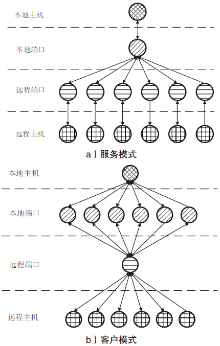
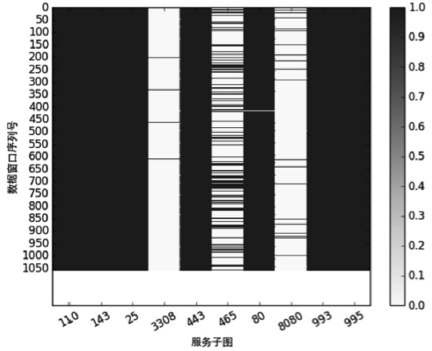
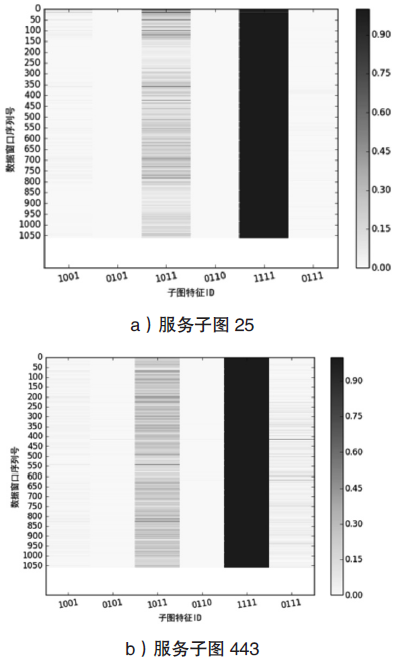
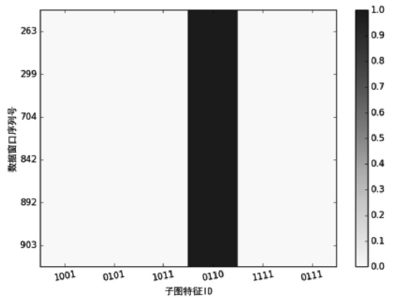
| [1] |
李巍,李丽辉,李佳,等. 远控型木马通信三阶段流量行为特征分析[J].信息网络安全,2015(5):10-15.
|
| [2] |
BHUYAN M H, BHATTACHARYYA D K, KALITA J K.A Multi-step Outlier-based Anomaly Detection Approach to Network-wide Traffic[J]. Information Sciences, 2016, 348:243-271.
|
| [3] |
LEVCHUK G. Function and Activity Classification in Network Traffic Data: Existing Methods, Their Weaknesses,a Path forward[EB/OL].,2017-11-12.
|
| [4] |
KARAGIANNIS T, PAPAGIANNAKI K, FALOUTSOS M. BLINC: Multilevel Traffic Classification in the Dark[EB/OL]. ,2017-11-10.
|
| [5] |
LEVCHUK G, Colonna-Romano J, ESLAMI M. Application of Graph-based Semi-supervised Learning for Development of Cyber COP and Network Intrusion Detection[EB/OL].,2017-10-30.
|
| [6] |
HIMURA Y, FUKUDA K, CHO K, et al.Synoptic Graphlet: Bridging the Gap between Supervised and Unsupervised Profiling of Host-level Network Traffic[J]. IEEE/ACM Transactions on Networking (TON), 2013, 21(4): 1284-1297.
|
| [7] |
ASAI H, FUKUDA K, ESAKI H. Traffic Causality Graphs: Profiling Network Applications through Temporal and Spatial Causality of Flows[EB/OL]. , 2017-10-25.
|
| [8] |
CHENG G, TANG Y.PortView: Identifying Port Roles Based on Port Fuzzy Macroscopic Behavior[J]. Journal of Internet Services and Applications, 2013, 4(9): 2-12.
|
| [9] |
JIN Y, SHARAFUDDIN E, ZHANG Z L.Unveiling Core Network-wide Communication Patterns through Application Traffic Activity Graph Decomposition[J]. ACM SIGMETRICS Performance Evaluation Review, 2009, 37(1): 49-60.
|
| [10] |
ILIOFOTOU M, KIM H, FALOUTSOS M, et al.Graption: A Graph-based P2P Traffic Classification Framework for the Internet Backbone[J]. Computer Networks, 2011, 55(8): 1909-1920.
|
| [11] |
LATAPY M, VIARD T, MAGNIEN C. Stream Graphs and Link Streams for the Modeling of Interactions over Time[EB/OL]. .
|
| [12] |
FRANÇOIS J, WANG S, ENGEL T. BotTrack: Tracking Botnets Using NetFlow and PageRank[EB/OL]. .
|
| [13] |
VENKATESH B, CHOUDHURY S H, NAGARAJA S, et al.BotSpot: Fast Graph Based Identification of Structured P2P Bots[J]. Journal of Computer Virology and Hacking Techniques, 2015, 11(4): 247-261.
|
| [14] |
JUSZCZYSZYN K, KAZIENKO P, MUSIAL K, et al.Temporal Changes in Connection Patterns of an Email-based Social Network[C]// IEEE Computer Society. Proceedings of the 2008 IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology, December 9-12, 2008, Washington, DC, USA. New York:IEEE, 2008: 9-12.
|
| [15] |
JUSZCZYSZYN K, KAZIENKO P, MUSIAŁ K. Local Topology of Social Network Based on Motif Analysis[EB/OL]. ,2017-11-23.
|
| [16] |
JUSZCZYSZYN K, KOŁACZEK G. Motif-based Attack Detection in Network Communication Graphs[EB/OL]. ,2017-11-29.
|
| [17] |
HARSHAW C R, BRIDGES R A, IANNACONE M D, et al.Graphprints: towards a Graph Analytic Method for Network Anomaly Detection[C]// ACM. Proceedings of the 11th Annual Cyber and Information Security Research Conference, April 5-7, 2016, New York, NY, USA. New York:ACM, 2016: 15.
|
| [18] |
PRZULJ N, CORNEIL D G, JURISICA I.Modeling Interactome: Scale-free or Geometric?[J]. Bioinformatics, 2004, 20(18):3508-3515.
|
| [19] |
杨连群,温晋英,刘树发,等. 一种改进的图分割算法在用户行为异常检测中的应用[J].信息网络安全,2016(6):35-40.
|
| [20] |
周颖杰. 基于行为分析的通信网络流量异常检测与关联分析[D].成都:电子科技大学,2013.
|
| [21] |
安冉,朱小波,严寒冰.一种基于时间序列分解的数据窃密事件检测方法研究[J].信息网络安全,2017(8):76-82.
|
| [22] |
CLEVELAND R B, CLEVELAND W S, TERPENNING I.STL: A Seasonal-trend Decomposition Procedure Based on Loess[J]. Journal of Official Statistics, 1990, 6(1): 3-33.
|
| [23] |
VALLIS O, HOCHENBAUM J, KEJARIWAL A.A Novel Technique for Long-term Anomaly Detection in the Cloud[C]// The Advanced Computing Systems Association. Proceedings of the 6th USENIX Workshop on Hot Topics in Cloud Computing (HotCloud 14), June17-18, 2014, Philadelphia, PA, United States. Berkeley, CA : USENIX, 2014: 1-6.
|
 ), Xiaoxiao DI1,2, Di WANG1,2, Yunchun LI1,3
), Xiaoxiao DI1,2, Di WANG1,2, Yunchun LI1,3