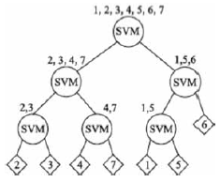
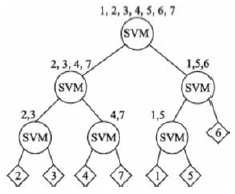
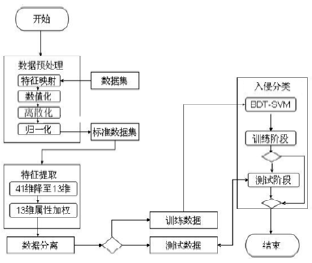
| [1] |
杨庚,许建,陈伟,等. 物联网安全特征与关键技术[J]. 南京邮电大学学报,2010,30(4):20-29.
|
| [2] |
Tsai C F, Hsu Y F, Lin C Y, et al.Intrusion Detection by Machine Learning: A Review[J]. Expert Systems with Applications, 2009, 36(10): 11994-12000.
|
| [3] |
De Leusse P, Periorellis P, Dimitrakos T, et al.Self managed security cell, a security model for the Internet of Things and Services[C]//2009 First Internatiional Conference on Future Internet. IEEE, 2009:47-52.
|
| [4] |
Mattern F, Floerkemeier C.From the internet of computers to the internet of things[C]// From Active Data Management to Event-based Systems and More. Springer Berlin Heidelberg, 2010:242-259.
|
| [5] |
曹宏鑫. 基于SVM的网络入侵检测研究[D].南京:南京理工大学,2004.
|
| [6] |
HUSH D, SCOVEL C.Polynomial-time decomposition algorithms for support vector machines[R]. LANL Technical Report LA-UR-00-3800, Los Alamos: Los Alamos National Laboratory, 2000.
|
| [7] |
OSUNA E, FREUND R, GIROSI F.Training support vector machines: an application to face detection [C]//Proceedings of CVPR’97 Puerto Rico, 1997.
|
| [8] |
林志杰, 余春艳. 改进的基于平衡二叉决策树的SVM多分类算法[J]. 小型微型计算机系统, 2014,35(5):1128-1132.
|
| [9] |
Gjorgji Madzarov, Dejan Gjorgjevikj, Iyzn Chorbev.A multiclass SVM classifier utilizing binary decision tree[J]. Informatica, 2009,33(2):233-241.
|
| [10] |
刁智华, 赵春江, 郭新宇. 一种新的基于平衡决策树的SVM多类分类算法[J]. 控制与决策, 2011,26(1):149-156.
|
| [11] |
张义荣, 鲜明, 肖顺平, 等. 一种基于粗糙集属性约简的支持向量异常入侵检测方法[J].计算机科学. 2006, 33(6): 64-68.
|
| [12] |
Randall Wilson D, Tony R Martinez.Improved Heterogeneous Distance Functions[J].Journal of Artificial Intelligence Research,1997,6(1):1-34.
|
| [13] |
张晓惠,林柏钢.基于特征选择和多分类支持向量机的异常检测[J].通信学报,2009,30(10A):68-73.
|
| [14] |
Pawlak Z.Rough Sets[J]. International Journal of Computer and Information Sciences, 1982, 11(5):341-356.
|
| [15] |
王再见. 模糊入侵检测规则的自动发现算法研究[D].合肥:中国科学技术大学,2005.
|
| [16] |
张束. 基于贝叶斯MARS的入侵检测算法研究[D].哈尔滨:哈尔滨工程大学,2006.
|
| [17] |
边肇祺,张学工.模式识别[M].第2版.北京:清华大学出版社,2000.
|
 ), LIN Bo-gang2
), LIN Bo-gang2