| [1] |
Rekhter Y, Li T, Hares S.A Border Gateway Protocol 4(BGP-4)[S]. RFC 4271, 1995.
|
| [2] |
刘欣, 王小强, 朱培栋,等. 互联网域间路由系统安全态势评估[J]. 计算机研究与发展, 2009, 46(10):1669-1677.
|
| [3] |
齐峰,马春光,周永进,等. 一种基于网络编码的机会社会网络路由算法[J]. 信息网络安全,2015,(2):51-56.
|
| [4] |
王小强, 朱培栋, 卢锡城. 防范路由劫持的协同监测方法[J]. 软件学报, 2014, 25(3): 642-661.
|
| [5] |
Kent S, Lynn C, Seo K.Secure Border Gateway Protocol (S-BGP)[J]. IEEE journal on selected areas in communications, 2000, 18(4):103-116.
|
| [6] |
Oti S B, Hayfron-Acquah J B. Practical Security Approaches against Border Gateway Protocol (BGP) Session Hijacking Attacks between Autonomous Systems[J]. Journal of Computer & Communications, 2014, (2):10-21.
|
| [7] |
Kranakis E, Wan T, Oorschot P C.On Interdomain Routing Security and Pretty Secure BGP (psBGP)[J]. ACM Trans. Information and System Security (TISSEC), 2007, 10(3):1-41.
|
| [8] |
Karlin J, Forrest S, Rexford J.Pretty good BGP: Improving BGP by Cautiously Adopting Routes[C]//Proc. of the IEEE ICNP, 2006. 283-292.
|
| [9] |
Subramanian L, Roth V, Stoica I, et al.Listen and Whisper: Security Mechanisms for BGP[C]//Proc. of the NSDI, 2004.
|
| [10] |
赵玉东,徐恪,朱亮. 一种路由设备服务可信属性定义方法与可信路由协议设计[J]. 信息网络安全,2015,(1):24-31.
|
| [11] |
Mayer D. University of Oregon Route Views Project [EB/OL]. .
|
| [12] |
RIPE NCC. RIPE RIS Project [EB/OL]. .
|
| [13] |
BGP. Telstra CIDR Report [EB/OL]. .
|
| [14] |
Cymru Team. The Team Cymru Bogon Route Server Project[EB/OL]. .
|
| [15] |
Renesys. Routing Intelligence [EB/OL]. .
|
| [16] |
Lad M, Massey D, Pet D.PHAS: A prefix hijack alert system[C]//Proc. of the 15th USENIX Security Symposium, USENIX-SS’06. Vancouver, BC, Canada, 2006:108-119.
|
| [17] |
BGP Mon. BGP Mon part of OpenDNS [EB/OL]. .
|
| [18] |
唐敏,施新刚,喻星,等.路由监控分析系统的设计和实现[J].计算机科学,2008,(1): 56-59.
|
| [19] |
Shi X, Xiang Y, Wang Z, et al.Detecting prefix hijackings in the internet with argus[C]//Proceedings of the 2012 ACM conference on Internet measurement conference. ACM, 2012: 15-28.
|
| [20] |
Deng W, Zhu P, Lu X.ROUSSEAU: A monitoring system for inter-domain routing security[C]//Communication Networks and Services Research Conference, 2008. CNSR 2008. 6th Ann ual. IEEE, 2008: 255-262.
|
| [21] |
Fixedorbit. Fixedorbit [EB/OL]. .
|
| [22] |
CAIDA. CAIDA [EB/OL]. .
|
| [23] |
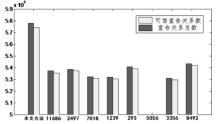
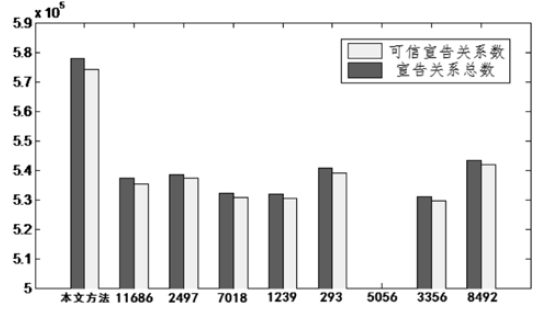
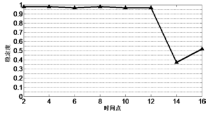
燕强, 王小强, 蔡开裕,等. 基于稳定度的可信AS-IP宣告关系构建方法[J]. 计算机与现代化, 2011, (11):93-96.
|
| [24] |
苏彬庭,方禾,许力. 基于Q-Learning的无线传感器网络生命周期平衡路由[J]. 信息网络安全,2015,(4):74-77.
|
| [25] |
王小强. 互联网域间路由系统动态行为研究与机制设计[D].长沙:国防科学技术大学,2014.
|
| [26] |
Hu X, Mao Z M, Hu X.Accurate Real-time Identification of IP Prefix Hijacking[C]// Proceedings of the 2007 IEEE Symposium on Security and Privacy. IEEE Computer Society, 2007:3-17.
|