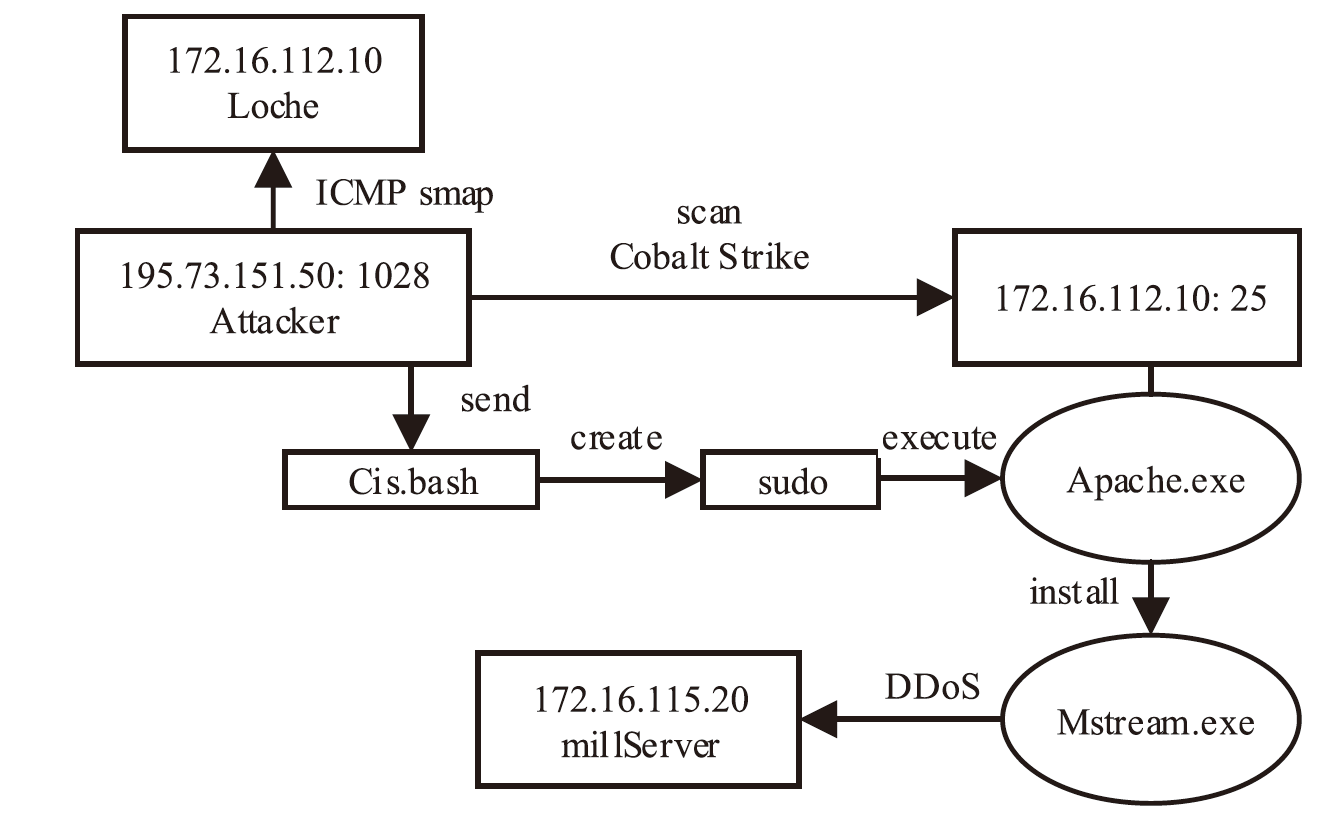
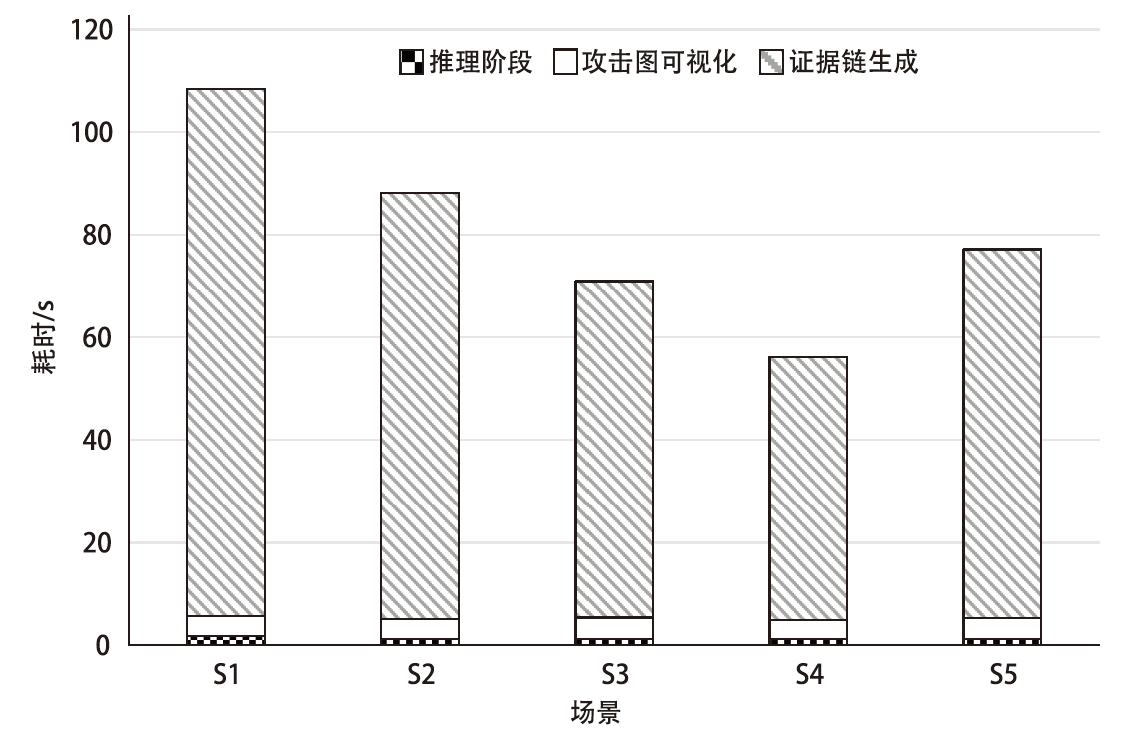
Netinfo Security ›› 2023, Vol. 23 ›› Issue (12): 59-68.doi: 10.3969/j.issn.1671-1122.2023.12.007
Previous Articles Next Articles
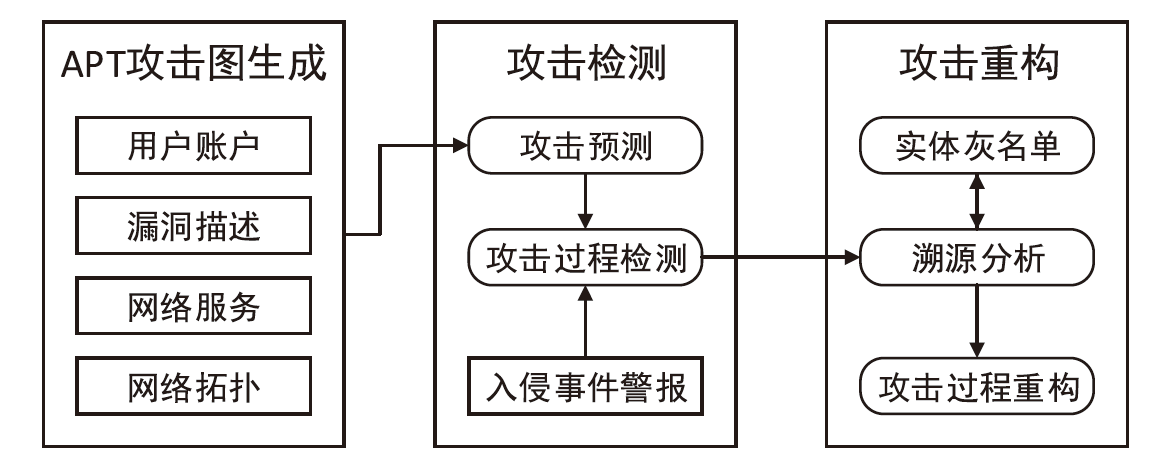
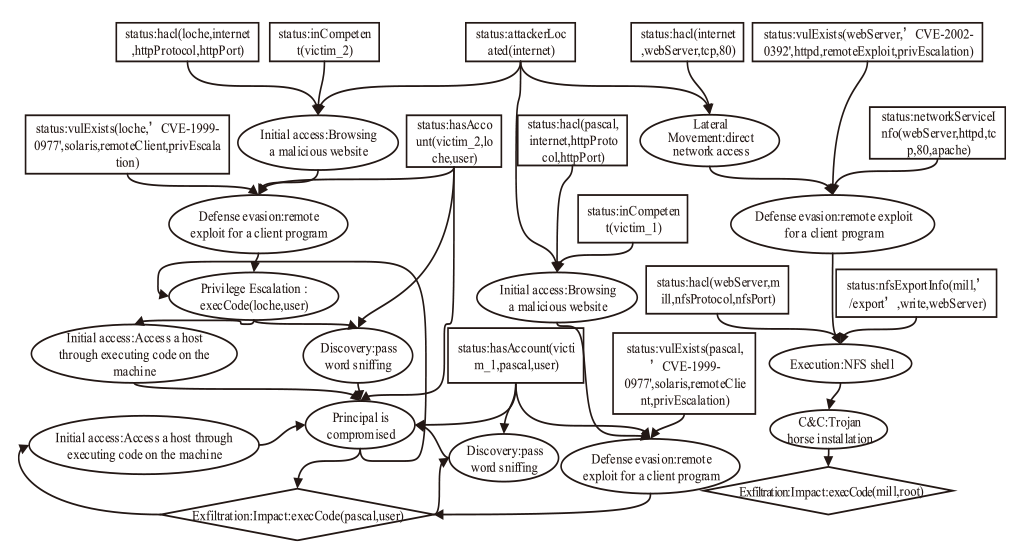
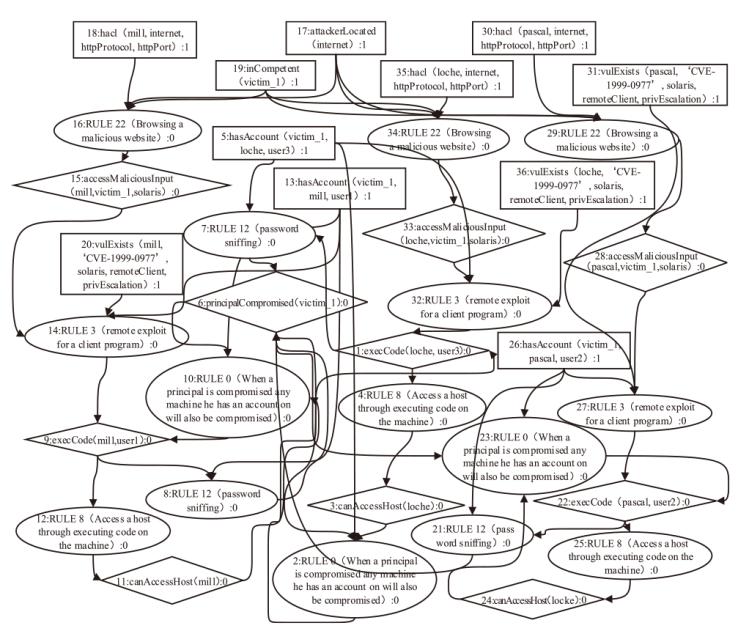
An Advanced Persistent Threat Detection Method Based on Attack Graph
GAO Qingguan1,2, ZHANG Bo3, FU Anmin3( )
)
- 1. School of Computer Science and Engineering, Southeast University, Nanjing 211189, China
2. Nanjing Saining Information Technology Co., Ltd., Nanjing 211100, China
3. School of Computer Science and Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
-
Received:2023-02-17Online:2023-12-10Published:2023-12-13
CLC Number:
Cite this article
GAO Qingguan, ZHANG Bo, FU Anmin. An Advanced Persistent Threat Detection Method Based on Attack Graph[J]. Netinfo Security, 2023, 23(12): 59-68.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.12.007
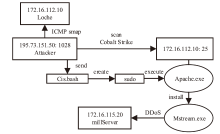
| 进程 名称 | 攻击类别 | 时间 | 路径信息 | 进程ID |
|---|---|---|---|---|
| shell | shell远程控制 | Tue 07 Mar 10:34:57-10:35:01 AM | /usr/bin/sh | 2783.2785.2789 |
| I386 | 建立外部连接 | Tue 07 Mar 10:35:01 AM | /usr/bin/i386 | 2783.2785.2790 |
| quota | 提升权限 | Tue 07 Mar 10:35:01 AM | /usr/lib/fs/ufs/quota | 2783.2785.2791 |
| cat | 文件改写 | Tue 07 Mar 10:35:01 AM | /usr/bin/cat | 2783.2785.2792 |
| 文件传送 | Tue 07 Mar 10:35:01 AM | /usr/bin/mail | 2783.2785.2793 | |
| shell | shell远程控制 | Tue 07 Mar 10:50:38 AM | /usr/bin/sh | 2783.2785.2849 |
| I386 | 建立外部连接 | Tue 07 Mar 10:50:38 AM | /usr/bin/i386 | 2783.2785.2850 |
| quota | 提升权限 | Tue 07 Mar 10:50:38 AM | /usr/lib/fs/ufs/quota | 2783.2785.2851 |
| cat | 文件改写 | Tue 07 Mar 10:50:38 AM | /usr/bin/cat | 2783.2785.2852 |
| 文件传送 | Tue 07 Mar 10:50:38 AM | /usr/bin/mail | 2783.2785.2853 | |
| mkdir | 创建目录 | Tue 07 Mar 10:50:38 AM | /usr/bin/mkdir | 2783.2785.2854 |
| rcp | 远程文件复制 | Tue 07 Mar 10:50:38 AM | /usr/bin/rcp | 2783.2785.2855 |
| chmod | 权限修改 | Tue 07 Mar 10:50:38 AM | /usr/bin/chmod | 2783.2785.2856 |
| shell | shell远程控制 | Tue 07 Mar 10:50:53 AM | /usr/bin/sh | 2783.2785.2858 |
| Server-sol | 连接木马组件 | Tue 07 Mar 10:50:54 AM | /tmp/.mstream/server-sol | 2783.2785.2859 |
| [1] | REN Yitong, XIAO Yanjun, ZHOU Yinghai, et al. CSKG4APT: A Cybersecurity Knowledge Graph for Advanced Persistent Threat Organization Attribution[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(6): 5695-5709. |
| [2] |
LI Teng, JIANG Ya, LIN Chi, et al. DeepAG: Attack Graph Construction and Threats Prediction with Bi-Directional Deep Learning[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 20(1): 740-757.
doi: 10.1109/TDSC.2022.3143551 URL |
| [3] | ALSHAMRANI A, MYNENI S, CHOWDHARY A, et al. A Survey on Advanced Persistent Threats: Techniques, Solutions, Challenges, and Research Opportunities[J]. IEEE Communications Surveys & Tutorials, 2019, 21(2): 1851-1877. |
| [4] | ADEL A, SOWMYA M, ANKUR C, et al. A Survey on Advanced Persistent Threats: Techniques, Solutions, Challenges, and Research Opportunities[J]. IEEE Communications Surveys & Tutorials, 2019, 21(2): 1851-1877. |
| [5] | CVERC. Report on the Investigation of Northwestern Polytechnical University’s Network Attack by the US NSA(Part One)[EB/OL]. (2022-09-25) [2023-02-13]. https://www.cverc.org.cn/head/zhaiyao/news20220905-NPU.htm Sept. 2022. |
| 国家计算机病毒应急处理中心. 西北工业大学遭美国NSA网络攻击事件调查报告(之一)[EB/OL]. (2022-09-25)[2023-02-13]. https://www.cverc.org.cn/head/zhaiyao/news20220905-NPU.htm. | |
| [6] | MICHAEL H. Stuxnet Worm Attack on Iranian Nuclear Facilities[EB/OL]. (2016-08-03)[2023-02-13]. http://large.stanford.edu/courses/2015/ph241/holloway1/. |
| [7] | ZHANG Yuxiang, HAN Jiujiang, LIU Jian, et al. Network Advanced Threat Detection System Based on Event Sequence Correlation Under ATT&CK Framework[J]. Computer Science, 2023, 50(z1): 700-706. |
| 张宇翔, 韩久江, 刘建, 等. ATT&CK框架下基于事件序列关联的网络高级威胁检测系统[J]. 计算机科学, 2023, 50(z1): 700-706. | |
| [8] | XU Liping, HAO Wenjiang. Analysis and Enlightenment of US Government and Enterprise Cyber Threat Intelligence[J]. Netinfo Security, 2016, 16(9): 278-284. |
| 徐丽萍, 郝文江. 美国政企网络威胁情报现状及对我国的启示[J]. 信息网络安全, 2016, 16(9): 278-284. | |
| [9] | HASSAN W U, BATES A, MARINO D. Tactical Provenance Analysis for Endpoint Detection and Response Systems[C]// IEEE. IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1172-1189. |
| [10] | HODAYA B, RON B, MASAKI I, et al. A Framework for Modeling Cyber Attack Techniques from Security Vulnerability Descriptions[C]// ACM. 27th ACM SIGKDD Conference on Knowledge Discovery & Data Mining. New York: ACM, 2021: 2574-2583. |
| [11] | MARTIN B, EMIL C L. Naggen:A Network Attack Graph Generation Tool-IEEE CNS 17 Poster[C]// IEEE. IEEE Conference on Communications and Network Security (CNS). New York: IEEE, 2017: 378-379. |
| [12] | JIN Zhigang, WANG Xinjian, LI Gen, et al. The Generation Method of Network Defense Strategy Combining with Attack Graph and Game Model[J]. Netinfo Security, 2021, 21(1): 1-9. |
| 金志刚, 王新建, 李根, 等. 融合攻击图和博弈模型的网络防御策略生成方法[J]. 信息网络安全, 2021, 21(1): 1-9. | |
| [13] |
LUO Zhiyong, ZHANG Yu, WANG Qing, et al. Study of SDN Intrusion Intent Identification Algorithm Based on Bayesian Attack Graph[J]. Journal on Communications, 2023, 44(4): 216-225.
doi: 10.11959/j.issn.1000-436x.2023073 |
|
罗智勇, 张玉, 王青, 等. 基于贝叶斯攻击图的SDN入侵意图识别算法的研究[J]. 通信学报, 2023, 44(4): 216-225.
doi: 10.11959/j.issn.1000-436x.2023073 |
|
| [14] | SHEYNER O, HAINES J, JHA S, et al. Automated Generation and Analysis of Attack Graphs[C]// IEEE. IEEE Symposium on Security and Privacy. New York: IEEE, 2002: 254-265. |
| [15] |
YANG Hongyu, YUAN Haihang, ZHANG Liang. Host Security Assessment Method Based on Attack Graph[J]. Journal on Communications, 2022, 43(2): 89-99.
doi: 10.11959/j.issn.1000-436x.2022030 |
|
杨宏宇, 袁海航, 张良. 基于攻击图的主机安全评估方法[J]. 通信学报, 2022, 43(2): 89-99.
doi: 10.11959/j.issn.1000-436x.2022030 |
|
| [16] | MARTIN B, RODRIGO V S, RABIH M, et al. Tracking the Bad Guys: An Efficient Forensic Methodology to Trace Multi-Step Attacks Using Core Attack Graphs[C]// IEEE. 13th International Conference on Network and Service Management (CNSM). New York: IEEE, 2017: 1-7. |
| [17] | NICHOLS W, HAWRYLAK P, HALE J, et al. Introducing Priority into Hybrid Attack Graphs[C]// ACM. 12th Annual Conference on Cyber and Information Security Research. New York: ACM, 2017: 1-4. |
| [18] | THANH H N, MASON W, MICHAEL P W, et al. Multi-Stage Attack Graph Security Games: Heuristic Strategies, with Empirical Game-Theoretic Analysis[C]// ACM. Proceedings of the 2017 Workshop on Moving Target Defense. New York: ACM, 2017: 87-97. |
| [19] | WANG Xiaofan, ZHOU Tianyang, ZHU Junhu. Network Security Assessment Based on Full Host-Based Attack Graph[C]// ACM. International Conference on Cyberspace Innovation of Advanced Technologies. New York: ACM, 2020: 230-235. |
| [20] |
GHAZO A T A, IBRAHIM M, REN Hao, et al. A2G2V: Automatic Attack Graph Generation and Visualization and Its Applications to Computer and SCADA Networks[J]. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2020, 50(10): 3488-3498.
doi: 10.1109/TSMC.6221021 URL |
| [21] | AMJAD I, STEVICA B, ALEXANDER P. Attack Graph Generation for Microservice Architecture[C]// ACM. 34th ACM/SIGAPP Symposium on Applied Computing. New York: ACM, 2019: 1235-1242. |
| [22] |
LUO Zhiyong, YANG Xu, LIU Jiahui, et al. Network Intrusion Intention Analysis Model Based on Bayesian Attack Graph[J]. Journal on Communications, 2020, 41(9): 160-169.
doi: 10.11959/j.issn.1000-436x.2020172 |
|
罗智勇, 杨旭, 刘嘉辉, 等. 基于贝叶斯攻击图的网络入侵意图分析模型[J]. 通信学报, 2020, 41(9): 160-169.
doi: 10.11959/j.issn.1000-436x.2020172 |
|
| [23] | LI Heng, WANG Yongjun, CAO Yuan. Searching Forward Complete Attack Graph Generation Algorithm Based on Hypergraph Partitioning[C]// ACM. Procedia Computer Science. New York: ACM, 2017: 27-38. |
| [24] | LI Jiyong. Network Intrusion Detection Algorithm and Simulation of Complex System in Internet Environment[EB/OL]. (2022-12-29)[2023-02-13]. https://ieeexplore.ieee.org/document/9985720. |
| [25] | ZHANG Bo, CUI Jiawei, QU Su, et al. Research Progress and Challenge of Advanced Persistent Threat and Its Reconstruction[J]. Journal of Information Security Research, 2021, 7(6): 512-519. |
| [26] | KING I J, HUANG H H. Euler: Detecting Network Lateral Movement via Scalable Temporal Graph Link Prediction[J]. ACM Transactions on Privacy and Security, 2022, 26(3): 1-36. |
| [27] |
XIONG Chunlin, ZHU Tiantian, DONG Weihao, et al. CONAN: A Practical Real-Time APT Detection System with High Accuracy and Efficiency[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 19(1): 551-565.
doi: 10.1109/TDSC.2020.2971484 URL |
| [28] | YU Le, MA Shiqing, ZHANG Zhuo, et al. ALchemist: Fusing Application and Audit Logs for Precise Attack Provenance without Instrumentation[EB/OL]. (2021-02-21)[2023-02-13]. https://www.ndss-symposium.org/wp-content/uploads/ndss2021_7A-2_24445_paper.pdf. |
| [29] | ALSAHEEL A, NAN Yuhong, MA Shiqing, et al. ATLAS: A Sequence-Based Learning Approach for Attack Investigation[C]// USENIX. 30th USENIX Security Symposium (USENIX Security 21). Berlin:USENIX, 2021: 3005-3022. |
| [30] |
WU Yafeng, XIE Yulai, LIAO Xuelong, et al. Paradise: Real-Time, Generalized, and Distributed Provenance-Based Intrusion Detection[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 20(2): 1624-1640.
doi: 10.1109/TDSC.2022.3160879 URL |
| [31] | ZENG Jun, WANG Xiang, LIU Jiahao, et al. Shadewatcher: Recommendation-guided Cyber Threat Analysis Using System Audit Records[C]// IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 489-506. |
| [32] | Aptnotes. Data[EB/OL]. (2022-03-11)[2023-02-13]. https://github.com/aptnotes/data/. |
| [33] | OU Xinming, GOVINDAVAJHALA S, APPEL A W. MulVAL: A Logic-Based Network Security Analyzer[C]// USENIX. USENIX Security Symposium. Berlin:USENIX, 2005(8): 113-128. |
| [34] | FANG Pengcheng, GAO Peng, LIU Changlin, et al. Back-Propagating: System Dependency Impact for Attack Investigation[C]// USENIX. 31st USENIX Security Symposium (USENIX Security 22). Berlin:USENIX, 2022: 2461-2478. |
| [35] | HU Erteng, FU Anmin, ZHANG Zhiyi, et al. ACTracker: A Fast and Efficient Attack Investigation Method Based on Event Causality[C]// IEEE. IEEE INFOCOM 2021-IEEE Conference on Computer Communications Work-Shops. New York: IEEE, 2021: 1-6. |
| [36] |
GHAZO A T A, IBRAHIM M, REN Hao, et al. A2G2V: Automatic Attack Graph Generation and Visualization and Its Applications to Computer and SCADA Networks[J]. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2020, 50(10): 3488-3498.
doi: 10.1109/TSMC.6221021 URL |
| [37] | LIANG Ruozhou, GAO Yue, ZHAO Xibin. APT Attack Detection Method on Traceability Map Based on Sequence Feature Extraction[J]. Scientia Sinica (Informationis), 2022, 52(8): 1463-1480. |
| 梁若舟, 高跃, 赵曦滨. 基于序列特征提取的溯源图上APT攻击检测方法[J]. 中国科学:信息科学, 2022, 52(8): 1463-1480. |
| [1] | PU Junyan, LI Yahui, ZHOU Chunjie. Cross-Domain Dynamic Security Risk Analysis Method of Industrial Control System Based on Probabilistic Attack Graph [J]. Netinfo Security, 2023, 23(9): 85-94. |
| [2] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [3] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [4] | LIU Changjie, SHI Runhua. A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning [J]. Netinfo Security, 2023, 23(4): 90-101. |
| [5] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [6] | WANG Huazhong, TIAN Zilei. Intrusion Detection Method of ICS Based on Improved CGAN Algorithm [J]. Netinfo Security, 2023, 23(1): 36-43. |
| [7] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [8] | ZHANG Xinglan, FU Juanjuan. Auxiliary Entropy Reduction Based Intrusion Detection Model for Ordinary Differential Equations [J]. Netinfo Security, 2022, 22(6): 1-8. |
| [9] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [10] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, LIU Xuefeng. Insider Threat Detection Model Based on LSTM-Attention [J]. Netinfo Security, 2022, 22(2): 1-10. |
| [11] | YIN Ying, ZHOU Zhihong, YAO Lihong. Research on LSTM-Based CAN Intrusion Detection Model [J]. Netinfo Security, 2022, 22(12): 57-66. |
| [12] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [13] | HE Hongyan, HUANG Guoyan, ZHANG Bing, JIA Damiao. Intrusion Detection Model Based on Extra Trees-recursive Feature Elimination and LightGBM [J]. Netinfo Security, 2022, 22(1): 64-71. |
| [14] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [15] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||