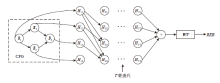
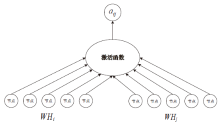
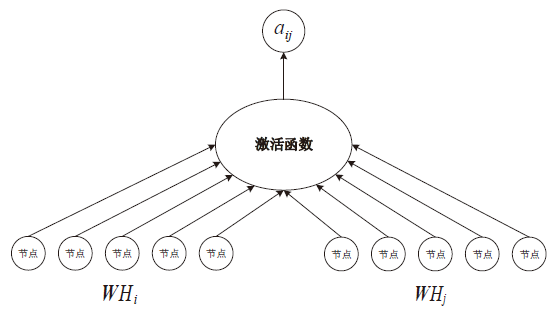
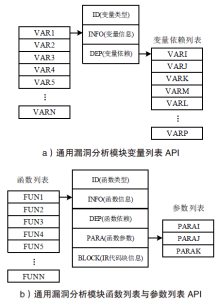
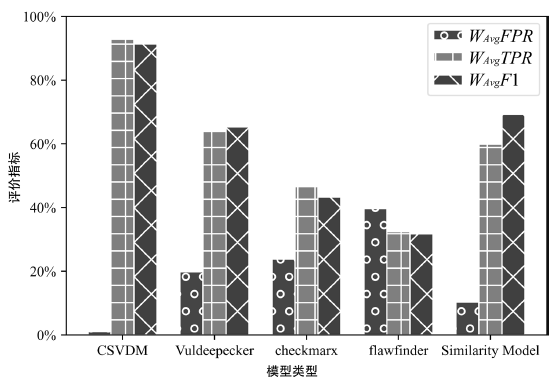
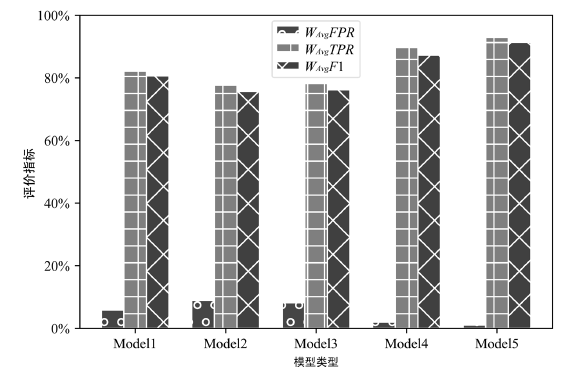
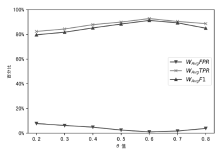
| [1] |
LIU Jian, SU Purui, YANG Min, et al. Software and Cyber Security-A Survey[J]. Journal of Software, 2018, 29(1): 42-68.
|
|
刘剑, 苏璞睿, 杨珉, 等. 软件与网络安全研究综述[J]. 软件学报, 2018, 29(1): 42-68.
|
| [2] |
KULENOVIC M, DONKO D. A Survey of Static Code Analysis Methods for Security Vulnerabilities Detection[C]// IEEE. 2014 37th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO). New York: IEEE, 2014: 1381-1386.
|
| [3] |
MA Mingrui, HAN Lansheng, QIAN Yekui. CVDF DYNAMIC-A Dynamic Fuzzy Testing Sample Generation Framework Based on Bi-LSTM and Genetic Algorithm[J]. Sensors, 2022, 22(3): 12-25.
|
| [4] |
LI Zhen, ZOU Deqing, XU Shouhuai, et al. Vulpecker: An Automated Vulnerability Detection System Based on Code Similarity Analysis[C]// ACM. Proceedings of the 32nd Annual Conference on Computer Security Applications. New York: ACM, 2016: 201-213.
|
| [5] |
XIA Zhiyang, YI Ping, YANG Tao. Static Vulnerability Detection Based on Neural Network and Code Similarity[J]. Computer Engineering, 2019, 45(12): 141-146.
|
|
夏之阳, 易平, 杨涛. 基于神经网络与代码相似性的静态漏洞检测[J]. 计算机工程, 2019, 45(12): 141-146.
|
| [6] |
LIANG Hongliang, WANG Lei, WU Dongyang, et al. MLSA: A Static Bugs Analysis Tool Based on LLVM IR[C]// IEEE. 2016 17th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD). New York: IEEE, 2016: 407-412.
|
| [7] |
FANG Zhejun, LIU Qixu, ZHANG Yuqing, et al. A Static Technique for Detecting Input Validation Vulnerabilities in Android Apps[J]. Science China Information Sciences, 2017, 60(5): 1-16.
|
| [8] |
GRIECO G, GRINBLAT G L, UZAL L, et al. Toward Large-Scale Vulnerability Discovery Using Machine Learning[C]// ACM. Proceedings of the Sixth ACM Conference on Data and Application Security and Privacy. New York: ACM, 2016: 85-96.
|
| [9] |
YAMAGUCHI F, MAIER A, GASCON H, et al. Automatic Inference of Search Patterns for Taint-Style Vulnerabilities[C]// IEEE. 2015 IEEE Symposium on Security and Privacy. New York: IEEE, 2015: 797-812.
|
| [10] |
LI Zhen, ZOU Deqing, XU Shouhuai, et al. Vuldeepecker: A Deep Learning-Based System for Vulnerability Detection[J]. (2018-01-05)[2022-06-22]. https://arxiv.org/abs/1801.01681v1.
|
| [11] |
LIN Guanjun, ZHANG Jun, LUO Wei, et al. Cross-Project Transfer Representation Learning for Vulnerable Function Discovery[J]. IEEE Transactions on Industrial Informatics, 2018, 14(7): 3289-3297.
|
| [12] |
ZHOU Yaqin, LIU Shangqing, SIOW J, et al. Devign: Effective Vulnerability Identification by Learning Comprehensive Program Semantics via Graph Neural Networks[J]. Advances in Neural Information Processing Systems, 2019(32): 12-18.
|
| [13] |
MIKOLOV T, CHEN Kai, CORRADO G, et al. Efficient Estimation of Word Representations in Vector Space[EB/OL]. (2012-09-07)[2022-06-22]. https://arxiv.org/abs/1301.3781.
|
| [14] |
TANG Jian, QU Meng, WANG Mingzhe, et al. LINE: Large-Scale Information Network Embedding[EB/OL]. (2015-03-12)[2022-06-22]. https://arxiv.org/abs/1503.03578.
|
| [15] |
NIST. NVD[EB/OL]. [2022-06-29]. https://nvd.nist.gov/.
|
 ), ZHU Dongzhao5
), ZHU Dongzhao5