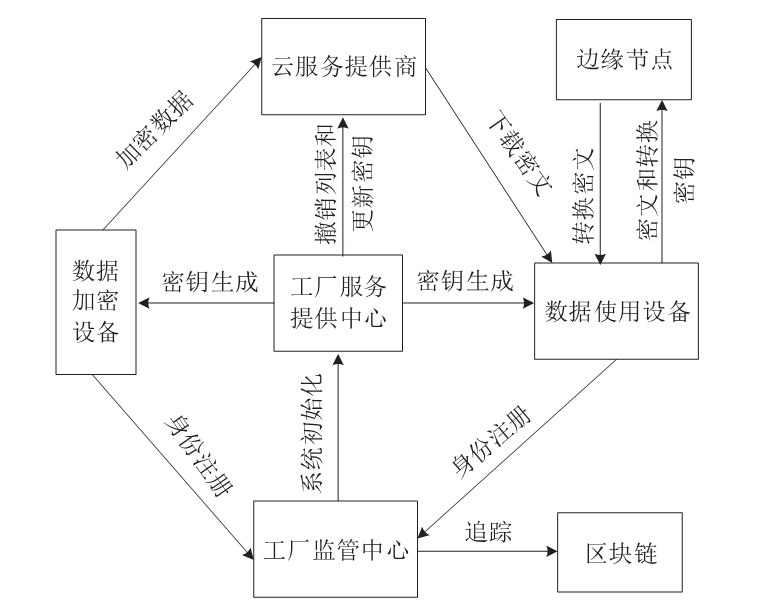
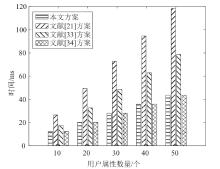
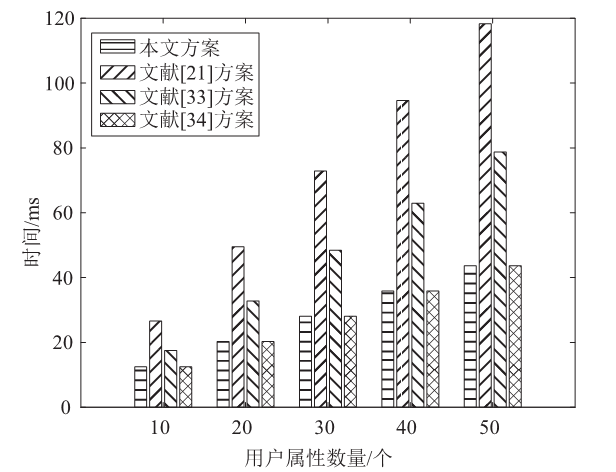
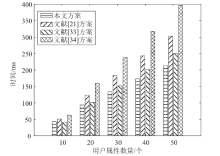
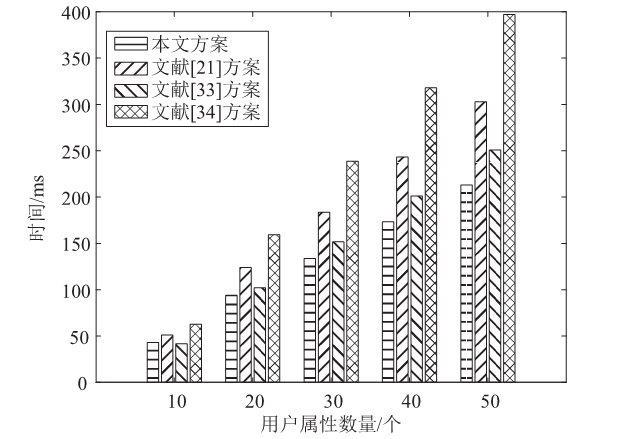
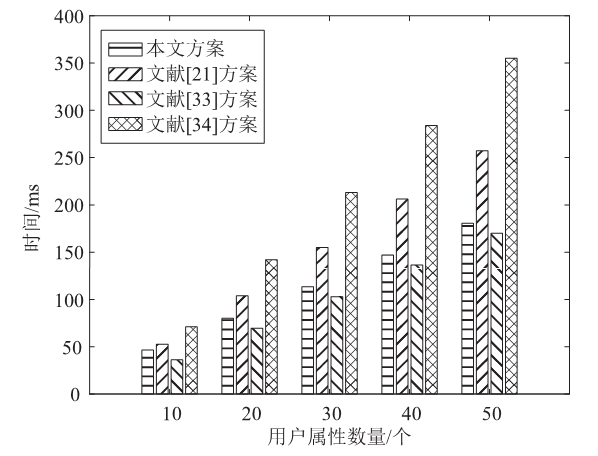
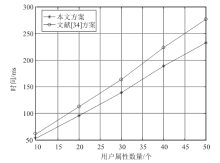
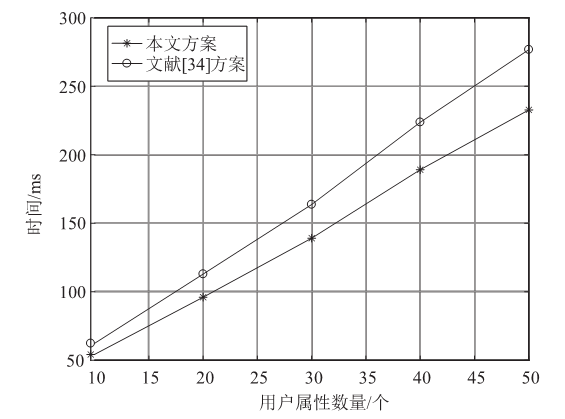
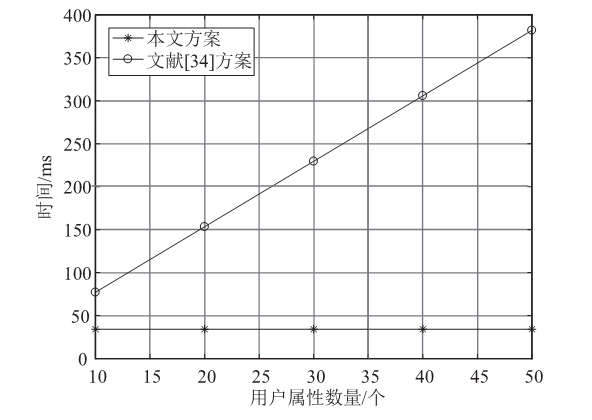
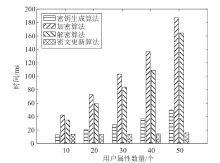
Netinfo Security ›› 2023, Vol. 23 ›› Issue (3): 1-12.doi: 10.3969/j.issn.1671-1122.2023.03.001
Previous Articles Next Articles
An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System
GUO Rui1,2, WEI Xin1,2( ), CHEN Li1,2
), CHEN Li1,2
- 1. School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
2. National Engineering Laboratory for Wireless Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2022-10-27Online:2023-03-10Published:2023-03-14 -
Contact:WEI Xin E-mail:weixin1128211@163.com
CLC Number:
Cite this article
GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System[J]. Netinfo Security, 2023, 23(3): 1-12.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.03.001
| 文献[21]方案 | 文献[33]方案 | |
|---|---|---|
| 密钥生成 | ||
| 加密 | ||
| 解密 | ||
| 外包解密 | — | — |
| 追踪 | — | |
| 密文更新 | — | — |
| 文献[34]方案 | 本文方案 | |
| 密钥生成 | ||
| 加密 | ||
| 解密 | ||
| 外包解密 | ||
| 追踪 | ||
| 密文更新 |
| [1] |
SISINNI E, SAIFULLAH A, HAN S, et al. Industrial Internet of Things: Challenges Opportunities and Directions[J]. IEEE Transactions on Industrial Informatics, 2018, 14(11): 4724-4734.
doi: 10.1109/TII.2018.2852491 URL |
| [2] |
BANERJEE S, BERA B, DAS A K, et al. Private Blockchain-Envisioned Multi-Authority CP-ABE-Based User Access Control Scheme in IIoT[J]. Computer Communications, 2021, 169: 99-113.
doi: 10.1016/j.comcom.2021.01.023 URL |
| [3] | KARMAKAR A, DEY N, BARAL T, et al. Industrial Internet of Things: A Review[C]// IEEE. 2019 International Conference on Opto-Electronics and Applied Optics(Optronix). New York: IEEE. 2019: 1-6. |
| [4] |
ZHENG Dong, ZHU Tianze, GUO Rui. Public Key Searchable Encryption Scheme in Blockchain-Enabled Multi-User Environment[J]. Journal on Communications, 2021, 42(10): 140-152.
doi: 10.11959/j.issn.1000-436x.2021130 |
|
郑东, 朱天泽, 郭瑞. 基于区块链的多用户环境中公钥可搜索加密方案[J]. 通信学报, 2021, 42(10):140-152.
doi: 10.11959/j.issn.1000-436x.2021130 |
|
| [5] |
WAN Jiafu, LI Jiapeng, IMRAN M, et al. A Blockchain-Based Solution for Enhancing Security and Privacy in Smart Factory[J]. IEEE Transactions on Industrial Informatics, 2019, 15(6): 3652-3660.
doi: 10.1109/TII.9424 URL |
| [6] |
YU Keping, TAN Liang, ALOQAILY M, et al. Blockchain-Enhanced Data Sharing with Traceable and Direct Revocation in IIoT[J]. IEEE Transactions on Industrial Informatics, 2021, 17(11): 7669-7678.
doi: 10.1109/TII.2021.3049141 URL |
| [7] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. EUROCRYPT 2005. Heidelberg: Springer, 2005: 457-473. |
| [8] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. 2007 IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [9] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control Of Encrypted Data[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [10] |
LI Yixin, ZHANG Yinghui, HU Lingyun, et al. Fine-Grained Bilateral Access Control Scheme in Online Consultation Environment[J]. Computer Engineering and Applications, 2022, 58(17): 139-147.
doi: 10.3778/j.issn.1002-8331.2106-0033 |
|
李艺昕, 张应辉, 胡凌云, 等. 在线问诊环境下细粒度双边访问控制方案[J]. 计算机工程与应用, 2022, 58(17):139-147.
doi: 10.3778/j.issn.1002-8331.2106-0033 |
|
| [11] |
WU Jingwen, YIN Xinchun, NING Jianting. Traceable and Revocable Multi-Authority Attribute-Based Encryption Scheme for Vehicular Ad Hoc Networks[J]. Journal of Computer Applications, 2022, 42(6): 1695-1701.
doi: 10.11772/j.issn.1001-9081.2021061449 |
|
吴静雯, 殷新春, 宁建廷. 车载自组网中可追踪可撤销的多授权中心属性基加密方案[J]. 计算机应用, 2022, 42(6):1695-1701.
doi: 10.11772/j.issn.1001-9081.2021061449 |
|
| [12] |
HAN Dezhi, PAN Nannan, LI K C. A Traceable and Revocable Ciphertext-Policy Attribute-based Encryption Scheme Based on Privacy Protection[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(1): 316-327.
doi: 10.1109/TDSC.2020.2977646 URL |
| [13] | NING Jianting, CAO Zhenfu, DONG Xiaolei, et al. Large Universe Ciphertext-Policy Attribute-Based Encryption with White-Box Traceability[C]// Springer. Computer Security-ESORICS 2014. Heidelberg: Springer, 2014: 55-72. |
| [14] | CHEUNG L, NEWPORT C. Provably Secure Ciphertext Policy ABE[C]// ACM. 14th ACM Conference on Computer and Communications Security. New York: ACM, 2007: 456-465. |
| [15] | BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[D]. Haifa: Israel Institute of Technology, 1996. |
| [16] | ZHANG Yinghui, DENG R H, XU Shengmin, et al. Attribute-Based Encryption for Cloud Computing Access Control: A Survey[J]. Association for Computing Machinery, 2020, 53(4): 1-41. |
| [17] | ZHANG Yunru, HE Debiao, CHOO K K R. BaDS: Blockchain-Based Architecture for Data Sharing with ABS and CP-ABE in IoT[J]. Wireless Communications and Mobile Computing, 2018(2): 1-9. |
| [18] |
GUO Lifeng, YANG Xiaoli, YAU W C. TABE-DAC: Efficient Traceable Attribute-Based Encryption Scheme with Dynamic Access Control Based on Blockchain[J]. IEEE Access, 2019, 9: 8479-8490.
doi: 10.1109/Access.6287639 URL |
| [19] | LIU Zechao, WANG Xuan, CUI Lei, et al. White-Box Traceable Dynamic Attribute Based Encryption[C]// IEEE. 2017 International Conference on Security, Pattern Analysis, and Cybernetics(SPAC). New York: IEEE, 2017: 526-530. |
| [20] |
LAI Junzuo, DENG R H, GUAN Chaowen, et al. Attribute-Based Encryption with Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(8): 1343-1354.
doi: 10.1109/TIFS.2013.2271848 URL |
| [21] |
ZHANG Yinghui, ZHENG Dong, DENG R H. Security and Privacy in Smart Health: Efficient Policy-Hiding Attribute-Based Access Control[J]. IEEE Internet of Things Journal, 2018, 5(3): 2130-2145.
doi: 10.1109/JIOT.2018.2825289 URL |
| [22] |
LIU Zhenhua, XU Jing, LIU Yan, et al. Updatable Ciphertext-Policy Attribute-Based Encryption Scheme with Traceability and Revocability[J]. IEEE Access, 2019, 7: 66832-66844.
doi: 10.1109/ACCESS.2019.2918434 |
| [23] | PAN Jingwen, CUI Jie, WEI Lu, et al. Secure Data Sharing Scheme for VANETs Based on Edge Computing[J]. EURASIP Journal on Wireless Communications and Networking, 2019(1): 1-11. |
| [24] |
CUI Hui, YI Xun, NEPAL S. Achieving Scalable Access Control over Encrypted Data for Edge Computing Networks[J]. IEEE Access, 2018, 6: 30049-30059.
doi: 10.1109/Access.6287639 URL |
| [25] |
ZHANG Peng, CHEN Zehong, LIU J K, et al. An Efficient Access Control Scheme with Outsourcing Capability and Attribute Update for Fog Computing[J]. Future Generation Computer Systems, 2018, 78: 753-762.
doi: 10.1016/j.future.2016.12.015 URL |
| [26] |
ZUO Cong, SHAO Jun, WEI Guiyi, et al. CCA-Secure ABE with Outsourced Decryption for Fog Computing[J]. Future Generation Computer Systems, 2018, 78: 730-738.
doi: 10.1016/j.future.2016.10.028 URL |
| [27] |
LIU C H, LIN Qiuxia, WEN Shilin. Blockchain-Enabled Data Collection and Sharing for Industrial IoT with Deep Reinforcement Learning[J]. IEEE Transactions on Industrial Informatics, 2019, 15(6): 3516-3526.
doi: 10.1109/TII.9424 URL |
| [28] |
HUANG Junqin, KONG Linghe, CHEN Guihai, et al. Towards Secure Industrial IoT: Blockchain System with Credit-Based Consensus Mechanism[J]. IEEE Transactions on Industrial Informatics, 2019, 15(6): 3680-3689.
doi: 10.1109/TII.9424 URL |
| [29] | TESLYA N, RYABCHIKOV I. Blockchain-Based Platform Architecture for Industrial IoT[C]// IEEE. 21st Conference of Open Innovations Association(FRUCT). New York:IEEE, 2017: 321-329. |
| [30] | ROUSELAKIS Y, WATERS B. Practical Constuctions and New Proof Methods for Large Universe Attribute-Based Encryption[C]// ACM. 2013 ACM SIGSAC Conference on Computer & Communications Security. New York: ACM, 2013: 463-474. |
| [31] |
GOLDWASSER S, MICALI S. Probabilistic Encryption[J]. Journal of Computer and System Science, 1984, 28(2): 270-299.
doi: 10.1016/0022-0000(84)90070-9 URL |
| [32] | ZHUANG Chaoyuan, GUO Rui, YANG Geng. Anonymous Attribute-Based Encryption Scheme with Verifiable Outsourcing Decryption in Blockchain[J] Journal of Computer Applications, 2022, 58(19): 124-134. |
|
庄朝源, 郭瑞, 杨耿. 区块链中可验证外包解密的匿名属性加密方案[J]. 计算机工程与应用, 2022, 58(19):124-134.
doi: 10.3778/j.issn.1002-8331.2107-0487 |
|
| [33] |
LI Jiguo, YAO Wei, HAN Jinguang, et al. User Collusion Avoidance CP-ABE with Efficient Attribute Revocation for Cloud Storage[J]. IEEE Systems Journal, 2018, 12(2): 1767-1777.
doi: 10.1109/JSYST.4267003 URL |
| [34] |
SETHI K, PRADHAN A, BERA P. PMTER-ABE: A Practical Multi-Authority CP-ABE with Traceability, Revocation and Outsourcing Decryption for Secure Access Control in Cloud Systems[J]. Cluster Computing, 2021, 24: 1-26.
doi: 10.1007/s10586-020-03165-4 |
| [1] | LI Chunxiao, WANG Yaofei, XU Enliang, ZHAO Yu. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings [J]. Netinfo Security, 2023, 23(3): 22-34. |
| [2] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [3] | WANG Jingyu, MA Zhaofeng, XU Danheng, DUAN Pengfei. Blockchain Transaction Data Privacy-Preserving Scheme Supporting National Cryptographic Algorithm [J]. Netinfo Security, 2023, 23(3): 84-95. |
| [4] | MU Zhiying, XU Jiaquan, LI Xiaoyu. Community-Detection-Based Influence Blocking Maximization Algorithm in Social Network [J]. Netinfo Security, 2023, 23(1): 44-56. |
| [5] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [6] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [7] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [8] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [9] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [10] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [11] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| [12] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [13] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [14] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [15] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||