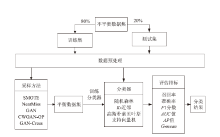
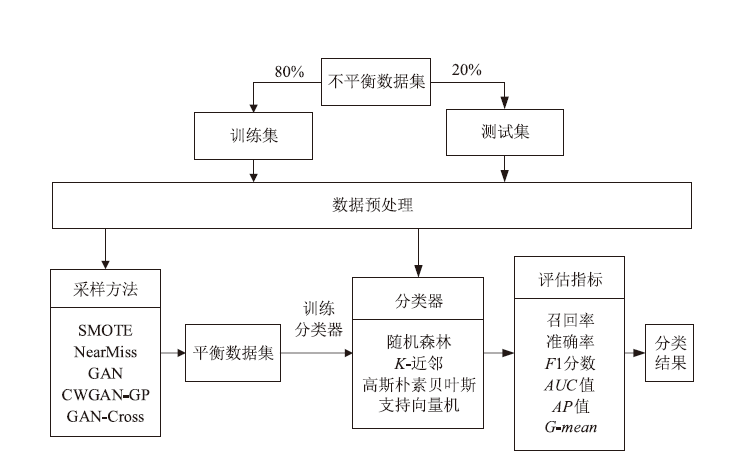
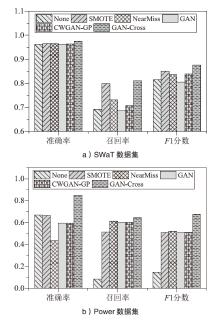
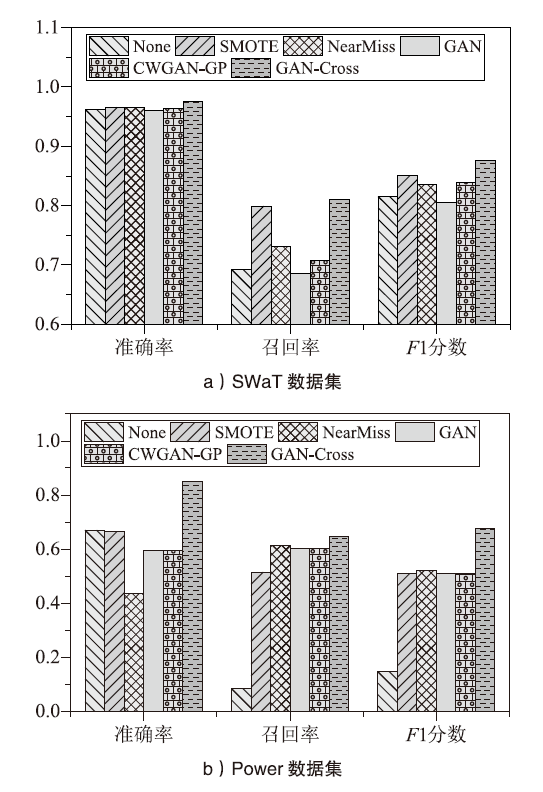
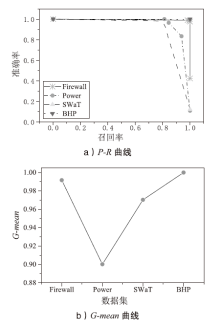
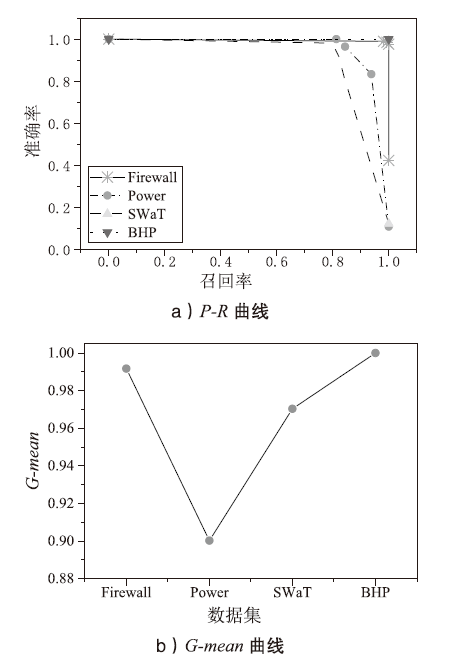
| [1] |
PENG Yong, JIANG Changqing, XIE Feng, et al. Research Progress on Information Security of Industrial Control System[J]. Journal of Tsinghua University(Natural Science Edition), 2012, 52(10): 1396-1408.
|
|
彭勇, 江常青, 谢丰, 等. 工业控制系统信息安全研究进展[J]. 清华大学学报(自然科学版), 2012, 52(10):1396-1408.
|
| [2] |
ZENG Yu, GUO Jinquan. Research of the Security Situation about Industrial Control Information System[J]. Netinfo Security, 2016, 16(9): 169-172.
|
|
曾瑜, 郭金全. 工业控制系统信息安全现状分析[J]. 信息网络安全, 2016, 16(9):169-172.
|
| [3] |
WANG Yubin, CHEN Si, CHENG Nan. Research on Industrial Control System Security Defense[J]. Netinfo Security, 2016, 16(9): 35-39.
|
|
王昱镔, 陈思, 程楠. 工业控制系统信息安全防护研究[J]. 信息网络安全, 2016, 16(9):35-39.
|
| [4] |
WANG Qikui, LI Xin, ZHAO Fu. Research on Information Security for Industrial Control System and the Solution for Numerical Control Network[J]. Netinfo Security, 2014, 14(9): 120-122.
|
|
王琦魁, 李昕, 赵甫. 工控系统信息安全与加工网络防护方案研究[J]. 信息网络安全, 2014, 14(9):120-122.
|
| [5] |
YANG An, SUN Limin, WANG Xiaoshan, et al. Intrusion Detection Techniques for Industrial Control System[J]. Journal of Computer Research and Development, 2016, 53(9): 2039-2054.
|
| [6] |
LAI Yingxu, LIU Zenghui, CAI Xiaotian, et al. Research on Intrusion Detection of Industrial Control System[J]. Journal on Communications, 2017, 38(2): 143-156.
|
|
赖英旭, 刘增辉, 蔡晓田, 等. 工业控制系统入侵检测研究综述[J]. 通信学报, 2017, 38(2):143-156.
|
| [7] |
LIU Dingxiang, QIAO Shaojie, ZHANG Yongqing, et al. A Survey on Data Sampling Methods in Imbalance Classification[J]. Journal of Chongqing University of Technology(Natural Science), 2019, 33(7): 102-112.
|
|
刘定祥, 乔少杰, 张永清, 等. 不平衡分类的数据采样方法综述[J]. 重庆理工大学学报(自然科学版), 2019, 33(7):102-112.
|
| [8] |
ZHANG Xiaoyu, WANG Huazhong. Intrusion Detection of ICS Based on Improved Border-SMOTE for Unbalance Data[J]. Netinfo Security, 2020, 20(7): 70-76.
|
|
张晓宇, 王华忠. 基于改进Border-SMOTE的不平衡数据工业控制系统入侵检测[J]. 信息网络安全, 2020, 20(7):70-76.
|
| [9] |
YIN Hua, GAI Keke. An Empirical Study on Preprocessing High-Dimensional Class-Imbalanced Data for Classification[C]//IEEE. IEEE 17th International Conference on High Performance Computing and Communications, 2015 IEEE 7th International Symposium on Cyberspace Safety and Security, and 2015 IEEE 12th International Conference on Embedded Software and Systems. New Jersey: IEEE, 2015: 1314-1319.
|
| [10] |
PAN Tingting, ZHAO Junhong, WU Wei. Learning Imbalanced Datasets Based on SMOTE and Gaussian Distribution[EB/OL]. [ 2021-02-11]. https://www.sciencedirect.com/science/article/abs/pii/S0020025519310187.
|
| [11] |
LIU Xuying, WU Jianxin, ZHOU Zhihua. Exploratory Under-Sampling for Class-Imbalance Learning[J]. IEEE Transactions on Systems, Man, and Cybernetics, Part B(Cybernetics), 2009, 39(2): 539-550.
|
| [12] |
GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Nets[EB/OL]. (2014-12-02)[2021-02-11]. https://dl.acm.org/doi/10.5555/2969033.2969125.
|
| [13] |
XU Lei, VEERAMACHANENI K. Synthesizing Tabular Data Using Generative Adversarial Networks[EB/OL]. [ 2021-02-11]. https://arxiv.org/abs/1811.11264.
|
| [14] |
BAOWALY M K, LIN Jiajing, LIU Chaolin, et al. Synthesizing Electronic Health Records Using Improved Generative Adversarial Networks[J]. Journal of the American Medical Informatics Association, 2019, 26(3): 228-241.
doi: 10.1093/jamia/ocy142
URL
|
| [15] |
ENGELMANN J, LESSMANN S. Conditional Wasserstein GAN-Based Oversampling of Tabular Data for Imbalanced Learning-ScienceDirect[EB/OL]. [ 2021-03-12]. https://www.sciencedirect.com/science/article/abs/pii/S0957417421000233.
|
| [16] |
ZHENG Ming, LI Tong, ZHU Rui, et al. Conditional Wasserstein generative adversarial Network-Gradient Penalty-Based Approach to Alleviating Imbalanced Data Classification[J]. Information Sciences, 2020, 512: 1009-1023.
doi: 10.1016/j.ins.2019.10.014
URL
|
| [17] |
WANG Ruoxi, FU Bin, FU Gang, et al. Deep & Cross Network for Ad Click Predictions[EB/OL]. [ 2021-03-12]. https://dl.acm.org/doi/10.1145/3124749.3124754.
|
| [18] |
BREIMAN L. Random Forests[J]. Mach Learn, 2001, 45: 5-32.
doi: 10.1023/A:1010933404324
URL
|
| [19] |
KALAL Z, MIKOLAJCZYK K, MATAS J. Tracking-Learning-Detection[J]. IEEE Transactions on Software Engineering, 2011, 34(7): 1409-1422.
|
| [20] |
DU Ruijie. Research of Bayesian Classifier and Its Applications[D]. Shanghai: Shanghai University, 2012.
|
|
杜瑞杰. 贝叶斯分类器及其应用研究[D]. 上海: 上海大学, 2012.
|
| [21] |
CRISTIANINI N, SHAWE-TAYLO J. An Introduction to Support Vector Machines and Other Kenerl-Based Learning Methods[M]. Beijing: Publishing House of Electronics Industry, 2004.
|
| [22] |
ARJOVSKY M, CHINTALA S, BOTTOU L. Wasserstein Generative Adversarial Networks[C]//ACM. 2017 9th International Conference on Machine Learning and Computing(ICMLC 2017). New York: PMLR, 2017: 214-223.
|
| [23] |
PEDREGOSA F, VAROQUAUX G. Scikit-Learn: Machine Learning in Python[J]. Journal of Machine Learning Research, 2013, 12(10): 2825-2830.
|
 )
)