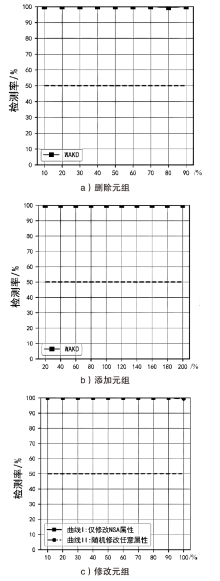
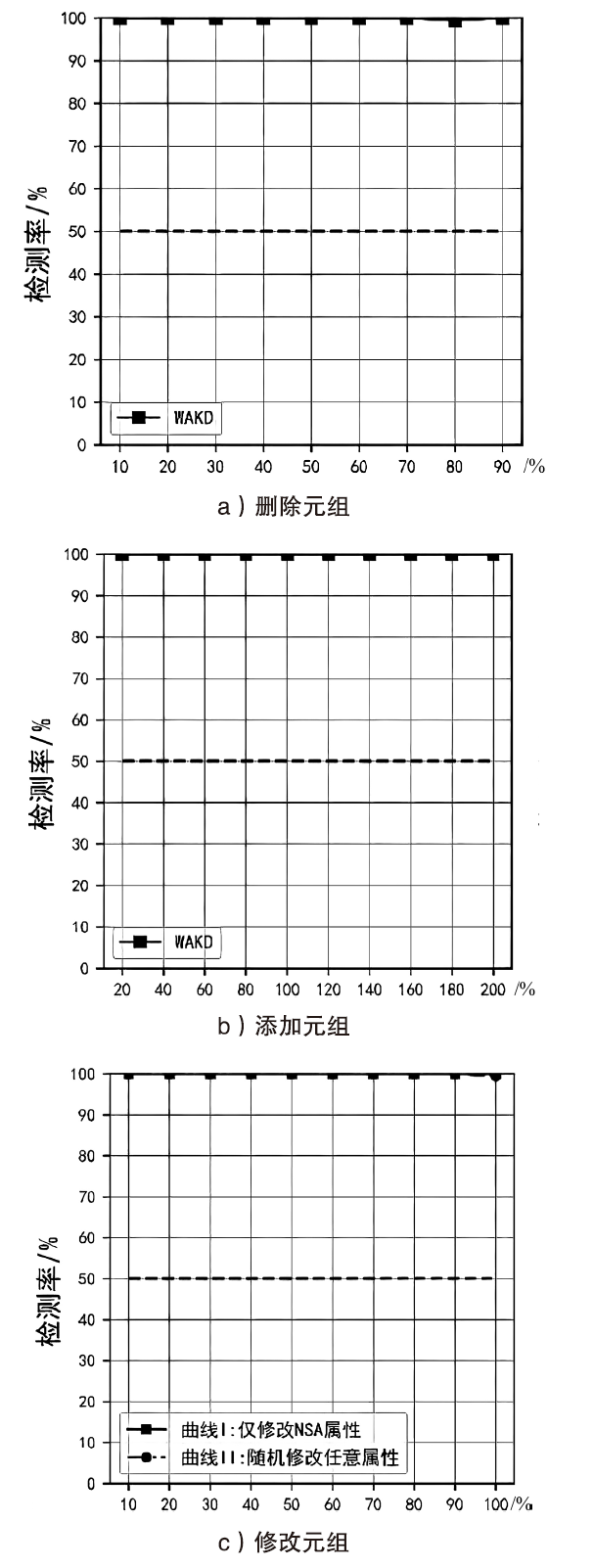
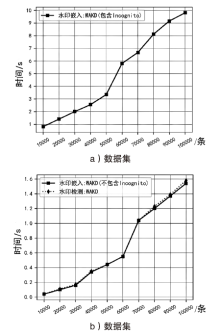
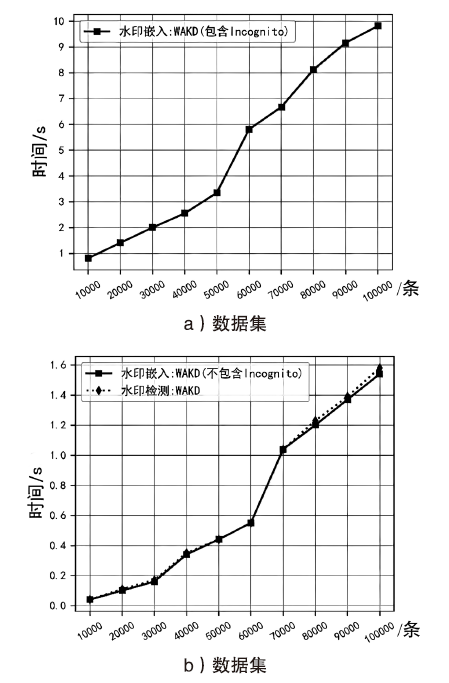
Netinfo Security ›› 2022, Vol. 22 ›› Issue (9): 11-20.doi: 10.3969/j.issn.1671-1122.2022.09.002
Previous Articles Next Articles
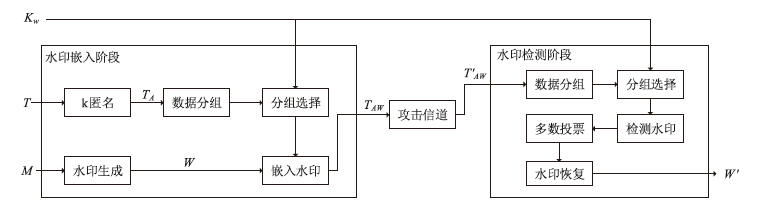
A Robust Watermarking Technology Based on k-Anonymity Dataset
YU Jing1,2, YUAN Shuguang1,2, YUAN Yulin1,2, CHEN Chi1,2( )
)
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100049, China
-
Received:2022-05-29Online:2022-09-10Published:2022-11-14 -
Contact:CHEN Chi E-mail:chenchi@iie.ac.cn
CLC Number:
Cite this article
YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset[J]. Netinfo Security, 2022, 22(9): 11-20.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.09.002
| DOBMM | DOBYY | YEAR | RACEAX | RACEBX | RACEWX | ACEIHN | EDUCYEAR | POVERTY | INCOME |
|---|---|---|---|---|---|---|---|---|---|
| 1 | 1975 | 2003 | 3 | 3 | 1 | 4 | 12 | 4 | 32021 |
| 2 | 1975 | 2003 | 3 | 3 | 1 | 1 | 11 | 3 | 3700 |
| 1 | 1975 | 2003 | 3 | 3 | 1 | 1 | 12 | 3 | 33300 |
| 2 | 1975 | 2003 | 3 | 3 | 1 | 4 | 12 | 4 | 18000 |
| 3 | 1975 | 2003 | 3 | 3 | 1 | 4 | 12 | 5 | 20178 |
| …… | |||||||||
| 7 | 1950 | 2003 | 3 | 3 | 1 | 1 | 14 | 3 | 12000 |
| 8 | 1950 | 2003 | 3 | 3 | 1 | 4 | 16 | 4 | 27200 |
| 5 | 1950 | 2003 | 3 | 3 | 1 | 1 | 9 | 1 | 9434 |
| 6 | 1950 | 2003 | 3 | 3 | 1 | 4 | 14 | 5 | 15 |
| 7 | 1950 | 2003 | 3 | 3 | 1 | 1 | 12 | 5 | 21549 |
| …… | |||||||||
| DOBMM | DOBYY | YEAR | RACEAX | RACEBX | RACEWX | ACEIHN | EDUCYEAR | POVERTY | INCOME |
|---|---|---|---|---|---|---|---|---|---|
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 1 | 4 | 12 | 4 | 32021 |
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 1 | 1 | 11 | 3 | 3700 |
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 1 | 1 | 12 | 3 | 33300 |
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 1 | 4 | 12 | 4 | 18000 |
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 1 | 4 | 12 | 5 | 20178 |
| …… | |||||||||
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 1 | 14 | 3 | 12000 |
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 4 | 16 | 4 | 27200 |
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 1 | 9 | 1 | 9434 |
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 4 | 14 | 5 | 15 |
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 1 | 12 | 5 | 21549 |
| …… | |||||||||
| DOBMM | DOBYY | YEAR | RACEAX | RACEBX | RACEWX | ACETHN | EDUCYEAR | POVERTY | INCOME |
|---|---|---|---|---|---|---|---|---|---|
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 1 | 4 | 4 | 4 | 32021 |
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 0 | 1 | 11 | 3 | 3700 |
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 0 | 1 | 12 | 3 | 33300 |
| 1:4 | 1975:1976 | 20032005 | 1 | 3 | 1 | 4 | 12 | 4 | 18000 |
| 1:4 | 1975:1976 | 20032005 | 3 | 3 | 1 | 4 | 12 | 7 | 20178 |
| …… | |||||||||
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 0 | 14 | 3 | 12000 |
| 5:8 | 1950:1951 | 20032005 | 3 | 2 | 1 | 4 | 16 | 4 | 27200 |
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 1 | 9 | 0 | 9434 |
| 5:8 | 1950:1951 | 20032005 | 3 | 2 | 1 | 4 | 14 | 5 | 15 |
| 5:8 | 1950:1951 | 20032005 | 3 | 3 | 1 | 0 | 12 | 5 | 21549 |
| …… | |||||||||
| [1] | ZHOU Xiang, HUANG Min, PENG Zhiyong. An Additive-Attack-Proof Watermarking Mechanism for Databases’ Copyrights Protection Using Image[C]// ACM. Proceedings of the 2007 ACM Symposium on Applied Computing. New York: ACM, 2007: 254-258. |
| [2] | WANG Haiqing, CUI Xinchun, CAO Zaihui. A Speech Based Algorithm for Watermarking Relational Databases[C]// IEEE. 2008 International Symposiums on Information Processing. New York: IEEE, 2008: 603-606. |
| [3] | SION R, ATALLAH M, PRABHAKAR S. Rights Protection for Relational Data[J]. IEEE Trans. Knowl. Data Eng. 2004, 16(12): 1509-1525. |
| [4] | SHEHAB M, BERTINO E, GHAFOOR A. Watermarking Relational Databases Using Optimization-Based Techniques[J]. IEEE Trans. Knowl. Data Eng., 2007, 20(1): 116-129. |
| [5] | FRANCO-CONTRERAS J, COATRIEUX G. Robust Watermarking of Relational Databases with Ontology-Guided Distortion Control[J]. IEEE Trans. Inf. Forensics Secur., 2015, 10(9): 1939-1952. |
| [6] | CUI Xinchun, QIN Xiaolin, SHENG Gang. A Weighted Algorithm for Watermarking Relational Databases[J]. Wuhan University Journal of Natural Sciences, 2007, 12(1): 79-82. |
| [7] | SCHRITTWIESER S, KIESEBERG P, ECHIZEN I, et al. Using Generalization Patterns for Fingerprinting Sets of Partially Anonymized Microdata in the Course of Disasters[C]// IEEE. Sixth International Conference on Availability, Reliability and Security. New York: IEEE, 2011: 645-649. |
| [8] | SCHRITTWIESER S, KIESEBERG P, ECHIZEN I, et al. An Algorithm for k-anonymity-based Fingerprinting[C]// Springer. Digital Forensics and Watermarking-10th International Workshop. Berlin: Springer, 2011: 439-452. |
| [9] | KIESEBERG P, SCHRITTWIESER S, MULAZZANI M, et al. An Algorithm for Collusion-Resistant Anonymization and Fingerprinting of Sensitive Microdata[J]. Electronic Markets, 2014, 24(2): 113-124. |
| [10] | GAMBS S, LOLIVE J, ROBERT J. Entwining Sanitization and Personalization on Databases[C]// ACM. Proceedings of the 2018 on Asia Conference on Computer and Communications Security. New York: ACM, 2018: 207-219. |
| [11] | AGRAWAL R, KIERNAN J. Watermarking Relational Databases[C]// VLDB. Proceedings of 28th International Conference on Very Large Data Bases. CA: Morgan Kaufmann, 2002: 155-166. |
| [12] | AGRAWAL R, HAAS P J, KIERNAN J. Watermarking Relational Data: Framework, Algorithms and Analysis[J]. The VLDB Journal, 2003, 12(2): 157-169. |
| [13] | GUO Fei, WANGJianmin, LIDeyi. Fingerprinting Relational Databases[C]// ACM. Proceedings of the 2006 ACM Symposium on Applied Computing. New York: ACM, 2006: 487-492. |
| [14] | SAMARATI P. Protecting Respondents Identities in Microdata Release[J]. IEEE transactions on Knowledge and Data Engineering, 2001, 13(6): 1010-1027. |
| [15] | SWEENEY L. Achieving k-Anonymity Privacy Protection Using Generalization and Suppression[J]. International Journal of Uncertainty, Fuzziness and Knowledge-Based Systems, 2002, 10(5): 571-588. |
| [16] | LEFEVRE K, DEWITT D J, RAMAKRISHNAN R. Incognito: Efficient Full-Domain k-Anonymity[C]// ACM. Proceedings of the 2005 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2005: 49-60. |
| [17] | SWEENEY L. Guaranteeing Anonymity When Sharing Medical Data, the Datafly System[C]// AMIA. American Medical Informatics Association Annual Symposium. TN: AMIA, 1997: 51-55. |
| [18] | FUNG B C, WANG K, YU P S. Top-Down Specialization for Information and Privacy Preservation[C]// IEEE. 21st International Conference on Data Engineering (ICDE’05). New York: IEEE, 2005: 205-216. |
| [19] | LEFEVRE K, DEWITT D J, RAMAKRISHNAN R. Mondrian Multidimensional k-Anonymity[C]// IEEE. 22nd International Conference on Data Engineering (ICDE’06). New York: IEEE, 2006: 25-28. |
| [20] | WANG K, YU P S, CHAKRABORTY S. Bottom-Up Generalization: A Data Mining Solution to Privacy Protection[C]// IEEE. Proceedings of the 4th IEEE International Conference on Data Mining (ICDM 2004). New York: IEEE, 2004: 249-256. |
| [1] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [2] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| [3] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| [4] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| [5] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [6] | REN Hang, CHENG Xiangguo, ZHANG Rui, XIA Hui. A Novel Fraud Prevention Strategy Based on Bargaining Bayesian Game Model [J]. Netinfo Security, 2021, 21(4): 81-88. |
| [7] | ZHOU Yousheng, WANG Ming, LIU Yuanni. Privacy Protection Scheme Supporting Interval Query for LBS Outsourced Data [J]. Netinfo Security, 2021, 21(3): 26-36. |
| [8] | LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing [J]. Netinfo Security, 2021, 21(11): 58-64. |
| [9] | LI Kunchang, SHI Runhua, LI En. Survey on Data Aggregation and Privacy Protection of User Query in Smart Grid [J]. Netinfo Security, 2021, 21(11): 65-74. |
| [10] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| [11] | LI Ningbo, ZHOU Haonan, CHE Xiaoliang, YANG Xiaoyuan. Design of Directional Decryption Protocol Based on Multi-key Fully Homomorphic Encryption in Cloud Environment [J]. Netinfo Security, 2020, 20(6): 10-16. |
| [12] | XIAO Biao, YAN Hongqiang, LUO Haining, LI Jucheng. Research on Improvement of Bayesian Network Privacy Protection Algorithm Based on Differential Privacy [J]. Netinfo Security, 2020, 20(11): 75-86. |
| [13] | HE Jingsha, DU Jinhui, ZHU Nafei. Research on k-anonymity Algorithm for Personalized Quasi-identifier Attributes [J]. Netinfo Security, 2020, 20(10): 19-26. |
| [14] | HUANG Baohua, CHENG Qi, YUAN Hong, HUANG Pirong. K-means Clustering Algorithm Based on Differential Privacy with Distance and Sum of Square Error [J]. Netinfo Security, 2020, 20(10): 34-40. |
| [15] | Wenjiang HAO, Yun LIN. Research on Social Responsibility of Internet Enterprises and Its Enlightenment [J]. Netinfo Security, 2019, 19(9): 130-133. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||