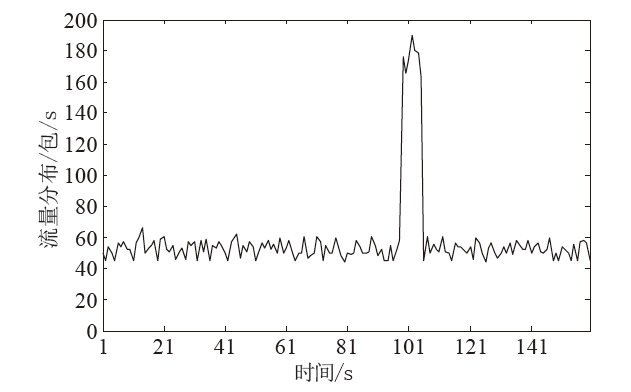
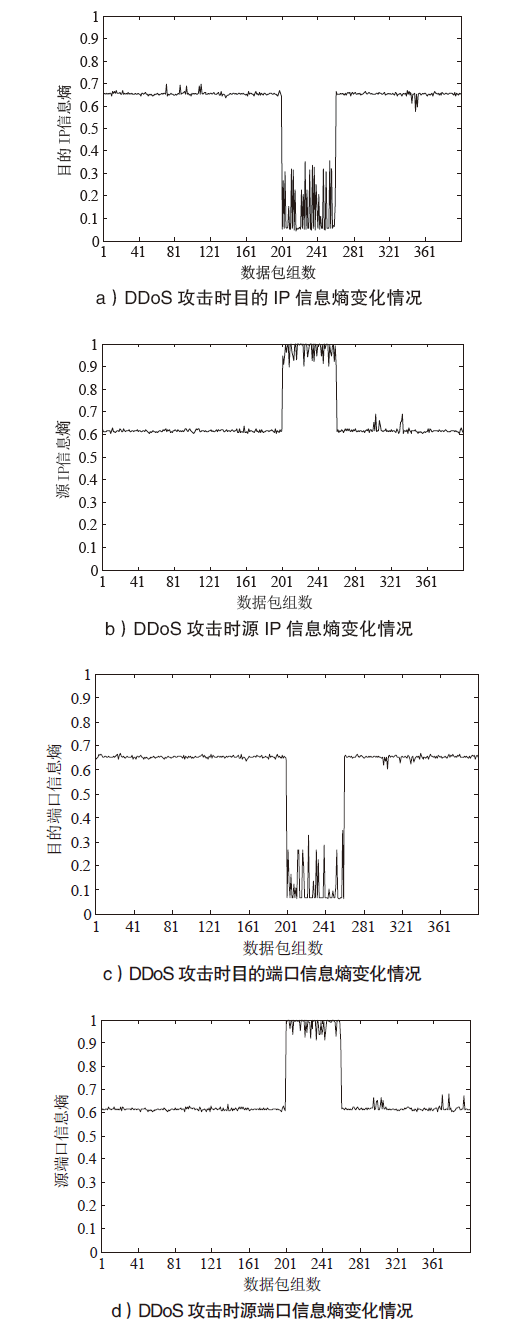
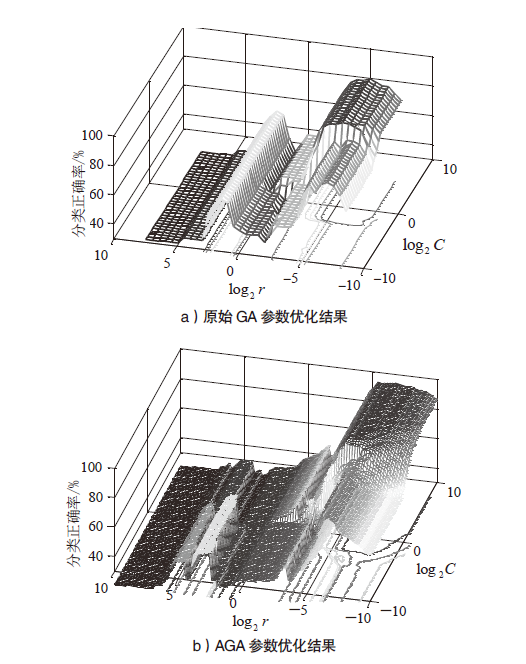
| [1] |
HONG C O, ALIH E. A Control Chart Based on Cluster-regression Adjustment for Retrospective Monitoring of Individual Characteristics[EB/OL]. https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0125835, 2015-04-29.
|
| [2] |
MARKOU M, SINGH S. Novelty Detection: A Review—part 2: Neural Network-based Approaches[J]. Signal Processing, 2003,83(12): 2499-2521.
|
| [3] |
WAGH S K, KOLHE S R. Effective Semi-supervised Approach Towards Intrusion Detection System Using Machine Learning Techniques[J]. International Journal of Electronic Security & Digital Forensics, 2015,7(3): 290-304.
|
| [4] |
TANG T A, MHAMDI L, MCLERNON D, et al. Deep Rrecurrent neural Network for Intrusion Detection in SDN-based Networks[C]//IEEE. The 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), June 25-29, 2018, Montreal, QC, Canada. NJ: IEEE, 2018: 202-206.
|
| [5] |
YAN Qiao, GONG Qingxiang, DENG F A. Detection of DDoS Attacks Against Wireless SDN Controllers Based on the Fuzzy Synthetic Evaluation Decision-making Model[J]. Ad Hoc & Sensor Wireless Networks, 2016,33(1): 275-299.
|
| [6] |
XIAO Linying, WANG Huaibin. Traffic Anomaly Detection Based on Hidden Markov Model and Conditional Entropy[J]. Journal of Tianjin University of Technology, 2019,35(5): 18-22, 28.
|
|
肖林英, 王怀彬. 基于隐马尔可夫模型和条件熵的异常流量检测方法研究[J]. 天津理工大学学报, 2019,35(5): 18-22,28.
|
| [7] |
TIAN Zhongda, LI Shujiang, WANG Yanhong, et al. Network Traffic Prediction Based on Gaussian Process RegressionCompensation Arima[J]. Journal of Beijing University of Posts and Telecommunications, 2017,40(6): 65-73.
|
|
田中大, 李树江, 王艳红, 等. 高斯过程回归补偿ARIMA的网络流量预测[J]. 北京邮电大学学报, 2017,40(6): 65-73.
|
| [8] |
MENG Yongwei, QIN Tao, ZHAO Liang, et al. Network Abnormal Traffic Detection Method Based on Residual Analysis[J]. Journal of Xi'an Jiaotong University, 2020,1(54): 42-48.
|
|
孟永伟, 秦涛, 赵亮, 等. 利用残差分析的网络异常流量检测方法[J]. 西安交通大学学报, 2020,1(54): 42-48.
|
| [9] |
LIU Yating, WANG Yongcheng, QIANG Yanfei, et al. Network Traffic Anomaly Detection Based on Random Mapping and Clustering[J]. Computer Integrated Manufacturing Systems, 2019,3(36): 289-293.
|
|
刘雅婷, 王永程, 强延飞, 等. 基于随机映射与聚类的网络流量异常检测[J]. 计算机仿真, 2019,3(36): 289-293.
|
| [10] |
PENG Huijun, SUN Zhe, ZHAO Xuejian, et al. A Detection Method for Anomaly Flow in Software Defined Network[J]. IEEE Access, 2018,6(5): 27809-27817.
|
| [11] |
LATAH M, TOKER L. Towards an Efficient Anomaly-based Intrusion Detection for Software-defined Networks[J]. Iet Networks, 2018,7(6): 453-459.
|
| [12] |
DONG Shuqin, ZHANG Bin. Network Traffic Anomaly Detection Method Based on Deep Feature Learning[J]. Journal of Electronics & Information Technology, 2020,42(3): 695-702.
|
|
董书琴, 张斌. 基于深度特征学习的网络流量异常检测方法[J]. 电子与信息学报, 2020,42(3): 695-702.
|
| [13] |
LAKHINA A, CROVELLA M, DIOT C. Mining Anomalies Using Traffic Feature Distributions[J]. Computer Communication Review, 2005,35(4): 217-228.
|
| [14] |
HESTERMAN J Y, CAUCCI L, KUPINSKI M A, et al. Maximum-likelihood Estimation With a Contracting-grid Search Algorithm[J]. IEEE Transactions on Nuclear Science, 2010,57(3): 1077-1084.
doi: 10.1109/TNS.2010.2045898
URL
pmid: 20824155
|
| [15] |
LÜ Zhaoming, ZHANG Yingjiang. Abnormal Traffic Identification Based on Improved GOA-SVM Algorithm[J]. Journal of Hunan University of Science & Technology(Natural Science Edition), 2019,34(4): 90-96.
|
|
吕赵明, 张颖江 .基于改进 GOA-SVM算法的异常流量识别[J]. 湖南科技大学学报(自然科学版), 2019,34(4): 90-96.
|
| [16] |
JIN Bo. Research and Improvement of Network Abnormal Traffic Detection Algorithm[J]. Computer & Digital Engineering, 2020,48(6): 1440-1449.
|
|
金波. 关于网络异常流量检测算法的研究与改进[J]. 计算机与数字工程, 2020,48(6): 1440-1449.
|
 ), LI Jianhua1, ZHANG Yitao2, MENG Tao1
), LI Jianhua1, ZHANG Yitao2, MENG Tao1