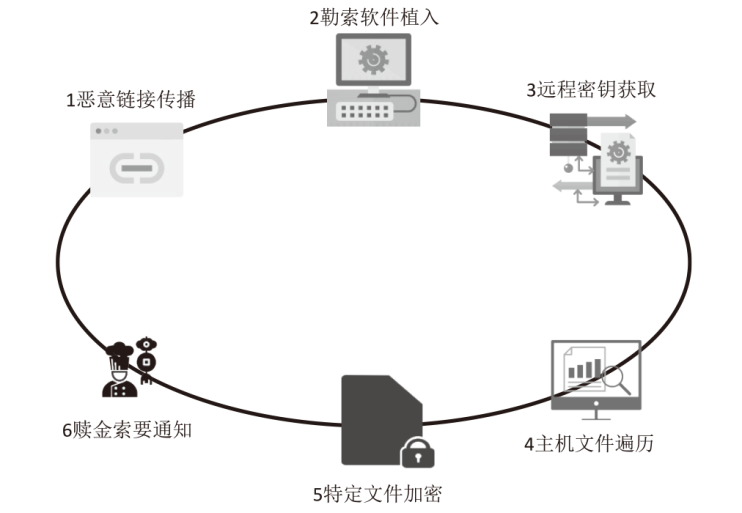
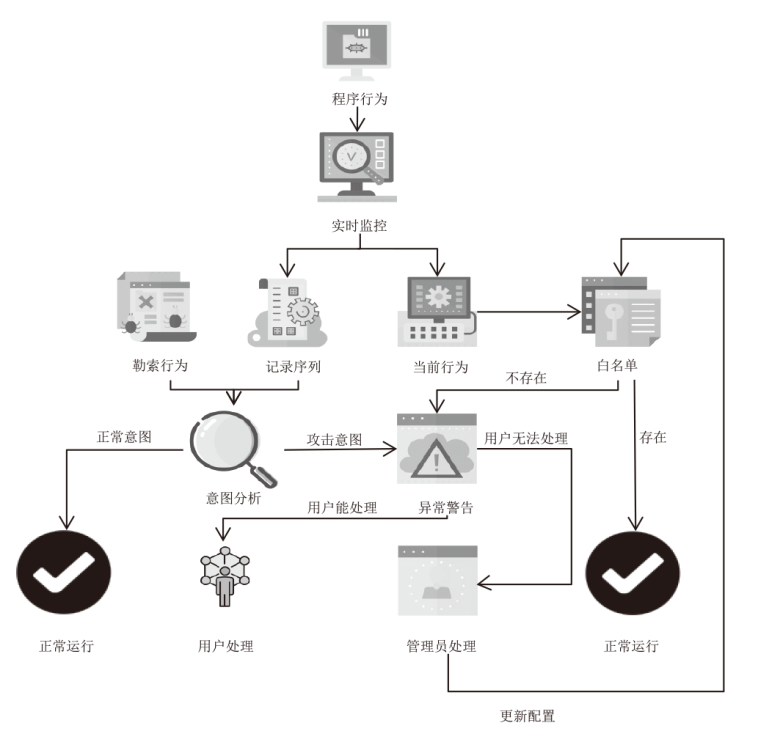
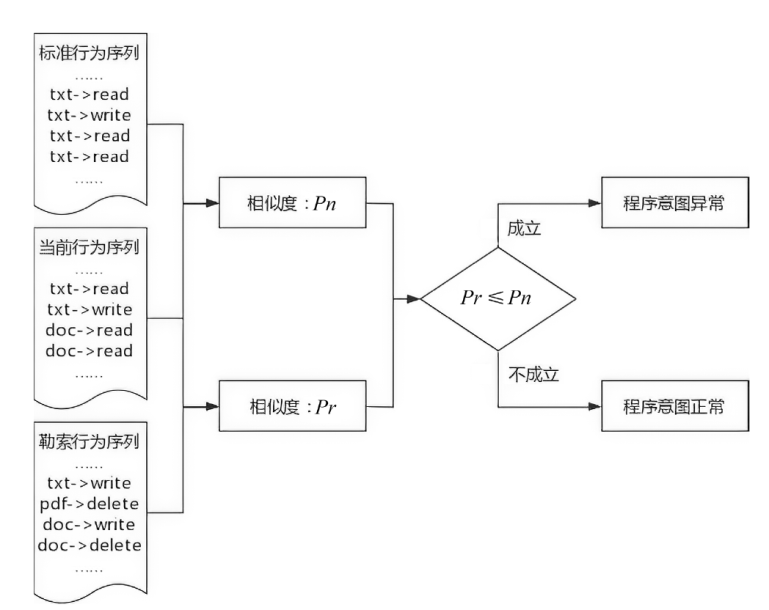
| [1] |
MELAND P H, BAYOUMY Y F F, SINDRE G. The Ransomware-as-a-Service Economy within Thedarknet[J]. Computers & Security, 2020, 92: 101762-101780.
doi: 10.1016/j.cose.2020.101762
URL
|
| [2] |
GUO Chun, CHEN Changqing, SHEN Guowei, et al. A Ransomware Classification Method Based on Visualization[J]. Netifo Security, 2020, 20(4): 31-39.
|
|
郭春, 陈长青, 申国伟, 等. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39.
|
| [3] |
FORTINET. The 2021 Ransomware Survey Report[R]. Sunnyvale:Fortinet, 1290667-0-0-EN, 2021.
|
| [4] |
MCINTOSH T, KAYES A S M, CHEN Y P P, et al. Dynamic User-Centric Access Control for Detection of Ransomware Attacks[J]. Computers & Security, 2021, 111: 102461-102476.
doi: 10.1016/j.cose.2021.102461
URL
|
| [5] |
AL-RIMY B A S, MAAROF M A, SHAID S Z M. Ransomware Threat Success Factors, Taxonomy, and Countermeasures: A Survey and Research Directions[J]. Computers & Security, 2018, 74: 144-166.
doi: 10.1016/j.cose.2018.01.001
URL
|
| [6] |
DARGAHI T, DEHGHANTANHA A, BAHRAMI P N, et al. A Cyber-Kill-Chain Based Taxonomy of Crypto-Ransomware Features[J]. Journal of Computer Virology and Hacking Techniques, 2019, 15(4): 277-305.
doi: 10.1007/s11416-019-00338-7
|
| [7] |
LEONG R, BEEK C, COCHIN C, et al. Understanding Ransomware and Strategies to Defeat it[J]. White Paper (McAfee Labs), 2016, 16: 1-16.
|
| [8] |
ZIMBA A. Malware-Free Intrusion: A Novel Approach to Ransomware Infection Vectors[J]. International Journal of Computer Science and Information Security, 2017, 15(2): 317-325.
|
| [9] |
ZHANG Pengtao, TAN Ying. Hybrid Concentration based Feature Extraction Approach for Malware Detection[C]// IEEE. 2015 IEEE 28th Canadian Conference on Electrical and Computer Engineering (CCECE). New York: IEEE, 2015: 140-145.
|
| [10] |
WANG Ping, WANG Y S. Malware Behavioural Detection and Vaccine Development by Using a Support Vector Model Classifier[J]. Journal of Computer and System Sciences, 2015, 81(6): 1012-1026.
doi: 10.1016/j.jcss.2014.12.014
URL
|
| [11] |
MCINTOSH T R, JANG-JACCARD J, WATTERS P A. Large Scale Behavioral Analysis of Ransomware Attacks[C]// Springer. 25th International Conference, ICONIP 2018. Berlin:Springer, 2018: 217-229.
|
| [12] |
ANDRONIO N, ZANERO S, MAGGI F. Heldroid: Dissecting and Detecting Mobile Ransomware[C]// Springer. International Symposium on Recent Advances in Intrusion Detection. Berlin:Springer, 2015: 382-404.
|
| [13] |
PRAKASH K P, NAFIS T, BISWAS S S. Preventive Measures and Incident Response for Locky Ransomware[J]. International Journal of Advanced Research in Computer Science, 2017, 8(5): 392-395.
|
| [14] |
SCAIFE N, CARTER H, TRAYNOR P, et al. Cryptolock (and Drop It): Stopping Ransomware Attacks on User Data[C]// IEEE. 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS). New York: IEEE, 2016: 303-312.
|
| [15] |
KAUR R, SINGH M. A Survey on Zero-Day Polymorphic Worm Detection Techniques[J]. IEEE Communications Surveys & Tutorials, 2014, 16(3): 1520-1549.
|
| [16] |
UGARTE-PEDRERO X, GRAZIANO M, BALZAROTTI D. A Close Look at a Daily Dataset of Malware Samples[J]. ACM Transactions on Privacy and Security (TOPS), 2019, 22(1): 1-30.
|
| [17] |
KHARRAZ A, KIRDA E. Redemption: Real-Time Protection Against Ransomware at End-Hosts[C]// Springer. International Symposium on Research in Attacks, Intrusions, and Defenses. Berlin:Springer, 2017: 98-119.
|
| [18] |
SERVOS D, OSBORN S L. Current Research and Open Problems in Attribute-Based Access Control[J]. ACM Computing Surveys (CSUR), 2017, 49(4): 1-45.
|
| [19] |
CONTI M, GANGWAL A, RUJ S. On the Economic Significance of Ransomware Campaigns: A Bitcoin Transactions Perspective[J]. Computers & Security, 2018, 79: 162-189.
doi: 10.1016/j.cose.2018.08.008
URL
|
 ), MIAO Zhangwang3, GAN Jinghong4,5, MA Cunqing1
), MIAO Zhangwang3, GAN Jinghong4,5, MA Cunqing1