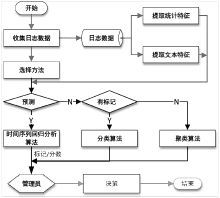
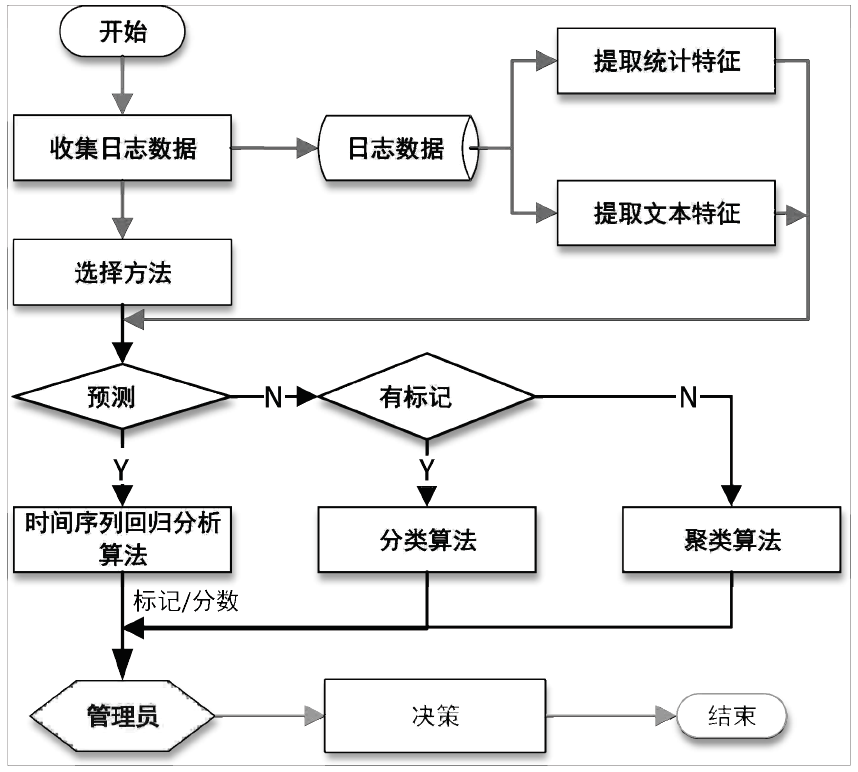
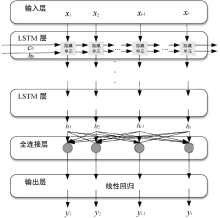
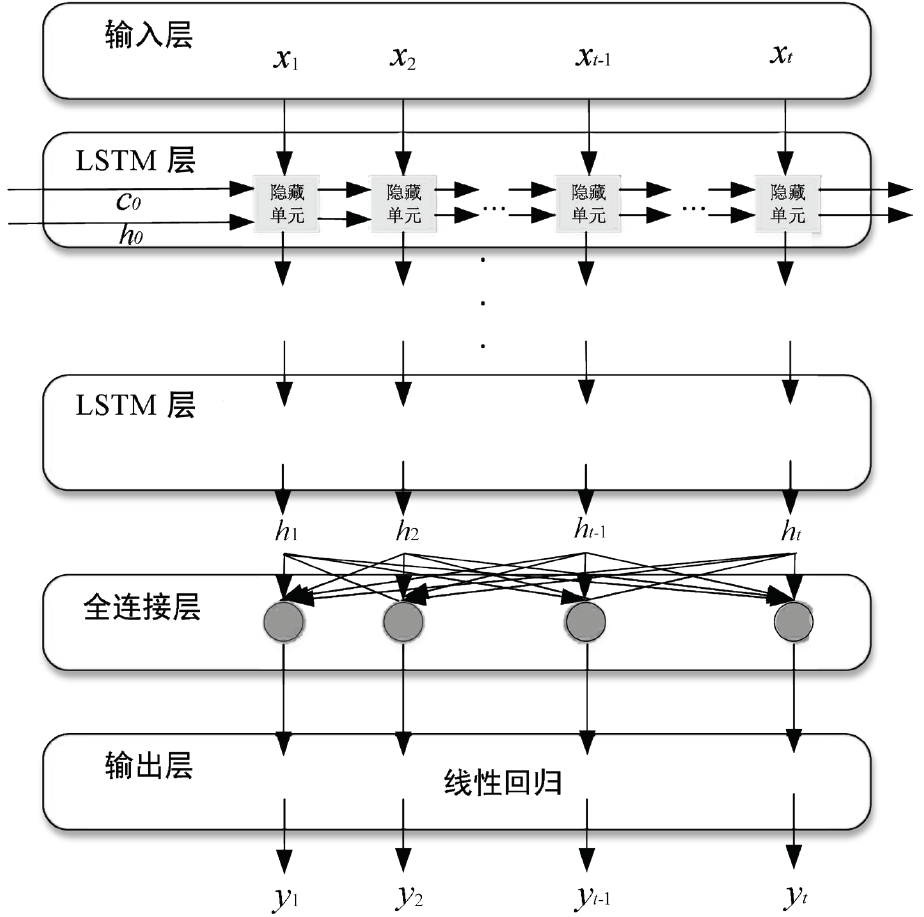
| [1] |
WANG Zhenhui, WANG Zhenduo, YAO Quanzhu. Insider Threat Detection Technology of Information System[J]. Computer System Applications, 2019,28(12):219-225.
|
|
王振辉, 王振铎, 姚全珠. 信息系统内部威胁检测技术研究[J]. 计算机系统应用, 2019,28(12):219-225.
|
| [2] |
WANG Xuebin, TAN Qingfeng, SHI Jinqiao, et al. Insider Threat Detection Using Characterizing User Behavior[C]// IEEE. IEEE Third International Conference on Data Science in Cyberspace (DSC). July 1-21, 2018, Guangzhou China. New York: IEEE, 2018: 476-482.
|
| [3] |
GAVAI G, SRICHARM K, GUNNING D, et al. Supervised and Unsupervised Methods to Detect Insider Threat from Enterprise Social and Online Activity Data[J]. Journal of Wireless Mobile Netwroks, Ubiquitous Computing, and Dependable Applications. 2015,6(4):47-63.
|
| [4] |
GUO Yuanbo, LIU Chunhui, KONG Jing, et al. Study on User Behavior Profiling in Insider Threat Detection[J]. Journal of Communications, 2018,39(12):141-150.
|
|
郭渊博, 刘春辉, 孔菁, 等. 内部威胁检测中用户行为模式画像方法研究[J]. 通信学报, 2018,39(12):141-150.
|
| [5] |
WANG Yifeng, GUO Yuanbo, LI Tao, et al. Method for Insider Threat Detection with Small Samples[J]. Journal of Chinese Computer System, 2019,40(11):2330-2336.
|
|
王一丰, 郭渊博, 李涛, 等. 一种小样本下的内部威胁检测方法研究[J]. 小型微型计算机系统, 2019,40(11):2330-2336.
|
| [6] |
LI Haibin, LI Qi, TANG Ruming, et al. User Behavior Anomaly Detection for Database Based on Unsupervised Learning[J]. Journal of Chinese Computer System, 2018,39(11):2464-2472.
|
|
李海斌, 李琦, 汤汝鸣, 等. 一种无监督的数据库用户行为异常检测方法[J]. 小型微型计算机系统, 2018,39(11):2464-2472.
|
| [7] |
LIU Yu, LUO Senlin, QU Lewei, et al. Full-features Information Equalization Modeling for insider Threat Detection[J]. Journal of Zhejiang University(Engineering Science), 2019,53(4):777-784.
|
|
刘宇, 罗森林, 曲乐炜, 等. 全特征信息均衡建模的内部威胁人物检测[J]. 浙江大学学报(工学版), 2019,53(4):777-784.
|
| [8] |
TUOR A, BAERWOLF R, KNOWLES Nicolas, et al. Recurrent Neural Network Language Models for Open Vocabulary Event-Level Cyber Anomaly Detection[EB/OL]. http://arxiv.org/pdf/1712.00557, 2017:285-293, 2020-5-15.
|
| [9] |
MCMAHAN H.Brendan, HOLT Gary, SCULLEY David, et al. Ad Click Prediction: A View From the Trenches[C]// ACM. ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 8-10, 2013, Chicago, USA. New York: ACM, 2013: 1222-1230.
|
 ), HE Jingsha2, WU Yabiao1, LI Jianguo1
), HE Jingsha2, WU Yabiao1, LI Jianguo1