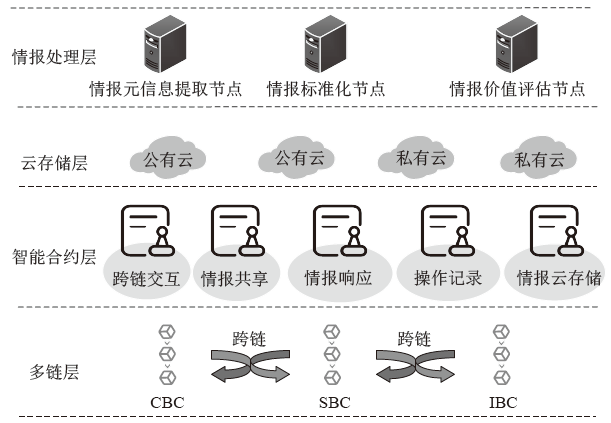
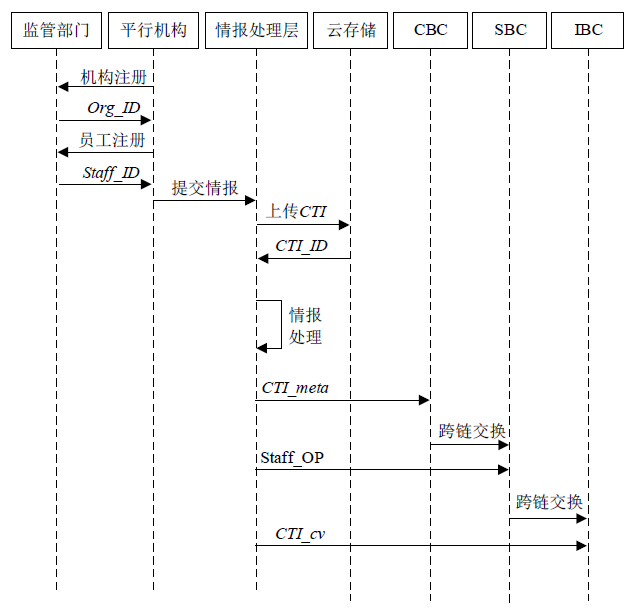
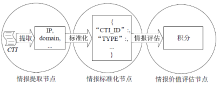
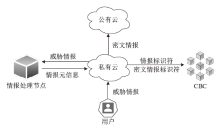
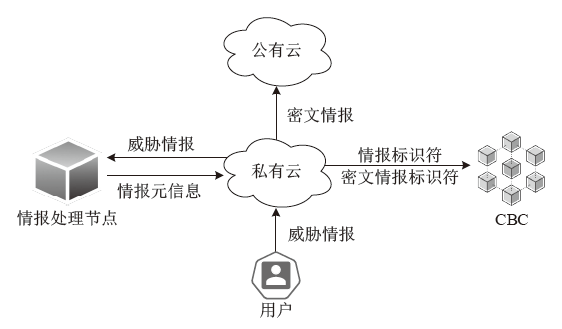
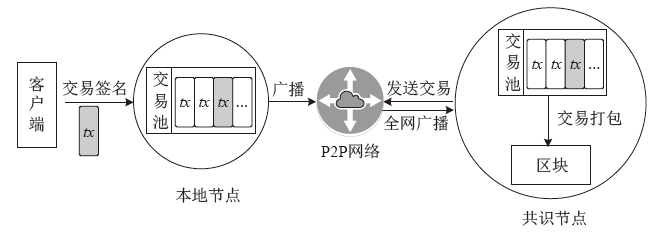
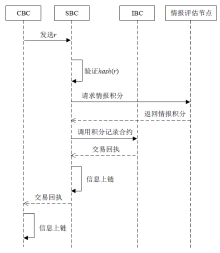
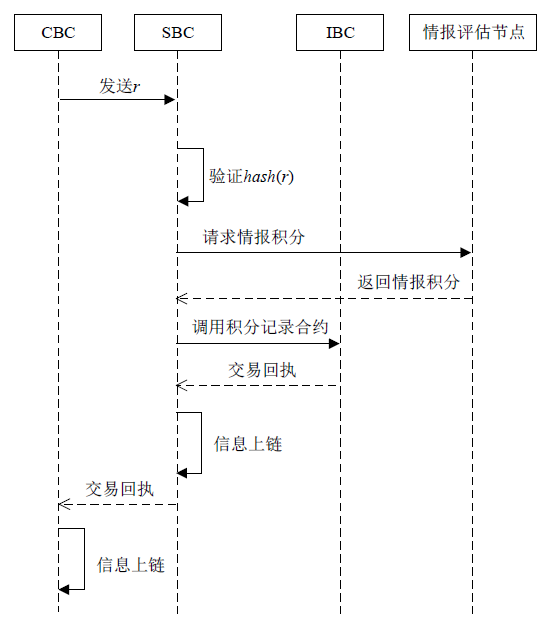
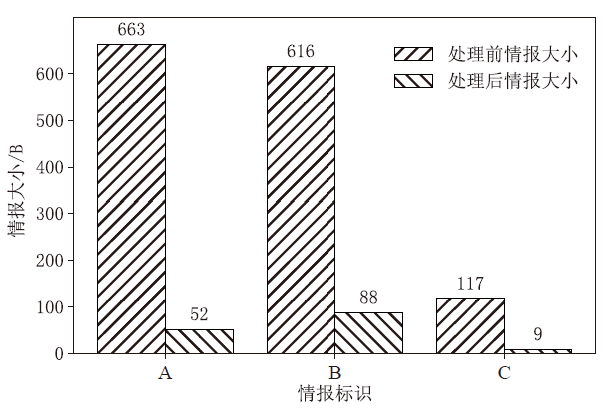
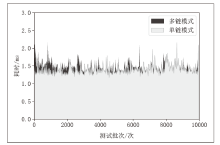
Netinfo Security ›› 2022, Vol. 22 ›› Issue (5): 21-29.doi: 10.3969/j.issn.1671-1122.2022.05.003
Previous Articles Next Articles
A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction
FENG Jingyu( ), ZHANG Qi, HUANG Wenhua, HAN Gang
), ZHANG Qi, HUANG Wenhua, HAN Gang
- National Engineering Laboratory for Wireless Security, Xi'an University of Posts and Telecommunications, Xi'an 710121, China
-
Received:2021-11-04Online:2022-05-10Published:2022-06-02 -
Contact:FENG Jingyu E-mail:fengjy@xupt.edu.cn
CLC Number:
Cite this article
FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction[J]. Netinfo Security, 2022, 22(5): 21-29.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.05.003
| [1] | CHENG Li, XU Dongfang, ZENG Kai, et al. Design and Application of Power Quality Terminal Information Security[J]. Electric Power Engineering Technology, 2020, 39(6): 26-33. |
| 程立, 许东方, 曾凯, 等. 电能质量终端信息安全设计及应用[J]. 电力工程技术, 2020, 39(6):26-33. | |
| [2] | LIN Yue, LIU Peng, WANG He, et al. Overview of Threat Intelligence Sharing and Exchange in Cybersecurity[J]. Journal of Computer Research and Development, 2020, 57(10): 2052-2065. |
| 林玥, 刘鹏, 王鹤, 等. 网络安全威胁情报共享与交换研究综述[J]. 计算机研究与发展, 2020, 57(10):2052-2065. | |
| [3] | ZIBAK A, SIMPSON A. Cyber Threat Information Sharing: Perceived Benefits and Barriers[C]// ACM. 14th International Conference on Availability, Reliability and Security. New York: ACM, 2019: 1-9. |
| [4] | WANG Hai, ZENG Fei, YANG Xiong. Blockchain-Based Data Security Protection for Distribution Internet of Things[J]. Electric Power Engineering Technology, 2021, 40(5): 47-53. |
| 王海, 曾飞, 杨雄. 基于区块链的配电物联网数据安全防护方法[J]. 电力工程技术, 2021, 40(5):47-53. | |
| [5] | KAMPANAKIS P. Security Automation and Threat Information-Sharing Options[J]. IEEE Security & Privacy, 2014, 12(5): 42-51. |
| [6] |
LESZCZYNA R, WROBEL M R. Threat Intelligence Platform for the Energy Sector[J]. Software: Practice and Experience, 2019, 49(8): 1225-1254.
doi: 10.1002/spe.2705 URL |
| [7] |
ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain Challenges and Opportunities: A Survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352-375.
doi: 10.1504/IJWGS.2018.095647 URL |
| [8] | GAI Keke, GUO Jinnan, ZHU Liehuang, et al. Blockchain Meets Cloud Computing: A Survey[J]. IEEE Communications Surveys & Tutorials, 2020, 22(3): 2009-2030. |
| [9] | ZHENG Peilin, ZHENG Zibin, CHEN Weili, et al. EtherShare: Share Information in Jointcloud Environment Using Blockchain-Based Smart Contracts[C]// IEEE. 2019 IEEE International Conference on Service-Oriented System Engineering(SOSE). New Jersey: IEEE, 2019: 233-238. |
| [10] |
DU Mingxiao, CHEN Qijun, CHEN Jieying, et al. An Optimized Consortium Blockchain for Medical Information Sharing[J]. IEEE Transactions on Engineering Management, 2020, 68(6): 1677-1689.
doi: 10.1109/TEM.2020.2966832 URL |
| [11] | PENG Ruyue, MA Zhaofeng, LUO Shoushan. Research and Implementation of Digital Content Service and Security Supervision Technology Based on Blockchain[J]. Netinfo Security, 2020, 20(10): 49-56. |
| 彭如月, 马兆丰, 罗守山. 基于区块链的数字内容服务与安全监管技术研究与实现[J]. 信息网络安全, 2020, 20(10):49-56. | |
| [12] |
GONG S, LEE C. BLOCIS: Blockchain-Based Cyber Threat Intelligence Sharing Framework for Sybil-Resistance[J]. Electronics, 2020, 9(3): 521-541.
doi: 10.3390/electronics9030521 URL |
| [13] | HOMAN D, SHIEL I, THORPE C. A New Network Model for Cyber Threat Intelligence Sharing Using Blockchain Technology[C]// IEEE. 10th IFIP International Conference on New Technologies, Mobility and Security(NTMS). New Jersey: IEEE, 2019: 1-6. |
| [14] | HUANG Kezhen, LIAN Yifeng, FENG Dengguo, et al. Cyber Security Threat Intelligence Sharing Model Based on Blockchain[J]. Journal of Computer Research and Development, 2020, 57(4): 836-846. |
| 黄克振, 连一峰, 冯登国, 等. 基于区块链的网络安全威胁情报共享模型[J]. 计算机研究与发展, 2020, 57(4):836-846. | |
| [15] | GB/T 36643-2018 Information Security Technology-Cyber Security Threat Information Format[S]. Beijing: Standards Press, 2018. |
| GB/T 36643-2018 信息安全技术网络安全威胁信息格式规范[S]. 北京: 标准出版社, 2018. | |
| [16] | Oasis. Introduction to Structured Threat Information Expression (STIX)[EB/OL]. [2021-10-05]. https://oasis-open.github.io/cti-documentation/stix/intro. |
| [17] | LU Aitong, ZHAO Kuo, YANG Jingying, et al. Research on Cross-Chain Technology of Blockchain[J]. Netinfo Security, 2019, 19(8): 83-90. |
| 路爱同, 赵阔, 杨晶莹, 等. 区块链跨链技术研究[J]. 信息网络安全, 2019, 19(8):83-90. | |
| [18] | LI Dawei, HUO Ying. Cross Domain Authentication of Power IoT Based on Side Chain[J]. Electric Power Engineering Technology, 2020, 39(6): 8-12. |
| 李大伟, 霍瑛. 基于侧链技术的电力物联网跨域认证[J]. 电力工程技术, 2020, 39(6):8-12. | |
| [19] | WeBank. WeCross Open Source Blockchain Platform[EB/OL]. [2021-10-11]. https://wecross.readthedocs.io/zh_CN/latest/. |
| WeBank. WeCross开源区块链跨链协作平台[EB/OL]. [2021-10-11]. https://wecross.readthedocs.io/zh_CN/latest/. | |
| [20] | Oasis. Oasis CTI TC Open Source Cyber Threat Reports[EB/OL]. [2021-10-05]. https://oasis-open.github.io/cti-documentation/stix/examples. |
| [1] | HUA Jingyu, HUANG Daming. Survey of Formal Specification Methods in Theorem Proving of Ethereum Smart Contract [J]. Netinfo Security, 2022, 22(5): 11-20. |
| [2] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [3] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [4] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 23(3): 20-28. |
| [5] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| [6] | WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage [J]. Netinfo Security, 2022, 22(2): 21-31. |
| [7] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [8] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain [J]. Netinfo Security, 2022, 22(2): 55-63. |
| [9] | LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng. An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework [J]. Netinfo Security, 2022, 22(1): 27-36. |
| [10] | FENG Jingyu, WANG Tao, YU Tingting, ZHANG Wenbo. A Secure Medical Data Sharing Scheme Based on Multi-clouds and Multi-chains Collaboration [J]. Netinfo Security, 2022, 22(1): 9-18. |
| [11] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance [J]. Netinfo Security, 2021, 21(9): 32-39. |
| [12] | CHEN Kaijie, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Method of PoS Consensus Protocol Based on Byzantine Fault Tolerance [J]. Netinfo Security, 2021, 21(8): 35-42. |
| [13] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [14] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| [15] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||