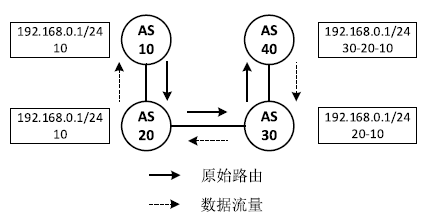
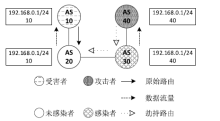
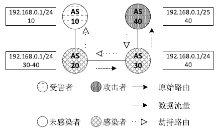
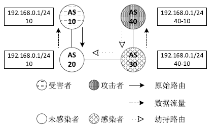
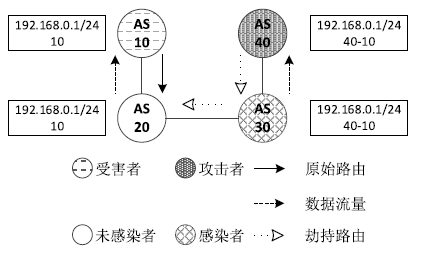
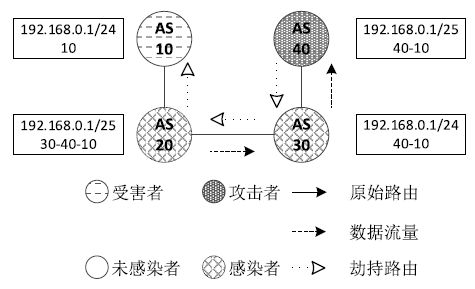
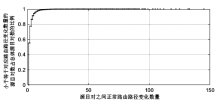
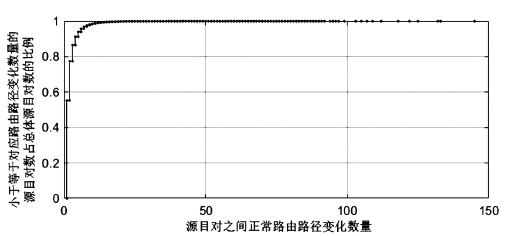
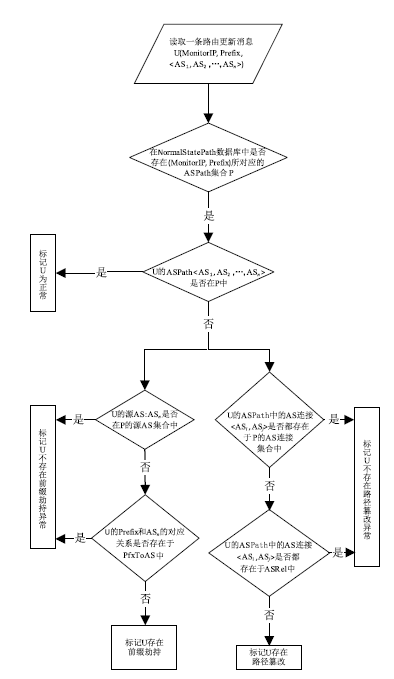
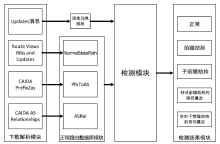
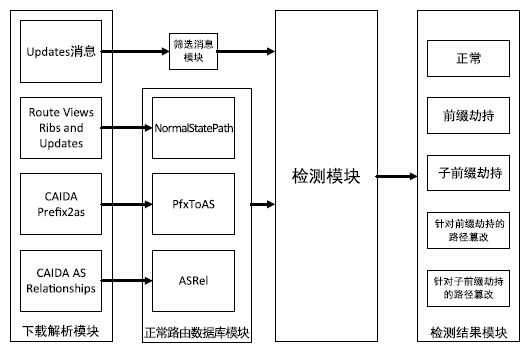
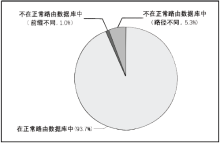
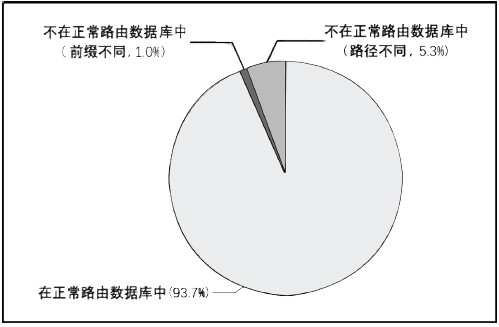
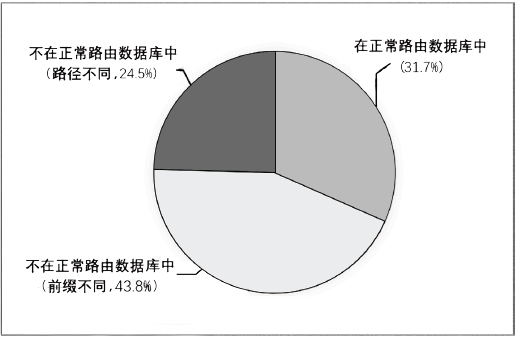
| [1] |
LIU Yujing.Research on Survivability of Internet Inter-domain Routing System[D]. Changsha: National University of Defense Technology, 2013.
|
|
刘宇靖. 互联网域间路由系统生存性研究[D].长沙:国防科学技术大学,2013.
|
| [2] |
DENG Wenping, ZHU Peidong, LU Xicheng, et al.On Evaluating BGP Routing Stress Attack[J]. JCM, 2010, 5(1): 13-22.
|
| [3] |
ZHU Peidong, CAO Huayang, DENG Wenping, et al.A Systematic Approach to Evaluating the Trustworthiness of the Internet Inter-domain Routing Information[J]. IEICE TRANSACTIONS on Information and Systems, 2012, 95(1): 20-28.
|
| [4] |
MIZUGUCHI T, YOSHIDA T. Inter-Domain Routing Security: BGP Route Hijacking[EB/OL]. , 2019-6-13.
|
| [5] |
KENT S, LYNN C, MIKKELSON J, et al. Secure Border Gateway Protocol(S-BGP) Real World Performance and Deployment Issues[EB/OL]. .
|
| [6] |
KRUEGEL C, MUTZ D, ROBERTSON W, et al.Topology-Based Detection of Anomalous BGP Messages[M]//Springer. Recent Advances in Intrusion Detection. Heidelberg: Springer-Verlag, 2003: 17-35.
|
| [7] |
LIU Yujing, WANG Zhilin, LI Nan.A Case Study of Detecting and Characterizing Large-Scale Prefix Hijackings in the Internet[C]//ACM. The 2017 VI International Conference on Network, Communication and Computing, December 8-10, 2017, Kunming, China. New York: ACM, 2017: 110-114.
|
| [8] |
LAD M, MASSEY D, PEI Dan, et al. PHAS: A Prefix Hijack Alert System[EB/OL]. , 2019-6-13.
|
| [9] |
ROUTE Views. University of Oregon Route Views Archive Project[EB/OL]. .
|
| [10] |
RIPE NCC. RIS RAW DATA[EB/OL]. , 2019-6-13.
|
| [11] |
ZHENG Changxi, JI Lusheng, PEI Dan, et al.A Light-Weights Distributed Scheme for Detecting IP Prefix Hijacks in Real-Time[C]//ACM. The 2007 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, August 27-31, 2007 , Kyoto, Japan. New York: ACM, 2007: 277-288.
|
| [12] |
ZHANG Zheng, ZHANG Ying, HU Y C, et al.iSPY: Detecting IP Prefix Hijacking on My Own[J]. IEEE/ACM Transactions on Networking, 2010, 18(6): 1815-1828.
|
| [13] |
HU Xin, MAO Z M.Accurate Real-time Identification of IP Prefix Hijacking[C]//IEEE. 2007 IEEE Symposium on Security and Privacy, May 20-23, 2007, Berkeley, USA. NJ: IEEE, 2007: 3-17.
|
| [14] |
SHI Xingang, XIANG Yang, WANG Zhiliang, et al.Detecting Prefix Hijackings in the Internet with Argus[C]//ACM. The 2012 ACM Internet Measurement Conference, November 14-16, 2012, Boston, Massachusetts, USA . New York: ACM, 2012: 15-28.
|
| [15] |
CAIDA. CAIDA Prefix2as[EB/OL]. , 2019-6-13.
|
| [16] |
CAIDA. CAIDA AS Relationships[EB/OL]. , 2019-6-13.
|
 ), Yixuan GE2, Jinshu SU1
), Yixuan GE2, Jinshu SU1