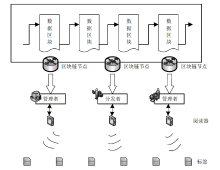
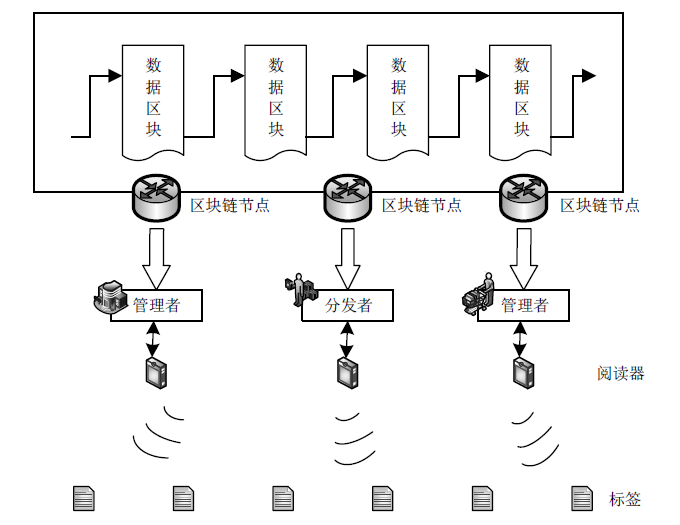
Netinfo Security ›› 2021, Vol. 21 ›› Issue (5): 1-11.doi: 10.3969/j.issn.1671-1122.2021.05.001
Previous Articles Next Articles
RFID Security Authentication Protocol Based on Blockchain Technology
LI Peng1,2( ), ZHENG Tiantian1, XU He1,2, ZHU Feng1,2
), ZHENG Tiantian1, XU He1,2, ZHU Feng1,2
- 1. School of Computer Science, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
2. Jiangsu High Technology Research Key Laboratory for Wireless Sensor Networks, Nanjing 210023, China
-
Received:2020-12-19Online:2021-05-10Published:2021-06-22 -
Contact:LI Peng E-mail:lipeng@njupt.edu.cn
CLC Number:
Cite this article
LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology[J]. Netinfo Security, 2021, 21(5): 1-11.
share this article
| [1] |
SUN Hong, SU Cheng, CHEN Shiping. A High Security RFID System Authentication Protocol Design Based on Cloud Computer[J]. Wireless Personal Communications, 2018,102(2):1255-1267.
doi: 10.1007/s11277-017-5192-1 URL |
| [2] |
CHIEN Hungyu, HUANG Chenwei. A Lightweight Authentication Protocol for Low-cost RFID[J]. Journal of Signal Processing Systems, 2010,59(1):95-102.
doi: 10.1007/s11265-008-0281-8 URL |
| [3] |
ZENG Shiqin, HUO Ru, HUANG Tao, et al. Survey of Blockchain: Principle, Progress and Application[J]. Journal on Communications, 2020,41(1):134-151.
doi: 10.1111/j.1460-2466.1991.tb02297.x URL |
| 曾诗钦, 霍如, 黄韬, 等. 区块链技术研究综述:原理、进展与应用[J]. 通信学报, 2020,41(1):134-151. | |
| [4] |
HE Debiao, KUMAR N, CHILAMKURTI N, et al. Lightweight ECC Based RFID Authentication Integrated with an ID Verifier Transfer Protocol[J]. Journal of Medical Systems, 2014,38(10):1-6.
doi: 10.1007/s10916-013-0001-1 URL |
| [5] | LEE Chini, CHIEN Hungyu. An Elliptic Curve Cryptography-based RFID Authentication Securing E-health System[J]. International Journal of Distributed Sensor Networks, 2015,12(11):1-7. |
| [6] |
FAN Kai, GONG Yuanyuan, LIANG Chen, et al. Lightweight and Ultralightweight RFID Mutual Authentication Protocol with Cache in the Reader for IoT in 5G[J]. Security and Communication Networks, 2016,9(16):3095-3104.
doi: 10.1002/sec.v9.16 URL |
| [7] |
LI Nan, SUSILO W, VARADHARAJAN V, et al. Vulnerabilities of An ECC-based RFID Authentication Scheme[J]. Security and Communication Networks, 2015,8(17):3262-3270.
doi: 10.1002/sec.1250 URL |
| [8] | HA J, KIM H, PARK J, et al. HGLAP-hierarchical Group-index Based Lightweight Authentication Protocol for Distributed RFID System[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1x240gd0hy6c0pw0dj7700r0aq265758&site=xueshu_se, 2020-12-06. |
| [9] | RHEE K, KWAK J, KIM S, et al. Challenge-response Based RFID Authentication Protocol for Distributed Database Environment[C]// Springer. International Conference on Security in Pervasive Computing, July 13-15, 2005, Boppard. Berlin: Springer, 2005: 70-84. |
| [10] | MUJAHID U, ISLAM M, SARWAR S. A New Ultralightweight RFID Authentication Protocol for Passive Low Cost Tags: KMAP[J]. Wireless Personal Communications, 2017,3(9):725-744. |
| [11] | TOYODA K, MATHIOPOULOS Pt, SASASE I, et al. A Novel Blockchain-based Product Ownership Management System (POMS) for Anti-counterfeits in the Post Supply Chain[J]. IEEE Access, 2017,17(5):17465-17477. |
| [12] | ZHANG Xiaohan. Research on Identity Authentication Protocol of Internet of Things Equipment Based on Blockchain[D]. Hefei: University of Science and Technology of China, 2019. |
| 张霄涵. 基于区块链的物联网设备身份认证协议研究[D]. 合肥:中国科学技术大学, 2019. | |
| [13] | SIDOROV M, ONG M, SRIDHARAN R, et al. Ultralightweight Mutual Authentication RFID Protocol for Blockchain Enabled Supply Chains[J]. IEEE Access, 2019,19(7):7273-7285. |
| [14] |
JANGIRALA S, DAS A, VASILAKOS A. Designing Secure Lightweight Blockchain-enabled RFID-based Authentication Protocol for Supply Chains in 5G Mobile Edge Computing Environment[J]. IEEE Transactions on Industrial Informatics, 2019,16(11):7081-7093.
doi: 10.1109/TII.9424 URL |
| [15] |
PREMNATH S, HAAS Z. Security and Privacy in the Internet-of-things Under Time-and-budget-limited Adversary Model[J]. IEEE Wireless Communications Letters, 2015,4(3):277-280.
doi: 10.1109/LWC.2015.2408609 URL |
| [16] | FERNÁNDEZ C, FRAGA L P. Reverse Engineering the Communications Protocol of an RFID Public Transportation Card[C]// IEEE. 2017 IEEE International Conference on RFID, May 9-11, 2017, Phoenix, AZ, USA. New York: IEEE, 2017: 30-35. |
| [17] | ZHAO Guogang, YU Haiye, WANG Guowei, et al. Applied Research of IOT and RFID Technology in Agricultural Product Traceability System[C]// Springer. International Conference on Computer and Computing Technologies in Agriculture, October 23-25, 2015, Cham. New York: Springer, 2015: 506-514. |
| [18] |
GOPE P, LEE J, QUEK T. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions[J]. IEEE Transactions on Information Forensics and Security, 2018,13(11):2831-2843.
doi: 10.1109/TIFS.2018.2832849 URL |
| [19] | WANG Siye, ZHU Shaoyi, ZHANG Yangfang. Blockchain-based Mutual Authentication Security Protocol for Distributed RFID Systems[C]// IEEE. 2018 IEEE Symposium on Computers and Communications (ISCC), June 25-28, 2018, Natal, Brazil. New York: IEEE, 2018: 74-77. |
| [20] |
LU Yang. The Blockchain: State-of-the-art and Research Challenges[J]. Journal of Industrial Information Integration, 2019,15(2):80-90.
doi: 10.1016/j.jii.2019.04.002 URL |
| [21] | ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends[J]. IEEE International Congress on Big Data, 2017,27(1):557-564. |
| [22] |
BURROWS M, ABADI M, NEEDHAM R. A Logic of Authentication[J]. ACM SIGOPS Operating Systems Review, 1989,23(5):1-13.
doi: 10.1145/74851.74852 URL |
| [23] | ABADI M, TUTTLE M. A Semantics for a Logic of Authentication[C]// Association for Computing Machinery. Proceedings of the Tenth Annual ACM Symposium on Principles of Distributed Computing, August 21-24, 1991, Montreal, Quebec, Canada. New York: ACM, 1991: 201-216. |
| [24] | GONG L, NEEDHAM R, YAHALOM R. Reasoning about Belief in Cryptographic Protocols[C]//IEEE Computer Society Press. the 1990 IEEE Computer Society Symposium on Research in Security and Privacy, May 7-9, 1990, Los Alamitos, California. New York: IEEE Computer Society Press, 1990: 234-248. |
| [1] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [2] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [3] | WANG Kaixuan, TENG Yajun, WANG Qiongxiao, WANG Wei. Research on the Application of SM Algorithms of Implicit Certificate [J]. Netinfo Security, 2021, 21(5): 74-81. |
| [4] | ZHANG Yu, SUN Guangmin, LI Yu. Research on Mobile Internet Authentication Scheme Based on SM9 Algorithm [J]. Netinfo Security, 2021, 21(4): 1-9. |
| [5] | WANG Jian, ZHAO Manli, CHEN Zhihao, SHI Bo. An Authentication Scheme for Conditional Privacy Preserving Based on Pseudonym in Intelligent Transportation [J]. Netinfo Security, 2021, 21(4): 49-61. |
| [6] | LIU Yanhua, LIU Zhihuang. An Anonymous Data Authentication Method Based on User Behavior Pattern [J]. Netinfo Security, 2021, 21(3): 44-52. |
| [7] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [8] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-keyword Fine-grained Searchable Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 34-44. |
| [9] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| [10] | DONG Qiang, LUO Guoming, SHI Hongkui, ZHANG Yongyue. Research on Authentication and Key Agreement Method of IMS-based Mobile Communication Private Network [J]. Netinfo Security, 2021, 21(1): 88-96. |
| [11] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [12] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| [13] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [14] | YU Guo, WANG Chonghua, CHEN Xuehong, LI Jun. Industrial Internet Identifier Resolution Security from the Perspective of Authentication [J]. Netinfo Security, 2020, 20(9): 77-81. |
| [15] | SHI Runhua, SHI Ze. Key Management Scheme for IoT Based on Blockchain Technology [J]. Netinfo Security, 2020, 20(8): 1-8. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||