018, Toronto, Canada. New York: Association for Computing Machiner, 2018: 1928-1943. |
| [16] | MA Chencheng, DU Xuehui, CAO Lifeng, et al. Burst-analysis Website Fingerprinting Attack Based on Deep Neural Network[J]. Journal of Computer Research and Development, 2020,57(4):746-766. |
| 马陈城, 杜学绘, 曹利峰, 等. 基于深度神经网络burst特征分析的网站指纹攻击方法[J]. 计算机研究与发展, 2020,57(4):746-766. | |
| [17] | WANG Xudong, YU Xiangzhan, ZHANG Hongli. Research on Traffic Identification Technology for Unknown Protocols[J]. Netinfo Security, 2019,19(10):74-83. |
| 王旭东, 余翔湛, 张宏莉. 面向未知协议的流量识别技术研究[J]. 信息网络安全, 2019,19(10):74-83. | |
| [18] | ATTARIAN R, ABDI L, HASHEMI S. AdaWFPA: Adaptive Online Website Fingerprinting Attack for Tor Anonymous Network: A Stream-wise Paradigm[J]. Computer Communications, 2019,19(148):74-85. |
| [19] | BIFET A, READ J, PFAHRINGER B, et al. CD-MOA: Change Detection Framework for Massive Online Analysis[C]// Springer. International Symposium on Intelligent Data Analysis, October 17-19, 2013, London, England. Heidelberg: Springer, 2013: 92-103. |
| [20] | WANG Tao, GOLDBERG I. Improved Website Fingerprinting on Tor[C]// ACM. Proceedings of the 12th ACM Workshop on Workshop on Privacy in the Electronic Society, November 5-7, 2013, Berlin, Germany. New York: Association for Computing Machiner, 2013: 201-212. |
| [21] |
GOMES H M, BIFET A, READ J, et al. Adaptive Random Forests for Evolving Data Stream Classification[J]. Machine Learning, 2017,106(9-10):1469-1495.
doi: 10.1007/s10994-017-5642-8 URL |
| [22] |
COHEN J. A Coefficient of Agreement for Nominal Scales[J]. Educational and Psychological Measurement, 1960,20(1):37-46.
doi: 10.1177/001316446002000104 URL |
| [23] | MONTIEL J, READ J, BIFET A, et al. Scikit-multiflow: A Multi-output Streaming Framework[J]. The Journal of Machine Learning Research, 2018,19(1):2915-2914. |
| [24] | ALEXA. Alexa-actionable Analytics for the Web[EB/OL]. http://www.alexa.com, 2020-10-02. |
| [25] | JUAREZ M. Tor Browser Crawler[EB/OL]. https://github.com/webfp/tor-browser-crawler, 2020-10-02. |
| [26] | HAYES J, DANEZIS G. K-fingerprinting: A Robust Scalable Website Fingerprinting Technique[EB/OL]. https://www.usenix.org/system/files/conference/usenixsecurity16/sec16_paper_hayes.pdf, 2020-10-02. |
| [1] | LIU Jianwei, HAN Yiran, LIU Bin, YU Beiyuan. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [2] | GUO Qiquan, ZHANG Haixia. Technology System for Security Protection of Critical Information Infrastructures [J]. Netinfo Security, 2020, 20(11): 1-9. |
| [3] | GU Zhaojun, HAO Jintao, ZHOU Jingxian. Classification of Malicious Network Traffic Based on Improved Bilinear Convolutional Neural Network [J]. Netinfo Security, 2020, 20(10): 67-74. |
| [4] | Liangchen CHEN, Baoxu LIU, Shu GAO. Research on Traffic Data Sampling Technology in Network Attack Detection [J]. Netinfo Security, 2019, 19(8): 22-28. |
| [5] | Yitao NI, Yongjia CHEN, Bogang LIN. Automatic De-obfuscation-based Malicious Webpages Detection [J]. Netinfo Security, 2019, 19(4): 37-46. |
| [6] | Liangchen CHEN, Shu GAO, Baoxu LIU, Zhigang LU. Research Status and Development Trends on Network Encrypted Traffic Identification [J]. Netinfo Security, 2019, 19(3): 19-25. |
| [7] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| [8] | Liping XU, Wenjiang HAO. Analysis and Enlightenment of US Government and Enterprise Cyber Threat Intelligence [J]. Netinfo Security, 2016, 16(9): 278-284. |
| [9] | Zehui WU, Qiang WEI. A Secure Fault Recovery Approach Using OwnShip-Proof Model for Controller Cluster of Software Defined Networks [J]. Netinfo Security, 2016, 16(12): 13-18. |
| [10] | Shi-yuan YU, San-jun CHENG. The Application of Big Data Tools in Monitoring Network Attack [J]. Netinfo Security, 2015, 15(9): 149-153. |
| [11] | LI Zhan-bao, ZHANG Wen-gui. Cyber Resilience: New Ideas of Cyber Security Development [J]. 信息网络安全, 2014, 14(9): 76-79. |
| [12] | HOU Yu-chen. Legal Protective System of Cyber Surveillance in the United States and Its Meaning to China [J]. 信息网络安全, 2014, 14(9): 189-192. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||