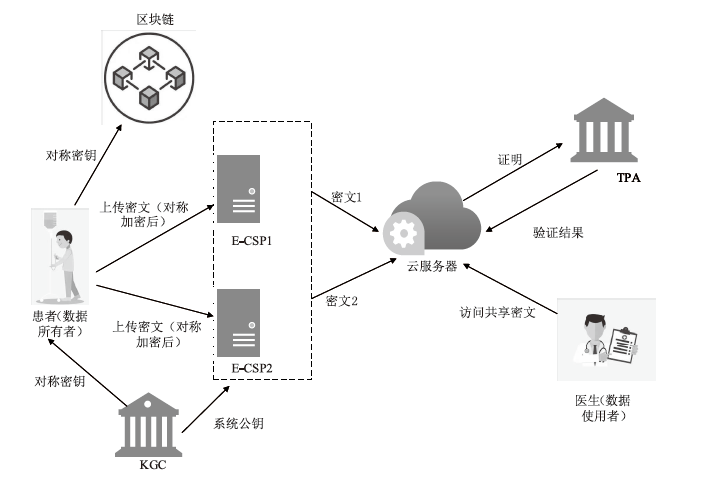
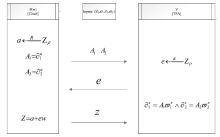
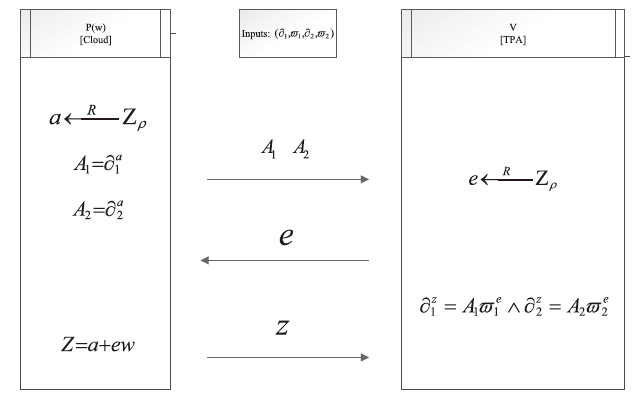
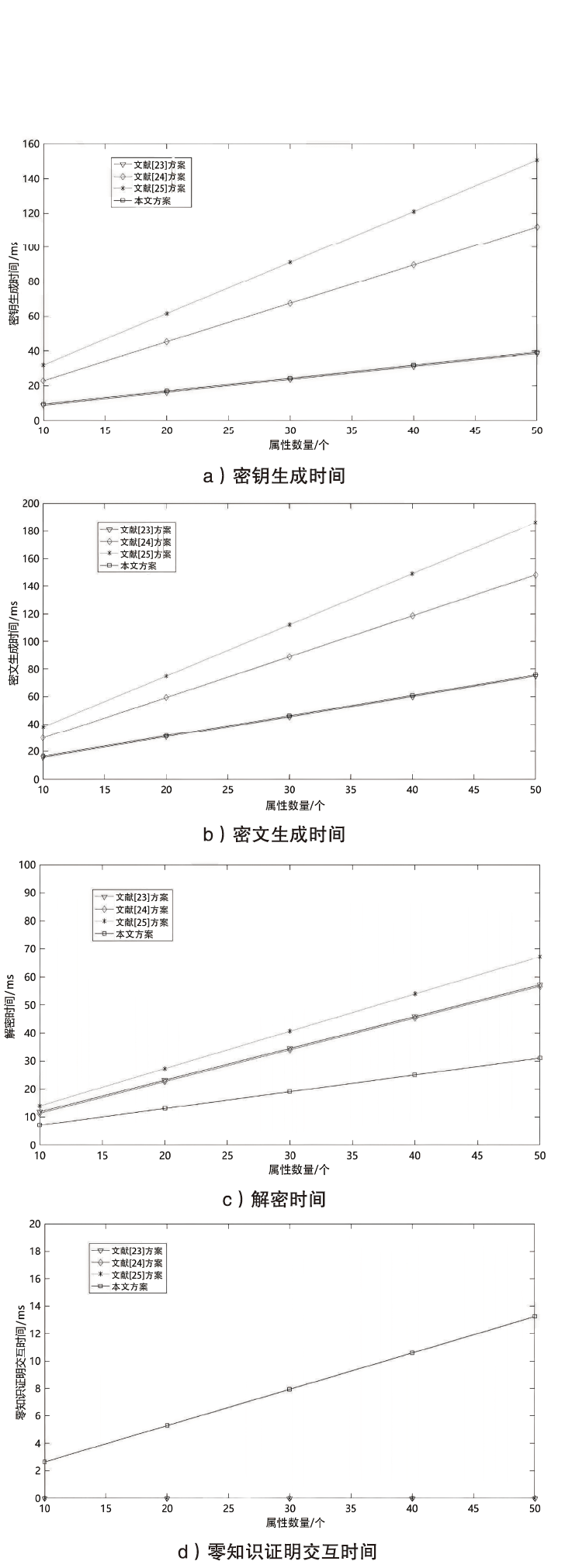
Netinfo Security ›› 2023, Vol. 23 ›› Issue (5): 85-94.doi: 10.3969/j.issn.1671-1122.2023.05.009
Previous Articles Next Articles
An Access Control Scheme for Verifying the Correctness of Outsourcing Encrypted Data in EHR System
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2022-12-10Online:2023-05-10Published:2023-05-15 -
Contact:SHI Runhua E-mail:rhshi@ncepu.edu.cn
CLC Number:
Cite this article
ZHANG Xiaoxu, SHI Runhua. An Access Control Scheme for Verifying the Correctness of Outsourcing Encrypted Data in EHR System[J]. Netinfo Security, 2023, 23(5): 85-94.
share this article
| [1] |
SU Yuan, LI Yanping, ZHANG Kai, et al. A Privacy-Preserving Public Integrity Check Scheme for Outsourced EHRs[J]. Information Sciences, 2021, 542: 112-130.
doi: 10.1016/j.ins.2020.06.043 URL |
| [2] |
XU Jian, WEI Laiwen, WU Wei, et al. Privacy-Preserving Data Integrity Verification by Using Lightweight Streaming Authenticated Data Structures for Healthcare Cyber-Physical System[J]. Future Generation Computer Systems, 2020, 108: 1287-1296.
doi: 10.1016/j.future.2018.04.018 URL |
| [3] |
SICARI S, RIZZARDI A, DINI G, et al. Attribute-Based Encryption and Sticky Policies for Data Access Control in a Smart Home Scenario: A Comparison on Networked Smart Object Middleware[J]. International Journal of Information Security, 2021, 20(5): 695-713.
doi: 10.1007/s10207-020-00526-3 |
| [4] |
QIN Xuanmei, HUANG Yongfeng, YANG Zhen, et al. LBAC: A Lightweight Blockchain-Based Access Control Scheme for the Internet of Things[J]. Information Sciences, 2021, 554: 222-235.
doi: 10.1016/j.ins.2020.12.035 URL |
| [5] |
WANG Tian, ZHANG Guangxue. A Secure IoT Service Architecture with an Efficient Balance Dynamics Based on Cloud and Edge Computing[J]. IEEE Internet of Things Journal, 2018, 6(3): 4831-4843.
doi: 10.1109/JIoT.6488907 URL |
| [6] |
WANG Tian, BHUIYAN M Z A, WANG Guojun, et al. Preserving Balance Between Privacy and Data Integrity in Edge-Assisted Internet of Things[J]. IEEE Internet of Things Journal, 2019, 7(4): 2679-2689.
doi: 10.1109/JIoT.6488907 URL |
| [7] | SANDHU R S, COYNE E J, FEINSTEIN H L, et al. Role-Based Access Control Models[J]. Computer, 1996, 29(2): 38-47. |
| [8] | HU V C, KUHN D R, FERRAIOLO D F, et al. Attribute-Based Access Control[J]. Computer, 2015, 48(2): 85-88. |
| [9] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. 2007 IEEE Symposium on Security and Privacy (SP'07). New York: IEEE, 2007: 321-334. |
| [10] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [11] |
YANG Yifan, SHI Runhua, LI Kunchang, et al. Multiple Access Control Scheme for EHRs Combining Edge Computing with Smart Contracts[J]. Future Generation Computer Systems, 2022, 129: 453-463.
doi: 10.1016/j.future.2021.11.002 URL |
| [12] |
ZHANG Qingyan, ZHONG Hong. AC4AV: A Flexible and Dynamic Access Control Framework for Connected and Autonomous Vehicles[J]. IEEE Internet of Things Journal, 2020, 8(3): 1946-1958.
doi: 10.1109/JIoT.6488907 URL |
| [13] |
LI Jiguo, YAO Wei, ZHANG Yichen, et al. Flexible and Fine-Grained Attribute-Based Data Storage in Cloud Computing[J]. IEEE Transactions on Services Computing, 2016, 10(5): 785-796.
doi: 10.1109/TSC.2016.2520932 URL |
| [14] |
TANG Zhaohui. Secret Sharing-Based IoT Text Data Outsourcing: A Secure and Efficient Scheme[J]. IEEE Access, 2021, 9: 76908-76920.
doi: 10.1109/ACCESS.2021.3075282 URL |
| [15] |
SETHI K, PRADHAN A, BERA P. Practical Traceable Multi-Authority CP-ABE with Outsourcing Decryption and Access Policy Updation[J]. Journal of Information Security and Applications, 2020, 51: 102435-102445.
doi: 10.1016/j.jisa.2019.102435 URL |
| [16] |
LI Jin, HUANG Xinyi, LI Jingwei, et al. Securely Outsourcing Attribute-Based Encryption with Checkability[J]. IEEE Transactions on Parallel and Distributed Systems, 2013, 25(8): 2201-2210.
doi: 10.1109/TPDS.2013.271 URL |
| [17] |
SONG Wenna, XIANG Guangli, LI Ankang, et al. Improved Attribute-Based Encryption Scheme[J]. Computer Science, 2017, 44(1): 167-171.
doi: 10.11896/j.issn.1002-137X.2017.01.032 |
|
宋文纳, 向广利, 李安康, 等. 一种改进的属性加密方案[J]. 计算机科学, 2017, 44(1): 167-171.
doi: 10.11896/j.issn.1002-137X.2017.01.032 |
|
| [18] | LIU Peng, HE Qian, LIU Wangyang, et al. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption[J]. Netinfo Security, 2020, 20(3): 90-97. |
| 刘鹏, 何倩, 刘汪洋, 等. 支持撤销属性和外包解密的 CP-ABE 方案[J]. 信息网络安全, 2020, 20(3): 90-97. | |
| [19] | WANG Le, YANG Zherong, LIU Rongjing, et al. A CP-ABE Privacy Preserving Method for Wearable Devices[J]. Netinfo Security, 2018, 18 (6): 77-84. |
| 王乐, 杨哲荣, 刘容京, 等. 基于属性加密算法的可穿戴设备系统隐私保护方法研究[J]. 信息网络安全, 2018, 18(6): 77-84. | |
| [20] | ZOU Liping, FENG Chaosheng, QIN Zhiguang, et al. CP-ABE Scheme with Fast Decryption for Public Cloud[J]. Journal of Software, 2020, 31(6): 1817-1828. |
| 邹莉萍, 冯朝胜, 秦志光, 等. 面向公有云的支持快速解密的CP-ABE方案[J]. 软件学报, 2020, 31(6): 1817-1828. | |
| [21] | CHEN Yu, MA Xuecheng, TANG Cong, et al. PGC: Decentralized Confidential Payment System with Auditability[C]// Springer. European Symposium on Research in Computer Security. Berlin:Springer, 2020:591-610. |
| [22] | YIN Hongjian, ZHU Yan, WANG Jing, et al. Design and Implementation of a Smart-Contract Voting System Based on Zero-Knowledge Proof[J]. Chinese Journal of Engineering, 2023, 45(4): 632-642. |
| 殷红建, 朱岩, 王静, 等. 基于零知识证明的智能合约投票系统设计与实现[J]. 工程科学学报, 2023, 45(4): 632-642. | |
| [23] | WATERS B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization[C]// Springer. International Workshop on Public Key Cryptography. Berlin:Springer, 2011: 53-70. |
| [24] | LI Jingwei, JIA Chunfu, LI Jin, et al. Outsourcing Encryption of Attribute-Based Encryption with Mapreduce[C]// Springer. International Conference on Information and Communications Security. Berlin:Springer, 2012: 191-201. |
| [25] |
ZHANG Rui, MA Hui, LU Yao. Fine-Grained Access Control System Based on Fully Outsourced Attribute-Based Encryption[J]. Journal of Systems and Software, 2017, 125: 344-353.
doi: 10.1016/j.jss.2016.12.018 URL |
| [1] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [2] | WANG Jian, HUANG Jun. Smart Contract-Based Log Secure Storage and Fair Access Method [J]. Netinfo Security, 2022, 22(7): 27-36. |
| [3] | GUO Baoxia, WANG Jiahui, MA Limin, ZHANG Wei. Research on Dynamic Access Control Model of Sensitive Data Based on Zero Trust [J]. Netinfo Security, 2022, 22(6): 86-93. |
| [4] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [5] | WANG Yong, CHEN Lijie, ZHONG Meiling. Progress in Blockchain Solutions Based on Zero-Knowledge Proof [J]. Netinfo Security, 2022, 22(12): 47-56. |
| [6] | LI Tong, REN Shuai, WANG Gang, MENG Qingyu. Cloud-edge-device Collaborative Integrity Verification Scheme Based on Chameleon Authentication Tree for Streaming Data [J]. Netinfo Security, 2022, 22(1): 37-45. |
| [7] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| [8] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [9] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [10] | ZHANG Shuqing, CAI Zhiwen. Revocable Encryption Scheme Based on Accountability Attribute under Cloud Data [J]. Netinfo Security, 2021, 21(12): 70-77. |
| [11] | WANG Jian, YU Hang, HAN Zhen, HAN Lei. Access Control Methods of Data Sharing in Cloud Storage Based on Smart Contract [J]. Netinfo Security, 2021, 21(11): 40-47. |
| [12] | LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing [J]. Netinfo Security, 2021, 21(11): 58-64. |
| [13] | WEI Zhanzhen, PENG Xingyuan, ZHAO Hong. Resource Access Control Scheme Based on User Credit in SDN [J]. Netinfo Security, 2021, 21(10): 33-40. |
| [14] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [15] | LIU Wenmao, YOU Yang. Shifting Security Protection Mindset and Mechanisms for Novel 5G Infrastructures [J]. Netinfo Security, 2020, 20(9): 67-71. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||