Netinfo Security ›› 2023, Vol. 23 ›› Issue (8): 86-98.doi: 10.3969/j.issn.1671-1122.2023.08.008
Previous Articles Next Articles
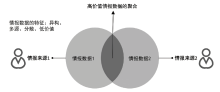
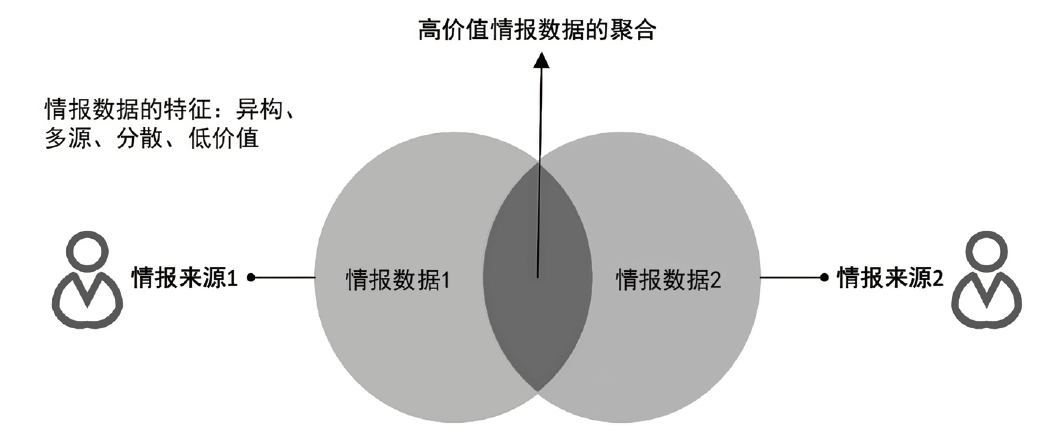
Multi-Source Heterogeneous Data Collaboration via Private Set Intersection
DING Jiang1, ZHANG Guoyan1,2, WEI Zichong3, WANG Mei1,4( )
)
- 1. School of Cyber Science and Technology, Shandong University, Qingdao 266237, China
2. Shandong Institute of Blockchain, Jinan 250102, China
3. Inspur Academy of Science and Technology, Jinan 250101, China
4. Quancheng Laboratory, Jinan 250100, China
-
Received:2023-01-30Online:2023-08-10Published:2023-08-08 -
Contact:WANG Mei E-mail:wangmeiz@sdu.edu.cn
CLC Number:
Cite this article
DING Jiang, ZHANG Guoyan, WEI Zichong, WANG Mei. Multi-Source Heterogeneous Data Collaboration via Private Set Intersection[J]. Netinfo Security, 2023, 23(8): 86-98.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.08.008
| [1] | FREEDMAN M J, NISSIM K, PINKAS B. Efficient Private Matching and Set Intersection[C]//Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2004: 1-19. |
| [2] | JARECKI S, LIU Xiaomin. Efficient Oblivious Pseudorandom Function with Applications to Adaptive OT and Secure Computation of Set Intersection[C]//Springer. Theory of Cryptography Conference. Berlin: Springer, 2009: 577-594. |
| [3] | CAMENISCH J, ZAVERUCHA G M. Private Intersection of Certified Sets[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2009: 108-127. |
| [4] | CRISTOFARO E D, TSUDIK G. Practical Private Set Intersection Protocols with Linear Complexity[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2010: 143-159. |
| [5] |
HAZAY C, LINDELL Y. Efficient Protocols for Set Intersection and Pattern Matching with Security Against Malicious and Covert Adversaries[J]. Journal of Cryptology, 2010, 23(3): 422-456.
doi: 10.1007/s00145-008-9034-x URL |
| [6] | HUANG Yan, DAVID E, JONATHAN K. Private Set Intersection:Are Garbled Circuits Better than Custom Protocols[C]//ISOC. Network and Distributed System Security. NewYork: ISOC, 2012: 1-15. |
| [7] | DONG Changyu, CHEN Liqun, WEN Zikai. When Private Set Intersection Meets Big Data:An Efficient and Scalable Protocol[C]//ACM. Proceedings of the 2013 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2013: 789-800. |
| [8] | PINKAS B, SCHNEIDER T, ZOHNER M. Faster Private Set Intersection Based on OT Extension[C]//ACM. Proceedings of the 23rd USENIX Security Symposium. Berkeley: USENIX Association, 2014: 797-812. |
| [9] | PINKAS B, SCHNEIDER T, SEGEV G, et al. Phasing:Private Set Intersection Using Permutation-Based Hashing[C]//ACM. Proceedings 24th USENIX Conference on Security Symposium. New York: ACM, 2015: 515-530. |
| [10] | DEBNATH S K, DUTTA R. Secure and Efficient Private Set Intersection Cardinality Using Bloom Filter[C]//Springer. Proceedings of the International Conference on Information Security. Berlin: Springer, 2015: 209-226. |
| [11] | BRADLEY T, FABER S, TSUDIK G. Bounded Size-Hiding Private Set Intersection[C]//Springer. International Conference on Security and Cryptography for Networks. Berlin: Springer, 2016: 449-467. |
| [12] | KOLESNIKOV V, KUMARESAN R, ROSULEK M, et al. Efficient Batched Oblivious PRF with Applications to Private Set Intersection[C]//ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 818-829. |
| [13] |
FREEDMAN, MICHAEL J, BENNY P, et al. Efficient Set Intersection with Simulation-Based Security[J]. Journal of Cryptology, 2016, 29(1): 115-155.
doi: 10.1007/s00145-014-9190-0 URL |
| [14] | DEBNATH S K, DUTTA R. How to Meet Big Data When Private Set Intersection Realizes Constant Communication Complexity[C]//Springer. International Conference on Information and Communications Security. Berlin: Springer, 2016: 445-454. |
| [15] | ABADI A, TERZIS S, DONG Changyu. VD-PSI: Verifiable Delegated Private Set Intersection on Outsourced Private Datasets[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2016: 149-168. |
| [16] |
DONG Changyu, LOUKIDES G. Approximating Private Set Union/Intersection Cardinality with Logarithmic Complexity[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(11): 2792-2806.
doi: 10.1109/TIFS.2017.2721360 URL |
| [17] | CHEN Hao, LAINE K, RINDAL P. Fast Private Set Intersection from Homomorphic Encryption[C]//ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1243-1255. |
| [18] | RINDAL P, ROSULEK M. Improved Private Set Intersection Against Malicious Adversaries[C]//Springer. Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2017: 235-259. |
| [19] | SHI Runhua, MU Yi, ZHONG Hong, et al. Quantum Private Set Intersection Cardinality and Its Application to Anonymous Authentication[J]. Information Sciences, 2016, 370(C): 147-158. |
| [20] |
AYDIN A, TERZIS S, METERE R, et al. Efficient Delegated Private Set Intersection on Outsourced Private Datasets[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 16(4): 608-624.
doi: 10.1109/TDSC.8858 URL |
| [21] | HEINRICH A, HOLLICK M, SCHNEIDER T, et al. PrivateDrop:Practical Privacy-Preserving Authentication for Apple AirDrop[C]//ACM. USENIX Security Symposium. Berkeley: USENIX Association, 2021: 3577-3594. |
| [22] | SAHAI A, WATERS B. Fuzzy Identity Based Encryption[C]//IACR. European Cryptology Conference. New York: ACM, 2005: 457-473. |
| [23] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fifine-Grained Access Control of Encrypted Data[C]//ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [24] | OSTROVSKY R, SAHAI A, WATERS B. Attribute-Based Encryption with Non-Monotonic Access Structures[C]//ACM. Proceedings of the 14th ACM Conference on Computer and Communications Security. New York: ACM, 2007: 195-203. |
| [25] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]//IEEE. Proceedings of IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [26] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]//IEEE. 2000 IEEE Symposium on Security and Privacy. New York: IEEE, 2000: 44-55. |
| [27] | GOH E J. Secure Index[EB/OL]. (2003-10-07)[2022-12-20]. https://eprint.iacr.org/archive/2003/216/1079467296.pdf. |
| [28] | BONEH D, CRESCENZO D G, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]//Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2004: 506-522. |
| [29] | CRESCENZO G D, SARASWAT V. Public Key Encryption with Searchable Keywords Based on Jacobi Symbols[C]//Springer. International Conference on Cryptology in India. Berlin: Springer, 2007: 282-296. |
| [30] | BAEK J, SAFAVI-NAINI R, SUSILO W. Public Key Encryption with Keyword Search Revisited[C]//IEEE. International Conference on Computational Science and lts Applications. New York: IEEE, 2008: 1249-1259. |
| [31] |
EMURA K, MIYAJI A, RAHMAN M S, et al. Generic Constructions of Secure Channel Free Searchable Encryption with Adaptive Security[J]. Security and Communication Networks, 2015, 8(8): 1547-1560.
doi: 10.1002/sec.1103 URL |
| [32] | BYUN J W, RHEE H S, PARK H A, et al. Off-Line Keyword Guessing Attacks on Recent Keyword Search Schemes over Encrypted Data[C]//Springer. The 3rd VLDB Workshop on Secure Data Management. Berlin: Springer, 2006: 75-83. |
| [33] | PARK D J, KIM K, LEE P J. Public Key Encryption with Conjunctive Field Keyword Search[C]//Springer. International Workshop on Information Security Applications. Berlin: Springer, 2004: 73-86. |
| [34] | BRINGER J, CHABANNE H, KINDARJI B. Error-Tolerant Searchable Encryption[C]//IEEE. 2009 IEEE International Conference on Communications. New York: IEEE, 2009: 1-35. |
| [35] | ZHENG Qingji, XU Shouhuai, ATENIESE G. VABKS:Verifiable Attribute-Based Keyword Search over Outsourced Encrypted Data[C]//IEEE. 2014 IEEE Conference on Computer Communications. New York: IEEE, 2014: 522-530. |
| [36] | LIU Pengliang, WANG Jianfeng, MA Hua, et al. Efficient Verifiable Public Key Encryption with Keyword Search Based on KP-ABE[C]//ACM. The 9th International Conference on Broadband and Wireless Computing. New York: ACM, 2014: 584-589. |
| [37] | KISSNER L, SONG D. Privacy-Preserving Set Operations[C]//Springer. Annual International Cryptology Conference. Berlin: Springer, 2005: 241-257. |
| [38] | SANG Yingpeng, SHEN Hong, TAN Yasuo, et al. Efficient Protocols for Privacy Preserving Matching Against Distributed Datasets[C]//Springer. International Conference on Information and Communications Security. Berlin: Springer, 2006: 210-227. |
| [39] | WANG Boyang, LI Baochun, LI Hui. Gmatch:Secure and Privacy-Preserving Group Matching in Social Networks[C]//IEEE. 2012 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2012: 726-731. |
| [40] | KAMARA S, MOHASSEL P, RAYKOVA M, et al. Scaling Private Set Intersection to Billion-Element Sets[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2014: 195-215. |
| [41] |
THAPA A, LI Ming, SALINAS S. Asymmetric Social Proximity Based Private Matching Protocols for Online Social Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2015, 26 (6): 1547-1559.
doi: 10.1109/TPDS.71 URL |
| [42] | YARLAGADDA N R, NARESH B. Improved Privacy Preserving Profile Matching in Online Social Networks[J]. Ijseat, 2015, 3(1): 1112-1115. |
| [43] | PATSAKIS C, ZIGOMITROS A, SOLANAS A. Privacy-Aware Genome Mining:Server-Assisted Protocols for Private Set Intersection and Pattern Matching[C]//IEEE. 2015 IEEE 28th International Symposium on Computer-Based Medical Systems. New York: IEEE, 2015: 276-279. |
| [44] | KOLESNIKOV V, MATANIA N, PINKAS B, et al. Practical Multi-Party Private Set Intersection from Symmetric-Key Techniques[C]//ACM. ACM Sigsac Conference on Computer & Communications Security. New York: ACM, 2017: 1257-1272. |
| [45] |
ZHANG En, LI Fenghua, NIU Ben, et al. Server-Aided Private Set Intersection Based on Reputation[J]. Information Sciences, 2017, 387: 180-194.
doi: 10.1016/j.ins.2016.09.056 URL |
| [46] | PINKAS B, SCHNEIDER T, WEINERT C, et al. Efficient Circuit-Based PSI via Cuckoo Hashing[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2018: 125-157. |
| [47] | NEVO O, TRIEU N, YANAI A S. Fast Malicious Multiparty Private Set Intersection[C]//ACM. 2021 ACM SIGSAC Conference on Computer and Communication Security. New York: ACM, 2021: 1151-1165. |
| [48] | FELLOWS M, KOBLITZ N. Combinatorial Cryptosystems Galore[J]. Contemporary Mathematics, 1994, 168: 1-12. |
| [49] | GENTRY C. A Fully Homomorphic Encryption Scheme[M]. Palo Alto: Stanford University, 2009. |
| [50] | BRAKERSKI Z, VAIKUNTANATHAN V. Fully Homomorphic Encryption from Ring-LWE and Security for Key Dependent Messages[C]//Springer. In Advances in Cryptology (CRYPTO’11). Berlin: Springer, 505-524. |
| [51] | BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V. Fully Homomorphic Encryption Without Bootstrapping[J]. ACM Transactions on Computation Theory, 2014, 6(3): 1-36. |
| [52] | FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. (2012-01-07)[2022-12-20]. https://eprint.iacr.org/2012/144.pdf. |
| [53] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate NumbersC//Springer. In International Conference on the Theory and Application of Cryptology and Information Security. Berlin: Springer, 2017: 409-437. |
| [54] | CHEN Hao, LAINE K, RINDAL P. Fast Private Set Intersection from Homomorphic Encryption[C]//ACM. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1243-1255. |
| [55] | CHEN Hao, HUANG Zhicong, LAINE K, et al. Labeled PSI from Fully Homomorphic Encryption with Malicious Security[C]//ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 1223-1237. |
| [56] | UZUN E, CHUNG S P, KOLESNIKOV V, et al. Fuzzy Labeled Private Set Intersection with Applications to Private Real-Time Biometric Search[C]//ACM. USENIX Security Symposium. Berkeley: USENIX Association, 2021: 911-928. |
| [57] | MANULIS M, PINKAS B, POETTERING B. Privacy-Preserving Group Discovery with Linear ComplexityC//Springer. International Conference on Applied Cryptography and Network Security(ACNS 2010). Berlin: Springer, 2010: 420-437. |
| [58] | CHO C, DACHMAN-SOLED D, JARECKI S. Efficient Concurrent Covert Computation of String Equality and Set Intersection. Berlin: Springer, 2016: 164-179. |
| [59] | PINKAS B, SCHNEIDER T, TKACHENKO O, et al. Efficient Circuit-Based PSI with Linear Communication[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2019: 122-153. |
| [60] | CHANDRAN N, GUPTA D, SHAH A. Circuit-PSI with Linear Complexity via Relaxed Batch OPPRF[C]//Springer. Proceedings on Privacy Enhancing Technologies. Berlin: Springer, 2021: 353-372. |
| [61] | CHANDRAN N, DASGUPTA N, GUPTA D, et al. Efficient Linear Multiparty PSI and Extensions to Circuit/Quorum PSI[C]//ACM. Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 1182-1204. |
| [62] | BENNY P, MIKE R, NI T, et al. SpOT-Light: Lightweight Private Set Intersection from Sparse OT Extension[C]//Springer. In Advances in Cryptology. Berlin: Springer, 2019: 401-431. |
| [63] | ISHAI Y, KILIAN J, NISSIM K, et al. Extending Oblivious Transfers Efficiently[C]//Springer. In Advances in Cryptology(CRYPTO 2003). Berlin: Springer, 2003: 145-161. |
| [64] | KOLESNIKOV V, ROSULEK M, TRIEU N, et al. Scalable Private Set Union from Symmetric-Key Techniques[C]//Springer. International Conference on the Theory and Application of Cryptology and Information Security(ASIACRYPT 2019). Berlin: Springer, 2019: 636-666. |
| [65] | PINKAS B, ROSULEK M, TRIEU N, et al. PSI from PaXoS: Fast, Malicious Private Set Intersection[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques(EUROCRYPT 2020). Berlin: Springer, 2020: 739-767. |
| [66] | MARCELA S M, BLANKSTEIN A, BONNEAU J, et al. CONIKS:Bringing Key Transparency to End Users[C]//USENIX. USENIX Security 2015. Berkeley: USENIX, 2015: 383-398. |
| [67] | CASACUBERTA S, HESSE J, LEHMANN A. SoK:Oblivious Pseudorandom Functions[C]//IEEE. 2022 IEEE 7th European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2022: 625-646. |
| [68] | EVERSPAUGH A, CHATERJEE R, SCOTT S, et al. The Pythia PRF Service[C]//USENIX. USENIX Security Symposium. Berkeley: USENIX, 2015: 547-562. |
| [69] | JARECKI S, KIAYIAS A, KRAWCZYK H, et al. TOPPSS: Cost-Minimal Password-Protected Secret Sharing Based on Threshold OPRF[C]//Springer. International Conference on Applied Cryptography and Network Security. Berlin: Springer, 2017: 39-58. |
| [1] | WANG Zhi, ZHANG Hao, Jason GU. A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN [J]. Netinfo Security, 2023, 23(10): 1-7. |
| [2] | ZHANG Yuchen, LI Lianghui, MA Chenyang, ZHOU Hongwei. A Log Anomaly Detection Method with Variables [J]. Netinfo Security, 2023, 23(10): 16-20. |
| [3] | TONG Xin, JIN Bo, WANG Binjun, ZHAI Hanming. A Malicious SMS Detection Method Blending Adversarial Enhancement and Multi-Task Optimization [J]. Netinfo Security, 2023, 23(10): 21-30. |
| [4] | ZHU Yixin, MIAO Zhangwang, GAN Jinghong, MA Cunqing. Design of Ransomware Defense System Based on Fine-Grained Access Control Scheme [J]. Netinfo Security, 2023, 23(10): 31-38. |
| [5] | ZHANG Lu, TU Chenyang, MIAO Zhangwang, GAN Jinghong. Design of an End-to-Cloud Trusted Transmission Solution for Location Information [J]. Netinfo Security, 2023, 23(10): 39-47. |
| [6] | CHEN Xingren, XIONG Yan, HUANG Wenchao, FU Guilu. A Multi-View Hardware Trojan Detection Method Based on Static Analysis [J]. Netinfo Security, 2023, 23(10): 48-57. |
| [7] | WANG Yu, LYU Liangshuang, XIA Chunhe. A Windows Malware Detection Method Based on Semantic Analysis [J]. Netinfo Security, 2023, 23(10): 58-63. |
| [8] | XING Lingkai, ZHANG Jian. Research and Implementation on Abnormal Behavior Detection Technology of Virtualization Platform Based on HPC [J]. Netinfo Security, 2023, 23(10): 64-69. |
| [9] | QIN Yifang, ZHANG Jian, LIANG Chen. Research on Feature Extraction Technology of Electronic Medical Record Data Based on Neural Networks [J]. Netinfo Security, 2023, 23(10): 70-76. |
| [10] | ZHAO Xinhe, XIE Yongheng, WAN Yueliang, WANG Jinmiao. Detection and Identification Model of Gambling Websites Based on Multi-Modal Data [J]. Netinfo Security, 2023, 23(10): 77-82. |
| [11] | YE Huanrong, LI Muyuan, JIANG Bo. Research on DGA Malicious Domain Name Detection Method Based on Transfer Learning and Threat Intelligence [J]. Netinfo Security, 2023, 23(10): 8-15. |
| [12] | QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders [J]. Netinfo Security, 2023, 23(9): 1-11. |
| [13] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [14] | DAI Yu, ZHOU Fei, XUE Dan. Handover Authentication Protocol Based on Chinese Remainder Theorem Secret Sharing [J]. Netinfo Security, 2023, 23(9): 118-128. |
| [15] | ZHANG Yuchen, ZHANG Yawen, WU Yue, LI Cheng. A Method of Feature Extraction for Network Traffic Based on Time-Frequency Diagrams and Improved E-GraphSAGE [J]. Netinfo Security, 2023, 23(9): 12-24. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||