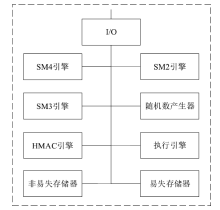
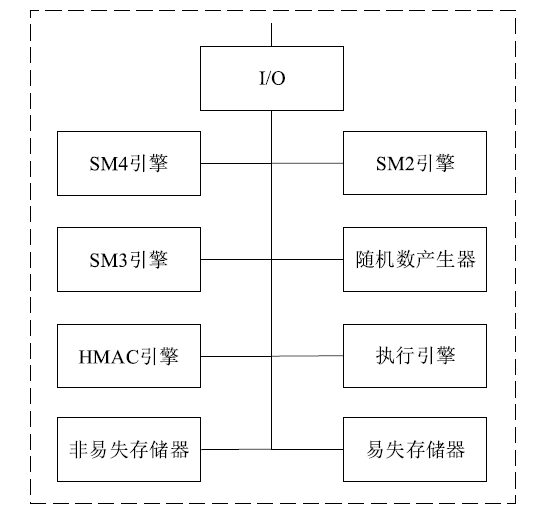
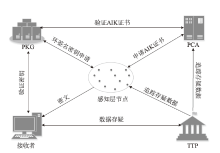
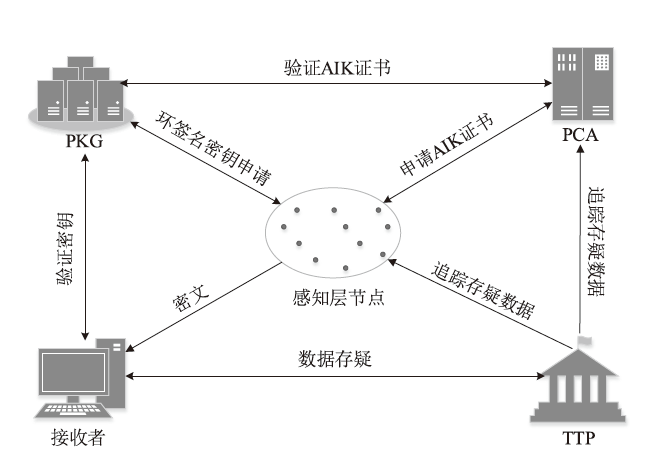
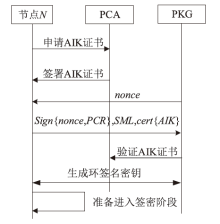
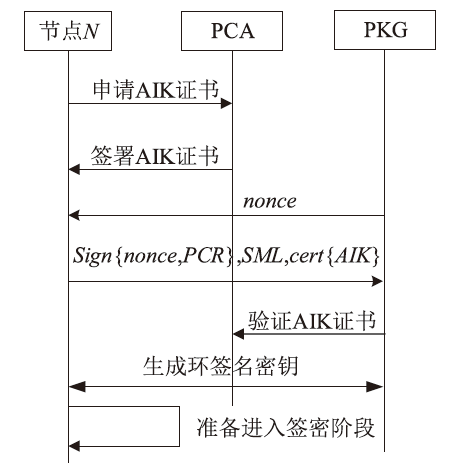
| [1] |
SRIVASTAVA L, KELLY T. The Internet of Things[EB/OL]. (2005-11-17)[2022-05-10]. https://www.itu.int/osg/spu/presentations/2005/srivastava_internetofthings_press%20.pdf.
|
| [2] |
GONZALEZ G R, ORGANERO M M, KLOOS C D. Early Infrastructure of an Internet of Things in Spaces for Learning[C]// IEEE. 8th IEEE International Conference on Advanced Learning Technologies. New York: IEEE, 2008: 381-383.
|
| [3] |
SARMA A C, GIRÃO J. Identities in the Future Internet of Things[J]. Wireless Personal Communications, 2009, 49(3): 353-363.
|
| [4] |
COSTIN A, ZADDACH J, FRANCILLON A, et al. A Large-Scale Analysis of the Security of Embedded Firmwares[C]// USENIX. 23nd USENIX Security Symposium. Berkeley: USENIX, 2014: 95-110.
|
| [5] |
FENG Dengguo, LIU Jingbin, QIN Yu, et al. Trusted Computing Theory and Technology in Innovation-Driven Development[J]. Scientia Sinica: Informationis, 2020, 50(8): 1127-1147.
|
|
冯登国, 刘敬彬, 秦宇, 等. 创新发展中的可信计算理论与技术[J]. 中国科学:信息科学, 2020, 50(8):1127-1147.
|
| [6] |
ZHANG Yan, ZHANG Liwu. Survey on Anonymous Credential Schemes[J]. Netinfo Security, 2012, 12(1): 17-22.
|
|
张严, 张立武. 匿名凭证方案研究进展[J]. 信息网络安全, 2012, 12(1):17-22.
|
| [7] |
BRICKELL E, CHENLiqun, LIJiangtao. A New Direct Anonymous Attestation Scheme from Bilinear Maps[C]// Springer. International Conference on Trusted Computing. Heidelberg: Springer, 2008: 166-178.
|
| [8] |
RIVEST R L, SHAMIR A, TAUMAN Y. How to Leak a Secret[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2001: 552-565.
|
| [9] |
HUANG Dawei, YANG Xiaoyuan, CHEN Haibin. Ring Signature Scheme with Revocable Anonymity[J]. Computer Engineering and Applications, 2010, 46(24): 88-89.
|
|
黄大威, 杨晓元, 陈海滨. 一种可撤销匿名性的环签名方案[J]. 计算机工程与应用, 2010, 46(24):88-89.
|
| [10] |
YANG Huajie, MIAO Xianghua, ZHU Haitao, et al. Efficient Certificateless Ring Signature Scheme with Identity Tracing[J]. Cyberspace Security, 2014, 5(7): 32-35.
|
|
杨华杰, 缪祥华, 朱海韬, 等. 一种高效无证书可追踪环签名方案[J]. 信息安全与技术, 2014, 5(7):32-35.
|
| [11] |
WANG Hongyuan, MENG Jin, DU Xilong, et al. Lightweight and Anonymous Mutual Authentication Protocol for Edge IoT Nodes with Physical Unclonable Function[EB/OL]. (2022-01-04)[2022-06-11]. https://doi.org/10.1155/2022/1203691.
|
| [12] |
GHAHRAMANI M, JAVIDAN R. A Robust Anonymous Remote User Authentication Protocol for IoT Services[J]. Wireless Personal Communications, 2021, 121(3): 2347-2369.
|
| [13] |
LI Xiong, NIU Jianwei, KUMARI S, et al. A Three-Factor Anonymous Authentication Scheme for Wireless Sensor Networks in Internet of Things Environments[J]. Journal of Network and Computer Applications, 2018, 103: 194-204.
|
| [14] |
SADRI M J, ASAAR M R. An Anonymous Two-Factor Authentication Protocol for IoT-Based Applications[EB/OL]. (2021-11-09)[2022-06-12]. https://doi.org/10.1016/j.comnet.2021.108460.
|
| [15] |
HUANG Jing, CHEN Jia, ZHANG Huijuan, et al. A Remote Attestation Mechanism Using a Threshold Ring Signature for a Perception Layer of Distributed Networking[EB/OL]. (2022-01-22)[2022-06-12]. https://doi.org/10.1155/2022/6603754.
|
| [16] |
YU Chen, CHEN Liquan, LU Tianyu. M2M Network Anonymous Attestation Scheme Based on Mimic Defense[J]. Journal of Cryptologic Research, 2021, 8(3): 468-477.
|
| [17] |
XIE Run, HE Chanlian, XU Chunxiang, et al. Lattice-Based Dynamic Group Signature for Anonymous Authentication in IoT[J]. Annals of Telecommunications, 2019, 74(7): 531-542.
|
| [18] |
NUNES I D O, DESSOUKY G, IBRAHIM A, et al. Towards Systematic Design of Collective Remote Attestation Protocols[C]// IEEE. 39th International Conference on Distributed Computing Systems(ICDCS). New York: IEEE, 2019: 1188-1198.
|
| [19] |
ZHAO Na, LONG Hui, SU Jinshu. A Scheme for Anonymous Authentication and Privacy Protection in the Internet of Things Environment[J]. Netinfo Security, 2018, 18(11): 1-7
|
|
赵娜, 龙慧, 苏金树. 一种适用于物联网环境的匿名认证与隐私保护方案[J]. 信息网络安全, 2018, 18(11):1-7.
|