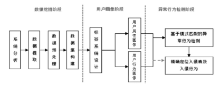
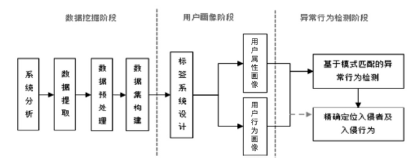
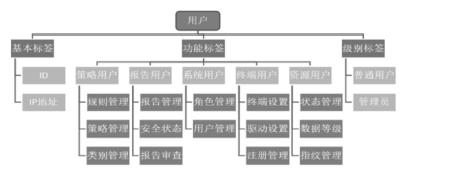
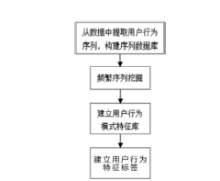
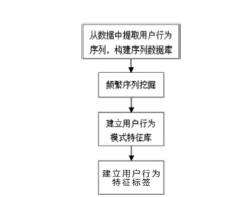
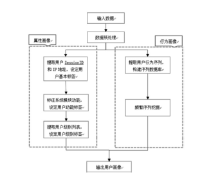
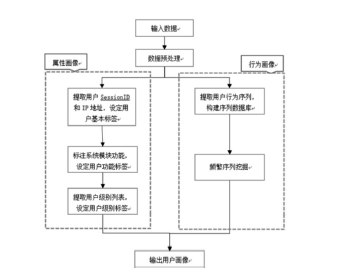
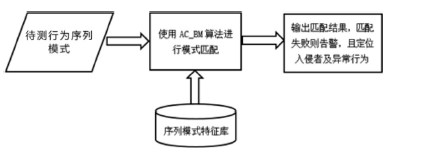
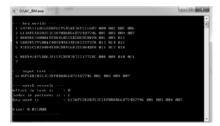
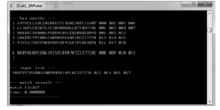
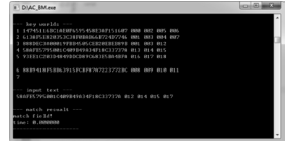
| [1] |
杨雅辉,黄海珍,沈晴霓,等. 基于增量式GHSOM神经网络模型的入侵检测研究[J].计算机学报, 2014, 37(5):1216-1224.
|
| [2] |
田志宏,王佰玲,张伟哲,等. 基于上下文验证的网络入侵检测模型[J].计算机研究与发展, 2013, 50(3):498-508.
|
| [3] |
张玲,白中英,罗守山,等.基于粗糙集和人工免疫的集成入侵检测模型[J].通信学报,2013,34(9): 166-176.
|
| [4] |
管磊,胡光俊,王专. 基于大数据的网络安全态势感知技术研究[J]. 信息网络安全,2016(9):45-50.
|
| [5] |
付鹏,林政,袁凤程,等.基于卷积神经网络和用户信息的微博话题追踪模型[J].模式识别与人工智能,2017,30(1):73-80.
|
| [6] |
李殿伟,何明亮,袁方. 基于角色行为模式挖掘的内部威胁检测研究[J]. 信息网络安全,2017(3):27-32.
|
| [7] |
曾鸿, 吴苏倪.基于微博的大数据用户画像与精准营销[J]. 现代经济信息,2016,(16):306-308.
|
| [8] |
张万军. 基于大数据的个人信用风险评估模型研究[D]. 北京:对外经济贸易大学,2015.
|
| [9] |
姬浩博, 王俊红. 一种改进的PrefixSpan算法及其在Web用户行为模式挖掘中的应用[J].计算机科学,2016,43(1):25-29.
|
| [10] |
HAN J, PEI J, MORTAZVIASL B, et al.Frequent Pattern Projected Sequential Pattern Mining[C]//ACM. the 6ACM-SIGKDD International Conference on Knowledge Discovery and Data Mining, August 10-13, 2015, Hilton, Sydney, Australia.New York: ACM,2000: 355-359.
|
| [11] |
PEI J,HAN J,MORTAZAVIASL B,et al.Mining Sequential Patterns by Pattern-growth: the PrefixSpan Approach[J].IEEE Transactions On Knowledge and Data Engineering,2004,16(11) : 1424-1440.
|
| [12] |
王一霈,石春戴,上静,等.一种改进的针对中文编码的Wu-Manber多模式匹配算法[J].小型微型计算机系统, 2015, 36(4):778-781.
|