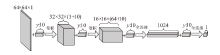
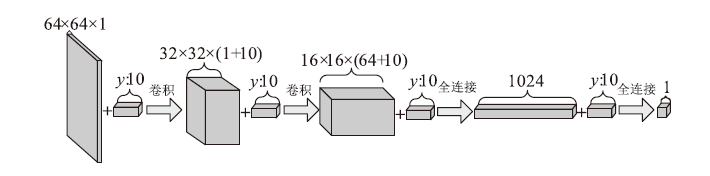
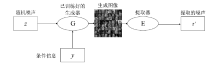
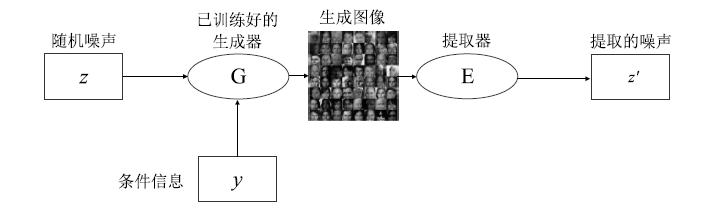
| [1] |
FILLER T, JUDAS J, FRIDRICH J. Minimizing Additive Aistortion in Steganography Using Syndrome-trellis Codes[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(3):920-935.
doi: 10.1109/TIFS.2011.2134094
URL
|
| [2] |
SALLEE P. Model-based Methods for Steganography and Steganalysis[J]. International Journal of Image and Graphics, 2005, 5(1):167-189.
doi: 10.1142/S0219467805001719
URL
|
| [3] |
PEVNY T, FILLER T, BAS P. Using High-dimensional Image Models to Perform Highly Undetectable Steganography[J]. Lecture Notes in Computer Science, 2010, 3(12):161-177.
|
| [4] |
HOLUB V, FRIDRICH J. Digital Image Steganography Using Universal Distortion[C]// ACM. The First ACM Workshop on Information Hiding and Multimedia Security, June 17-19, 2013, Montpellier, France. New York: ACM, 2013: 59-68.
|
| [5] |
HOLUB V, FRIDRICH J, DENEMARK T. Universal Distortion Function for Steganography in An Arbitrary Domain[J]. Eurasip Journal on Information Security, 2014, 1(1):1-13.
|
| [6] |
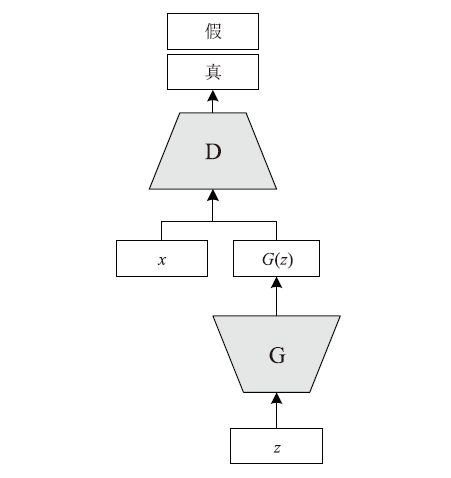
GOODFELLOW I J, POUGET A J, MIRZA M, et al. Generative Adversarial Nets[EB/OL]. https://arxiv.org/pdf/1406.2661.pdf, 2018-06-10.
|
| [7] |
TANG Weixuan, TAN Shunquan, LI Bin, et al. Automatic Stegano-graphic Distortion Learning Using A Generative Adversarial Net-Work[J]. IEEE Signal Processing Letters, 2017, 24(10):1547-1551.
doi: 10.1109/LSP.2017.2745572
URL
|
| [8] |
XU Guanshuo, WU Hanzhou, SHI Yunqing. Structural Design of Convolutional Neural Networks for Steganalysis[J]. IEEE Signal Processing Letters, 2016, 23(5):708-712.
doi: 10.1109/LSP.2016.2548421
URL
|
| [9] |
ZHOU Zhili, CAO Yi, SUN Xingming. Coverless Information Hiding Based on Bag-of-words Model of Image[J]. Journal of Applied Sciences, 2016, 34(5):527-536.
|
|
周志立, 曹燚, 孙星明. 基于图像bag-of-words 模型的无载体信息隐藏[J]. 应用科学学报, 2016, 34(5):527-536.
|
| [10] |
WU Kuochen, WANG Chungming. Steganography Using Reversible Texture Synjournal[J]. IEEE Transactions on Image Processing, 2015, 24(1):130-139.
doi: 10.1109/TIP.2014.2371246
pmid: 25415988
|
| [11] |
HU Donghui, WANG Liang, JIANG Wenjie, et al. A Novel Image Steganography Method via Deep Convolutional Generative[J]. IEEE Access, 2018, 99(6):38303-38314.
|
| [12] |
ZHANG Minqing, LI Zonghan, LIU Jia, et al. Generative Steganography Based on Boundary Equilibrium Generative Adversarial Network[EB/OL]. https://doi.org/10.13705/j.issn.1671-6841.2019419, 2020-01-06.
|
|
张敏情, 李宗翰, 刘佳, 等. 基于边界平衡生成对抗网络的生成式隐写[EB/OL]. https://doi.org/10.13705/j.issn.1671-6841.2019419, 2020-01-06.
|
| [13] |
ZHANG Zhuo, LIU Jia, KE Yan, et al. Generative Steganography by Sampling[J]. IEEE Access, 2019, 96(7):118586-118597.
|
| [14] |
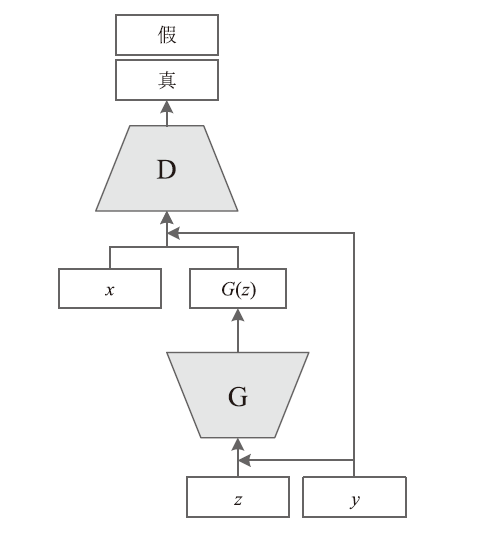
MIRZA M, OSINDERO S. Conditional Generative Adversarial Nets[EB/OL]. https://arxiv.org/abs/1411.1784.pdf, 2018-03-12.
|
| [15] |
LIU Jia, KE Yan, LEI Yu, et al. Application of Generative Adversarial Network in Image Steganography[J], Journal of Wuhan University(Natural Science Edition). 2019, 65(2):139-152.
|
|
刘佳, 柯彦, 雷雨, 等. 生成对抗网络在图像隐写中的应用[J], 武汉大学学报(理学版), 2019, 65(2):139-152.
|
| [16] |
VOLKHONSKIY D, NAZAROV I, BORISENKO B, et al. Steganographic Generative Adversarial Networks[EB/OL]. http://arxiv.org/abs/1703.05502.pdf, 2018-02-12.
|
| [17] |
SHI Haichao, DONG Jing, WANG Wei, et al. SSGAN: Secure Steganography Based on Generative Adversarial Networks[EB/OL]. https://arxiv.org/abs/1707.01613v3.pdf, 2018-04-12.
|
| [18] |
WANG Yaojie, NIU Ke, YANG Xiaoyuan. Image Steganography Scheme Based on GANs[J]. Netinfo Security, 2019, 19(5):54-60.
|
|
王耀杰, 钮可, 杨晓元. 基于生成对抗网络的图像隐藏方案[J]. 信息网络安全, 2019, 19(5):54-60.
|
| [19] |
LIU Mingming, ZHANG Minqing, LIU Jia, et al. Coverless Information Hiding Based on Generative Adversarial Networks[J]. Journal of Applied Sciences, 2018, 36(2):371-382.
|
|
刘明明, 张敏情, 刘佳, 等. 基于生成对抗网络的无载体信息隐藏[J]. 应用科学学报, 2018, 36(2):371-382.
|
| [20] |
CHEN Lu, MAO Weiyun, SU Lei, et al. Design of Steganography Based on Generative Adversarial Networks[J]. High Technology Letters, 2019, 29(7):632-639.
|
|
陈璐, 毛玮韵, 苏磊, 等. 基于生成对抗网络的隐写术设计[J]. 高技术通讯, 2019, 29(7):632-639.
|
 ), LIU Jia, LI Jun, KE Yan
), LIU Jia, LI Jun, KE Yan