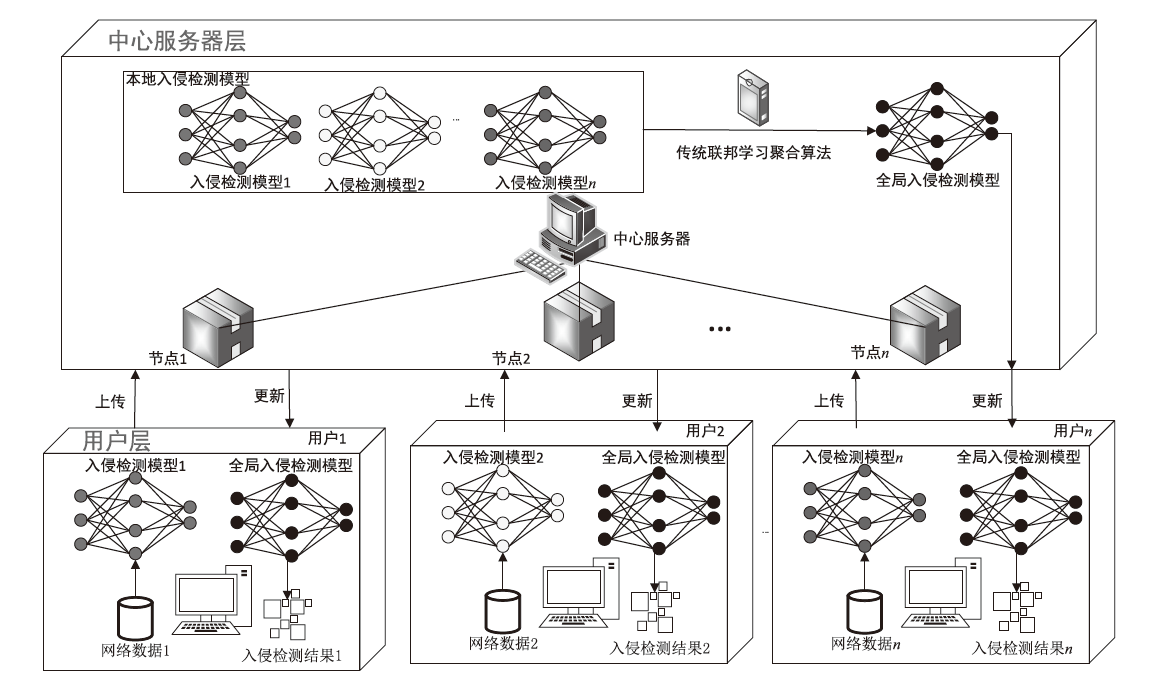
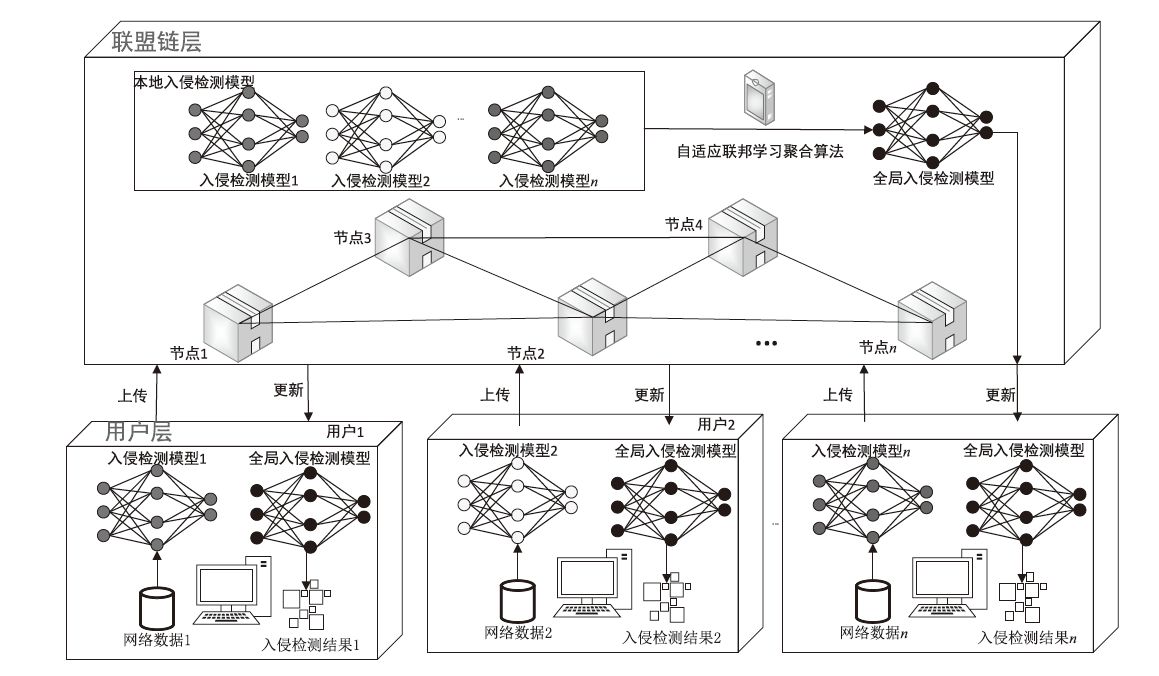
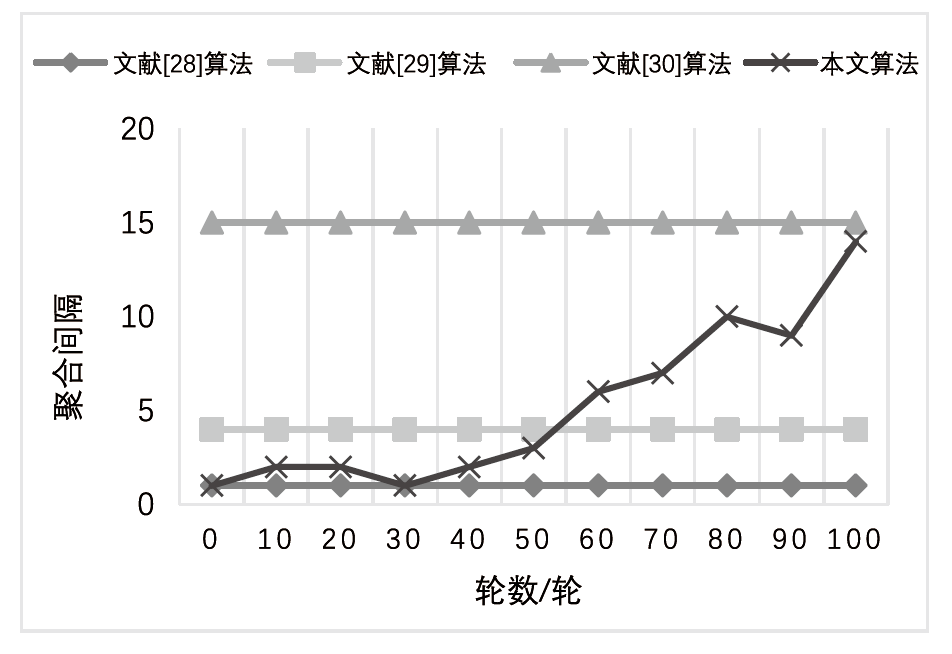
Netinfo Security ›› 2023, Vol. 23 ›› Issue (8): 76-85.doi: 10.3969/j.issn.1671-1122.2023.08.007
Previous Articles Next Articles
Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain
PENG Hanzhong1,2, ZHANG Zhujun1,2( ), YAN Liyue3, HU Chenglin3
), YAN Liyue3, HU Chenglin3
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100085, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100049, China
3. Chinese Electronics Standardization Institute, Beijing 100007, China
-
Received:2023-04-18Online:2023-08-10Published:2023-08-08 -
Contact:ZHANG Zhujun E-mail:zhangzhujun@iie.ac.cn
CLC Number:
Cite this article
PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain[J]. Netinfo Security, 2023, 23(8): 76-85.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.08.007
| [1] |
APRUZZESE G, PAJOLA L, CONTI M. The Cross-Evaluation of Machine Learning-Based Network Intrusion Detection Systems[J]. IEEE Transactions on Network and Service Management, 2022, 19(4): 5152-5169.
doi: 10.1109/TNSM.2022.3157344 URL |
| [2] | ZHANG Chunying, JIA Donghao, WANG Liya, et al. Comparative Research on Network Intrusion Detection Methods Based on Machine Learning[EB/OL]. (2022-10-15)[2023-04-05]. https://doi.org/10.1016/j.cose.2022.102861. |
| [3] |
TSAI C, HSU Y, LIN C, et al. Intrusion Detection by Machine Learning: A Review[J]. Expert Systems with Applications, 2009, 36(10): 11994-12000.
doi: 10.1016/j.eswa.2009.05.029 URL |
| [4] |
WANG Ziyue, PENG Yanjun, LI Dapeng, et al. Mmnet: A Multi-Scale Deep Learning Network for the Left Ventricular Segmentation of Cardiac Mri Images[J]. Applied Intelligence, 2022, 52(5): 5225-5240.
doi: 10.1007/s10489-021-02720-9 |
| [5] | VASILOMANOLAKIS E, KARUPPAYAH S, MÜHLHÄUSER M, et al. Taxonomy and Survey of Collaborative Intrusion Detection[J]. ACM Computing Surveys (CSUR), 2015, 47(4): 1-33. |
| [6] |
GONG Maoguo, XIE Yu, PAN Ke, et al. A Survey on Differentially Private Machine Learning[J]. IEEE Computational Intelligence Magazine, 2020, 15(2): 49-64.
doi: 10.1109/MCI.10207 URL |
| [7] | ZHANG Chen, XIE Yu, BAI Hang, et al. A Survey on Federated Learning[EB/OL]. (2022-10-15)[2023-04-05]. https://doi.org/10.1016/j.knosys.2021.106775. |
| [8] |
MOTHUKURI V, KHARE P, PARIZI R M, et al. Federated-Learning-Based Anomaly Detection for IoT Security Attacks[J]. IEEE Internet of Things Journal, 2021, 9(4): 2545-2554.
doi: 10.1109/JIOT.2021.3077803 URL |
| [9] | MA Chuan, LI Jun, DING Ming, et al. On Safeguarding Privacy and Security in the Framework of Federated Learning[J]. IEEE Network, 2020, 34(4): 242-248. |
| [10] |
MOTHUKURI V, PARIZI R M, POURIYEH S, et al. A Survey on Security and Privacy of Federated Learning[J]. Future Generation Computer Systems, 2021, 115: 619-640.
doi: 10.1016/j.future.2020.10.007 URL |
| [11] | LI Tian, SAHU A K, TALWALKAR A, et al. Federated Learning: Challenges, Methods, and Future Directions[J]. IEEE Signal Processing Magazine, 2020, 37(3): 50-60. |
| [12] |
ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain Challenges and Opportunities: A Survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352-375.
doi: 10.1504/IJWGS.2018.095647 URL |
| [13] | DIB O, BROUSMICHE K L, DURAND A, et al. Consortium Blockchains: Overview, Applications and Challenges[J]. International Journal on Advances in Telecommunications, 2018, 11: 51-64. |
| [14] |
ZHANG Weishan, LU Qinghua, YU Qiuyu, et al. Blockchain-Based Federated Learning for Device Failure Detection in Industrial IoT[J]. IEEE Internet of Things Journal, 2020, 8(7): 5926-5937.
doi: 10.1109/JIOT.2020.3032544 URL |
| [15] | ZAABAR B, CHEIKHROUHOU O, ABID M. Intrusion Detection System for IoMT through Blockchain-Based Federated Learning[C]//IEEE.2022 15th International Conference on Security of Information and Networks (SIN). New York: IEEE, 2022: 1-8. |
| [16] |
LIU Hong, ZHANG Shuaipeng, ZHANG Pengfei, et al. Blockchain and Federated Learning for Collaborative Intrusion Detection in Vehicular Edge Computing[J]. IEEE Transactions on Vehicular Technology, 2021, 70(6): 6073-6084.
doi: 10.1109/TVT.2021.3076780 URL |
| [17] | SARHAN M, LO W W, LAYEGHY S, et al. HBFL: A Hierarchical Blockchain-Based Federated Learning Framework for Collaborative IoT Intrusion Detection[EB/OL]. (2022-04-08)[2023-04-05]. https://doi.org/10.48550/arXiv.2204.04254. |
| [18] | ZHOU Wei, WANG Chao, XU Jian, et al. Decentralized Federated Learning Model for Privacy Protection Based on Blockchain[J]. Journal of Computer Research and Development, 2022, 59(11): 2423-2436. |
| 周炜, 王超, 徐剑, 等. 基于区块链的隐私保护去中心化联邦学习模型[J]. 计算机研究与发展, 2022, 59(11): 2423-2436. | |
| [19] |
TAN Rongjie, HONG Zhiyong, YU Wenhua, et al. Decentralized Federated Learning Strategy with Non-Independent Uniformly Distributed Data[J]. Computer Engineering and Applications, 2023, 59(1): 269-277.
doi: 10.3778/j.issn.1002-8331.2204-0165 |
|
谭荣杰, 洪智勇, 余文华, 等. 非独立同分布数据下的去中心化联邦学习策略[J]. 计算机工程与应用, 2023, 59(1): 269-277.
doi: 10.3778/j.issn.1002-8331.2204-0165 |
|
| [20] |
WANG Shiqiang, TUOR T, SALONIDIS T, et al. Adaptive Federated Learning in Resource Constrained Edge Computing Systems[J]. IEEE Journal on Selected Areas in Communications, 2019, 37(6): 1205-1221.
doi: 10.1109/JSAC.2019.2904348 |
| [21] | LUO Bing, LI Xiang, WANG Shiqiang, et al. Cost-Effective Federated Learning Design[C]//IEEE.IEEE INFOCOM 2021-IEEE Conference on Computer Communications. New York: IEEE, 2021: 1-10. |
| [22] |
LIN F P C, HOSSEINALIPOUR S, AZAM S S, et al. Semi-Decentralized Federated Learning with Cooperative D2D Local Model Aggregations[J]. IEEE Journal on Selected Areas in Communications, 2021, 39(12): 3851-3869.
doi: 10.1109/JSAC.2021.3118344 URL |
| [23] |
CHENG Jieren, LUO Ping, XIONG Naixue, et al. AAFL: Asynchronous-Adaptive Federated Learning in Edge-Based Wireless Communication Systems for Countering Communicable Infectious Diseasess[J]. IEEE Journal on Selected Areas in Communications, 2022, 40(11): 3172-3190.
doi: 10.1109/JSAC.2022.3211564 URL |
| [24] |
LIU Lumin, ZHANG Jun, SONG Shenghui, et al. Hierarchical Federated Learning with Quantization: Convergence Analysis and System Design[J]. IEEE Transactions on Wireless Communications, 2023, 22(1): 2-18.
doi: 10.1109/TWC.2022.3190512 URL |
| [25] | WU Jiagao, WANG Yu, SHEN Zhangchi, et al. Adaptive Client and Communication Optimizations in Federated Learning[EB/OL]. (2023-04-08)[2023-04-15]. https://doi.org/10.1016/j.is.2023.102226. |
| [26] | TANG Lun, WANG Zhiping, PU Hao, et al. Research on Efficient Federated Learning Communication Mechanism Based on Adaptive Gradient Compression[J]. Journal of Electronics and Information Technology, 2023, 45(1): 227-234. |
| 唐伦, 汪智平, 蒲昊, 等. 基于自适应梯度压缩的高效联邦学习通信机制研究[J]. 电子与信息学报, 2023, 45(1): 227-234. | |
| [27] | GONG Maoguo, GAO Yuan, WANG Jiongqian, et al. Adaptive Federated Learning Algorithm Based on Evolutionary Strategy[J]. Scientia Sinica (Informationis), 2023, 53(3): 437-453. |
| 公茂果, 高原, 王炯乾, 等. 基于进化策略的自适应联邦学习算法[J]. 中国科学:信息科学, 2023, 53(3): 437-453. | |
| [28] | WENG Jiasi, WENG Jian, ZHANG Jilian, et al. Deepchain: Auditable and Privacy-Preserving Deep Learning with Blockchain-Based Incentive[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(5): 2438-2455. |
| [29] |
LIU Wei, CHEN Li, CHEN Yunfei, et al. Accelerating Federated Learning via Momentum Gradient Descent. IEEE Transactions on Parallel and Distributed Systems, 2020, 31(8): 1754-1766.
doi: 10.1109/TPDS.71 URL |
| [30] |
PHONG L T, AONO Y, HAYASHI T, et al. Privacy-Preserving Deep Learning via Additively Homomorphic Encryption. IEEE Transactions on Information Forensics and Security, 2018, 13(5): 1333-1345.
doi: 10.1109/TIFS.2017.2787987 URL |
| [1] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [2] | CHEN Jing, PENG Changgen, TAN Weijie, XU Dequan. A Multi-Server Federation Learning Scheme Based on Differential Privacy and Secret Sharing [J]. Netinfo Security, 2023, 23(7): 98-110. |
| [3] | LIU Changjie, SHI Runhua. A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning [J]. Netinfo Security, 2023, 23(4): 90-101. |
| [4] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [5] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [6] | LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes [J]. Netinfo Security, 2022, 22(7): 37-45. |
| [7] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [8] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [9] | ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm [J]. Netinfo Security, 2022, 22(11): 17-23. |
| [10] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [11] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| [12] | LU Honglin, WANG Liming, YANG Jing. A New Parameter Masking Federated Learning Privacy Preserving Scheme [J]. Netinfo Security, 2021, 21(8): 26-34. |
| [13] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [14] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [15] | JIANG Nan, CUI Yaohui, WANG Jian, WU Jinchao. Context-based Attack Scenario Reconstruction Model for IDS Alarms [J]. Netinfo Security, 2020, 20(7): 1-10. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||