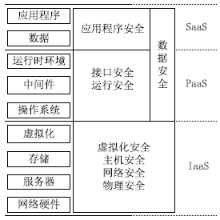
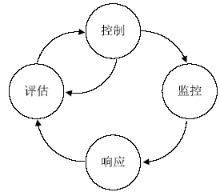
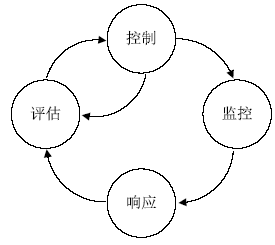
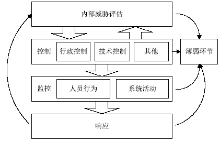
| [1] |
Anonymous. Nine key cyber threats identified in Verizon data breach report[J].Health Management Technology, 2014, 35(6):22.
|
| [2] |
王辉,胥扬,杨光灿,等. 基于Insider Threat的安全防御体系结构研究[J]. 微计算机信息,2012, (7):9-11.
|
| [3] |
D. Trcek.An integral framework for information systems security management[J]. Computers & Security, 2003, 22(4): 337-360.
|
| [4] |
李兴华,马建峰.WAPI 实施方案中的密钥协商协议的安全性分析[J]. 计算机学报,2006,29(4):576-580.
|
| [5] |
Rees J, Bandyopadhyay S, Spafford E H.A Policy Framework for Information Security[J]. Communications of the ACM, 2003, 46(7):101-106.
|
| [6] |
Cappelli D M, Moore A P, Trzeciak R F.Insider Threats in the Sdlc: Lessons Learned from Actual Incidents of Fraud, Theft of Sensitive Information and It Sabotage[R]. USA: Software Engineering Institute of Carnegie Mellon University, 2006.
|
| [7] |
Keeney M, Kowalski E, Cappelli D, et al.Insider Threat Study: Computer System Sabotage in Critical Infrastructure Sectors [R]. USA: Secret Service and CERT Coordination Center, 2005.
|
| [8] |
王斌君. 信息安全[M].北京:高等教育出版社,2008.
|
| [9] |
郭平,但光祥. 云计算中的混合加密算法[J].吉林大学学报(工学版),2012,42(S1):327-331.
|
| [10] |
HUANG Q L, MA Z F, YANG Y X, et al.Secure and Privacy-preserving DRM Scheme Using Homomorphic Encryption in Cloud Computing[J]. The Journal of China Universities of Posts and Telecommunications, 2013, (6):88-95.
|
| [11] |
Goyal V, Pandey O, Sahai A, et al.Attribute-based Encryption for Fine- grained Access Control of Encrypted Datap[C]//Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM Press, 2007.
|
| [12] |
Goyal V, Pandey O, Sahai A, et al.Attribute-based Encryption for Fine- grained Access Control of Encrypted Datap[C]//Proceedings of the 13th ACM Conference on Computer and Communications Security, New York: ACM Press, 2007.
|
| [13] |
彭伟. 面向云计算安全的同态加密技术应用研究[D]. 重庆:重庆大学,2014.
|
| [14] |
Ferraiolo D F, Kuhn D R.Role-based access control[C]//Proceedings of the15th National Computer Security Conference USA: Baltimore, 1992.
|
| [15] |
Sandhu R, Coyne E, Feinstein H, et al.Role-based Access Control Models[J]. IEEE Computer,1996, 29(2):38-47.
|
| [16] |
李凤华,苏铓,史国振,等.访问控制模型研究进展及发展趋势[J].电子学报,2012,(4):805-813.
|