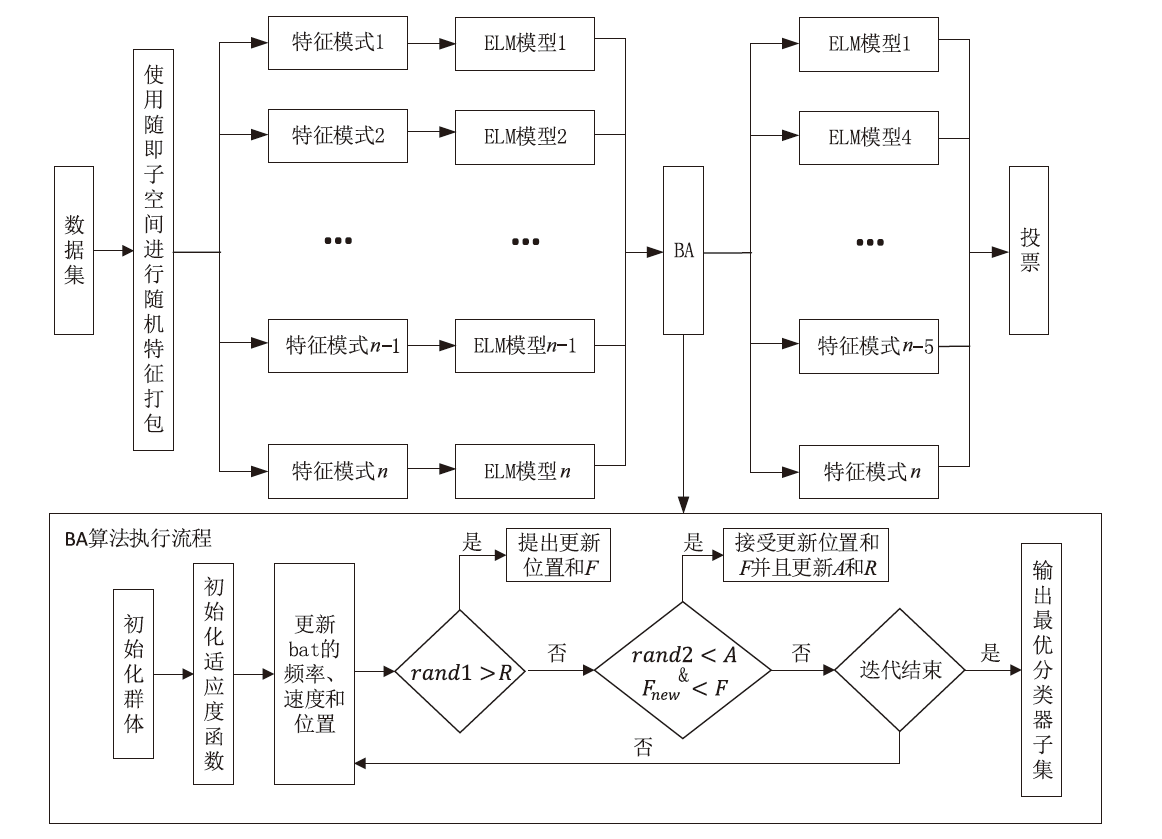
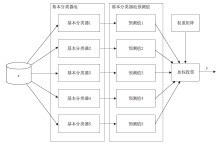
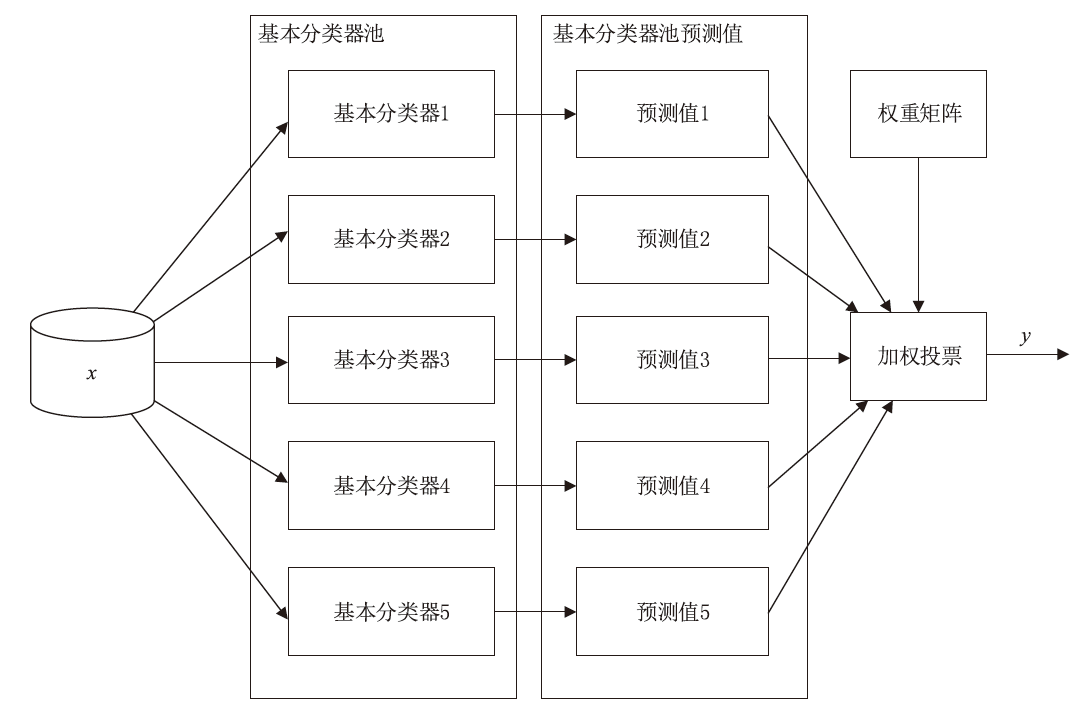
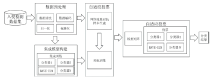
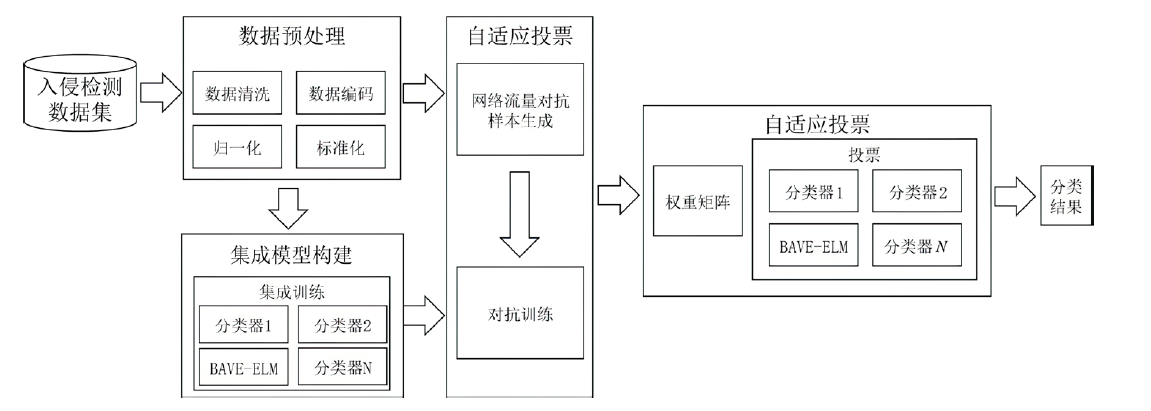
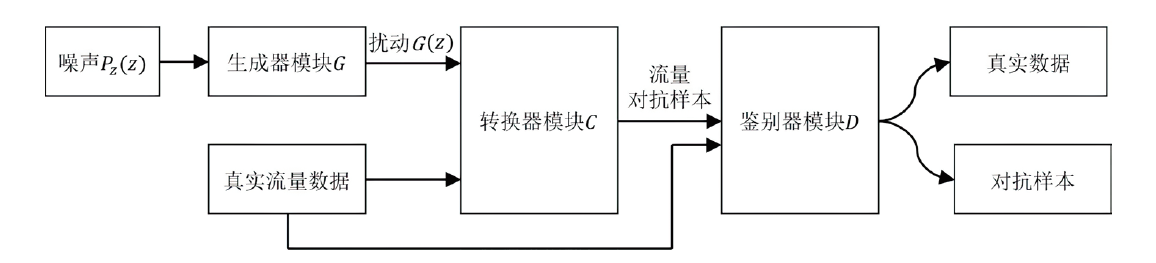
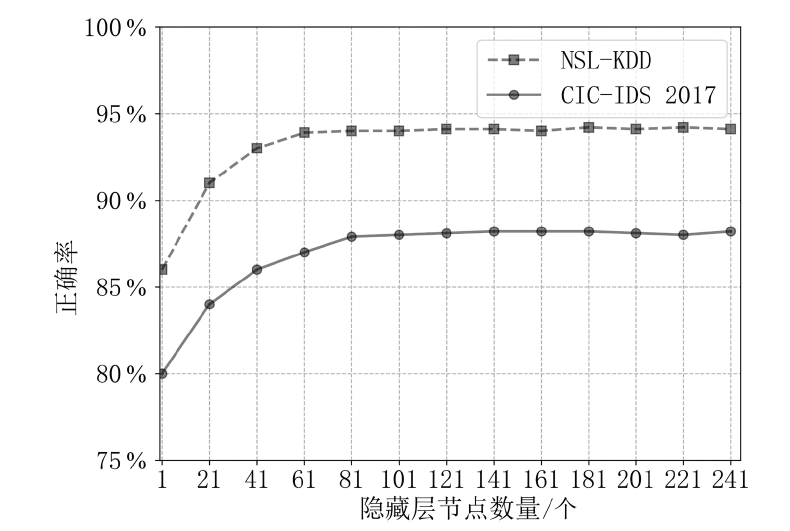
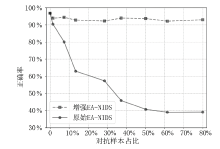
| [1] |
IMRAN M, HAIDER N, SHOAIB M, et al. An Intelligent and Efficient Network Intrusion Detection System Using Deep Learning[J]. Computers and Electrical Engineering, 2022, 99: 764-772.
|
| [2] |
DIXIT P, SILAKARI S. Deep Learning Algorithms for Cybersecurity Applications: A Technological and Status Review[J]. Computer Science Review, 2021, 39: 317-328.
|
| [3] |
SARANYA T, SRIDEVI S, DEISY C, et al. Performance Analysis of Machine Learning Algorithms in Intrusion Detection System: A Review[J]. Procedia Computer Science, 2020, 171: 1251-1260.
doi: 10.1016/j.procs.2020.04.133
URL
|
| [4] |
INJADAT M N, MOUBAYED A, NASSIF A B, et al. Machine Learning Towards Intelligent Systems: Applications, Challenges, and Opportunities[J]. Artificial Intelligence Review, 2021, 54: 3299-3348.
doi: 10.1007/s10462-020-09948-w
|
| [5] |
FARNAAZ N, JABBAR M. Random Forest Modeling for Network Intrusion Detection System[J]. Procedia Computer Science, 2016, 89: 213-217.
doi: 10.1016/j.procs.2016.06.047
URL
|
| [6] |
JIANG Hui, HE Zheng, YE Gang, et al. Network Intrusion Detection Based on PSO-XGBoost Model[J]. IEEE Access, 2020, 8: 58392-58401.
doi: 10.1109/Access.6287639
URL
|
| [7] |
WISANWANICHTHAN T, THAMMAWICHAI M. A Double-Layered Hybrid Approach for Network Intrusion Detection System Using Combined Naive Bayes and SVM[J]. IEEE Access, 2021, 9: 138432-138450.
doi: 10.1109/ACCESS.2021.3118573
URL
|
| [8] |
YANG Junzheng, LIU Feng, ZHAO YuanJie, et al. An Ensemble Learning Based Non-Intrusive Network Security Risk Assessment Prediction Model[C]//IEEE. 2022 7th IEEE International Conference on Data Science in Cyberspace (DSC). New York: IEEE, 2022: 17-23.
|
| [9] |
RING M, WUNDERLICH S, SCHEURING D, et al. A Survey of Network-Based Intrusion Detection Data Sets[J]. Computers & Security, 2019, 86: 147-167.
doi: 10.1016/j.cose.2019.06.005
URL
|
| [10] |
VOROBEYCHIK Y, KANTARCIOGLU M. Adversarial Machine Learning[J]. Synthesis Lectures on Artificial Intelligence and Machine Learning, 2018, 12(3): 160-169.
|
| [11] |
SZEGEDY C, ZAREMBA W, SUTSKEVER I, et al. Intriguing Properties of Neural Networks[C]//ICLR. The 2nd International Conference on Learning Representations. New York: ICLR, 2014: 189-201.
|
| [12] |
GOODFELLOW I J, SHLENS J, SZEGEDY C. Explaining and Harnessing Adversarial Examples[C]//ICLR. The 3rd International Conference on Learning Representations. New York: ICLR, 2015: 371-384.
|
| [13] |
CARLINI N, WAGNER D. Towards Evaluating the Robustness of Neural Networks[C]//IEEE. 2017 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2017: 39-57.
|
| [14] |
MOOSAVI-DEZFOOLI S M, FAWZI A, FROSSARD P. Deepfool:A Simple and Accurate Method to Fool Deep Neural Networks[C]//IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 2574-2582.
|
| [15] |
DONG Yingpeng, LIAO Fangzhou, PANG Tianyu, et al. Boosting Adversarial Attacks with Momentum[C]//IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2018: 9185-9193.
|
| [16] |
MARDRY A, MAKELOV A, SCHMIDT L, et al. Towards Deep Learning Models Resistant to Adversarial Attacks[C]// ICLR. The 6th International Conference on Learning Representations. New York: ICLR, 2018: 211-220.
|
| [17] |
MOGHADDASI S S, FARAJI N. A Hybrid Algorithm Based on Particle Filter and Genetic Algorithm for Target Tracking[J]. Expert Systems with Applications, 2020, 147: 188-199.
|
| [18] |
LIU Feng, WANG Hanyang, Zhang Jiaohao, et al. EvoGAN: An Evolutionary Computation Assisted GAN[J]. Neurocomputing, 2022, 469: 81-90.
doi: 10.1016/j.neucom.2021.10.060
URL
|
| [19] |
FERRAG M A, MAGLARAS L, MOSCHOYIANNIS S, et al. Deep Learning for Cyber Security Intrusion Detection: Approaches, Datasets, and Comparative Study[J]. Journal of Information Security and Applications, 2020, 50: 419-430.
|
| [20] |
LATAH M, TOKER L. An Efficient Flow-Based Multi-Level Hybrid Intrusion Detection System for Software-Defined Networks[J]. CCF Transactions on Networking, 2020, 3(3-4): 261-271.
doi: 10.1007/s42045-020-00040-z
|
| [21] |
WU Kehe, CHEN Zuge, LI Wei. A Novel Intrusion Detection Model for a Massive Network Using Convolutional Neural Networks[J]. IEEE Access, 2018, 6: 50850-50859.
doi: 10.1109/ACCESS.2018.2868993
URL
|
| [22] |
AMBUSAIDI MA, HE XiangJian, NANDA P, et al. Building an Intrusion Detection System Using a Filter-Based Feature Selection Algorithm[J]. IEEE Transactions on Computers, 2016, 65(10): 2986-2998.
doi: 10.1109/TC.2016.2519914
URL
|
 ), MU Zhiying
), MU Zhiying