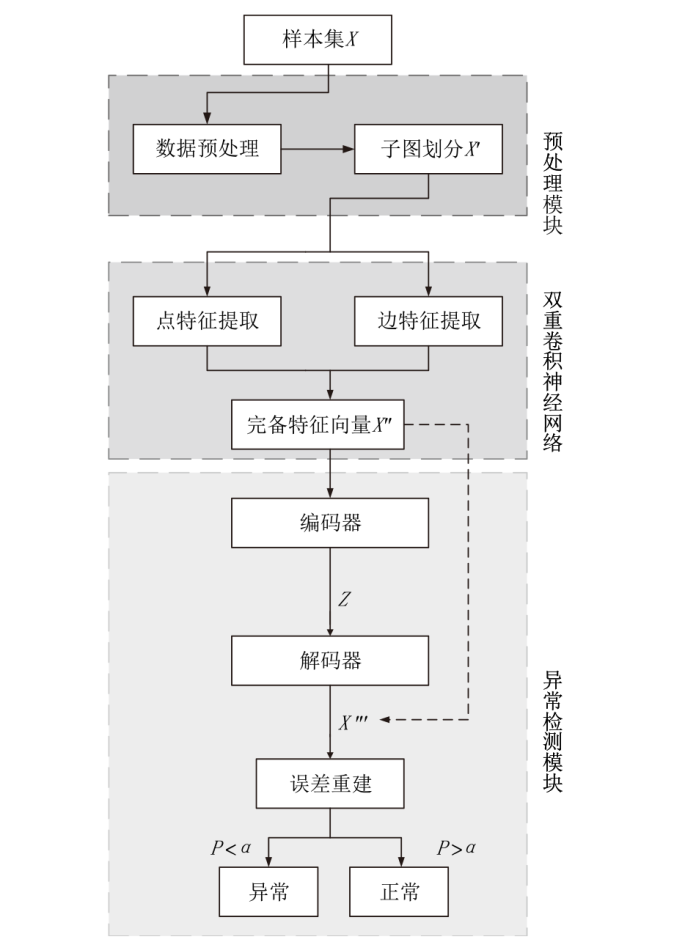
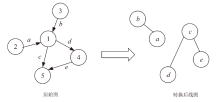
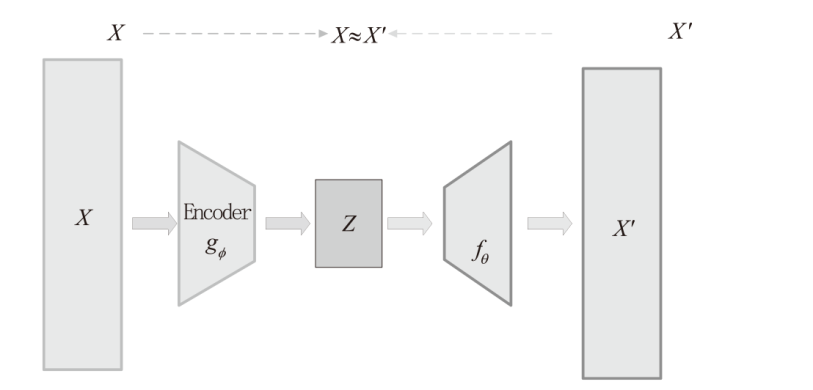
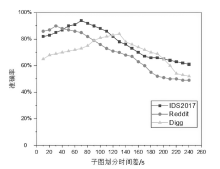
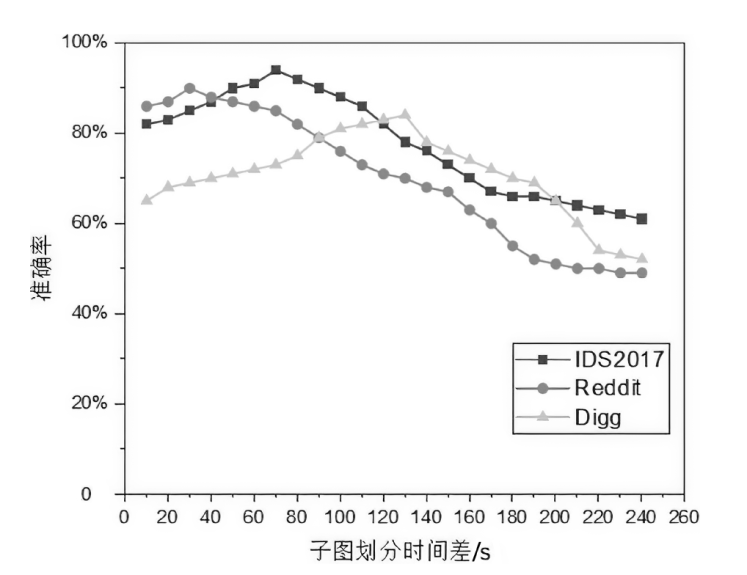
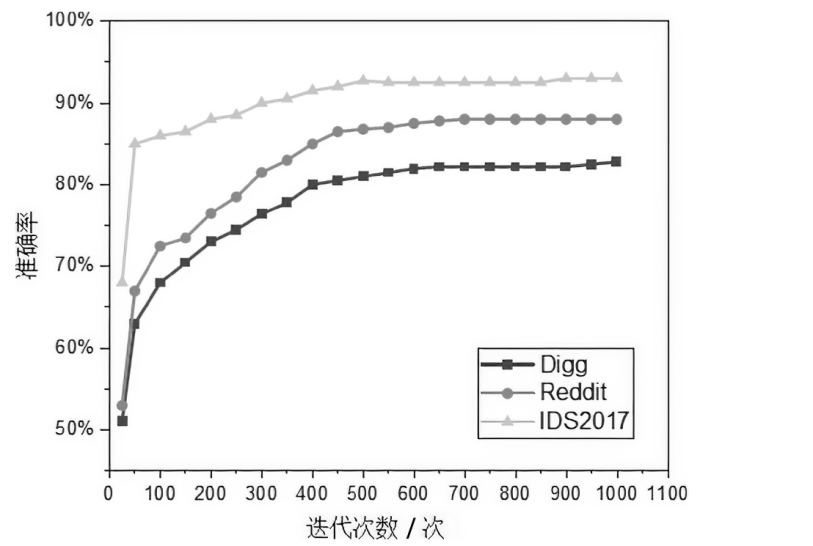
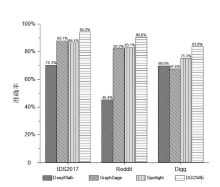
Netinfo Security ›› 2023, Vol. 23 ›› Issue (9): 1-11.doi: 10.3969/j.issn.1671-1122.2023.09.001
Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders
QIN Zhongyuan( ), MA Nan, YU Yacong, CHEN Liquan
), MA Nan, YU Yacong, CHEN Liquan
- School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
-
Received:2023-06-05Online:2023-09-10Published:2023-09-18 -
Contact:QIN Zhongyuan E-mail:zyqin@seu.edu.cn
CLC Number:
Cite this article
QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders[J]. Netinfo Security, 2023, 23(9): 1-11.
share this article
| [1] | YOST J R. The March of IDES: Early History of Intrusion-Detection Expert Systems[J]. IEEE Annals of the History of Computing, 2016, 38(4): 42-54. |
| [2] | JAMES G, WITTEN D, HASTIE T, et al. An Introduction to Statistical Learning: With Applications in R[M]. New York: Springer, 2021. |
| [3] |
THAKKAR A, LOHIYA R. A Review on Machine Learning and Deep Learning Perspectives of IDS for IoT: Recent Updates, Security Issues, and Challenges[J]. Archives of Computational Methods in Engineering, 2021, 28(4): 3211-3243.
doi: 10.1007/s11831-020-09496-0 |
| [4] |
VINAYAKUMAR R, ALAZAB M, SOMAN K P, et al. Deep Learning Approach for Intelligent Intrusion Detection System[J]. IEEE Access, 2019, 7: 41525-41550.
doi: 10.1109/ACCESS.2019.2895334 |
| [5] | ESWARAN D, FALOUTSOS C. SedanSpot: Detecting Anomalies in Edge Streams[C]// IEEE. 2018 IEEE International Conference on Data Mining (ICDM). New York: IEEE, 2018: 953-958. |
| [6] | ZHU Huidi, LU Jialiang. Graph-Based Intrusion Detection System Using General Behavior Learning[C]// IEEE. GLOBECOM 2022-2022 IEEE Global Communications Conference. New York: IEEE, 2022: 2621-2626. |
| [7] | YAO Yepeng, SU Liya, LU Zhigang. DeepGFL: Deep Feature Learning via Graph for Attack Detection on Flow-Based Network Traffic[C]// IEEE. MILCOM 2018-2018 IEEE Military Communications Conference (MILCOM). New York: IEEE, 2018: 579-584. |
| [8] |
FANG Yong, WANG Congshuang, FANG Zhiyang, et al. LMTracker: Lateral Movement Path Detection Based on Heterogeneous Graph Embedding[J]. Neurocomputing, 2022, 474: 37-47.
doi: 10.1016/j.neucom.2021.12.026 URL |
| [9] |
WU Zonghua, PAN Shirui, CHEN Fengwen, et al. A Comprehensive Survey on Graph Neural Networks[J]. IEEE Transactions on Neural Networks and Learning Systems, 2020, 32(1): 4-24.
doi: 10.1109/TNNLS.5962385 URL |
| [10] | CAVILLE E, LO W W, LAYEGHY S, et al. Anomal-E: A Self-Supervised Network Intrusion Detection System Based on Graph Neural Networks[J]. Knowledge-Based Systems, 2022, 258: 1-12. |
| [11] | KIPF T N, WELLING M. Semi-Supervised Classification with Graph Convolutional Networks[EB/OL]. (2016-09-09)[2023-05-13]. https://arxiv.org/abs/1609.02907. |
| [12] | LIU Jie, LI Xiwang. Anomaly Detection Algorithm in Industrial Control Network Based on Graph Neural Network[J]. Computer Systems & Applications, 2020, 29(12): 234-238. |
| 刘杰, 李喜旺. 基于图神经网络的工控网络异常检测算法[J]. 计算机系统应用, 2020, 29(12): 234-238. | |
| [13] |
TANG Qiuhang, CHEN Huadong, GE Binbin, et al. AIGCN: Attack Intention Detection for Power System Using Graph Convolutional Networks[J]. Journal of Signal Processing Systems, 2022, 94(11): 1119-1127.
doi: 10.1007/s11265-021-01724-5 |
| [14] | POURHABIBI T, ONG K L, KAM B, et al. Fraud Detection: A Systematic Literature Review of Graph-Based Anomaly Detection Approaches[J]. Decision Support Systems, 2020, 133: 1-15. |
| [15] |
KIM H, LEE B S, SHIN W Y, et al. Graph Anomaly Detection with Graph Neural Networks: Current Status and Challenges[J]. IEEE Access, 2022, 10: 111820-111829.
doi: 10.1109/ACCESS.2022.3211306 URL |
| [16] |
DING Qingfeng, LI Jinguo. A Distributed Abnormal Traffic Detection Scheme in the Internet of Things Environment[J]. Computer Engineering, 2022, 48(8): 152-159.
doi: 10.19678/j.issn.1000-3428.0063284 |
|
丁庆丰, 李晋国. 一种物联网环境下的分布式异常流量检测方案[J]. 计算机工程, 2022, 48(8): 152-159.
doi: 10.19678/j.issn.1000-3428.0063284 |
|
| [17] | ZOLA F, SEGUROLA-GIL L, BRUSE J L, et al. Network Traffic Analysis through Node Behaviour Classification: A Graph-Based Approach with Temporal Dissection and Data-Level Preprocessing[J]. Computers & Security, 2022, 115: 1-17. |
| [18] | LO W W, LAYEGHY S, SARHAN M. E-GraphSAGE: A Graph Neural Network Based Intrusion Detection System for IoT[C]// IEEE/IFIP. 2022 IEEE/IFIP Network Operations and Management Symposium (NOMS 2022). New York: IEEE, 2022: 1-9. |
| [19] | LIU Jinpeng. Network Security Protection Based on Machine Learning Technology[J]. Cybersecurity, 2018, 9(9): 96-102. |
| 刘金鹏. 基于机器学习技术的网络安全防护[J]. 网络空间安全, 2018, 9(9): 96-102. | |
| [20] |
EDDAHMANI I, PHAM C H, NAPOLEON T, et al. Unsupervised Learning of Disentangled Representation via Auto-Encoding: A Survey[J]. Sensors, 2023, 23(4): 1-19.
doi: 10.3390/s23010001 URL |
| [21] | SAKURADA M, YAIRI T. Anomaly Detection Using Autoencoders with Nonlinear Dimensionality Reduction[C]// MLSDA. Proceedings of the MLSDA 2014 2nd Workshop on Machine Learning for Sensory Data Analysis. New York: ACM, 2014: 4-11. |
| [22] | NOBLE C C, COOK D J. Graph-Based Anomaly Detection[C]// ACM SIGKDD. The Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2003: 631-636. |
| [23] | PEROZZI B, AL-RFOU R, SKIENA S. DeepWalk: Online Learning of Social Representations[C]// ACM SIGKDD. The 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2014: 701-710. |
| [24] | HAMILTON W, YING R, LESKOVEC J, et al. Inductive Representation Learning on Large Graphs[J]. Neural Information Processing Systems, 2017, 1(2): 1024-1034. |
| [25] | ESWARAN D, FALOUTSIS C, GUHA S, et al. SpotLight: Detecting Anomalies in Streaming Graphs[C]// ACM SIGKDD. KDD '18: Proceedings of the 24th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining. New York: ACM, 2018: 1378-1386. |
| [1] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [2] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [3] | GU Zhaojun, LIU Tingting, GAO Bing, SUI He. Anomaly Detection of Imbalanced Data in Industrial Control System Based on GAN-Cross [J]. Netinfo Security, 2022, 22(8): 81-89. |
| [4] | ZHOU Jingyi, LI Hongjiao. False Data Injection Attack Detection Method against PMU Measurements [J]. Netinfo Security, 2022, 22(5): 75-83. |
| [5] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [6] | XU Ruzhi, LYU Changran, LONG Yan, LIU Yuanbin. Defense Research of High-Hidden Data Attack in Industry Control System [J]. Netinfo Security, 2022, 22(12): 34-46. |
| [7] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| [8] | NIU Yinuo, ZHANG Yifei, GAO Neng, MA Cunqing. Design of Log-Based Anomaly Detection System Based on Temporal and Logical Relationship [J]. Netinfo Security, 2022, 22(11): 1-6. |
| [9] | TONG Xin, JIN Bo, WANG Jingya, YANG Ying. A Multi-View and Multi-Task Learning Detection Method for Android Malware [J]. Netinfo Security, 2022, 22(10): 1-7. |
| [10] | ZHU Lina, MA Mingrui, ZHU Dongzhao. Detection Method for C Language Family Based on Graph Neural Network and Generic Vulnerability Analysis Framework [J]. Netinfo Security, 2022, 22(10): 59-68. |
| [11] | QIN Zhongyuan, HU Ning, FANG Lanting. Network Anomaly Detection Method Based on Immune Bionic Mechanism and Graph Neural Network [J]. Netinfo Security, 2021, 21(8): 10-16. |
| [12] | XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network [J]. Netinfo Security, 2021, 21(7): 54-62. |
| [13] | LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering [J]. Netinfo Security, 2021, 21(3): 53-63. |
| [14] | WU Jiajie, WU Shaoling, WANG Wei. An Anomaly Detection and Location Algorithm Based on TCN and Attention Mechanism [J]. Netinfo Security, 2021, 21(11): 85-94. |
| [15] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||