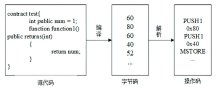
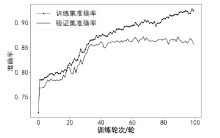
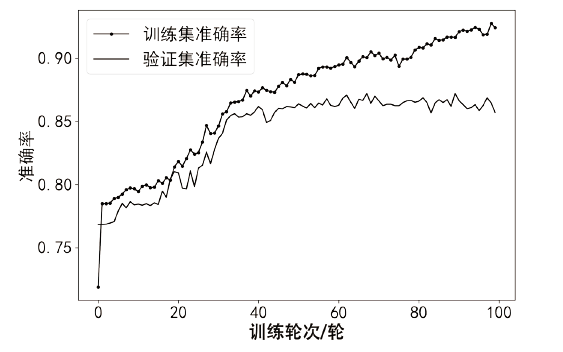
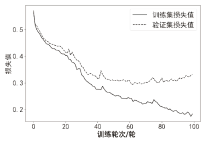
Netinfo Security ›› 2022, Vol. 22 ›› Issue (9): 46-54.doi: 10.3969/j.issn.1671-1122.2022.09.006
Previous Articles Next Articles
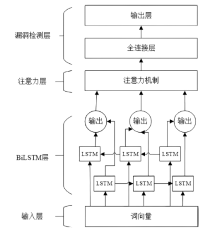
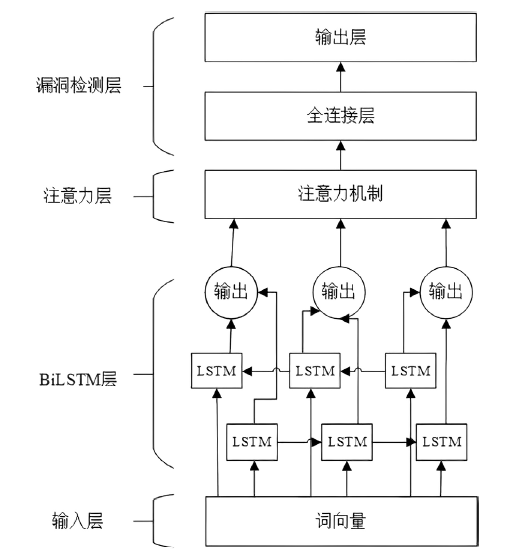
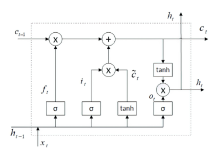
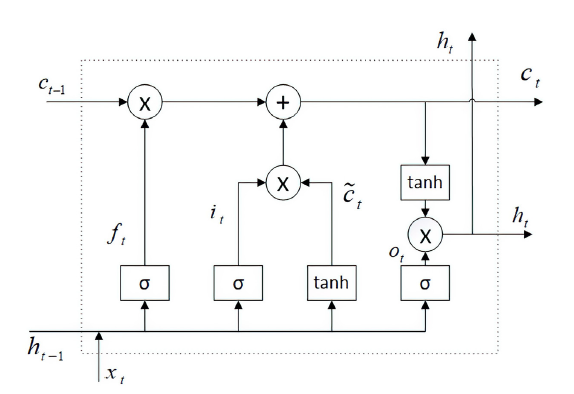
Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism
ZHANG Guanghua1,2, LIU Yongsheng2, WANG He1, YU Naiwen2( )
)
- 1. School of Cyber Engineering, Xidian University, Xi’an 710071, China
2. School of Information Science and Engineering, Hebei University of Science Technology, Shijiazhuang 050018, China
-
Received:2022-06-28Online:2022-09-10Published:2022-11-14 -
Contact:YU Naiwen E-mail:yunaiwen@hebust.edu.cn
CLC Number:
Cite this article
ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism[J]. Netinfo Security, 2022, 22(9): 46-54.
share this article
| 模型 | RNN[ | LSTM[ | TextCNN[ | 本文模型 | |
|---|---|---|---|---|---|
| 整数溢出 漏洞 | 精确率 | 85.64% | 86.60% | 86.16% | 94.92% |
| 召回率 | 86.22% | 89.09% | 90.52% | 91.50% | |
| F1值 | 85.93% | 87.82% | 88.29% | 93.18% | |
| 可重入漏洞 | 精确率 | 75.00% | 69.39% | 64.86% | 76.39% |
| 召回率 | 27.55% | 36.69% | 54.23% | 65.48% | |
| F1值 | 40.30% | 47.86% | 59.07% | 70.51% | |
| 以太币锁定 漏洞 | 精确率 | 65.62% | 69.84% | 74.58% | 87.95% |
| 召回率 | 46.26% | 58.15% | 53.44% | 79.76% | |
| F1值 | 54.26% | 63.46% | 62.26% | 83.65% |
| 模型 | SmartCheck[ | Mythril[ | Slither[ | 本文模型 | |
|---|---|---|---|---|---|
| 整数溢出 漏洞 | 精确率 | 33.33% | 74.64% | — | 94.92% |
| 召回率 | 30.30% | 77.94% | — | 91.50% | |
| F1值 | 31.74% | 75.82% | — | 93.18% | |
| 可重入 漏洞 | 精确率 | 39.40% | 52.30% | 35.48% | 76.39% |
| 召回率 | 41.25% | 49.69% | 42.31% | 65.48% | |
| F1值 | 40.59% | 50.98% | 38.59% | 70.51% | |
| 以太币锁定 漏洞 | 精确率 | 85.18% | — | 59.18% | 87.95% |
| 召回率 | 26.13% | — | 56.86% | 79.76% | |
| F1值 | 39.98% | — | 57.99% | 83.65% |
| [1] | SZABO N. Smart Contracts: Building Blocks for Digital Markets[J]. EXTROPY: The Journal of Transhumanist Thought, 1996, 18(2): 28-30. |
| [2] | HU Tianyuan, LI Zecheng, LI Bixin, et al. Contractual Security and Privacy Security of Smart Contract: A System Mapping Study[J]. Chinese Journal of Computers, 2021, 44(12): 2485-2514. |
| 胡甜媛, 李泽成, 李必信, 等. 智能合约的合约安全和隐私安全研究综述[J]. 计算机学报, 2021, 44(12): 2485-2514. | |
| [3] | YANG Zheng, LEI Hang. Lolisa: Formal Syntax and Semantics for a Subset of the Solidity Programming Language in Mathematical Tool Coq[EB/OL]. (2018-05-27)[2022-05-25]. https://arxiv.org/abs/1803.09885. |
| [4] | MEHAR M I, SHIER C L, GIAMBATTISTA A, et al. Understanding a Revolutionary and Flawed Grand Experiment in Blockchain: The DAO Attack[J]. Journal of Cases on Information Technology (JCIT), 2019, 21(1): 19-32. |
| [5] | PALLADINO S. The Parity Wallet Hack Explained[EB/OL]. (2017-07-19)[2022-05-25]. https://blog.openzeppelin.com/on-the-parity-wallet-multisig-hack-405a8c12e8f7. |
| [6] | HESSENAUER S. Batch Overflow Bug on Ethereum ERC20 Token Contracts and SafeMath[EB/OL]. (2018-04-26)[2022-05-25]. http://blog.matryx.ai/batch-overflow-bug-on-ethereum-erc20-token-contracts-and-safemath-f9ebcc137434. |
| [7] | LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]// ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 254-269. |
| [8] | NIKOLIC I, KOLLURI A, SERGEY I, et al. Finding the Greedy, Prodigal, and Suicidal Contracts at Scale[C]// ACM. 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 653-663. |
| [9] | TORRES C F, SCHÜTTE J, STATE R. Osiris: Hunting for Integer Bugs in Ethereum Smart Contracts[C]// ACM. 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 664-676. |
| [10] | MUELLER B. MYTHRIL: A Framework for Bug Hunting on the Ethereum Blockchain[EB/OL]. (2017-07-11)[2022-05-25]. https://mythx.io/. |
| [11] | TSANKOV P, DAN A, DRACHSLER C D, et al. Securify: Practical Security Analysis of Smart Contracts[C]// ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 67-82. |
| [12] | JIANG Bo, LIU Ye, CHAN W K. Contractfuzzer: Fuzzing Smart Contracts for Vulnerability Detection[C]// IEEE. 2018 33rd IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2018: 259-269. |
| [13] | HE Jingxuan, BALUNOVIĆ M, AMBROLADZE N, et al. Learning to Fuzz from Symbolic Execution with Application to Smart Contracts[C]// ACM. 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 531-548. |
| [14] | NGUYEN T D, PHAM L H, SUN Jun, et al. sFuzz: An Efficient Adaptive Fuzzer for Solidity Smart Contracts[C]// ACM. ACM/IEEE 42nd International Conference on Software Engineering. New York: ACM, 2020: 778-788. |
| [15] | LIANAN. VaaS: Automated Formal Verification Platform for Smart Contract[EB/OL]. (2019-07-03)[2022-05-11]. https://www.lianantech.com/. |
| [16] | AMANI S, BÉGEL M, BORTIN M, et al. Towards Verifying Ethereum Smart Contract Bytecode in Isabelle/HOL[C]// ACM. 7th ACM SIGPLAN International Conference on Certified Programs and Proofs. New York: ACM, 2018: 66-77. |
| [17] | FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]// IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain(WETSEB). New York: IEEE, 2019: 8-15. |
| [18] | TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. Smartcheck: Static Analysis of Ethereum Smart Contracts[C]// ACM. 1st International Workshop on Emerging Trends in Software Engineering for Blockchain. New York: ACM, 2018: 9-16. |
| [19] | QIAN Peng, LIU Zhenguang, HE Qinming, et al. Towards Automated Reentrancy Detection for Smart Contracts Based on Sequential Models[J]. IEEE Access, 2020(8): 19685-19695. |
| [20] | TANN W J W, HAN Xingjie, GUPTA S S, et al. Towards Safer Smart Contracts: A Sequence Learning Approach to Detecting Security Threats[EB/OL]. (2018-11-16)[2022-05-25]. https://arxiv.org/abs/1811.06632v3. |
| [21] | SUN Yuhang, GU Lize. Attention-Based Machine Learning Model for Smart Contract Vulnerability Detection[EB/OL]. (2021-01-15)[2022-05-25]. https://iopscience.iop.org/article/10.1088/1742-6596/1820/1/012004. |
| [22] | WANG Wei, SONG Jingjing, XU Guangquan, et al. Contractward: Automated Vulnerability Detection Models for Ethereum Smart Contracts[J]. IEEE Transactions on Network Science and Engineering, 2020, 8(2): 1133-1144. |
| [23] | YU Xingxin, ZHAO Haoyue, HOU Botao, et al. DeeSCVHunter: A Deep Learning-Based Framework for Smart Contract Vulnerability Detection[C]// IEEE. 2021 International Joint Conference on Neural Networks (IJCNN). New York: IEEE, 2021: 1-8. |
| [24] | MIKOLOV T, CHEN Kai, CORRADO G, et al. Efficient Estimation of Word Representations in Vector Space[EB/OL]. (2013-01-16)[2022-05-25]. https://arxiv.org/abs/1301.3781. |
| [25] | HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780. |
| [26] | BAHDANAU D, CHO K, BENGIO Y. Neural Machine Translation by Jointly Learning to Align and Translate[EB/OL]. (2014-09-01)[2022-05-25]. https://arxiv.org/abs/1409.0473v7. |
| [27] | ALBERT E, GORDILLO P, LIVSHITS B, et al. Ethir: A Framework for High-Level analysis of Ethereum Bytecode[C]// Springer. International Symposium on Automated Technology for Verification and Analysis. Heidelberg: Springer, 2018: 513-520. |
| [28] | ZAREMBA W, SUTSKEVER I, VINYALS O. Recurrent Neural Network Regularization[EB/OL]. (2014-09-08)[2022-05-25]. https://arxiv.org/abs/1409.2329. |
| [29] | KIM Y. Convolutional Neural Networks for Sentence Classification[EB/OL]. (2014-08-25)[2022-05-25]. https://arxiv.org/abs/1408.5882v2. |
| [1] | ZHANG Yujian, LIU Daifu, TONG Fei. Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching [J]. Netinfo Security, 2022, 22(8): 1-7. |
| [2] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [3] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [4] | WANG Jian, HUANG Jun. Smart Contract-Based Log Secure Storage and Fair Access Method [J]. Netinfo Security, 2022, 22(7): 27-36. |
| [5] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| [6] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [7] | HUA Jingyu, HUANG Daming. Survey of Formal Specification Methods in Theorem Proving of Ethereum Smart Contract [J]. Netinfo Security, 2022, 22(5): 11-20. |
| [8] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [9] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [10] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [11] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 23(3): 20-28. |
| [12] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| [13] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, LIU Xuefeng. Insider Threat Detection Model Based on LSTM-Attention [J]. Netinfo Security, 2022, 22(2): 1-10. |
| [14] | WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage [J]. Netinfo Security, 2022, 22(2): 21-31. |
| [15] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||