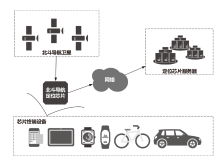
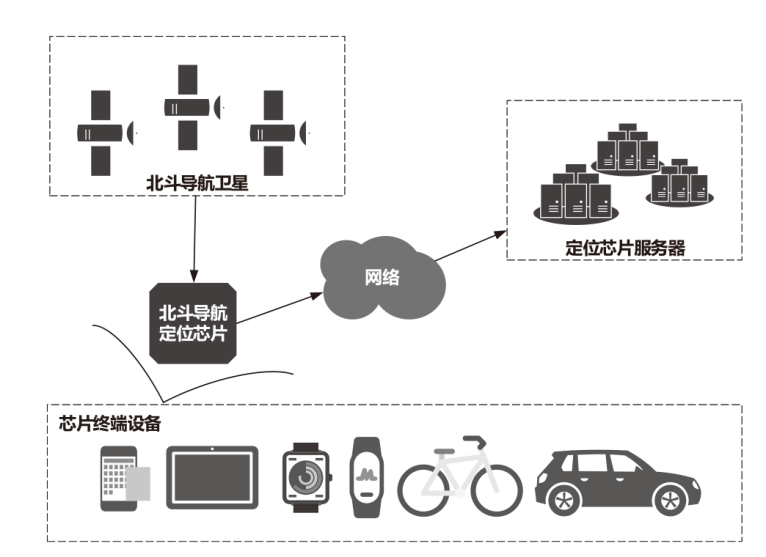
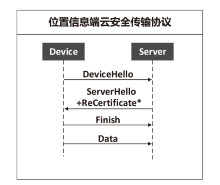
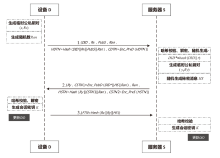
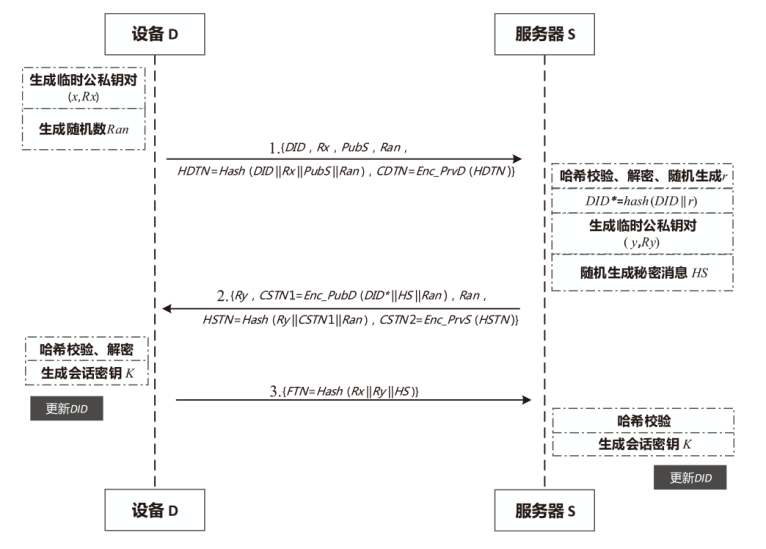
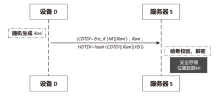
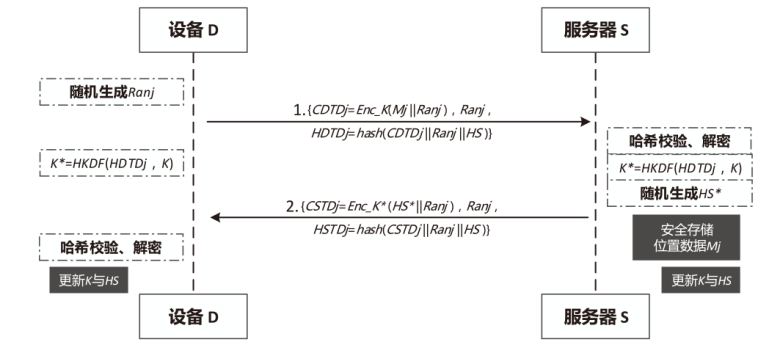
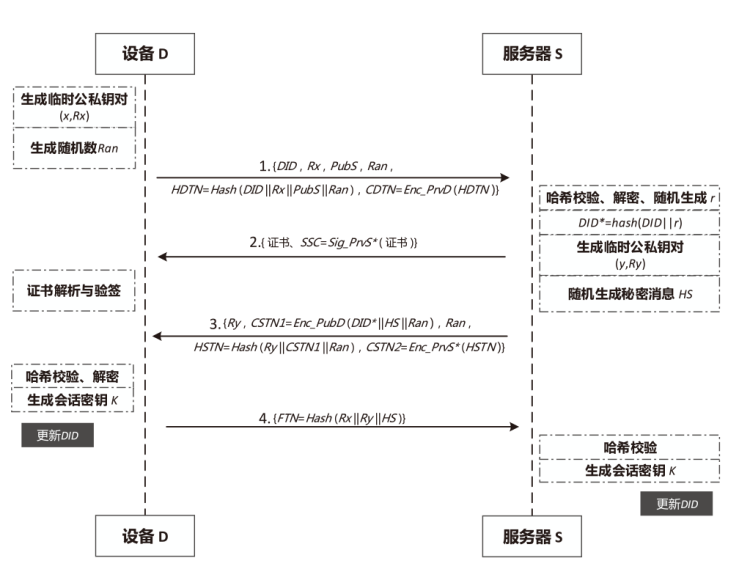
| [1] |
VERMA P, GUPTA D S. An Improved Certificateless Mutual Authentication and Key Agreement Protocol for Cloud-Assisted Wireless Body Area Networks[J]. Wireless Personal Communications, 2023, 131(4): 2399-2426.
doi: 10.1007/s11277-023-10536-8
|
| [2] |
ZHOU Yuxiang, TAN Haowen, KARUNARATHINA C A A I. A Secure Authentication and Key Agreement Scheme with Dynamic Management for Vehicular Networks[EB/OL]. (2023-02-22) [2023-06-20]. https://doi.org/10.1080/09540091.2023.2176825.
|
| [3] |
WANG An, DONG Yongyin, ZHU Liehuang, et al. APT Backdoor for Block Cipher Software and Its Countermeasures[J]. Journal of Cryptologic Research, 2021, 8(1): 65-75.
|
|
王安, 董永银, 祝烈煌, 等. 一种针对分组密码软件的APT后门及其防范[J]. 密码学报, 2021, 8(1):65-75.
doi: 10.13868/j.cnki.jcr.000420
|
| [4] |
MA Guojun, BAI Lei, PEI Qingqi, et al. An End-to-End Security Scheme of the Internet of Things[J]. Netinfo Security, 2017, 17(10): 13-21.
|
|
马国峻, 白磊, 裴庆祺, 等. 一种物联网端到端安全方案[J]. 信息网络安全, 2017, 17(10): 13-21.
|
| [5] |
ZHU Ying, YAN Yan, WAN Fang, et al. Comparison of Domestic Password and International Password Performance under Instant Messaging System[J]. Information Technology and Informatization, 2022(9): 164-167.
|
|
朱颖, 严妍, 万芳, 等. 即时通信系统下国密与国际密码性能比较[J]. 信息技术与信息化, 2022(9):164-167.
|
| [6] |
GAO Mengzhou. Research on Selective and Stochastic Encryption Strategies for the Resource-Constrained Control Systems Security[D]. Hangzhou: Zhejiang University, 2017.
|
|
高梦州. 面向资源受限控制系统安全的选择性及随机性加密策略研究[D]. 杭州: 浙江大学, 2017.
|
| [7] |
SAQIB M, MOON A H. A Systematic Security Assessment and Review of Internet of Things in the Context of Authentication[EB/OL]. (2022-12-13) [2023-06-20]. https://doi.org/10.1016/j.cose.2022.103053.
|
| [8] |
HOGLUND J, FURUHED M, RAZA S. Lightweight Certificate Revocation for Low-Power IoT with End-to-End Security[J]. Journal of Information Security and Applications, 2023, 73: 1-12.
|
| [9] |
DENG Dong. Research on Authentication and Key Management Based on Non-Traditional Certificates for WSN[D]. Chengdu: University of Electronic Science and Technology of China, 2022.
|
|
邓东. WSN中基于非传统证书的身份认证和秘钥管理关键技术研究[D]. 成都: 电子科技大学, 2022.
|
| [10] |
PERAZZO P, RIGHETTI F, MANNA M L, et al. Performance Evaluation of Attribute-Based Encryption on Constrained IoT Devices[J]. Computer Communications, 2021, 170: 151-163.
doi: 10.1016/j.comcom.2021.02.012
URL
|
| [11] |
AZIZ M F, KHAN A N, SHUJA J, et al. A Lightweight and Compromise-Resilient Authentication Scheme for IoTs[EB/OL]. (2019-11-25) [2023-06-20]. https://doi.org/10.1002/ett.3813.
|
| [12] |
XU Guodong. Research on Lightweight IoT Secure Transmission Protocol[D]. Nanjing: Nanjing University Of Information Science &Technology, 2022.
|
|
许国栋. 轻量级物联网安全传输协议研究[D]. 南京: 南京信息工程大学, 2022.
|
| [13] |
LI Fengyin, YU Xinying, CUI Yang, et al. An Anonymous Authentication and Key Agreement Protocol in Smart Living[J]. Computer Communications, 2022, 186: 110-120.
doi: 10.1016/j.comcom.2022.01.019
URL
|
| [14] |
SALEEM M A, LI Xiong, AYUB M F, et al. An Efficient and Physically Secure Privacy-Preserving Key-Agreement Protocol for Vehicular Ad-Hoc Network[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(9): 9940-9951.
doi: 10.1109/TITS.2023.3266030
URL
|
| [15] |
VINOTH R, DEBORAH L J. An Efficient Key Agreement and Authentication Protocol for Secure Communication in Industrial IoT Applications[J]. Journal of Ambient Intelligence and Humanized Computing, 2023, 14: 1431-1443.
doi: 10.1007/s12652-021-03167-z
|
| [16] |
BRAEKEN A. Authenticated Key Agreement Protocols for Dew-Assisted IoT Systems[EB/OL]. (2022-02-28) [2023-06-20]. https://doi.org/10.1007/s11227-022-04364-z.
|
| [17] |
RANA M, MAMUN Q, ISLAM R. Lightweight Cryptography in IoT Networks: A Survey[J]. Future Generations Computer Systems: FGCS, 2022, 129: 77-89.
|
 ), MIAO Zhangwang3, GAN Jinghong4,5
), MIAO Zhangwang3, GAN Jinghong4,5