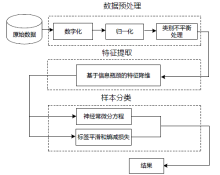
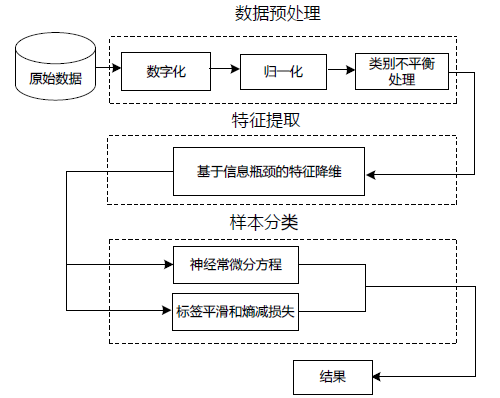
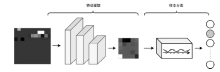
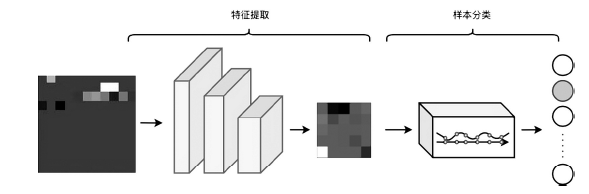
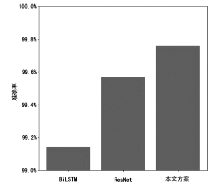
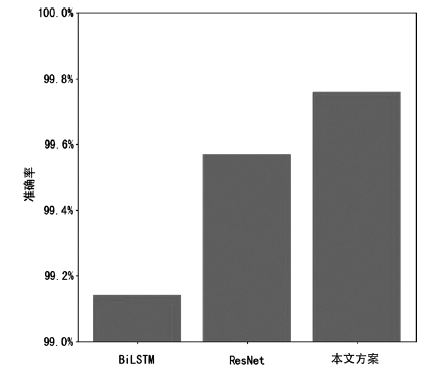
| [1] |
KANG M J, KANG J W, TANG T. Intrusion Detection System Using Deep Neural Network for in-Vehicle Network Security[EB/OL]. [2021-10-28]. https://xueshu.baidu.com/usercenter/paper/show?paperid=345b81696b59762c8cb484998e10a90e.
|
| [2] |
LOUKAS G, VUONG T. Cloud-Based Cyber-Physical Intrusion Detection for Vehicles Using Deep Learning[J]. IEEE Access, 2017(6): 3491-3508.
|
| [3] |
KIM J, SHIN N, JO S Y, et al. Method of Intrusion Detection Using Deep Neural Network[C]// IEEE. IEEE International Conference on Big Data and Smart Computing. New York: IEEE, 2017: 313-316.
|
| [4] |
YIN Chuanlong, ZHU Yuefei. A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks[J]. IEEE Access, 2017(5): 21954-21961.
|
| [5] |
ZHAO Guangzheng, ZHANG Cuixiao, ZHENG Lijuan. Intrusion Detection Using Deep Belief Network and Probabilistic Neural Network[C]// IEEE. 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC). New York:IEEE, 2017: 639-642.
|
| [6] |
WU Kehe, CHEN Zuge, LI Wei. A Novel Intrusion Detection Model for a Massive Network Using Convolutional Neural Networks[J]. IEEE Access, 2018(6): 50850-50859.
|
| [7] |
SHONE N, NGOC T N, PHAI V D, et al. A Deep Learning Approach to Network Intrusion Detection[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018, 2(1): 41-50.
doi: 10.1109/TETCI.2017.2772792
URL
|
| [8] |
KASONGO S M, SUN Yanxia. A Deep Learning Method with Filter Based Feature Engineering for Wireless Intrusion Detection System[J]. IEEE Access, 2019(7): 38597-38607.
|
| [9] |
TANG T A, MHAMDI L. Deep Recurrent Neural Network for Intrusion Detectionin SDN-Based Networks[C]// IEEE. IEEE International Conference on Network Softwarization (NetSoft). New York:IEEE, 2018: 202-206.
|
| [10] |
SALAMA M A, EID H F, RAMADAN R A, et al. Hybrid Intelligent Intrusion Detection Scheme[C]// Springer. Online World Conference on Soft Computing in Industrial Applications. Berlin: Springer, 2010: 293-303.
|
| [11] |
ZHANG Yong, CHEN Xu, JIN Lei, et al. Network Intrusion Detection: Based on Deep Hierarchical Network and Original Flow Data[J]. IEEE Access, 2019( 7): 37004-37016.
|
| [12] |
SZEGEDY C, IOFFE S, VANHOUCKE V, et al. Inception-V4, Inception-ResNet and the Impact of Residual Connections on Learning[J]. Computer Vision and Pattern Recognition, 2017: 4278-4284.
|
| [13] |
CHEN R T Q. Neural Ordinary Differential Equations[EB/OL]. [2021-10-26]. https://arxiv.org/abs/1806.07366.
|
| [14] |
ALEMI A A. Deep Variational Information Bottleneck[EB/OL]. [2021-10-05]. https://arxiv.org/abs/1612.00410.
|
| [15] |
TAVALLAEE M, BAGHERI E, LU W, et al. A Detailed Analysis of the KDD CUP 99 Data Set[C]// IEEE. 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications. New York: IEEE, 2009: 1-6.
|
| [16] |
REVATHI S, MALATHI A. A Detailed Analysis on NSL-KDD Dataset Using Various Machine Learning Techniques for Intrusion Detection[J]. International Journal of Engineering Research & Technology, 2013, 2(12): 1848-1853.
|
| [17] |
DIRO A A, CHILAMKURTI N. Distributed Attack Detection Scheme Using Deep Learning Approach for Internet of Things[J]. Future Generations Computer Systems, 2017, 82(5): 761-768.
doi: 10.1016/j.future.2017.08.043
URL
|
| [18] |
GU Jie, LU Shan. An Effective Intrusion Detection Approach Using SVM with Nave Bayes Feature Embedding[EB/OL]. [2021-10-28]. https://xueshu.baidu.com/usercenter/paper/show?paperid=11250ev0nc390vc01y1f0250fu672113.
|